Over the past few years, indie game developers have gathered together to release their products in the widely popular Humble Indie Bundle, a collection that gamers can purchase for whatever price they want. It's a win-win for both. Developers get more exposure for their games, and customers get tons of games for whatever they could afford. Heck, charities even get a little piece of the pie.

There's no shortage of ice cream recipes out there, but one ice cream shop in London has found a unique recipe to sell to its customers, and of course it's controversial—breast milk ice cream.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.
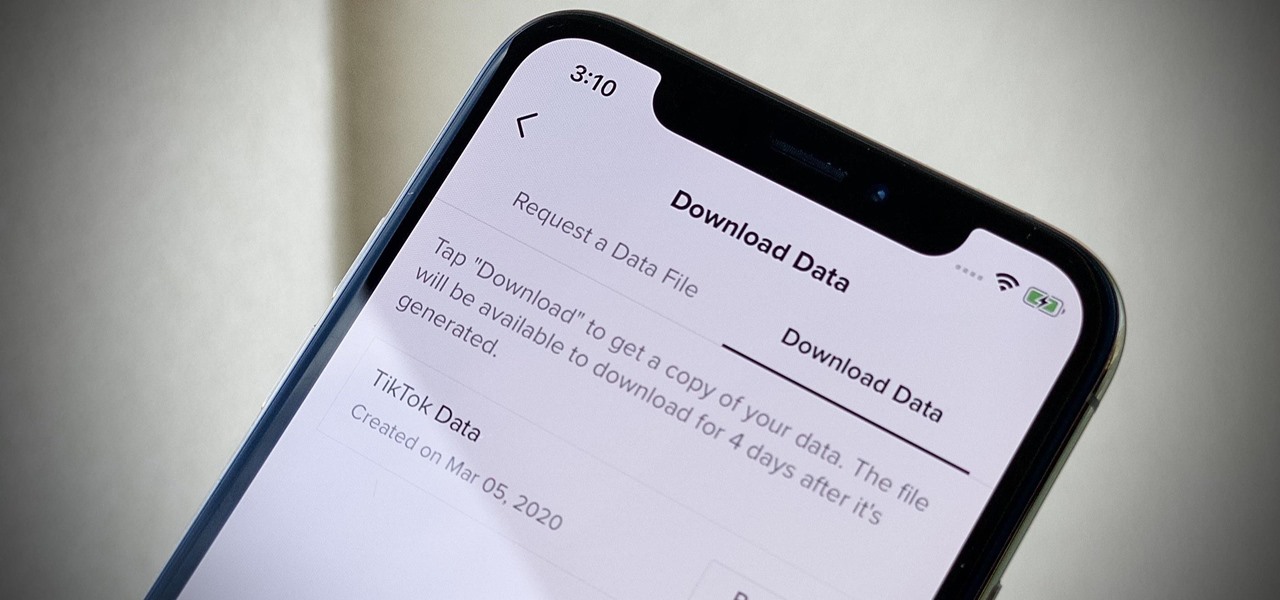
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

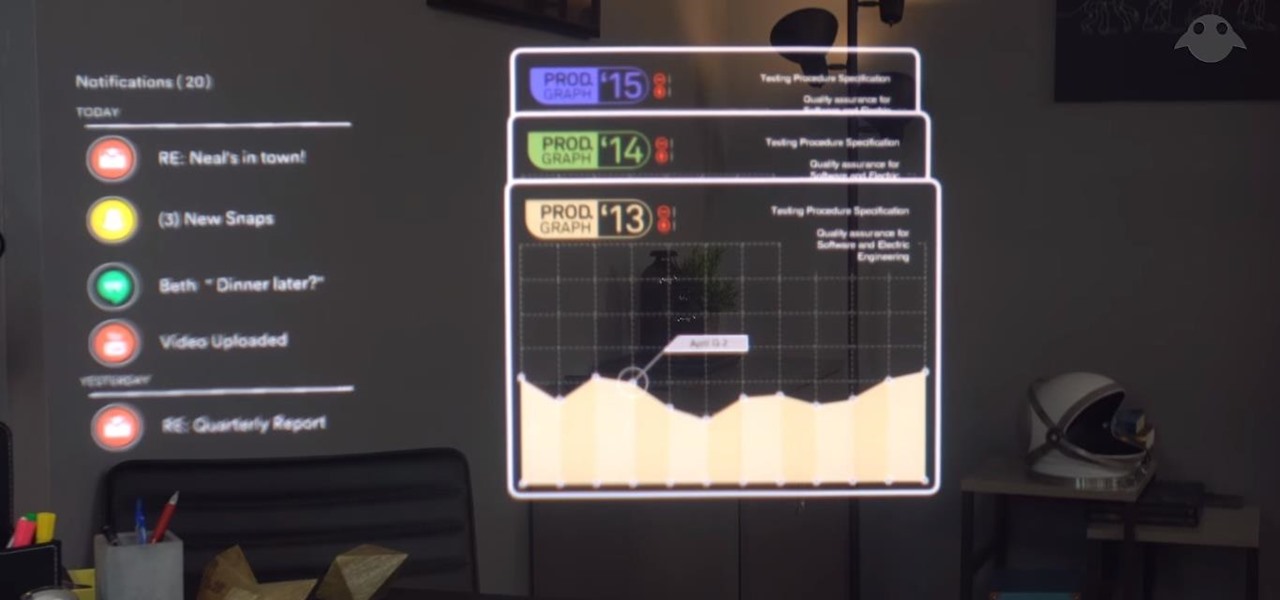
Despite funding difficulties that forced Meta to place employees on temporary leave in September, the augmented reality headset maker is reminding enterprise companies that it remains a viable option for visualizing and working with 3D design models.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

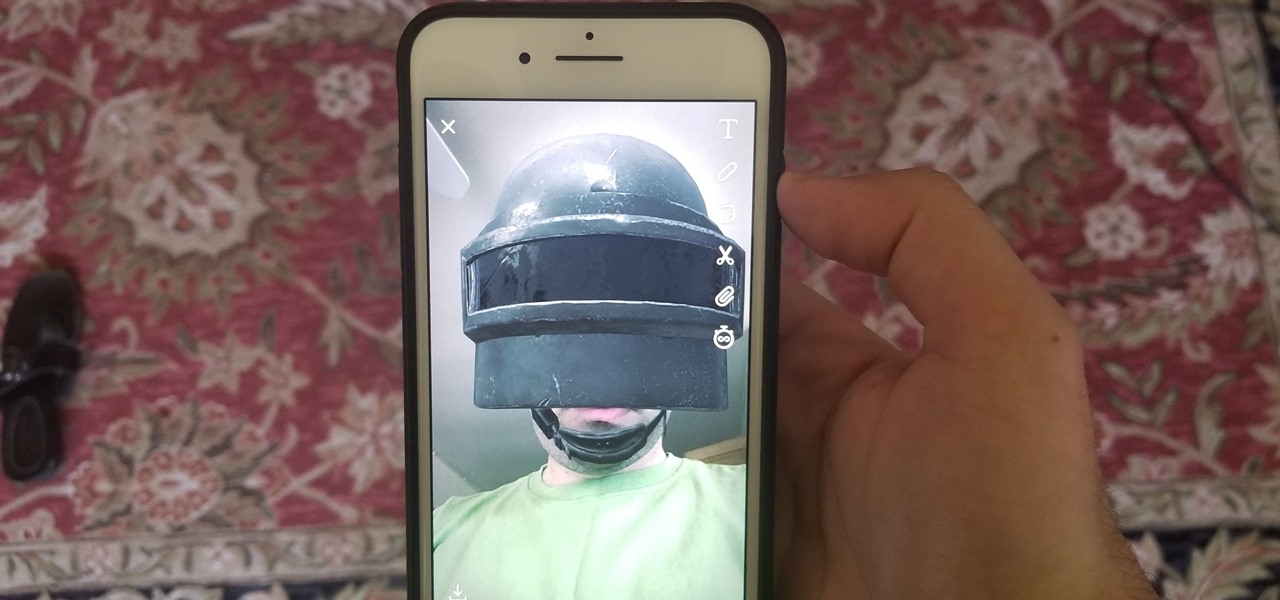
Spring is finally here (in earnest now), and a new batch of great augmented reality Snapchat lenses have come along with it. New life has been breathed into meme culture with the spring lineup of TV shows, Mark Zuckerberg's ongoing investigation, and college kids with too much time on their hands.

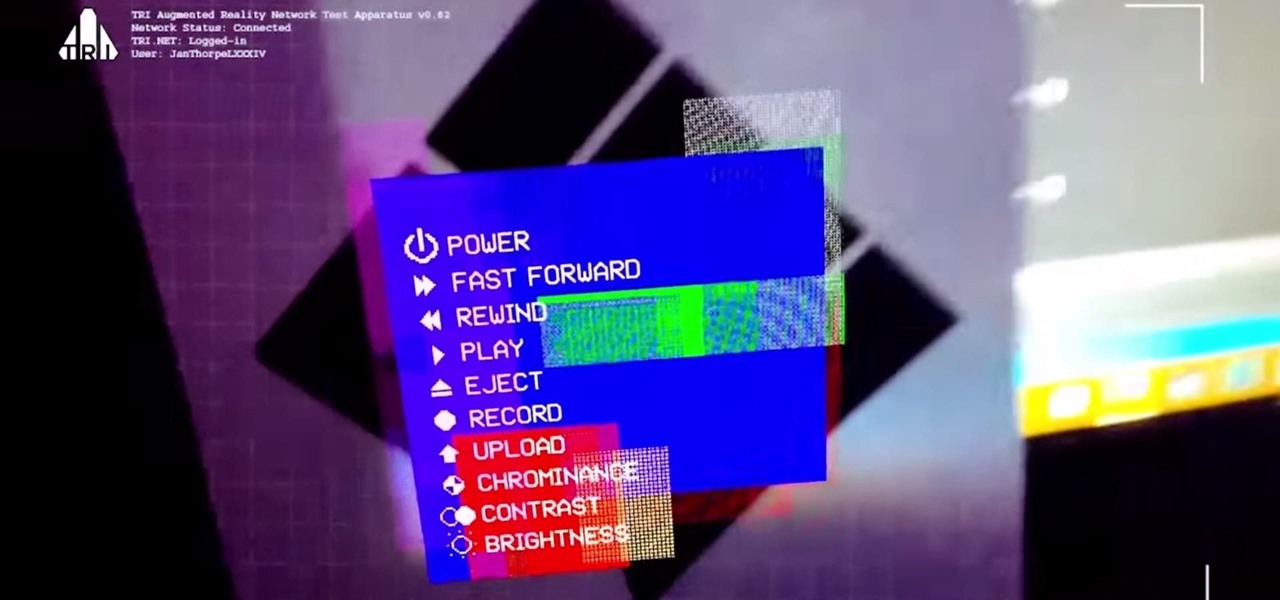
The augmented reality business was all about audiences this week. Vuzix looked for an audience with the Supreme Court of New York regarding a defamation lawsuit against an investor. Magic Leap held an audience with royalty, showing off the Magic Leap One in a rare public appearance. And Snapchat wanted to remind its consumer audience of all the things its camera can do.

It turns out that the government of Saudi Arabia has managed to do something last month's Game Developers Conference couldn't — give us a few new glimpses of the Magic Leap One being worn by someone other than Shaq.

Huawei's push into the US market has by no means stopped, even despite the recent US government pushback. Huawei has already released their top-notch flagship device from 2017, the Mate 10 Pro, and a couple great budget and midrange devices. Their latest release offers an upgrade to a past release.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.

Anyone who knows me well is aware that I am a cyberpunk junkie. The conflict between lowlifes, corporations, and the government, flavored with dystopian future, high technology, transhumanism, artificial intelligence, and noir storytelling, just does something for me.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

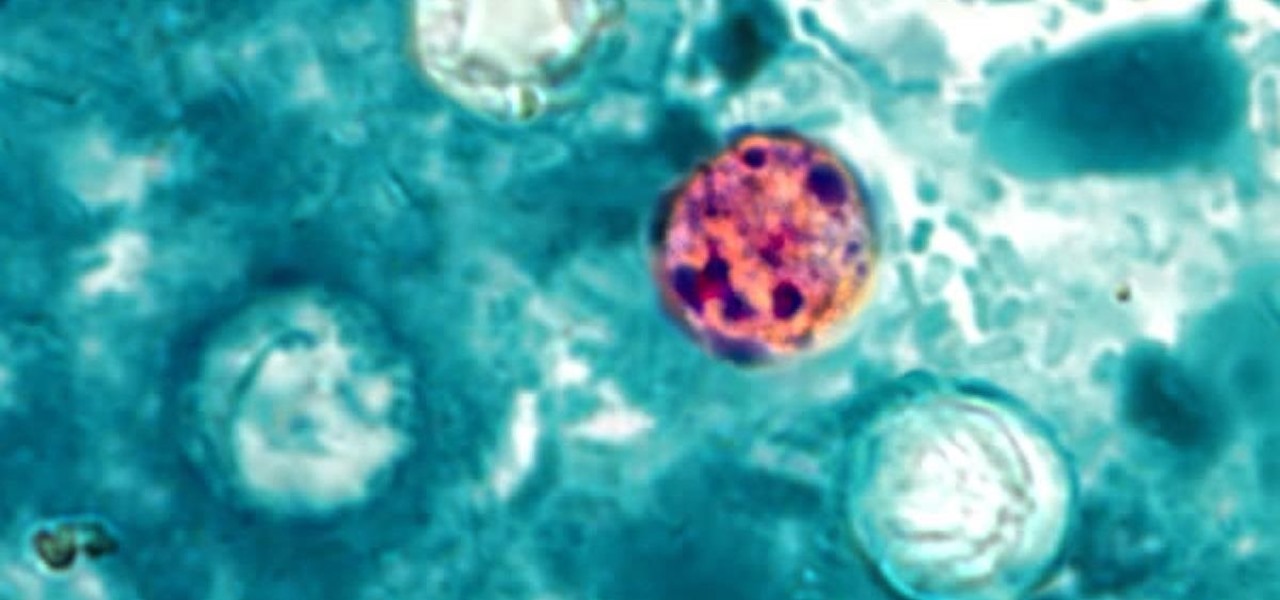
The intestinal parasite Cyclospora cayetanensis has a dramatically increased infection rate this summer, and the source is still unknown, the CDC advised today. 2017 is a good year for Cyclospora looking for homes to start their families and a bad year for those of us who don't like food-stealing tenants living in our bodies.

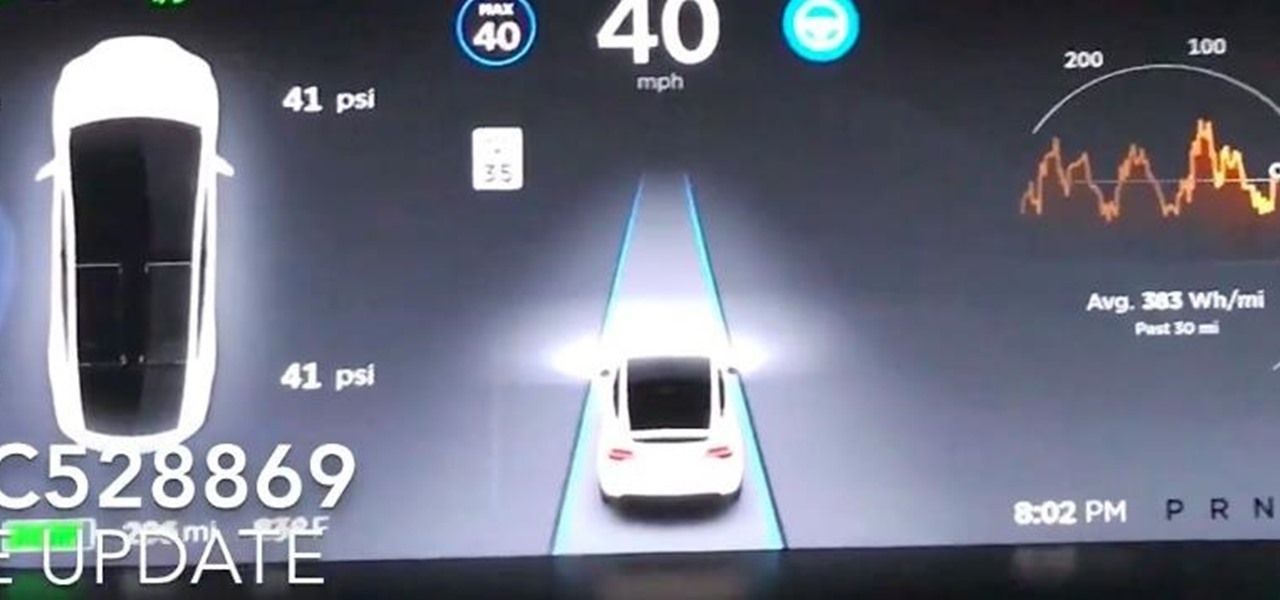
Some drivers give Tesla's Autopilot update released this week rave reviews, after version 8.1 has taken longer than expected to live up to Elon Musk's "smooth as silk" Tweet from earlier this year.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

In this Tuesday's Brief Reality report, there's a trio of stories from the healthcare world where augmented reality is helping out with surgical microscopes, asthma treatment, and other diagnostic and treatment tools. There's also something for all of you AR/VR storytellers out there.

Uber wants you to forget about cars and start thinking about fully autonomous flying as an alternative—a more "economically favorable" way of getting to your grinding nine-to-five.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Welcome back, my rookie hackers!

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.