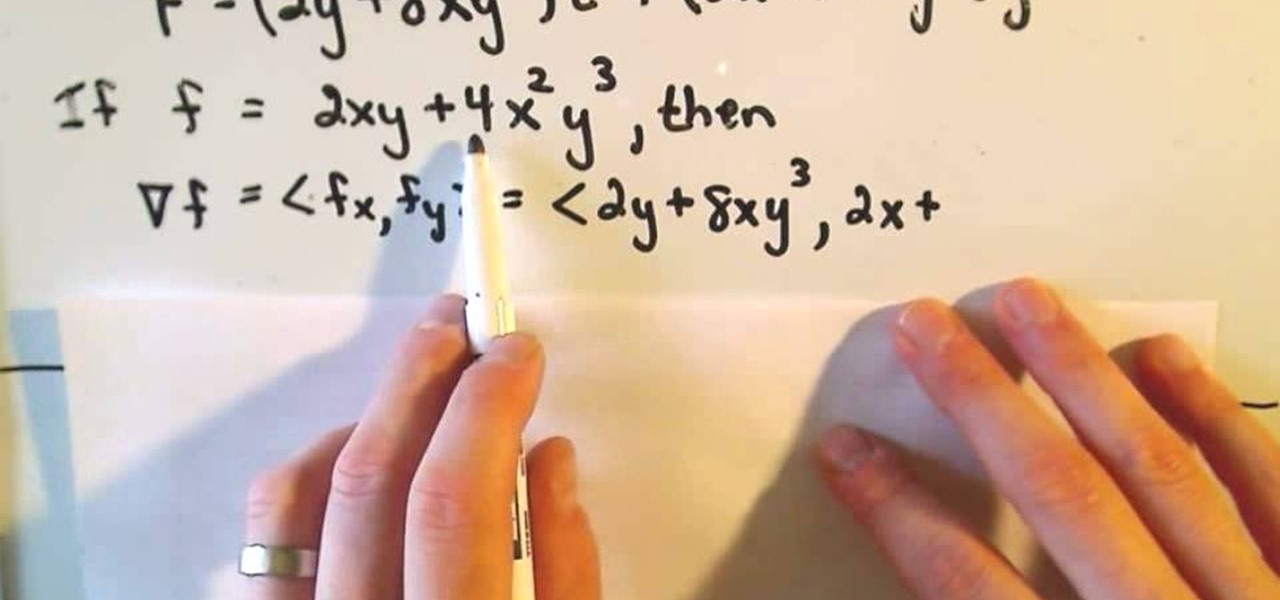Professor ElvisZap teaches you how to stretch shift and reflect the graph of a square root. A square root function is the opposite of a squared function. You start with y=square root of (x-1) it becomes 0<=x-1. then 1 <=x. You use the graph and solve it as you would for any function using small values first, then you have y=square root of x - 1, the domain 0<=x. This shifted the graph down 1 unit. 0=square root of x - 1, 1=square root of x, 1=x. Then the range is [-1 + infinity). Continue in ...
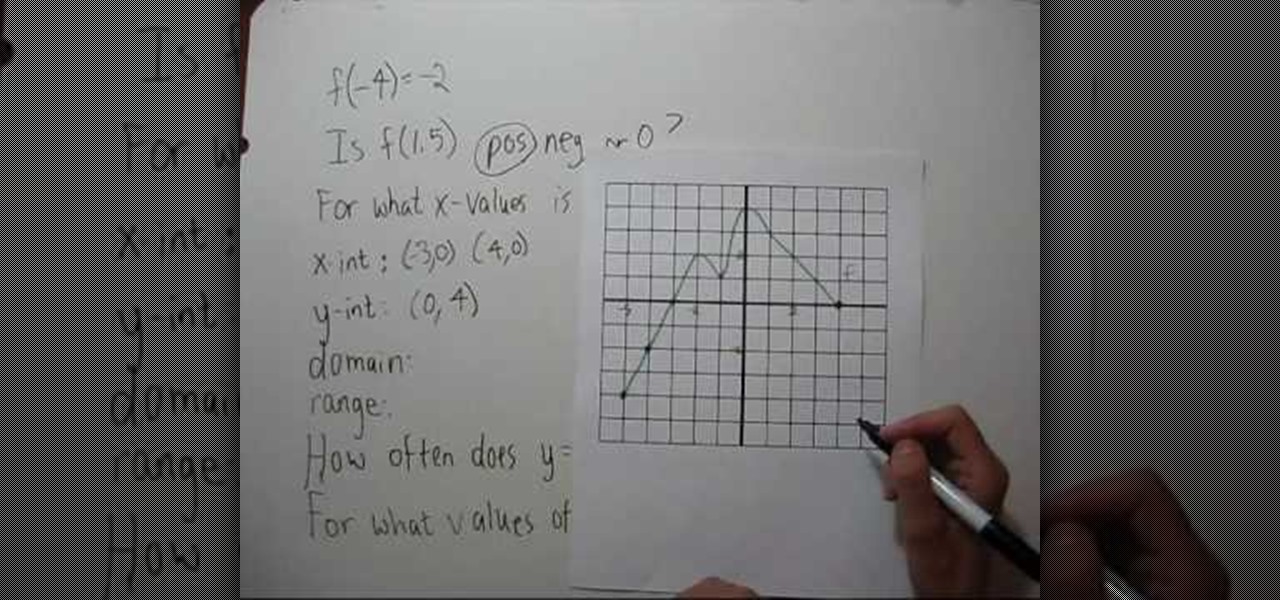
YouTube user NotesCollegeAlgebra teaches you how to interpret a graph. You will learn how to read it and extract information. You go to the graph to see that f(-4)=-2. f(1.5)=2, so it's positive. You then have the question: For what x-values is f(x)<0? You go to the graph and see that you come up with (-5,3). The x-int is (3,0) (4,0). The y-int is (0,4). The domain is (-5,4) and the range is (-4,4). You then have the question: how often does y=7/5 intercept the graph? The answer is 4 times. T...
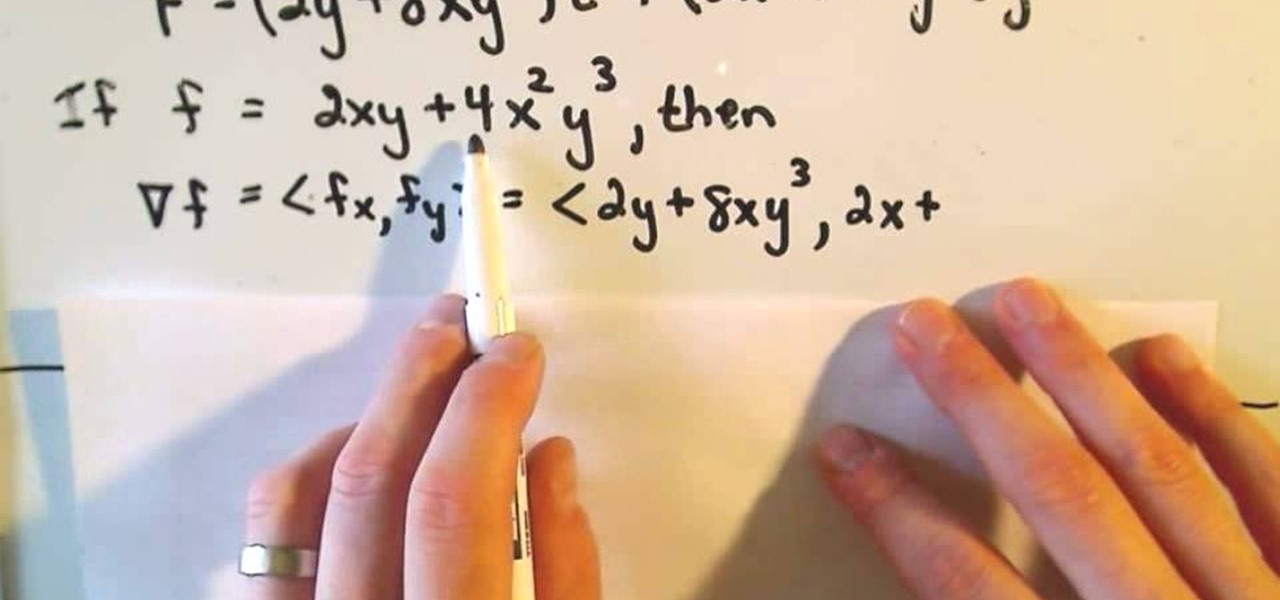
A conservative vector field is defined as being the gradient of a function, or as a scaler potential. Conservative vector fields are not dependent on the path; they are path independent. Conversely, the path independence of the vector field is measured by how conservative it is. These fields are also characterized as being ir-rotational, which means they have vanishing curls. Actually, ir-rotational vector fields are conservative as long as a certain condition on the geometry of the domain is...

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create rotating planets and moons in Photoshop.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyone to learn or brush up on their Morse code skills — and it works on both Android and iOS.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

When typing an email or website address in a compatible input field on an iPhone, most people will manually type in the domain extension. But there's a much faster way to enter domain suffixes for email addresses and website URLs that you should be using on your keyboard. Even better, there's a way to customize what domain extensions appear in the keyboard shortcut!

We're beyond the days where iPhones fit perfectly in most hands. The iPhone 11 Pro is still a bit big for many people, and the 11 Pro Max is truly massive. If you're having trouble typing out your thoughts without using two hands, know that there's a quick way to make one-handed typing possible on any iPhone.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Watch this video and learn how to make a wonderful magical snow globe perfect for Christmas or any other holiday. You just need a jar with a lid, some pure glycerin, glittery snowflakes, and a Christmas figurine of your choice (e.g., Santa, reindeer, elves, etc.).

When words aren't enough, emojis are there to help. Your iPhone has almost two thousand of them for you to communicate in a more lively manner or to express indifference, excitement, joy, and other emotional states. However, the more emojis that come out, the more difficult it is to find the one you want — unless you know your way around your keyboard.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

As long as you have the meeting ID, you can join and interrupt virtually any video call on Zoom. And that's how we get terms such as "Zoom-bombing," where someone jumps into a chat to say or visually show vulgar and inappropriate things to the other participants. However, hosts can put an end to it.

The deadly Wuhan coronavirus outbreak has not only has claimed lives in China but also has caused disruption around the globe, particularly in the tech industry. To date, the virus has claimed more than 1,000 lives in China, according to the country's officials.

In recent years, Google's Arts & Culture project has been leading the way in terms of innovating the practice of using technology to preserve landmarks and great works of art via digital 3D copies. Increasingly, these efforts are also giving history buffs the chance to experience classic works and spaces with unparalleled intimacy through the wonders of augmented reality.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

Augmented reality platform maker Zappar and its marker-based augmented reality technology have been around well before Apple and Google brought markerless AR to mobile apps.

As Magic Leap continues to spread its influence in the US with the help of wireless carrier AT&T, the augmented reality startup is also working its way into East Asia.

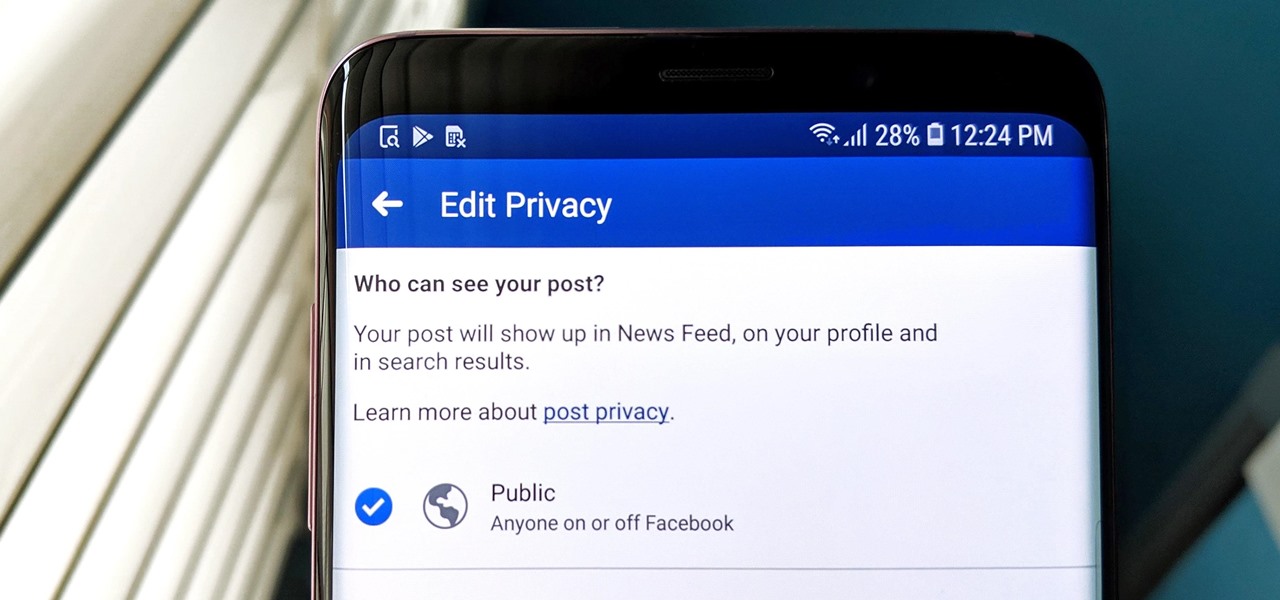
Facebook has grown into one of the central hubs of the internet where ideas are shared with others. But with the rise of brand development, individuals and companies need to get their messages out beyond their group of Facebook friends so it can be seen by more of the world.

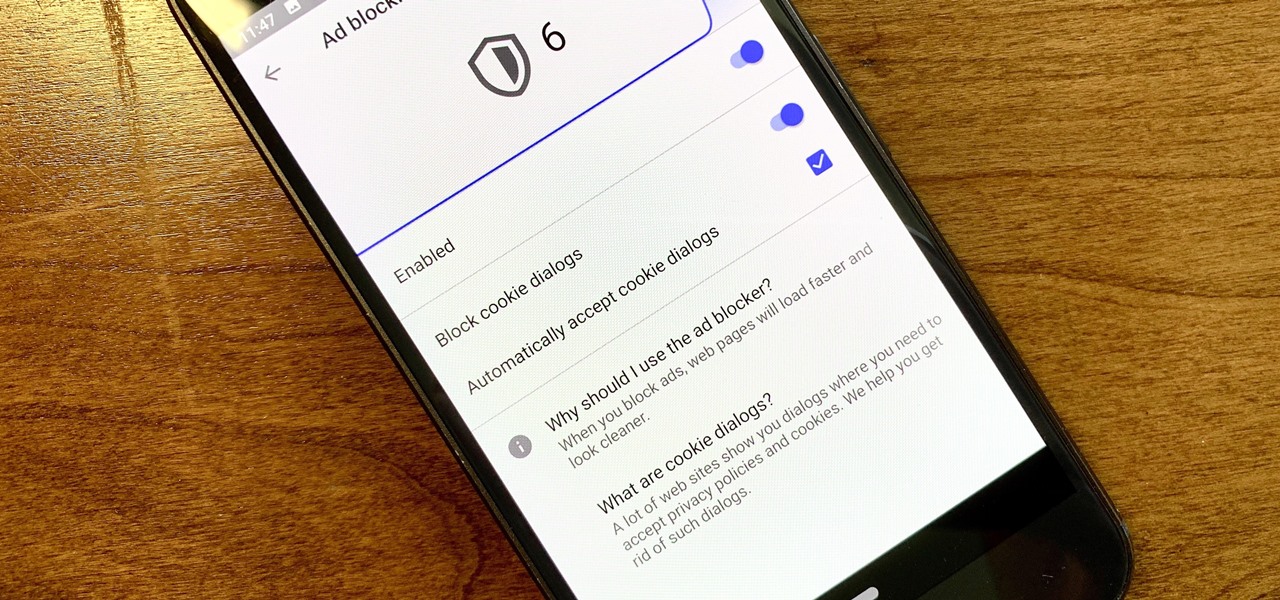
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

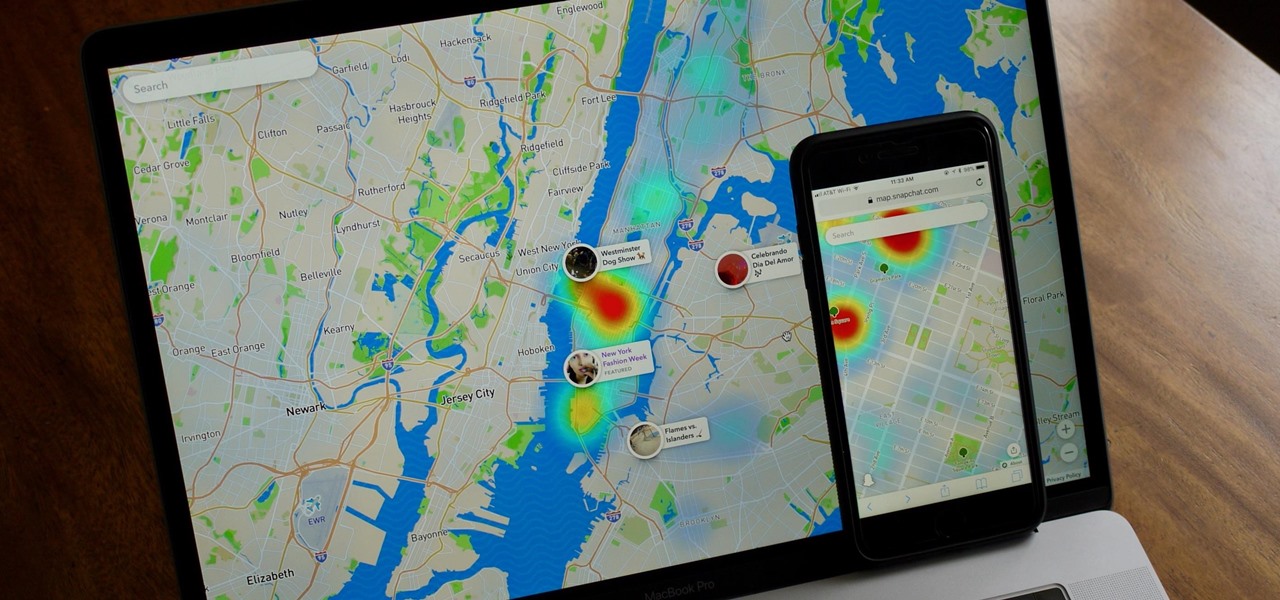
When first released, Snap Map made a lot of users uneasy. Beaming their location to the world at all times isn't necessarily the definition of privacy, but Snapchat's map is nonetheless intriguing, offering users a view into the lives of people across the globe. Now, you don't even need to have an account to access Snap Map — you can view it right from your web browser.

Volunteer project Standard Ebooks strives to enhance some of the work available from Project Gutenberg and other public domain text sources, making them easier on the eyes.

While the numbers may not always seem to agree, the message remains the same: augmented reality is a growth segment. This week's edition of Market Reality starts with two new reports outlining the expected good fortunes for the industry and concludes with an example of a company capitalizing on their own growth.

The company that pioneered music scanning for mobile devices is moving into the augmented reality advertising arena. Included in an update of their iOS and Android apps last week, Shazam can now scan special codes to immerse users in 3D animations, 360-degree videos, mini-games, and other AR content.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

In 2014, Snapchat introduced a special type of Filter called Geofilters. Geofilters only appear when you're in a specific location. For example, a Disney Land Geofilter will only appear if you're actually there. Rather, your phone needs to think that you're at Disney Land. By spoofing your GPS location, you can effectively travel all across the globe — at least in the eyes of Snapchat.

Mother Nature is one creative entity, especially when it comes to fruit. Let's face it: most major supermarkets stock only the most common fruits like apples, pears, and grapes, but they're so basic. Why not explore other options, from the stinky-yet delicious durian to the captivating citrus caviar that is finger limes?