Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

The US Department of Transportation says it is actively completing a previously promised revision of voluntary guidelines for driverless vehicles originally drafted by President Obama's administration.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

As we slowly approach its January 3 start date, CES 2017 seems to be shaping up to be an exciting year for smart glasses as well as augmented and mixed reality.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

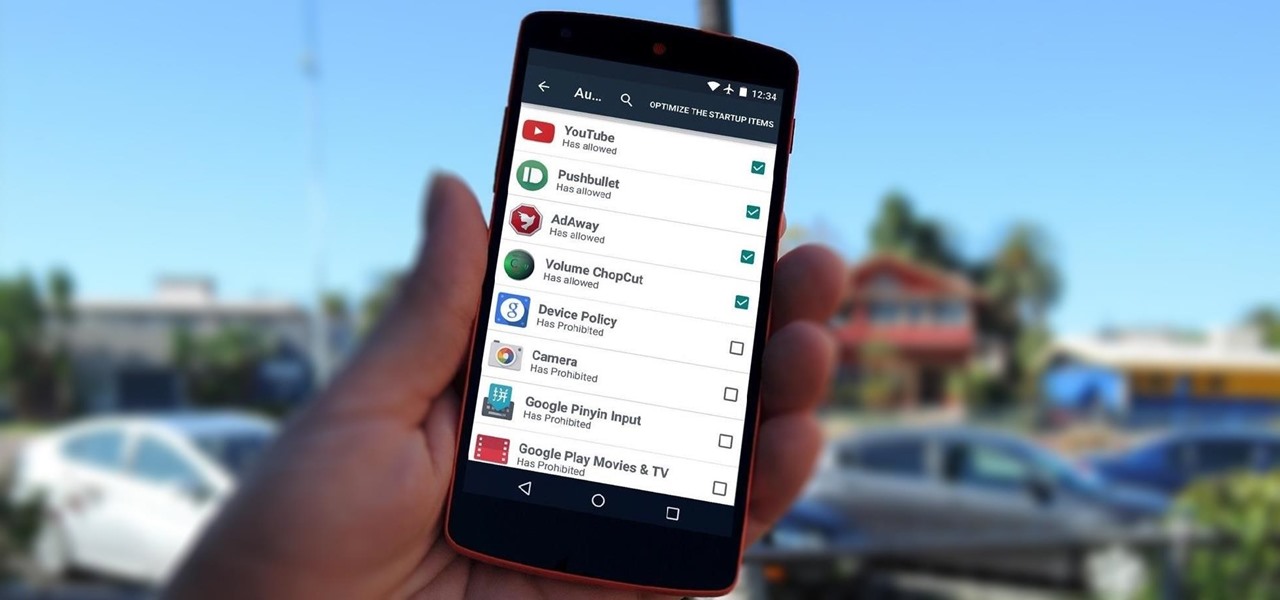
By default, any app that requests a certain permission can run automatically as soon as you start your device. Since Android doesn't offer a granular permission control system like iOS, this gets lumped in with all of the other permissions that you have to accept when you're installing an app from the Google Play Store, and you effectively have no choice in the matter.

With the bombardment of technical issues that have plagued GTA Online since its inauguration, it hasn't been easy to enjoy stealing cars and killing hookers with all your friends.
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

Economists have long since known that people want to be rewarded for taking on risk. Investments are thus judged by their risk-adjusted returns (Sharpe ratios). A typical hedge fund has a Sharpe ratio of around 0.5. This means that its excess annual return over the risk-free rate is about half its annual standard deviation.

The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

What runs underneath the hood of your car is pretty important. No, scratch that. IT IS VERY IMPORTANT. That is the life force of your vehicle and if you want to make sure you are able to make that car last and use up every penny you have spent on that beautiful piece of machinery, then you better make sure that you constantly check the fluids throughout your car frequently. Oil, transmission, clutch, brake, etc. those fluids help make sure your car will run nice and smoothly for years to come...

In this Computers & Programming video tutorial you will learn how to upgrade from Windows XP to Windows 7 with CNET. You need to do these 3 things. 1st - run the Windows 7 upgrade advisor to know if your computer can handle any version of Windows 7. 2nd – check the Windows 7 compatibility center to know if you need to upgrade your drivers or apps. 3rd – make a copy of your hard drive. Down load and run the ‘windows easy transfer’ wizard. This will back up all your files and settings to an ext...

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...

The world has gone Lady Gaga MAD! Run for cover! ... But run for cover in STYLE with this makeup tutorial by makeup master, Michelle Phan. In this video, Phan re-creates the "big eye" look for Lady Gaga's "Bad Romance" music video.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to make high quality audio/video cables.

You may remember the recipe for a basic non-Newtonian fluid from grade school science experiments (one part water to one and one third part corn flour or cornstarch), but those trials probably stopped at squeezing the mixture in your hands. While a regular fluid's viscosity wouldn't allow you to walk on it, a little bit of technique and the magic of physics will have you walking on a non-Newtonian fluid as well as Jesus. This video science experiment shows how to use 50kg of corn flour/cornst...

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Ready to make a statement in your town and get involved? Check out this tutorial and learn how to run for mayor. If you can't beat city hall, why not join it?

It's summer again and it's time to get out of the house and there's no better way than with a fun game like some improvised baseball. You don't need a whole team of people all you need is a bat, a ball and another person to play with.

Learn how to exercise your dog. Follow a regular exercise routine together with your pet. It will benefit you both!

Five simple tricks to keep your laptop running longer.

Three quick ways to help your computer work faster if you are running Windows XP.

This video demonstrates how to run macros in Excel 2007. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to run macros in Excel 2007, For Dummies.

All-Star Harold Reynolds shows the proper techniques for stealing, running the bases more effectively and mastering the base paths! Baserunning is a valuable skill for earning runs and stealing bases. Steal and run the bases with Harold Reynolds.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

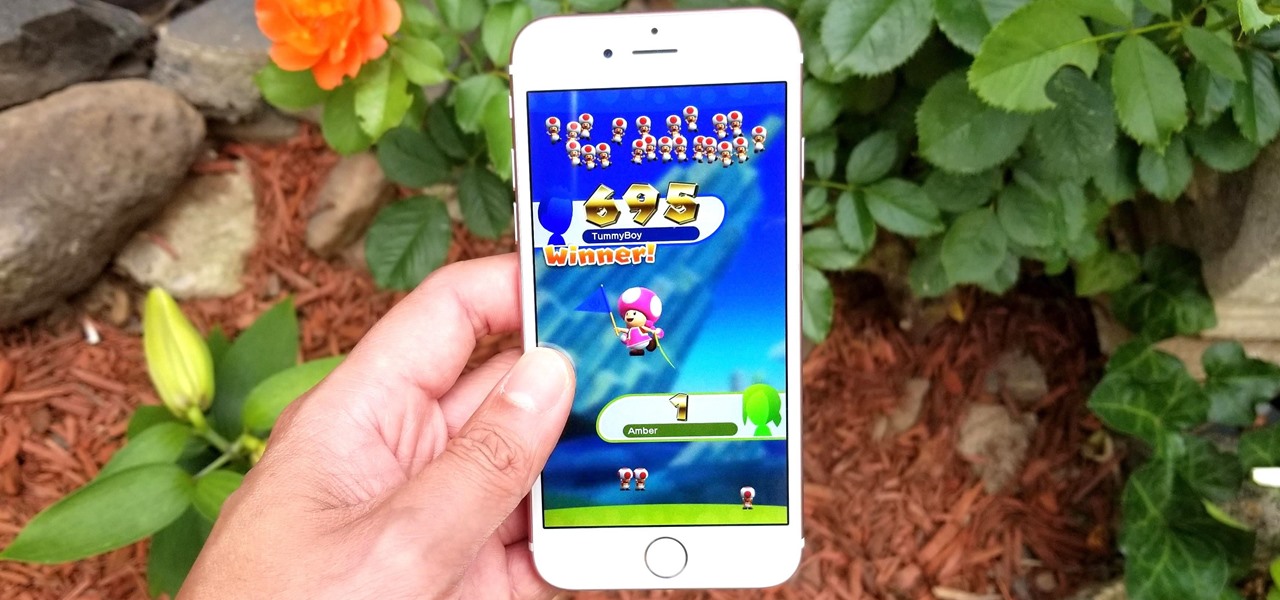
One of the best features in Super Mario Run is a multiplayer race that lets you test your skills against other players. Toad Rally, as it's called, pits you against other players in a battle for Toads. The more Toads you collect, the easier it is to build your kingdom and collect more rewards on your Android or iPhone.

At the WinHEC Shenzen 2016 Keynote, Microsoft showed off a system running Windows 10 smoothly on an ARM processor. This could be great news for developers of mixed reality software.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Being able to run mobile apps on a computer is nothing new. Maybe you don't have a mobile device, or maybe you just like seeing the apps on a larger screen. Whatever the reason, with programs like Bluestacks, you can use your laptop to Instagram, play Angry Birds, and run countless other apps made for smartphones.

Reading FC Academy Manager Eamonn Dolan takes you through some simple turning drills. These are important for every player on the field to turn on a defender. Running, turning and dribbling with the ball is important to moving the soccer ball up the field. You can practice with a square as a group. Practice turning, dribbling and running with the ball.

In this video tutorial, Creative Cow Contributing Editor Eran Stern will show you a different technique to create the Running Numbers Effect using Trapcode Form plug-in. For more on using the Trapcode Form plug-in Adobe After Affects video tutorial. Create a running numbers effect in Trapcode Form.