Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

Have the sniffles? Yes. Does your head hurt? Yes. Coughing? Yes. Could you have influenza? Yes. How do you know the difference? With these symptoms, you could also have a cold.

It hasn't even been eight years since Candida auris was discovered—cultured and identified from the ear canal of a patient in Japan—and now it's drug-resistant, setting up residence in hospitals, killing patients, and wreaking havoc across the globe.

One thousand feet under the ground, extremophile microbes that have not seen the light of day for four million years are giving up some fascinating facts to scientists who go the distance.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

Seaweed isn't just for rolling sushi anymore. The food science world is introducing chefs and home cooks to dulse (rhymes with pulse), kale's wacky seaweed cousin that tastes surprisingly like bacon and may even be the next big superfood.

Whether you simply can't stand it or consider it a separate food group (or not food at all), there's no denying that Spam is everywhere. America's favorite canned mystery meat got its humble beginning in Minnesota, but is now used in dishes and found in homes around the globe.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

Though nobody's going to hide the fact that they're getting sloshed on major holidays, you might want to be more discreet when it comes to your morning pick-me-up or lunchtime tipple during the rest of the year. It used to be that having four martinis at lunch was acceptable and even desirable, but that's really not the case anymore.

Some women see Halloween as a once-a-year opportunity to dress in something skimpy without dealing with as much scrutiny as usual. That can be fun, but not everyone is comfortable enough wearing so little, and the costumes are so boring and repetitive. Some of us just don't feel like freezing.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Why is transferring contacts from an old smartphone to a new one still insanely difficult? I can check my bank account, upload a picture to Instagram, email someone across the globe, and check the weather forecast on my phone—all in under five minutes.

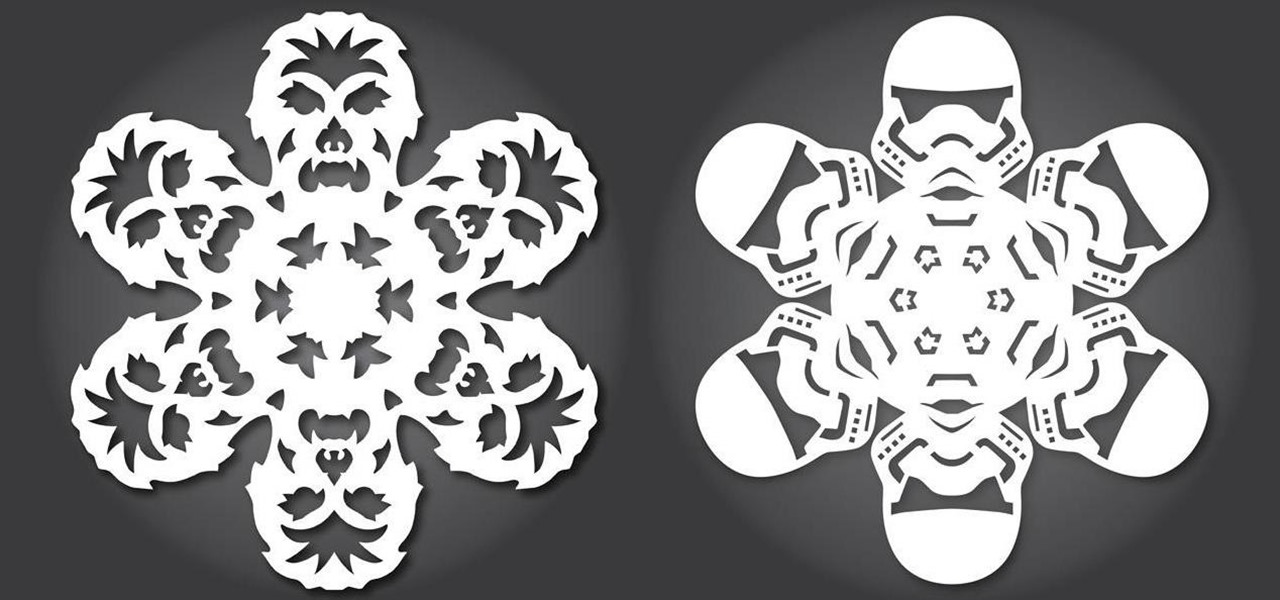
Everyone knows how to make paper snowflakes, but the kind you learned to cut in kindergarten can get a little boring. However, they are free DIY holiday decorations, and they don't have to be a generic snowflake design. They can be anything you want, from nerdy math kirigami to all the Star Wars characters you can think of!

United Arab Emirates is the cosmopolitan country that offers various attractions for tourists across the world. This country has buildup its image as one the fastest growing country of this region. Besides visiting worth seeing places, travelers can also enjoy tasty traditional food of UAE across the country. Whether you have chosen Dubai, Abu Dhabi, Ajman or Ras Al Khaimah, you will get the chance to enjoy best traditional food everywhere.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Welcome back, my rookie hackers!

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

After closing its office last year, enterprise AR company Daqri has moved on to the final stage of its lifecycle with the liquidation of its assets.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

Since the release of iOS 13.3 beta 3 on Nov. 20, Apple has remained silent on new beta updates. That's likely because there was a holiday the following week, and then all of the major shopping events after that. But now, it's back in the game, and on Thursday, Dec. 5, Apple pushed out iOS 13.3 developer beta 4 and public beta 4.

Apple is often unpredictable when it comes to beta releases, especially with public betas. Developers receive their updates first, then public testers have to wait and see if Apple will do the same for us. Sometimes, the iPhone OEM makes us wait until the following day, but not with iOS 13.3 public beta 2. This update is now available to download and install.

We're finally back in the swing of things. For the first 26 days after the release of iOS 13.2, which introduced 22 new features and changes to the iOS 13 era, there wasn't a new beta. Then, Apple released iOS 13.3 developer beta 1, and now we seem to be back on schedule, as Apple just released 13.3 beta 2 to developers.

Who's ready for another beta season? We beta testers have had quite the break: Apple released the fourth public beta for 13.2 on Oct. 23, and since then, two full weeks have gone by without a shred of beta news. It seems this Wednesday, Nov. 6 is our lucky day, as Apple just released the first public beta for iOS 13.3.

The latest official update for iPhone, iOS 13.2, introduced 22 new features and changes to the iOS 13 era, building off the improvements brought by iOS 13.1 and iOS 13 proper before it. It's time to take our first peek into what's next for iPhone and iOS, as Apple releases iOS 13.3 developer beta 1 today, Tuesday, Nov. 5.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

Viewing and reading content on websites is inherently harder to do on an iPhone due to the relatively small display. Even if you have an iPhone XS Max or 11 Pro Max, you'll probably struggle sometimes to read through tiny text while browsing online. Thanks to a feature found within Safari's view menu in iOS 13, your eyes can rest a little easier.