After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder.

The auto industry continues to shift into high gear to lay the groundwork for driverless cars with an electric vehicle (EV) emphasis.

The company that brought us a BB-8 droid controlled with the Force — okay, just a high-tech wristband — is releasing its take on Spider-Man. Toymaker Sphero collaborated with Marvel to release an app-enabled Spider-Man toy equipped with numerous features, as well as games for your smartphone.

Uber and Waymo's lawsuit is starting to pan out. Following a ruling on Monday, May 15, Judge Alsup, who called Waymo's patent infringement claims "meritless," ordered Uber to perform a series of actions and duties for Waymo. Without further ado, here's what Uber must do to begin to put this lawsuit behind them (well, maybe):

Snapchat is attempting to take over the world via augmented reality technology. Well, it's more of a virtual makeover than a takeover, but still ...

Intel launched their Advanced Vehicle Lab in Silicon Valley this week, and the tech giant is now on the hunt for potential partners.

It be would the ideal morning commute—sit back, drink some coffee, and read the news as your car drives you to your destination. That reality isn't quite here yet, but Cadillac is offering something close with "Super Cruise" on the CT6.

Blizzard's Hearthstone was a rousing success with more than 10 million downloads on the Google Play Store. Not taking things lying down, Bethesda, the creator of The Elder Scrolls, has come up with a card game based off its popular fantasy franchise. The Elder Scrolls: Legends is now out in the wild, though, officially only available for select Android tablets. But with a little creativity, there's a way to game the system and play Legends on any Android device. The Elder Scrolls: Legends is ...

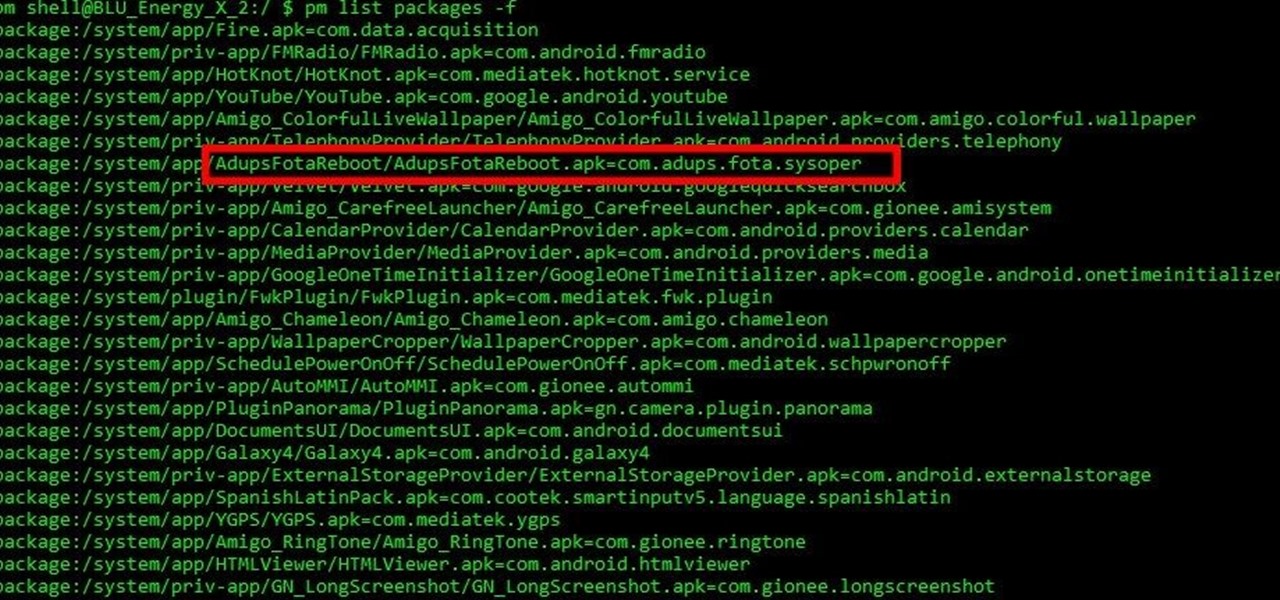
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

In Italian, the word affogato means "drowned." Kind of a morbid name for such a delicious goodie, right? But there's a reason it's called that.

We love a refreshing glass of wine in the summertime, but who doesn't, right? More often than not, we favor a rosé or a light red, depending upon the meal, but when the sun is setting and the evenings are warm, chilled wine is the way to go.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

I recently had a small gathering of friends over for a quick cookout consisting of mostly burgers on the grill. One of my friends informed me beforehand that she didn't eat red meat, but that she would be perfectly okay with eating a turkey burger.

Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and rapid-fire gesture typing comprise a hard combination to beat.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

A simply frosted or glazed cupcake is like a blank canvas for creative decorations. Intricate cupcakes are works of art, but piping frosting or rolling fondant can be tricky. Luckily, even the most craft-challenged person can use pre-made decorations to create party-worthy cupcakes. Use chocolates or candies to make designs or other decorations and you can have endless fun (and very little stress) creating eye-catching treats.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Meet the Wonderbag. The "first non-electric slow cooker" uses an insulated bag made of poly-cotton fabric, polyester, and repurposed foam chips. You bring your one-pot meal to the desired cooking temperature, usually via the stovetop. Then you turn off the heat, pop the pot into the Wonderbag, and it will continue to cook thanks to the retained heat in the bag.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Brought to you by Brother International Corporation. Whether you are looking to complete a home improvement task, or you are hoping to start a new hobby, staying focused and energized during projects can be daunting. With emphasis on organization, planning, and creativity, we gathered together tips that will help you successfully tackle any project on your plate!

Surely you're aware of the Sony hacking scandal by now (here's a quick primer if you're not), as well as the multi-billion dollar company initially bowing to threats by canceling the Christmas release of the The Interview, the film at the center of the whole debacle.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

Even the best-maintained kitchens occasionally get a fruit fly infestation. These critters descend, lay eggs (up to 500 at a time!), and then disappear usually only after extreme cleaning efforts (i.e., finally attacking that weird puddle of goo behind your refrigerator).

Every now and then, you'll bite into the end piece of a perfectly good cucumber only to get an unwelcome bitter and acrid taste. This happened to me for years, no matter how carefully I selected my cukes, although I generally had better luck with ones I got from local growers and the farmer's market.

There's nothing better than gathering up all the cushions, pillows, and blankets in your home and having a good ol' fashion movie night. But if you're still rocking the old 19-inch TV your parents gave you in college, you may want to upgrade to something bigger.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

So you've decided to transform your drab backyard into a Japanese Zen garden. You've made the right choice. Yes, tire swings and crab grass can slowly kill the soul. That being said, a bit of planning lies ahead. This article offers a list of How To tips, culled from the Landscape Network and other professional Japanese style landscapers, for planning an effective Japanese style landscape in your home. Step 1: Research.

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

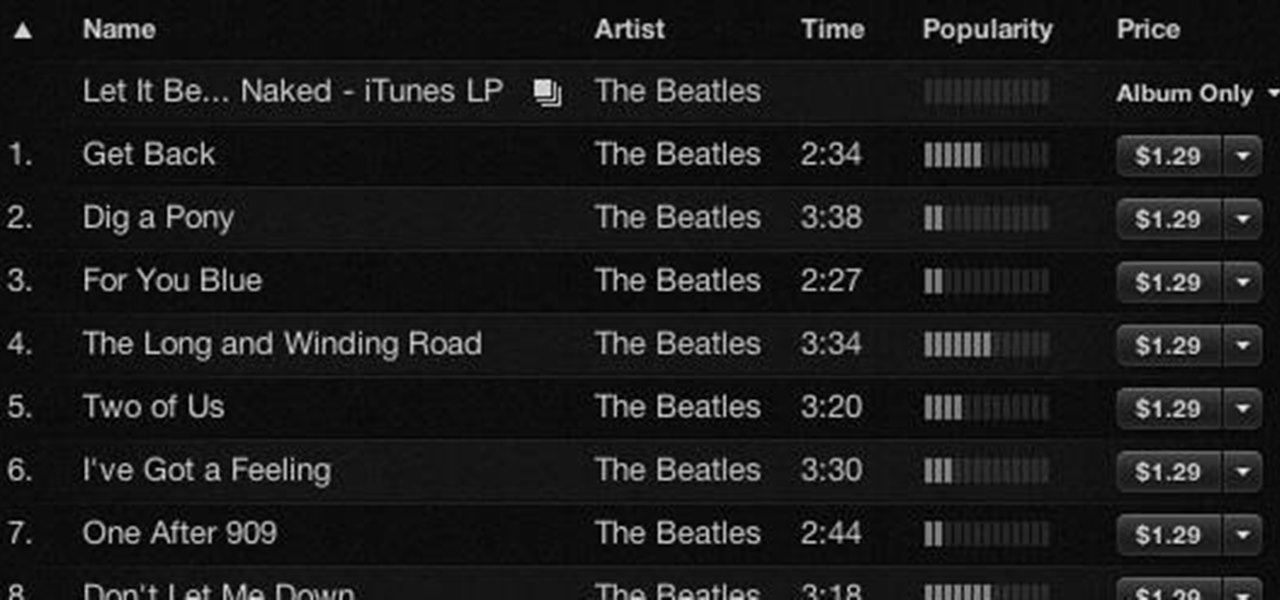
If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.