There's absolutely nothing comfortable about flying, unless you happen to be tiny enough to fit into the limited space offered on airplanes, or wealthy enough to afford a first-class ticket. And if you're about to embark on a long flight, catching a few Zs can feel like an impossible task. But it's definitely not impossible to get some quality sleep for a few hours, you just need to know how to use that limited space to your advantage.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Sooner or later, you're going to come across a person at work that you don't like—or someone that doesn't like you. This can result in uncomfortable tension, insulting gossip, and a disrespectful attitude, to name just a few of the negatives. But it doesn't have to be that way. The next time you're having a workplace conflict with a particularly challenging coworker, the best thing you can do is keep your mouth shut, and here's how to do it.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.

Baking is one of life's greatest joys. There's something truly magical about taking a half a dozen humble ingredients, mixing them until they're an odd-colored sludge, tossing them into an oven, and watching them emerge as something elegant and delicious.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

What is gluten, why do some people think it is pure culinary evil, and why are there more and more products devoted to being free of this mysterious substance? Here's what one person thinks: What Is Gluten Really?

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

To make soap, you need fat, and if you've seen Fight Club, you're probably well aware of where soapmaker Tyler Durden got his fat from. Liposuction clinics. If you're not willing to go that far for a perfect bar of homemade soap, you can just use some drain cleaner and America's favorite food instead—bacon!

When you're using vacuum power, moving water, or compressing air, it's more than likely being done with some sort of pump. I'll be needing a pump for some of my future projects, so in this tutorial, I'll be showing you how to make your own customizable PVC hand pump that will let you do all three.

The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

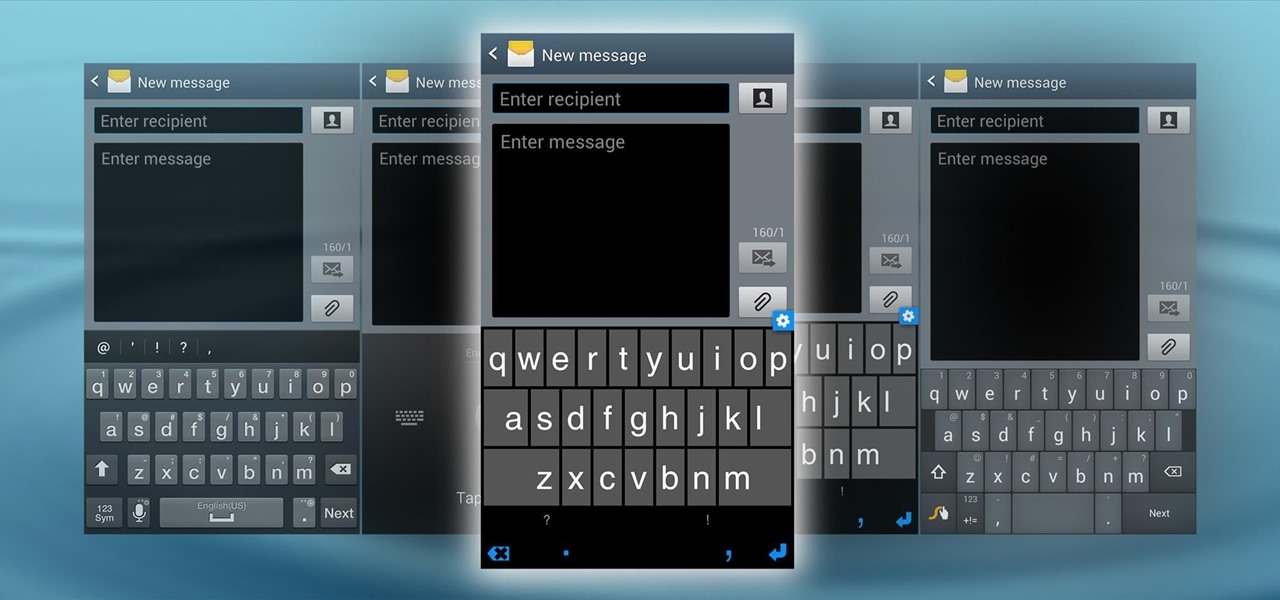
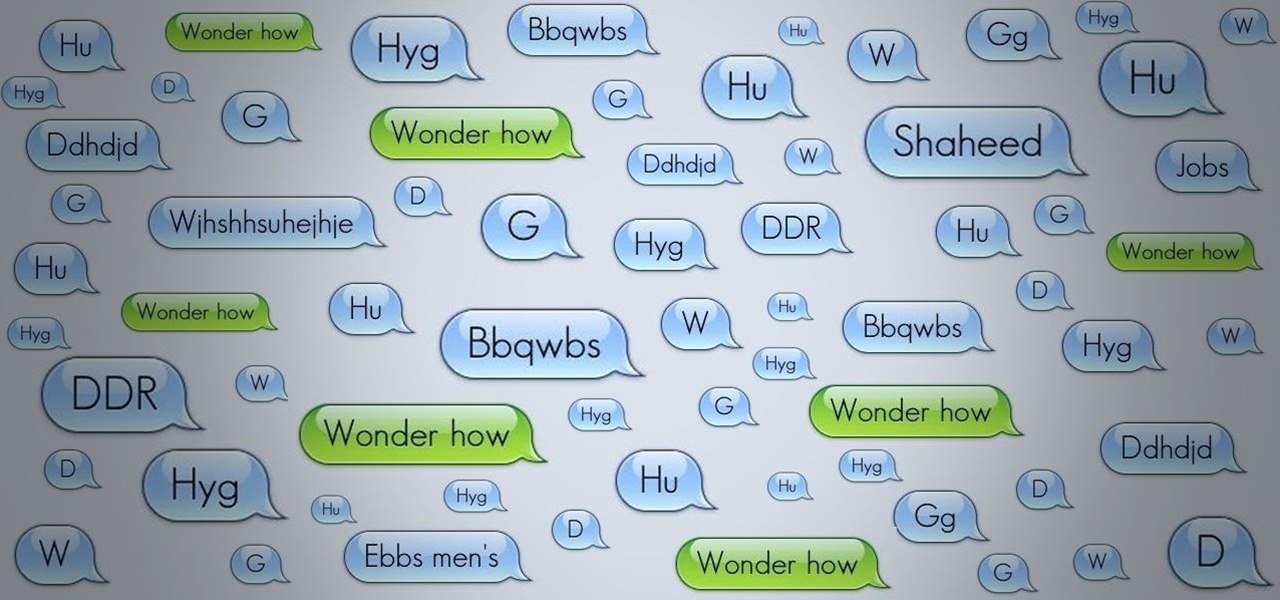
The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

Before I really get into this article, it's important to note that you do not need a Steampunk persona (or "steamsona") in order to be a Steampunk, or wear Steampunk clothes. Some people like to pretend to be a different person when dressed up in Steampunk clothing, but that is entirely optional, and only to be done if it appeals to you. That said, even if you aren't actually acting as your character, it may still be helpful to have one in mind when putting together an outfit. Personally, I'v...

I'm constantly searching for a homemade pizza dough that tastes good but isn't too challenging to execute. In other words, a recipe that doesn't require any arcane "dough whispering" skills. However, my hunt may be coming to an end thanks to one celebrity chef's concept.

We usually focus on augmented reality here, but when something important in VR happens, we highlight it as part of the overall immersive computing story.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

Two of the three entities behind Pokemon GO, the reigning champion in mobile augmented reality gaming, are joining forces again to see if lightning can strike more than once.

While most established media brands are satisfied with copying Pokémon GO to jump into augmented reality gaming, at least one property is taking a slightly different approach.

If you're an aspiring or even well-established web or app developer, the good news is that there's a virtually limitless number of lucrative opportunities waiting for you, regardless of whether you're looking to work for a company or as a freelancer.

Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.