
How To: Detect paint layers on a car
See what to look for in a car's paint job to detect that the car paint has been redone or replaced, uncovering clues about the car's accident history and resale value.


See what to look for in a car's paint job to detect that the car paint has been redone or replaced, uncovering clues about the car's accident history and resale value.

Your iPhone's clipboard can only save one item at a time, so it may seem impossible to retrieve your entire history of copied text, images, and other content. Luckily, there is a workaround you can use to find and copy your past clipboard contents, but you have to implement it first.

You can quickly correct a mistake in an iMessage you send, but the recipient will still see whatever you originally wrote since there's a history of edits. When you don't want the other person in the conversation to know what you originally sent, there's a better thing you can do.

One of the most iconic architectural landmarks on the planet, the Arc de Triomphe in Paris, France, will become a part of augmented reality history thanks to a new project from Snap.

We already know that the US Army will be using its modified HoloLens 2 for special missions, and major businesses are deploying the augmented reality device for enterprise use cases.
Your iPhone keeps track of every single place you go, especially those you frequent most often, and syncs those locations across all your iCloud-connected devices. People who gain access or already have access to your iPhone, iPad, iPod touch, or Mac may be able to view all of these locations to see where you've been and where you might be. If this worries you, there are things you can do.

The pandemic has forced a number of public-facing businesses to either temporarily close or permanently cease operations, with one of the biggest victims of this trend being the movie theater business.
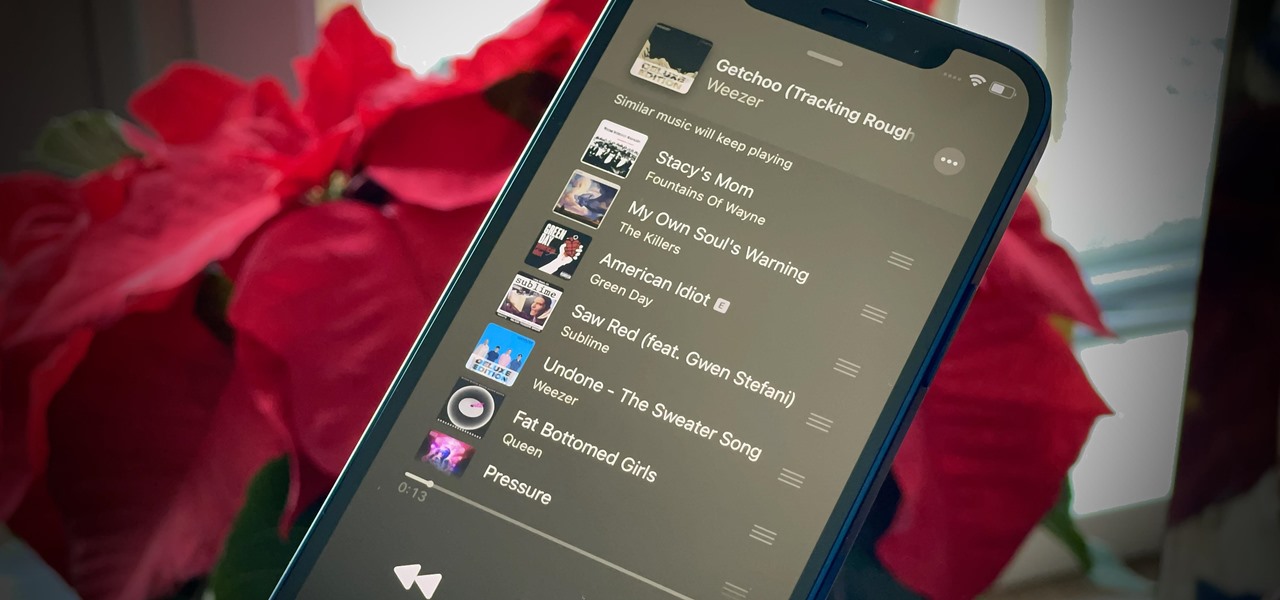
No matter how expertly crafted a playlist is or how long your favorite album runs, they all come to an end eventually. And nothing quite kills the vibe like your DJ suddenly running out of steam. But a feature in Apple Music for iOS and Android will continue playing songs after an album or playlist is over, choosing tracks that fit perfectly with what you were just listening to.

The true crime genre has long been popular on television and more recently on podcasts with shows like Serial.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.
Unless you've been hiding under a (moon) rock for the past month, you already know that Saturday, July 20 is the 50th anniversary of NASA's Apollo 11 lunar landing.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.
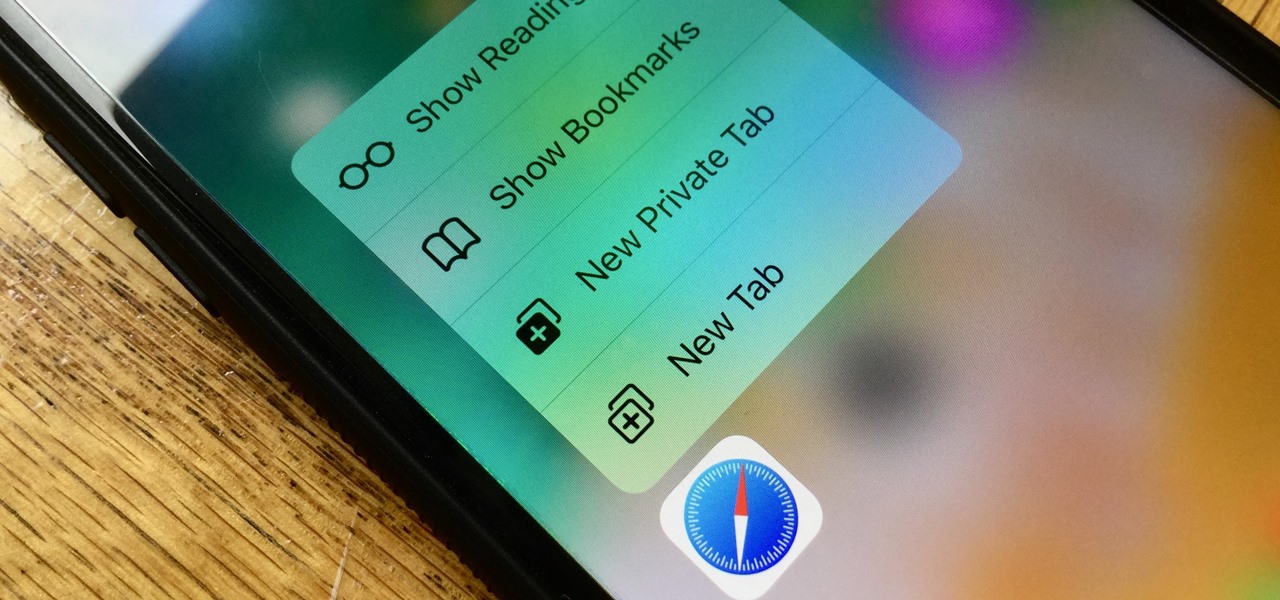
Introduced on the iPhone 6s, 3D Touch is just about the closest thing to a "right-click" that we have on iOS. Apple and app developers utilize this feature to give us helpful options that might otherwise clutter the overall app experience, as well as opportunities to "peek" into an action without committing to it. Safari on iPhone is no exception.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.
While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

For as long as 14,000 years, the First Nations people of the Heitsuk Nation have made their home along the Central Coast of the Canadian province of British Columbia. Among the territory's inlets, islands, rivers, and valleys lie a clay deposit on the north side of Kisameet Bay, near King Island. For as long as most can remember, the tribe has used the clay as medicine. Now science says microbes that live in that clay may have important antibacterial properties.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

We all know you are what you eat—or so the expression goes—but it's good to remember that what you are (at least intestinally) is mainly bacteria. A new study has shown that what you eat, and how your gut microbiome reacts to that food, might be a key player in your risk of developing a certain type of colon cancer—and changing your diet can help decrease your risk.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Though the word "pie" may conjure up images of a dessert made of dough with various fillings, the famous Frito Pie is, in fact, something of an entirely different nature. Absurdly simple in its construction, this pile of Fritos and chili is served in the actual chip bag and more closely resembles nachos than it does a traditional pie.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

If you think that "pawpaw" is just an affectionate name for your grandfather or a cute way of talking about your cat's feet, you're missing out on one of the most interesting fruits out there.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Any beer aficionado who's been to Ireland will always talk about how the Guinness there "just tastes different." But save your eye rolls, skeptics: it turns out your favorite lagerhead actually has a valid point.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

When I was younger, my family would go to fancy restaurants and I would invariably order a Shirley Temple. (Ironically, the real Shirley Temple actually didn't like it much.) But it's hard to really find anything offensive in this kiddie cocktail: It's ginger ale with a splash of grenadine. There's also the less famous Roy Rogers, which is Coca-Cola with grenadine. The grenadine, red and sumptuous, always made its drinks look and taste much cooler.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Welcome back, my aspiring hackers!

Everyone hates to feel like they've been taken advantage of, especially when buying a used vehicle. The thought comes across every car buyer's mind... "Did I just get taken by that smooth-talking salesman?" When it comes to cars, how do you know if you're really getting a good deal, or if you're being offered a fair price for your car? After all, cars are most peoples second largest investment, so we need to make this decision wisely.

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.