By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

As a part of the already crowded field of diseases transmitted by ticks, you may not know the disease babesiosis, a dangerous infection caused by a parasite that infiltrates blood cells.

Being a city dweller does not mean you cannot save the planet — or your food scraps. Climate change and resource management are big issues. Composting in any size space is not only possible, but it gives you a chance to reduce greenhouse gasses and reuse food scraps. Right now, about 40% of all food in the US goes to the landfill. In addition to planning meals and using your food in creative ways to reduce the amount that goes to waste, you can compost.

You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

The search for the causative agent of colony collapse—the mass die off of honey bees throughout the US and Europe—has escalated with increasing confusion lately. Everything from pesticides and stress to viruses and mites have been implicated, and some researchers think that many of these environmental factors work together to take down hives.

Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

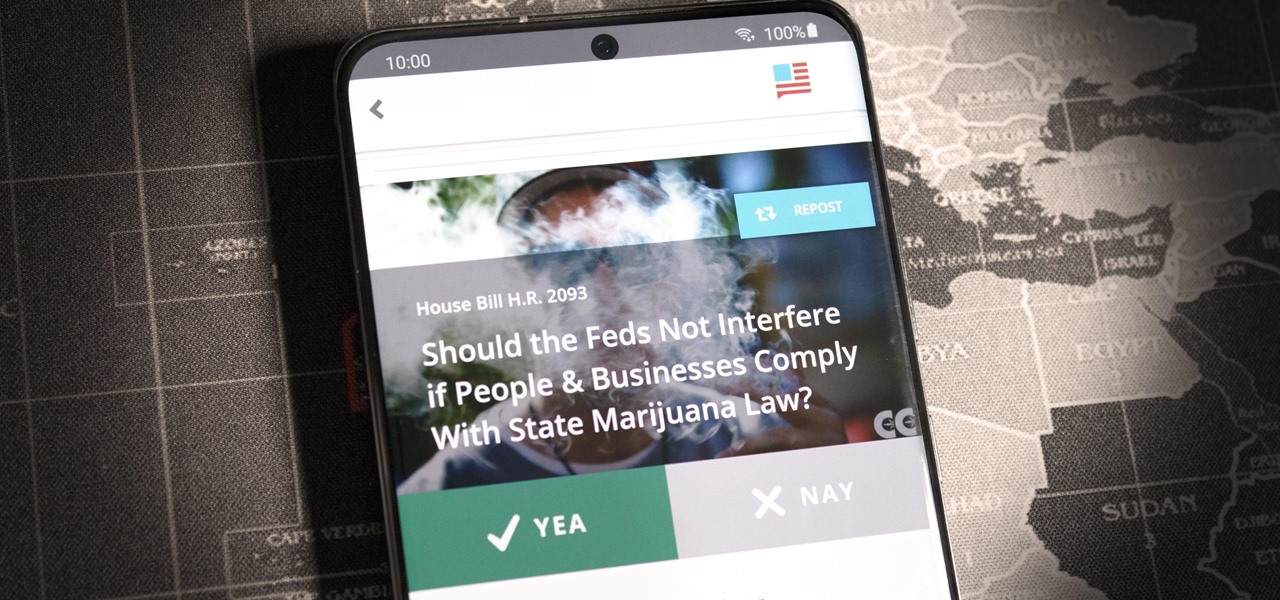
If you live in the US, it's your civic duty to understand our governing bodies and the political system that puts them in place. It doesn't matter what your age is, knowing who to vote for is as important as voting at all. That starts with policing your own representatives to help decide whether or not we should re-elect them.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

Amid the coronavirus chaos, two companies at the forefront of augmented reality technology took starkly different approaches to their upcoming developers conferences, as Facebook has canceled its annual F8 conference and Magic Leap plans to invite a limited number of attendees to its Florida headquarters for LEAP Developer Days.

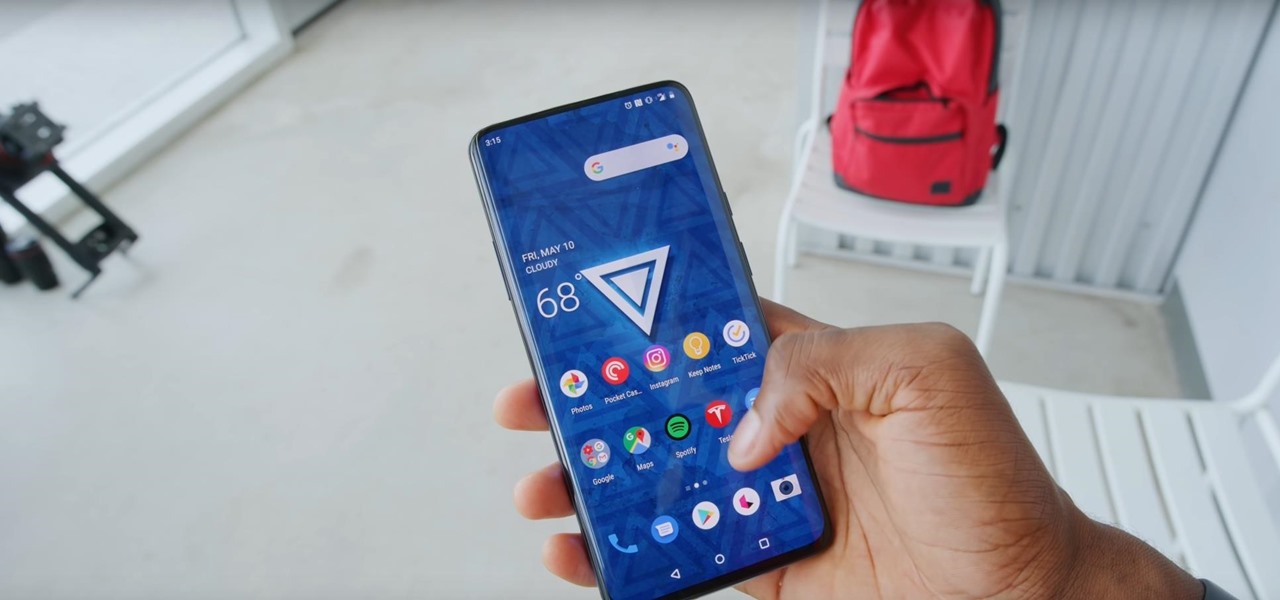
We've all been there — using Google Maps for navigation and waiting for the app to find our location. As we drive around, we keep hoping it will get a lock in time to make the next turn. Well in the US, we finally have a solution to this problem, and it's the OnePlus 7 Pro.

The recent announcement of a $480 million US Army contract awarded to Microsoft over Magic Leap for supplying 100,000 augmented reality headsets shows just a how lucrative the enterprise (and government) sector can be for AR.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Despite Huawei's ongoing battle with the US government, the Chinese company has continued to release phones in the US under its Honor brand. The Honor X series has been consistently released for several years, offering midrange specs at ridiculously low pricing, and the Honor 8X is no exception.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

A recent study offers information that might help combat a deadly virus that affects an estimated 300,000 people each year in West Africa.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

I'll admit it: I ignore expiration dates. No matter if it's a sell-by date, "best if used before" date, or even a use-by date, I don't care. I just check for signs of food decay and keep on eating.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

There's no doubt you've heard the old saying, "When life gives you lemons, make lemonade." The phrase was penned in an obituary to a dwarf actor in 1915 by an anarchist named Elbert Hubbard, who lost his life five months later aboard the RMS Lusitania when it was torpedoed by a German submarine.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?