Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

As we slowly approach its January 3 start date, CES 2017 seems to be shaping up to be an exciting year for smart glasses as well as augmented and mixed reality.

The highly anticipated VR headset hasn't been on the market long, but there's an issue that has some consumers, and even government officials, concerned about the Oculus Rift. You probably guessed the issue surrounds privacy and the extensive, not-so-secret way that it's collecting your personal data. The privacy concerns came about as various customers and media outlets took notice of the rather lengthy Terms and Services that pop up once you strap yourself into the Rift headset.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

With the bombardment of technical issues that have plagued GTA Online since its inauguration, it hasn't been easy to enjoy stealing cars and killing hookers with all your friends.
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

Economists have long since known that people want to be rewarded for taking on risk. Investments are thus judged by their risk-adjusted returns (Sharpe ratios). A typical hedge fund has a Sharpe ratio of around 0.5. This means that its excess annual return over the risk-free rate is about half its annual standard deviation.

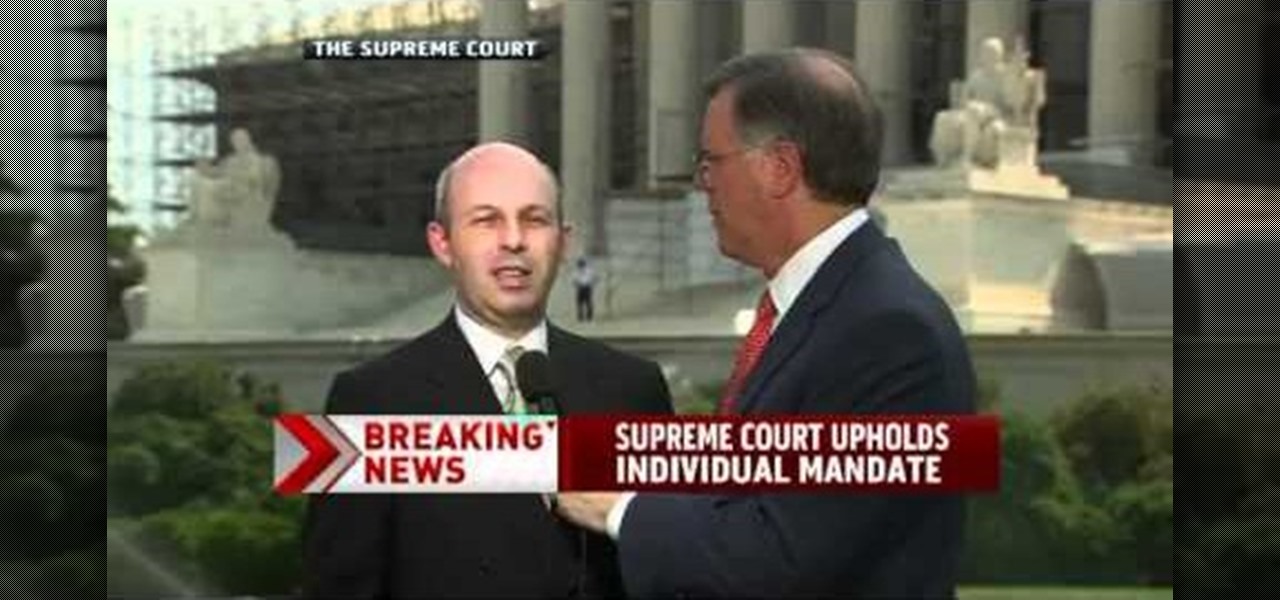
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

Ever wondered how to make slime? Now you can learn! Make slime just like they use on Nickelodeon for Halloween, pranks, or just to play with! So gather up your ingredients and get cookin'!

July and August are blackberry picking months. Gather up some fresh blackberries and bake yourself a homemade blackberry pie. Once you make this delicious dessert people will be volunteering to help pick the blackberries themselves.

Too busy for omelets in the morning? In this how to video the chef shows you a remarkable technique for fluffy and cheesy frittata.

What's pavlova? Well if you don't know what it is, watch this how to video to learn what it is and how to make it. Gather your sugar, corn starch, and whipping cream for this delicious sweet dessert. Decorate you pavlova with chocolate swirls.

Are you a new parent? Changing a diaper can look a bit complicated- see an experienced mom demonstrate the simple steps required so you'll be an expert in no time. First things first, gather all the items that you need: a diaper, any ointments or creams that your doctor may have recommended, wipes or soft towels a large towel or changing pad and some of you might want to use a changing table if that is your choice.

This video tutorial shows you how to wallpaper. 1. Set the mood: To wallpaper a room you need caffeine and music, it's best to get that first. 2. Prepare the space: Basically this step is set to gathering tools, patching holes, cleaning and sanding the walls, moving furniture and removing outlet and switch face plates. The tools are as follows: level, pencil, tape measure, step stool, wallpaper paste, paint tray, paint rollers and brushes, wall paper, squeegee, water bucket, sponge. utility k...

This makeup palette is the Forest Fairy Sprite Wood Nymph created by MissChievious. Begin with regular foundation. Get a little dark gold and golden cream eyeshadow with a knife & mix it into foundation. Take a large makeup blush type brush & put green shadow around top & sides of forehead blending it up into hairline & around the sides of face, continuing slightly onto the cheek hollows as you might do a light contouring. Take golden cream & dark gold & mix them before applying to center of ...

Learn how to practice proper etiquette on a BlackBerry, smartphone or PDA. Make sure your love for your BlackBerry or other PDA device isn't making you obnoxious.

Learn how to drop in on a quarter-pipe. Dropping in on a quarter-pipe or other vertical ramp is something to try after you have been skateboarding for at least a few months.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

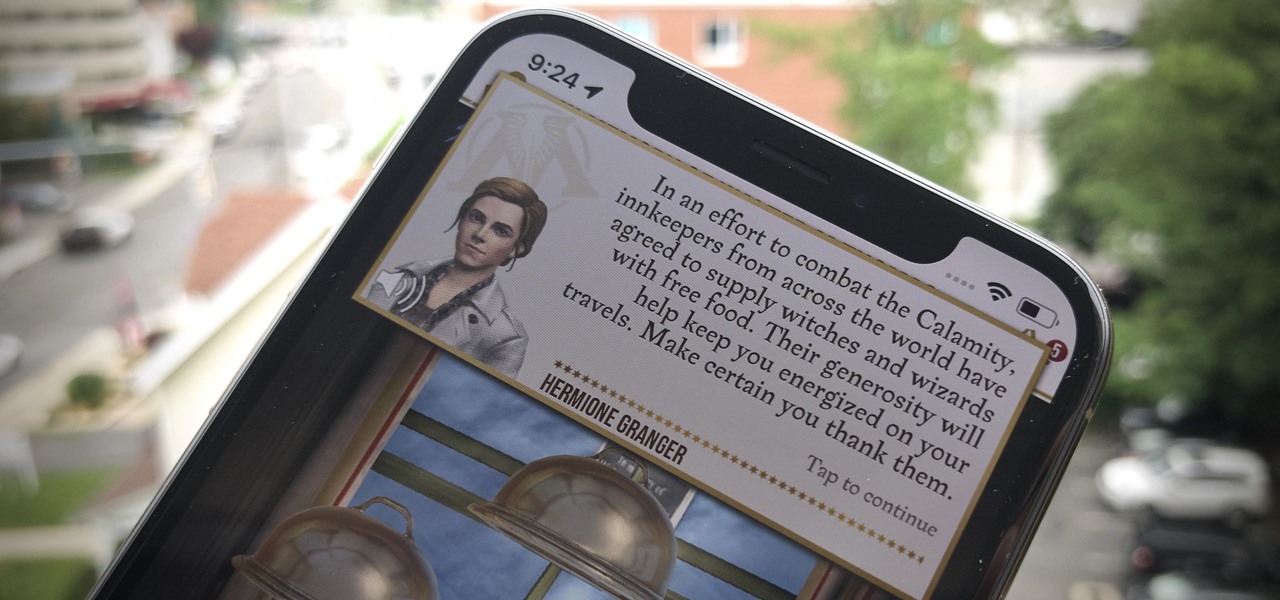
We Harry Potter fans all remember Hogwarts students pulling Mandrake Roots in the greenhouses in Chamber of Secrets. Well, in Harry Potter: Wizards Unite, we now have an opportunity to work in our own Greenhouses, as well as dine inside Inns scattered throughout the map. Let's take a look at how these two establishments help you along your magical AR journey.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Maybe you are looking for a fun, festive, decoration for your next party or gathering, or maybe you've got a room full of balloons and you don't know what to do with them. Well, this video has answers. This video will show you how to make a balloon arch.

This how to video tutorial demonstrates how to sew a straight stitch by hand, just in case you don't have a sewing machine. The straight stitch is excellent for simple hems, decorative stitching and gathering fabric.

Knowing all the information about your car is important for many reasons. Some being for the fact that the government needs it and another being it can help with trying to find parts for the car. So in this very helpful tutorial, you'll find out how to locate the VIN ID numbers on a classic VW Beetle Bug. It's easy to follow and will make life easier for you. So good luck and enjoy!

Though Microsoft has had trouble keeping up with the demand for HoloLens 2, the company has been able to supply modified headsets to the US Army.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Augmented reality seems to come into its own in museums, where audiences are ready and willing to try out new immersive tech. Now, that tech-powered palette is about to get a little larger.

The Pixel 3 has an indisputably great camera, but a software update coming soon is going to make it even better. Google will be adding a "Night Sight" shooting mode that's so good with low-light situations that you'll have to see it to believe it.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

You want whales? Ok, you'll get whales! That seems to be the unspoken message from Magic Leap via its latest update in the form of several new experiments posted inside its Helio app.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Hearthstone, Blizzard's online card game, combines strategy with a fun spin on the World of Warcraft lore to create a unique experience. With the latest expansion (The Witchwood) on the horizon, you'll want to make sure your collection is ready for when the set drops in April. Fortunately, you can get free packs on iPhone or Android to help prepare.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Last week, Magic Leap CEO Rony Abovitz teased his Twitter followers with some "fun and cool stuff" to share in the coming days. On Monday, he made good on that promise, sort of.