
News: Anthrax Outbreak in Tanzania Brings a Dangerous Bioterror Threat Back to the World Stage
An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.


An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

China just confirmed a sixth avian flu outbreak since October. On Tuesday, the Ministry of Agriculture stated that there had been another instance of bird flu in the Hubei province, of the H5N6 influenza virus. The outbreak occurred in the city of Daye, which is home to some 900,000 people, but hasn't been linked to human infections yet.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.
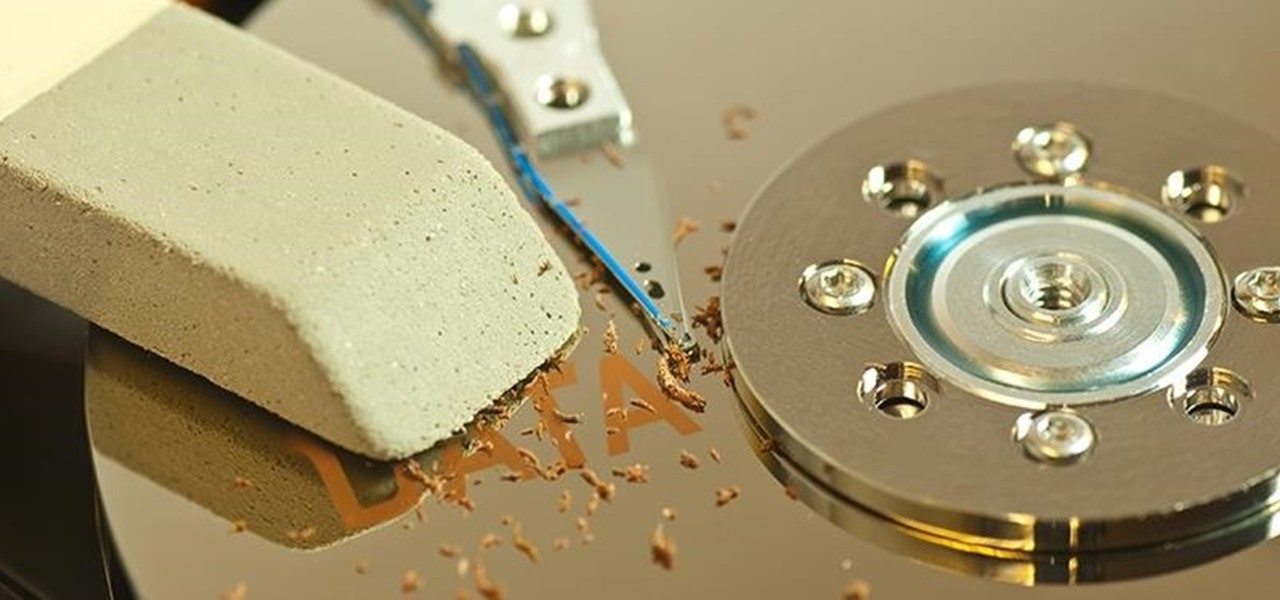
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

It's time for another mobile prank. The classic pranks and practical jokes are always great, but let's hit your friends where it really hurts—their precious (and expensive) smartphones. And what better way to scare the shit out of them than making them believe their phone's been infected by malware?

Update: August 1, 2014 Earlier today, President Obama signed into law the Unlocking Consumer Choice and Wireless Competition Act, making the act of unlocking your unsubsidized cell phone 100% legal.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

With this article, I'll be continuing the series I started with my recent plague doctor article. That is, examining tropes that may at first appear to not fit into Steampunk.

With presidential voting going down on Tuesday, November 6th, voters are beginning to anchor down on their choice for president. But with the way the media works, this may be difficult for some people because the news sites they listen to give conflicting and sporadic information on the candidates.

As Hurricane Sandy barrels towards the East Coast, 50 million people are expected to be affected in the nation's most populated corridor. The behemoth super storm is a cause for concern, evident by the massive evacuations. The picture above is an eerie snap of the mostly crowded Times Square subway station in New York. Government officials have warned over half a million people to evacuate their homes and head to higher grounds. To help prepare for this storm, the internet has provided severa...

I'm sure a lot of people have been following the news and depending on your position on the issue, you might have been happy or dissappointed about the fact that Obamacare has been OK'd by Congress. Let's see what this really means to us.

Want to start a fire? Make arrows for your bow? Not sure where flint is in Minecraft? It's actually right in your inventory already, you just haven't been looking hard enough! In this video you will learn how to create flint by laying gravel and destroying it multiple times until it yields flint. Repeat the process until all your gravel is gone and you're all set!

In this tutorial, we learn how to make cotton candy with a cotton candy machine. First, you will want to take your choice of flavored sugar and pour it into the top of the cotton candy machine. Next, you will take your paper cone for cotton candy and place it in your hand. Turn on the machine on and when it's heated up and sprays out sugar strings, move your hand quickly around the machine and gather the cotton candy up with the cone! You can enjoy as soon as it's done and layer different fla...

Ever wonder how to make futomaki sushi and California rolls? Cut ingredients for filling. Remove both ends of cucumber. Make 6 cucumber sticks. Cut avocado in ½, twist, remove seed. Remove peel. Slice into thin pieces. Cut shiitake mushrooms into fine strips. Cut barbequed eel lengthwise. Using 2 eggs seasoned with salt and sugar, make egg omelet. Heat pan; add a little oil. Pour 1/3 egg mixture into the pan and when almost cooked gather on far end of the pan. Re-oil pan. Add 1/3 mixture of e...

Check out this supernatural tutorial video that offers 7 tips on getting started in becoming a paranormal investigator. Just follow these simple steps:

Watch this how to video as Jennifer Thoden takes you through every step of installing a bead chain system for your Roman shades or balloon shades. Gather your supplies and learn how to assemble the clutch and thread the unit. Keep your windows from looking bare with a Roman shade bead chain system.

To become a Victoria's Secret model, use the Internet to locate agency Web sites and register photos on-line to be viewed by modeling agencies. Build a portfolio and gather head shots for becoming a Victoria's Secret model with tips from a modeling instructor in this free how to video on modeling.

Artificial flowers are a wonderful way to add joy and color to your home without the cost or mess of freshly cut flowers. They don’t need to be watered but they can get dusty. Keep your artificial flowers shining brightly with this simple trick.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.