As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

Is "Last Resort" Steampunk? Well, no. I mean, how could it be?

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

To wear a sari takes only the ability to properly fold and wrap the yards of often brightly colored and flowing fabric. With just a pin at the shoulder you can replicate the technique for this traditional Indian garb.

Freezing is a great way to preserve the nutrients and lengthen shelf-life of food. No need to waste extra apples from the fall. Freeze your apples to be used in a variety of ways at the date of your choosing.

Keep the kids learning and entertained with this fun pinwheel project. Summer is a great time for family activities, and these Fourth of July pinwheels are a math lesson, craft project and decoration-making session all-in-one.

This video shows you how to turn a 5" crochet headband into a beanie hat. #1 Gather your supplies-embroidery floss, 5 1/2" crochet headband, needle and scissors.

Evony is so slow sometimes, so why not speed it up a bit? Speed hack it! In order to do that, you need Cheat Engine.

If you are having a small issue with someone or are having trouble recovering money from somewhere, you may want to consider filing a lawsuit. Filing in small claims court is complicated, but with this tutorial, you will be on your way to understanding the steps a bit better.

Depending on where you live, you will have to prepare for the hazards from different types of natural disasters. You can sleep easy if you have a secure location, stalked with food and supplied you might need if there is an emergency.

Head shrinking is not only a thing of legends. Make your own cute, shrunken apple heads to add to the spirit of the season. Gather the family and get creative, carving whatever kind of face you would like on a legion of little apple heads.

Here is a take on a cheap but very romantic valentines gift that your loved ones would truly enjoy. Here's how to make your perfect chocolate dipped strawberries. Gather the ingredients that you'll be needing: a batch of chocolate chips (dark and white chocolate) and 16 oz strawberries. Prepare also the following cooking utensils: 1 pot and 2 heat proof bowls along with a laid out foil or wax paper (whichever is available to you). Start by cleaning and rinsing strawberries along with their st...

Gather your hoop and supplies. Wrap the suede evenly around the entire ring. Wrap it either eight or sixteen times, depending upon your preference. Glue the ends to the hoop. Secure them with a clothespin until the glue dries. Make the web. Tie the nylon string to the suede. Make eight knots evenly dispersed around the ring. Keep the thread taunt between knots. Make a second row. Place each knot "between" the knots of the previous row. Continue in this manner until a small hole remains in the...

In this video series, watch as Matt Cail teaches how to decorate for the Thanksgiving holidays. Learn how to use paper, balloons, pumpkins, plates, knick knacks, streamers, candles, and art to make your Thanksgiving a festive and beautiful gathering that will be remembered even after the world comes to an end and life as we know it has ceased to exist and cannot be found even in the collective memories of the fading atoms and molecules that use to comprise this cold, dark world.

The season for outdoor activities and indoor heavy cleaning has arrived, and with that comes all the aches and pains of enjoying it. If you find yourself with sore muscles and no easy way to fix it, then a portable massager you can use whenever you're in pain is something that could put the spring back in your step.

Becoming a competitive candidate in IT and Data Science takes more than knowing a few coding languages and being good with computers. To really stand out from the crowd, your knowledge should be extensive and your experience should be diverse. The 2021 Complete Computer Science Training Bundle provides that depth of knowledge and a starting point for gathering that experience. Right now, it's on sale for just $39.99.

Between all the streaming services you have to contend with, it's hard to want to go through the trouble of plugging in an adapter and loading up a DVD when you could find another movie without needing to move.

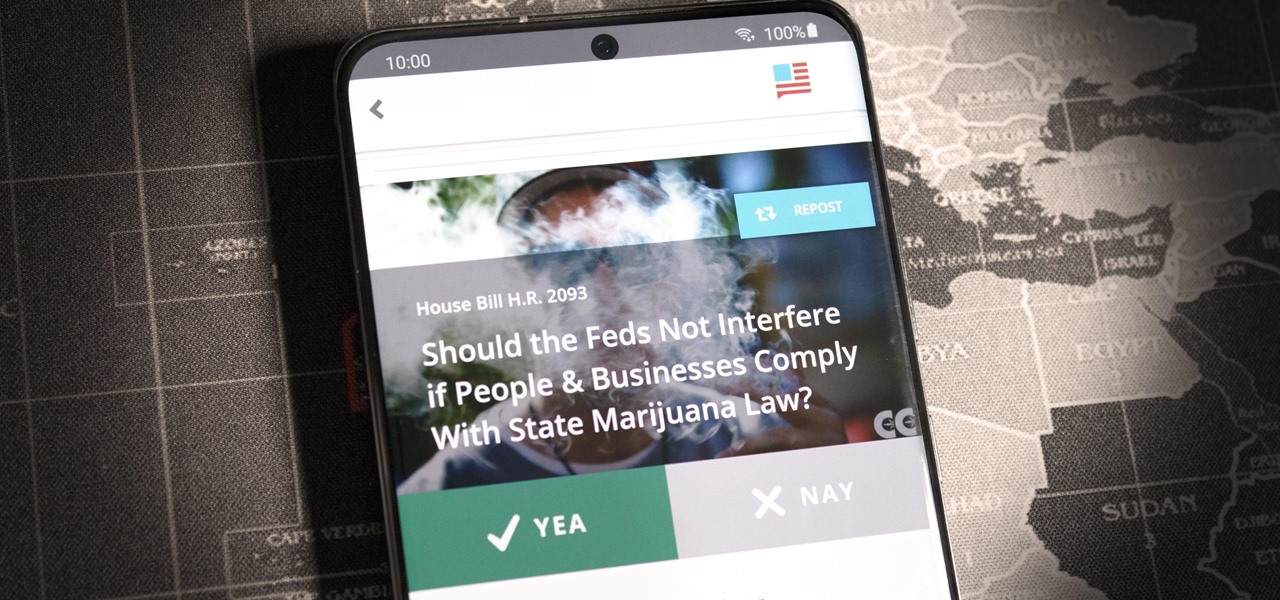
If you live in the US, it's your civic duty to understand our governing bodies and the political system that puts them in place. It doesn't matter what your age is, knowing who to vote for is as important as voting at all. That starts with policing your own representatives to help decide whether or not we should re-elect them.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

This week's Apple earnings offered a report of solid performance and guarded optimism about future iPhone sales, which may be impacted later this year by issues around the current coronavirus epidemic in China.

It seems like all tech companies want to know where we are. Even Apple and Google have been caught abusing their location access on iOS and Android. Luckily, there are apps that can trick your phone into thinking it's somewhere it's not.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Move over, Star Wars. You're not the only Disney property that can play in the Lenovo Mirage AR headset anymore.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

As the Augmented World Expo (AWE) prepares to open its doors to AR developers and enthusiasts, we sat down with founder Ori Inbar to talk about AR's growth over the past decade, and what the future may hold.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

There are a lot of things that make iOS great, but lock screen widgets are not among them. If you want more information on your lock screen other than the date, time, and notifications without having to swipe to a sidebar of widgets, you'd normally look toward Android. However, iOS 12 aims to shake that up a bit with a secret Weather widget for the lock screen — not for the Today view.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.