When you were unboxing your Galaxy Note7, you probably wondered why a little metal claw tool was included in the packaging. Then, if you looked closer, you saw there were five plastic sticks included with the claw tool that came in two different colors.

Pickles are insanely versatile: we eat them on their own as a snack, as a tasty zing on burgers, and some of us even like them in a sandwich with peanut butter. And if you're already an avid reader of our site, you'd know that we're even crazier about pickle juice and its myriad uses.

From fungi to foie gras, the weird ingredient cocktail game across the nation is growing by leaps and bounds. We had our hesitations about trying some of them out, and especially about attempting to make any ourselves, so we did a bit more research and realized the flavor profiles aren't as unfathomable as one may think.
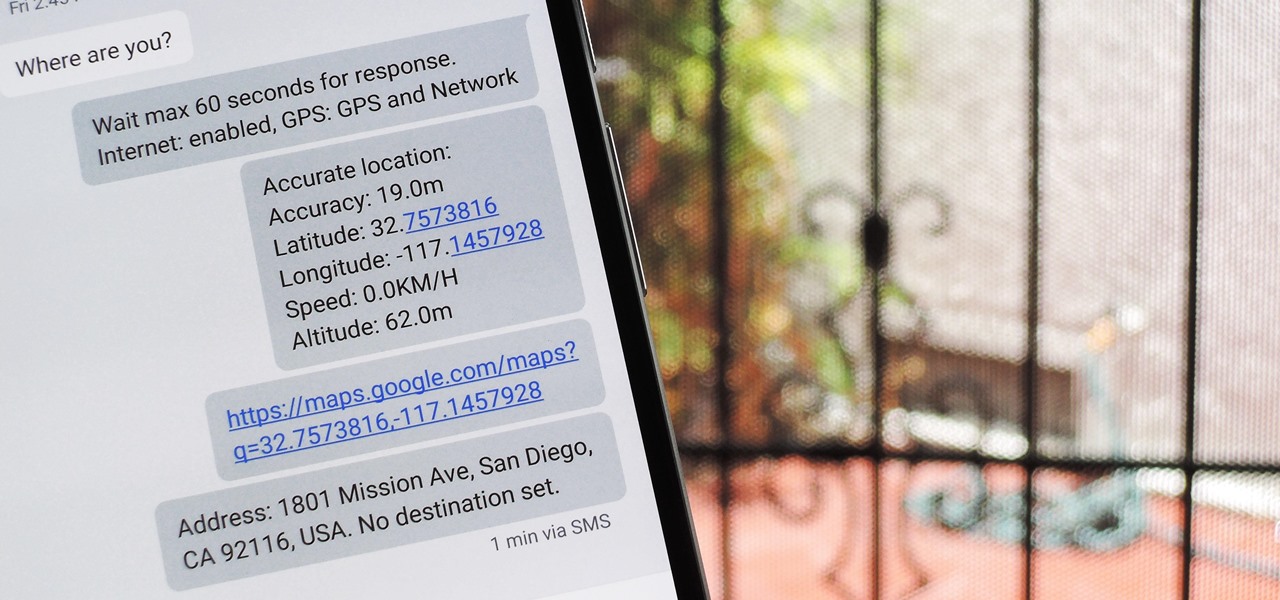
When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.

The cool tang and citrusy taste of a margarita in the summer is refreshing, to say the least. But when making margaritas at home, many of us opt for the ease of store-bought mix when it's actually really simple to make it instead.
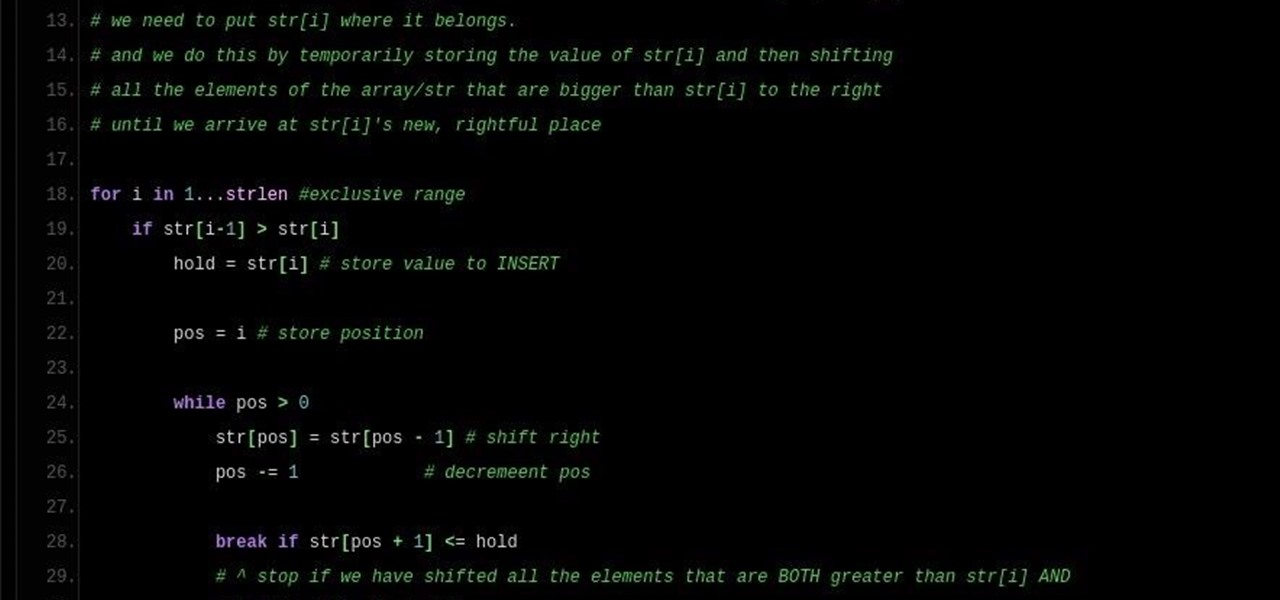
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

So, how does someone keep their hacking life completely secret? What This Is:

Winter—or any cold, gray day, for that matter—is the best time for a warm cup of something hot. For me, hot chocolate is my "warm cup" of choice: rich and milky, deliciously sweet, and oh-so-comforting. On super-cold days when I can't feel my face, a nice, large cup of hot chocolate warms my tummy and cheers me up. (And lucky for me, it's pretty healthy for me too!)

I'll bet this scenario will sound familiar to you: you're in the middle of making a spectacular dessert that will knock the socks off of your guests, and you've almost finished gathering all of your ingredients to create your mise en place. The last ingredient listed is powdered sugar, and you reach for where it's stored, when—drat! You don't have enough for the recipe.

There are few things that make me smile more than ice cream… or bread! So why not combine them for double the happiness? We've discussed the art of making ice cream bread before, but not everyone has the time (or, let's face it—the patience) to bake bread in the oven, no matter how few ingredients the recipe may take.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

Oatmeal isn't the most glamorous breakfast, but it's definitely one of the best. It's healthy, filling, delicious, and easy to personalize. And, if you have instant packets, oatmeal is also a very quick and easy breakfast.

Tomatoes are the perfect barometer for kitchen knives and knife skills. If you've ever watched an infomercial for a set of knives, you've surely seen the enthusiastic host waxing about how well the knives cut tomatoes. And if you've ever had your knives sharpened, you've most likely tested them out on a tomato.

For 365 days of the year, our mothers show their love for us by driving us places, cooking us food, doing our laundry, and being our number-one cheerleader. But for one day of the year, we all get up early in the morning and show our love for our favorite women. Often, that means cooking breakfast or making brunch, or running to the store to grab a pre-selected bouquet of flowers.

If you've never heard of or eaten temari sushi, then you're in for a treat. These pretty sushi balls are good for parties and festive gatherings, and even though they are so colorful and striking, they are not hard to make. Just like every other type of sushi, they are customizable, and they have the cute factor necessary for kids or appetizers.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

A salad can mean everything from fruit to meat and everything in-between, but it never means finger food. Forks are required. So that means that even though salads are versatile, delicious, and customizable, they are hell at cocktail parties. How do you hold your glass and take a bite of your salad at the same time? It's awkward.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

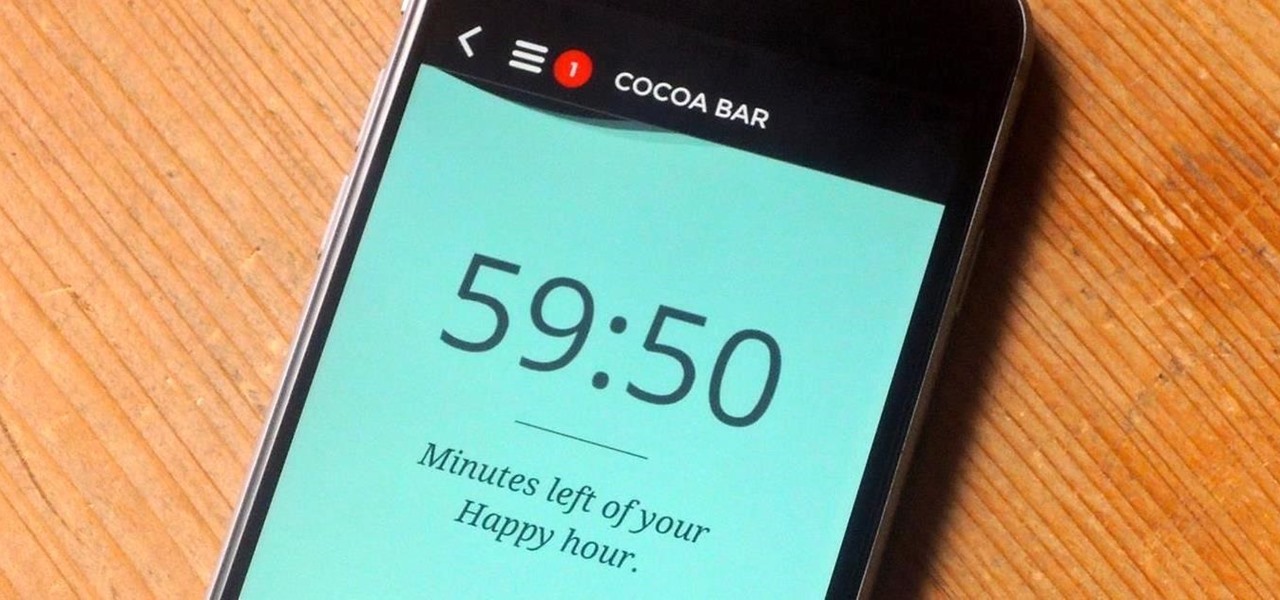
Happy hour is a great way to wind down after a long day at work or school, to relax with friends and enjoy a well-deserved drink. While the experience of this on-the-cheap imbibing promotion is great, the hours usually aren't.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

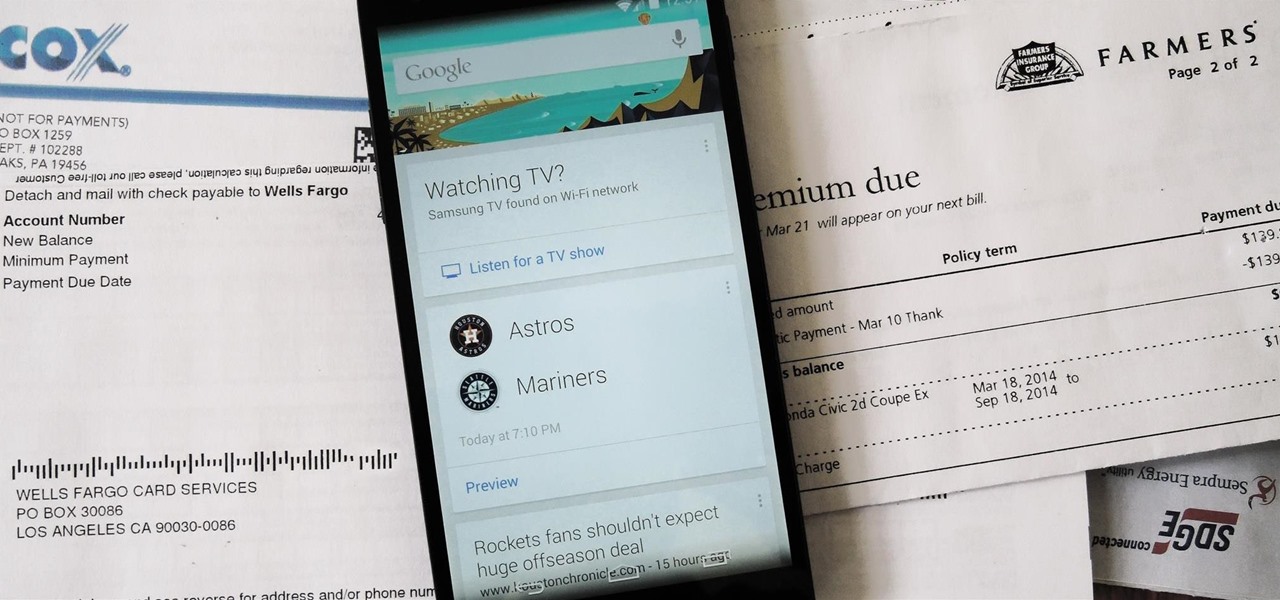
Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...

Welcome back, my greenhorn hackers!

Mobile scanning applications are nothing new in the world of Apple, except that the majority of them usually come with pesky in-app purchases that stifle the entire experience and render some features useless until you pay for them.

Microwave popcorn promises so much—a tasty, relatively healthy snack that's ready in minutes—yet it rarely delivers. Most of the time you'll end up with a scorched bagful or a bunch of stubborn un-popped kernels, but it doesn't have to be that way. With a few simple tricks, it's easy to get perfectly fluffy, tender-crisp popcorn every time.

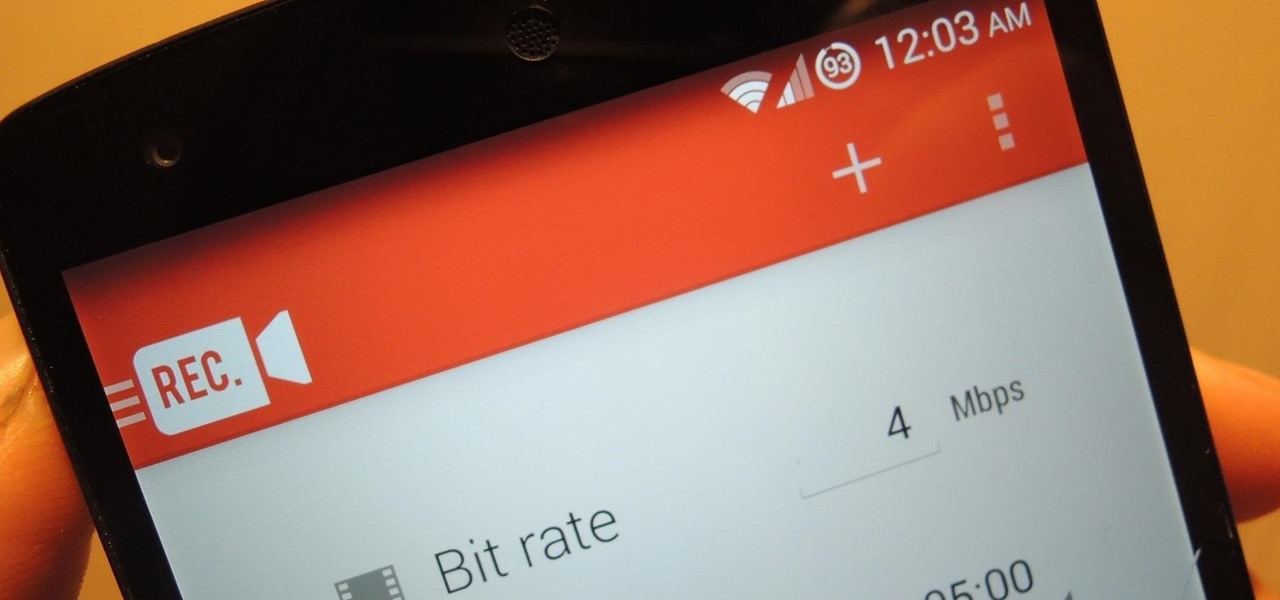
Not too long ago, we told you about a new feature within Android KitKat that allowed for video recording directly from the screen of your Nexus 5. Though functional, the method was a bit clunky and involved hooking your phone up to your computer and sending over an ADB command to start the recording.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

It's a done deal. KitKat is the shit, and everyone wants in on it. Unfortunately, the Samsung Galaxy S3 won't see any of Android 4.4's features incorporated into TouchWiz for some time, as we're still on a 4.1 version. Still, we can throw a few of KitKat's features onto the device ourselves, like the home launcher and new keyboard. And now, we can even get a feel for its smarter phone app.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.