Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Great news, zombie killers! Zombie Gunship's long overdue sequel, Zombie Gunship Survival, has finally arrived for iOS and Android devices as a soft launch available for download in the Philippines—which means that with a little tinkering, you can play the new game in any country.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

Some manufacturers, like Samsung and LG, have had split-screen multitasking on their custom versions of Android for years. But starting with Android Nougat, Google added this functionality to AOSP, which means that all phones and tablets running Android 7.0 or higher will now have a new multi-window mode.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Today we are pleased to announce the end to the Apple vs. Android war. About a year ago, our Gadget Hacks team started working on a top-secret project to dual-boot both Android and iOS on the same phone—and we couldn't be more proud to announce that we've finally succeeded! Your phone can now run both iOS and Android—whenever you want. Right now.

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

If your Samsung Galaxy Note 2 has been feeling sluggish lately, or you've noticed the battery not lasting as long as usual, the problem could be that you have too many applications running in the background.

I rarely ever turn my desktop off. For starters, it takes a few minutes to boot up, which I hate, and secondly, putting the computer to sleep is perfectly adequate. You really only need to completely shut down your computer every once in a while.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

With the new year right around the corner, it's time to talk about the end of the 19th century, a time which plays an enormous role in Steampunk. If you've done any reading of British books written from about 1890 to 1899, you may have come across the phrase 'fin de siecle' and wondered what it meant. You also may have come across this term in reading about the late Victorian era. No worries, I'll tell you all about it! Image by Giovanni Dicandia

Can't quite figure out how to run a macro when using Microsoft Excel 2011 on your Mac? This video will show you how it's done. Whether you're new to Microsoft's popular digital spreadsheet application, new to Excel 2011 or even an expert merely looking to brush up on the fundamentals, you're sure to be well served by this quality video tutorial from the folks at Lynda. For all of the details, and to get started using macros in your own MS Excel '11 projects, watch the video.

In this video, we learn how to bleed and adjust trailer brakes. First, level the trailer and use a jack stand to support it. Now, hand bleed the brakes using the master cylinder. From here, let any air out of the break line, doing this on all the different brake lines. Next, fill up the master cylinder with oil to make sure it doesn't run dry. Open the pressure valve and then close it as your run through the process. When finished, you will need to adjust the brakes by lifting the trailer. Af...

In this tutorial, we learn how to make a homemade compost tumbler. Find a large barrel and mount it on a wood frame. You can use recycled materials, like an old pickle barrel if you can find one. There should be an axle in the middle of the wooden posts that runs through the tumbler as well. There should be a pipe in the middle bottom of the barrel to run air through, that will exit through the top where the handles are at. The aeration system will help your compost work properly, so you can ...

In this tutorial, we learn how to get scrunchy hair right out of the shower. First, take a smoothing liquid you like in your hair and run it through your entire head of hair. After this, take a volumizing gel and run it through your hair as well. Now, spray hair spray all over your hair, working it from the top to the bottom all over. Next, you will take your hands and scrunch your hair by pushing it up and crunching it with your hands. Do this all over until you have the scrunch that you wou...

In this tutorial, we learn how to manage your American Girl dolls' curly hair. First, you will need a spray bottle with water in it to spray on the curls. If you can't brush it, that's fine, just run your fingers through it. If you can brush it, run your brush through the hair after spraying it. To curl her hair, you will separate the hair into sections. Then, you will curl the sections by rolling them around the finger to create a spiral curl. When finished, the hair will look gorgeous and l...

In this video, we learn how to flat iron your American Girl doll's hair. First, heat up your flat iron on the lowest heat setting it has. Now, brush your doll's hair so it doesn't have any lumps or bumps in it. Clip the to of the hair up and then take a small section from the bottom of the head. Then, squirt some water on the hair until it's wet. Comb through the hair and then run the flat iron through the hair very quickly. Run it through again if needed, then continue on to other sections i...

In this video, we learn how to change a circuit breaker. First, turn the main breaker off so there is no running electricity. Then, go to the meter area around your circuit breaker system. With these, there will be wires running all around the entire system. With most breakers, you can pull them right out from where they clip in. There will be a wire connected to this which you can remove. Do this, and then connect the wire to the new breaker. Snap this back into place and make sure it's secu...

In this video, we learn how to make your own solar panel.The amorphous solar glass is the cheapest but it's also the least efficient. You can do anything you want with these and they are durable. The hexagon cells are the most efficient and most expensive as well. The poly crystalline is almost 2 watts a piece and can be purchase in lots of any size. You have to tab these cells together and they are extremely fragile. Be careful when you work with these. To make these, you will solder tabbing...

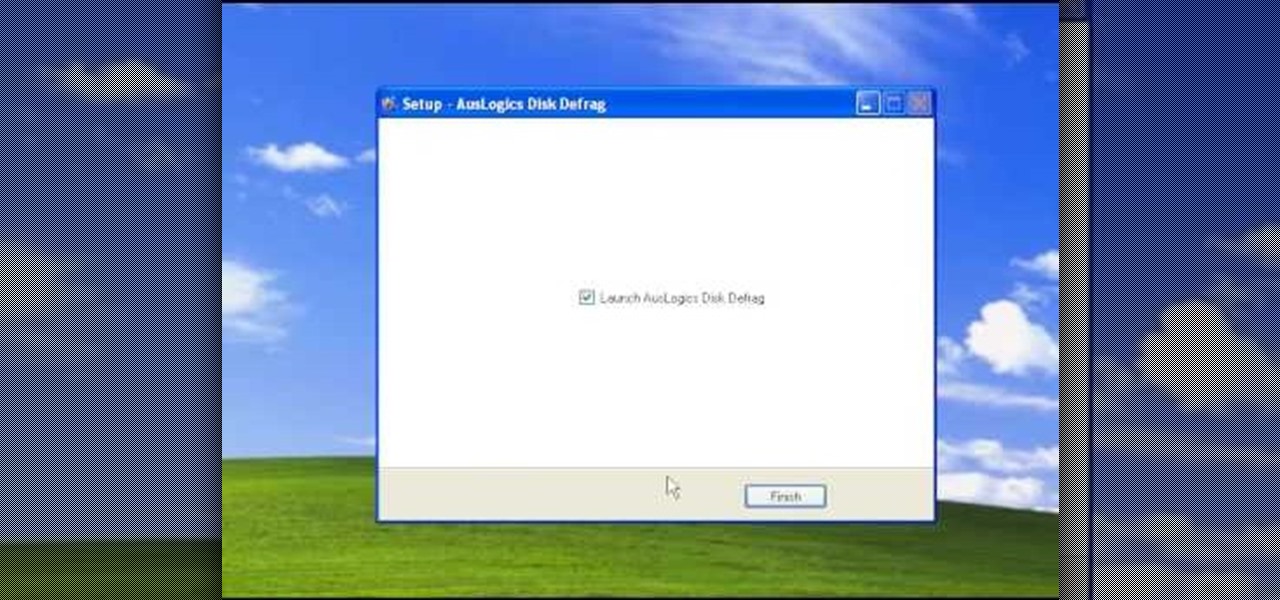
This video tutorial is in the Computers & Programming category which will show you how to defragment your computer step-by-step. This will make your computer run efficiently and faster. Do a Google search for auslogics disk defrag and download and save the program. This program allows you to continue using your computer while the defrag is in progress. Then run the set up, accept the license agreement and launch the program. Here you can select the drive that you want to defrag and click on n...

In this video, we learn how to use the Auslogics disk defrag on your computer. Fragmenting your computer will help move around your files and clean out items that you don't ever use so it can run quicker and perform better. First, open up the Disk Defragmenter on your computer and then go to the Auslogics website to download their disk defrag. After you have this installed, run it on your computer and let it go through the process of cleaning out your computer. Once it's finished, you will be...

In this tutorial, we learn how to change your engine oil for maximum auto performance. First, you will need to find your drain plug underneath your car and let the oil drain out of the tank until it doesn't run any longer. You may need to jack your vehicle up to do this. Once it's done draining, replace the drain plug to the oil tank. Use a new washer and bolt if you need to. Now, pop the hood on your vehicle and find the oil tank. Remove the cap and place a funnel inside of it. Pour your new...

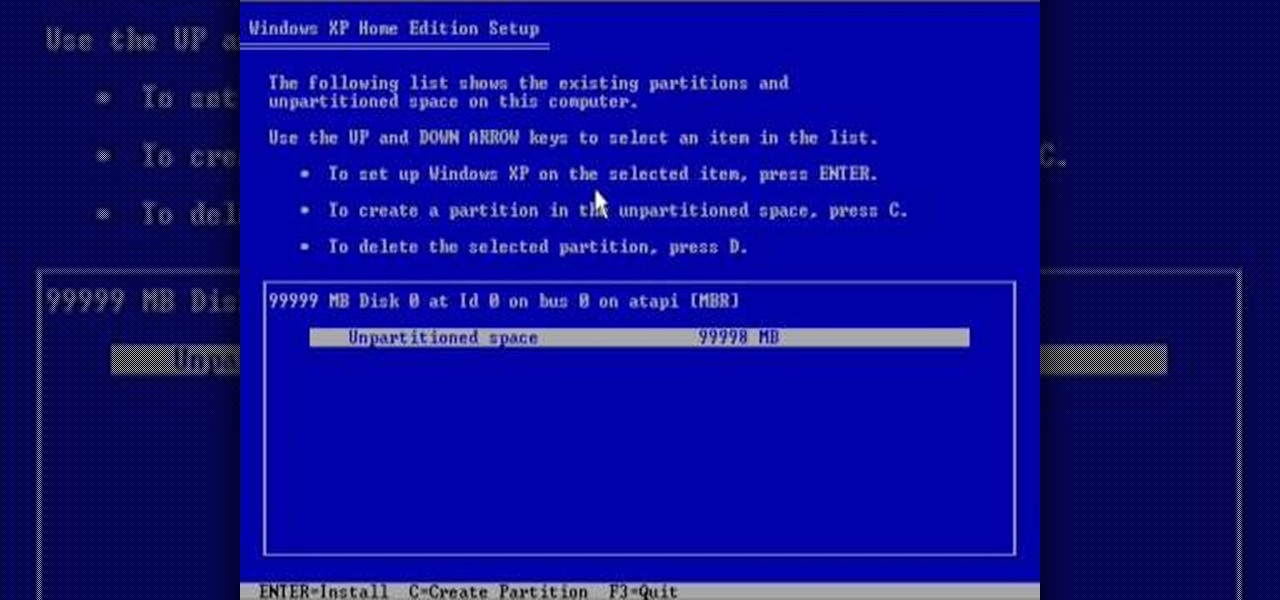
In this tutorial, we learn how to reformat your computer. If you're computer is running very slow, this is a great way to get it to run faster. First, insert your operating CD system and restart your computer. After this, a blue screen will show up and you will see a list for "unpartitioned space", which will show the size of the drive. Then, you will need to choose which of the options that you would like to do. You can choose the option by reading through the menu and using the keys on your...

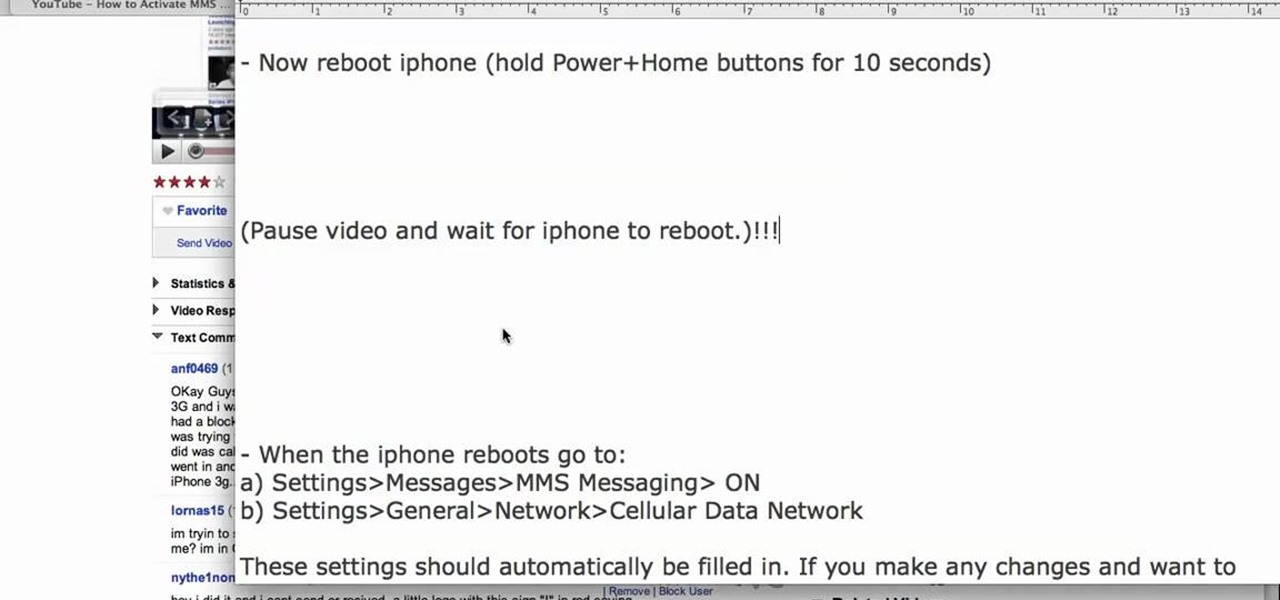
In this tutorial, we learn how to use MMS on T-mobile or ATT iPhone using 3.1 or lower. First, you need to make sure you have iTunes down and it's not running on your computer at all. After this, go to the start menu, then click on the run. Next, type in "command" and hit enter. Then, type or copy and paste "C:/Program Files/iTunes/iTunes.exe/setPreflnt carrier-testin 1" into the command console that comes up. Then, hit enter and reboot your iPhone. When this reboots, go to the settings menu,...

This is a very easy process. All you need is a PSP, a PS3 and a USB chord. Connect your USB chord into your PSP and the PS3. Download the software FUSA gamepad from QJ.net. This is a customized firmware for this purpose. Load the software into your game folder. Look for your memory stick in the game section. Run the software. Once you run the software with the PSP and PS3 connected, the PSP becomes the controller. Test by using the various buttons on the PSP to see if the PS3 responds properl...

In this tutorial, we learn how to jump higher and run faster doing plyometric exercises. Start out with an alternating exercise that you will rotate through all of and get progressively stronger within 10 weeks. In week on, start out with 15 speed squats. Then you will have 30 seconds of recovery followed by 15 lunges with each leg for a total of 30 lunges. Take another 30 second break, then do 10 lateral cone hops, barely touching the ground. Another 30 second recovery after this, then do 10...