In order to make manganese dioxide electrodes, you're going to need cobalt nitrate and manganese nitrate to do it. Making cobalt nitrate is fairly easy, but making the manganese nitrate is a little more complicated. But not impossible.

What is MnSO4 and MNO2, anyway? They are they molecular formula for Manganese Sulfate and Manganese Dioxide. And you can make one from the other. But how?

Want to know about Newton's three laws of motion and how they affect aircraft landings? NASA has answers. NASA, aka the National Aeronautics and Space Administration, tells how Newton's laws apply to landings. There's no better place to learn from than the juggernaut of space exploration.

This video tutorial from TutVid shows how to create a simple movie poster text effect in Adobe Photoshop CS4.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

You have a Rubik's Cube, maybe your mother gave it to you for your birthday, maybe you actually bought it for yourself, or maybe you just found that colorful puzzle cube in the gutter, but either way... you don't know how to solve it.

Watch this short animation tutorial on how to perform the sandercurl trick for claymation animation videos.

This automotive video tutorial will show you the steps on how to properly drive a manual transmission car.

When a dog pulls on the leash, the first temptation would be to jerk back. Even if you win the power struggle, the negative reinforcement creates a bad association with you which should be avoided when training your pet dog. Dog trainer Eric Letendre shows how to do an easy technique that will stop a dog from pulling while walking on the leash.

Learn how to be safe and stop someone from invading your home.

Pushing music from your iPhone to your HomePod or HomePod mini by just moving the devices close to each other is certainly a great party trick. But if Handoff is too easily triggered, you might not think it's worth the wow factor. Thankfully, there's an easy way to stop your iPhone from sharing audio to your HomePod or HomePod mini (and vice versa) if you're finding it happens way too often.

The native timer feature on your iPhone works well enough that you probably haven't even thought about installing a third-party timer. With just a few taps, you can get a countdown for any amount of time up to 24 hours (or one second shy of 24 hours, to be precise). But as fast as it can be to set a timer from the Clock app, there are even faster ways to start the countdown.

Since its introduction in iOS 11, the Screen Recording tool has been a great way to show less tech-savvy users how to use their iPhones better. It's never been easier to show your grandmother how to disable Live Photos or lower screen brightness. However, banner notifications can appear during a recording, forcing you to start over. They can even interrupt a screen share during a Zoom or Skype meeting.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

It seems like all tech companies want to know where we are. Even Apple and Google have been caught abusing their location access on iOS and Android. Luckily, there are apps that can trick your phone into thinking it's somewhere it's not.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

Though many were hoping for it, a notification indicator around the Galaxy S10's front camera punch hole never came to fruition. Since then, we've been finding other uses for the camera cutout, from turning it into a circular battery meter to using creative wallpapers. Thankfully, there's now an app that will give you LED-style alerts with a ring around your S10's camera.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

There's more to recording calls than just protecting yourself against liability or an angry ex — oftentimes, this feature is the perfect tool to save momentous calls like breaking news of your recent engagement to loved ones. And with the prevalence of video calls, you can even capture memorable video chats such as your mom's first glimpse of your newborn on your mobile, courtesy of Skype.

Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

Malaria is a massive worldwide health problem. The Centers for Disease Control and Prevention estimate that 212 million cases of malaria occurred worldwide in 2015 and 429,000 of the infected people died.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

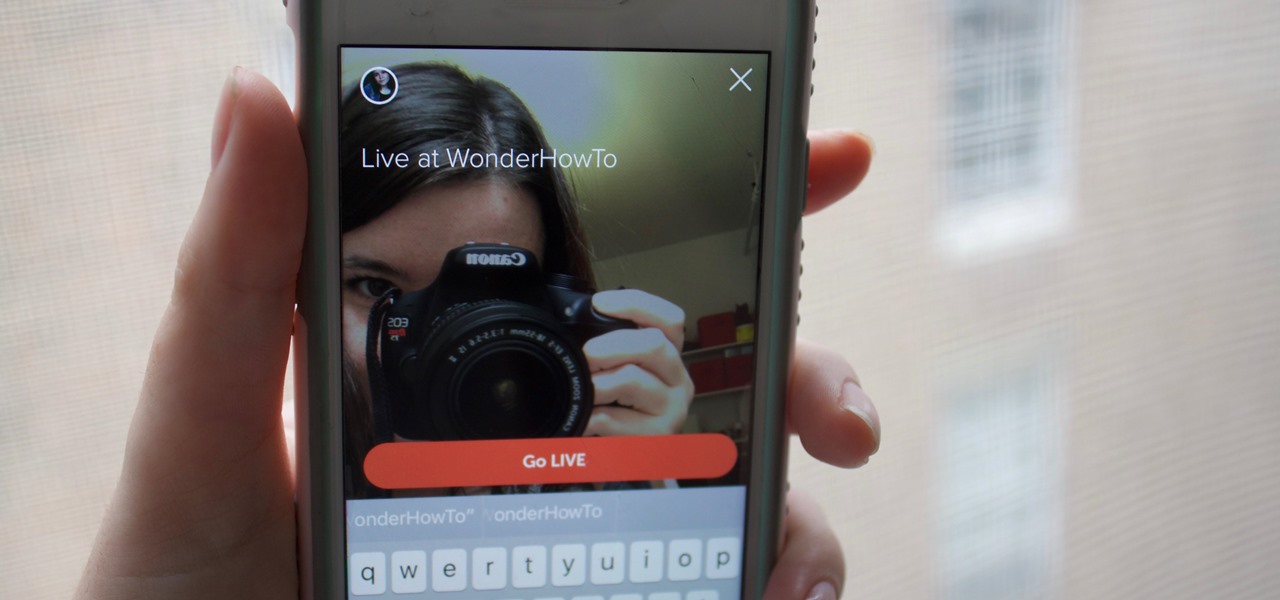
It seems that every major social media platform is adding a "Go live" feature to their apps lately. Twitter, in particular, has been at the forefront of the live broadcasting craze for quite some time now.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

Citrus greening disease — caused by a bacteria spread by psyllid insects — is threatening to wipe out Florida's citrus crop. Researchers have identified a small protein found in a second bacteria living in the insects that helps bacteria causing citrus greening disease survive and spread. They believe the discovery could result in a spray that could potentially help save the trees from the bacterial invasion.

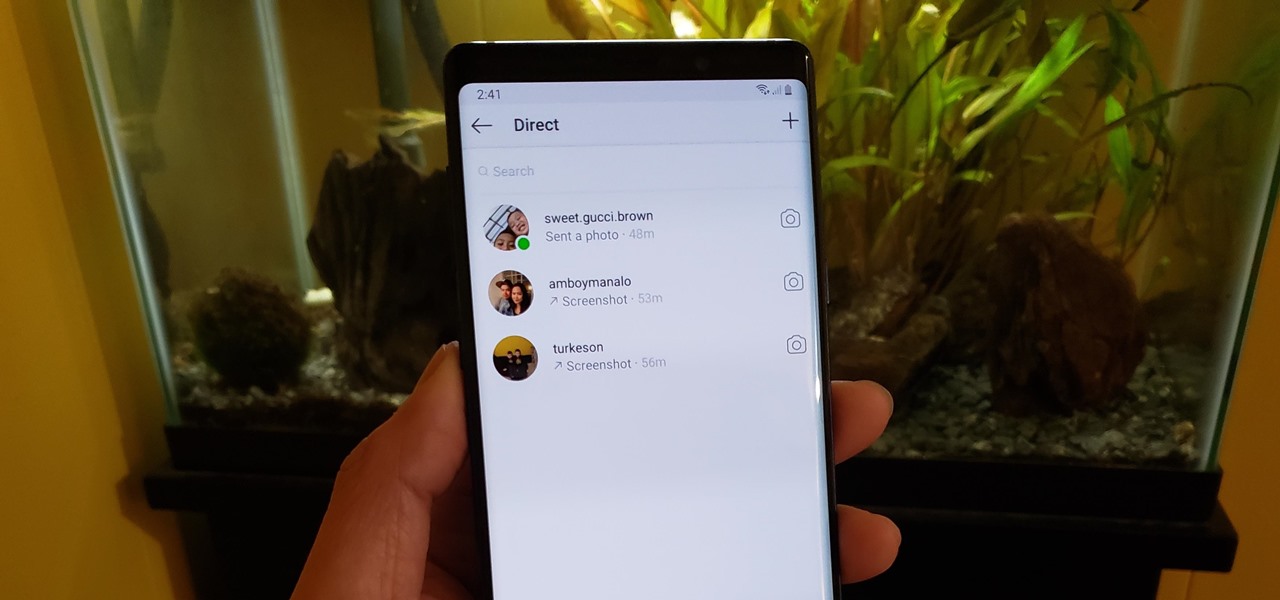
If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.

The evolution of our infection-fighting systems may have something to teach modern scientists. That's what a group from the University of Granada in Spain found when they studied a protein that's been around for over four billion years. Their work, by senior author José Sánchez-Ruiz and colleagues in the Department of Physical Chemistry, was published in the journal Cell Reports.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.