
How To: Create a underground wire tunnel
Tim Carter of Ask the Builder, demonstrates how to drill a hole under a sidewalk, driveway or walkway so you can install an underground wire.


Tim Carter of Ask the Builder, demonstrates how to drill a hole under a sidewalk, driveway or walkway so you can install an underground wire.

Are you determined to go running every single day? Even during the winter? If the snow and cold can't deter you, you might as well learn how to run safely in the winter months. It's all about how you dress. Dressing warmly is the key to having safe jog. Here are some tips from the members of the morning run club at St. Louis Park Lifetime Fitness.
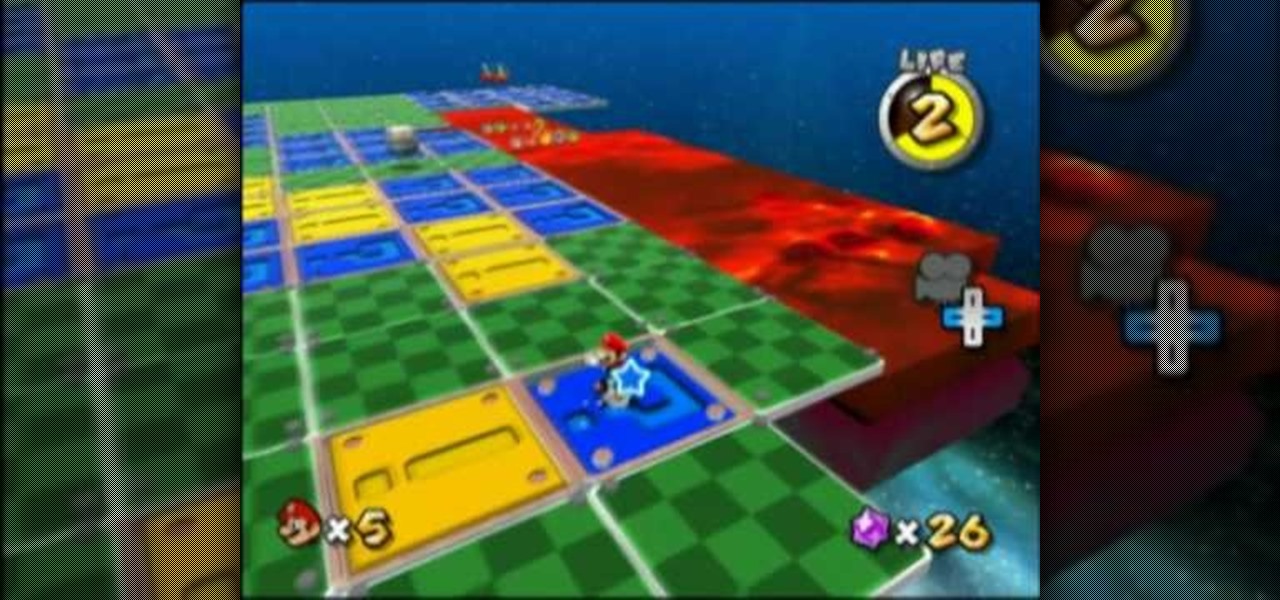
On your mission to collect all 242 stars in Super Mario Galaxy 2 on the Nintendo Wii, this is your last World before moving on to the 120 green stars and bonus stars. World S is the key to get the rest!

Getting regular cardiovascular exercise is extremely important to maintain good health but it can be difficult to find an exercise that isn't strenuous on the joints. Luckily aqua jogging is a great workout for any age.
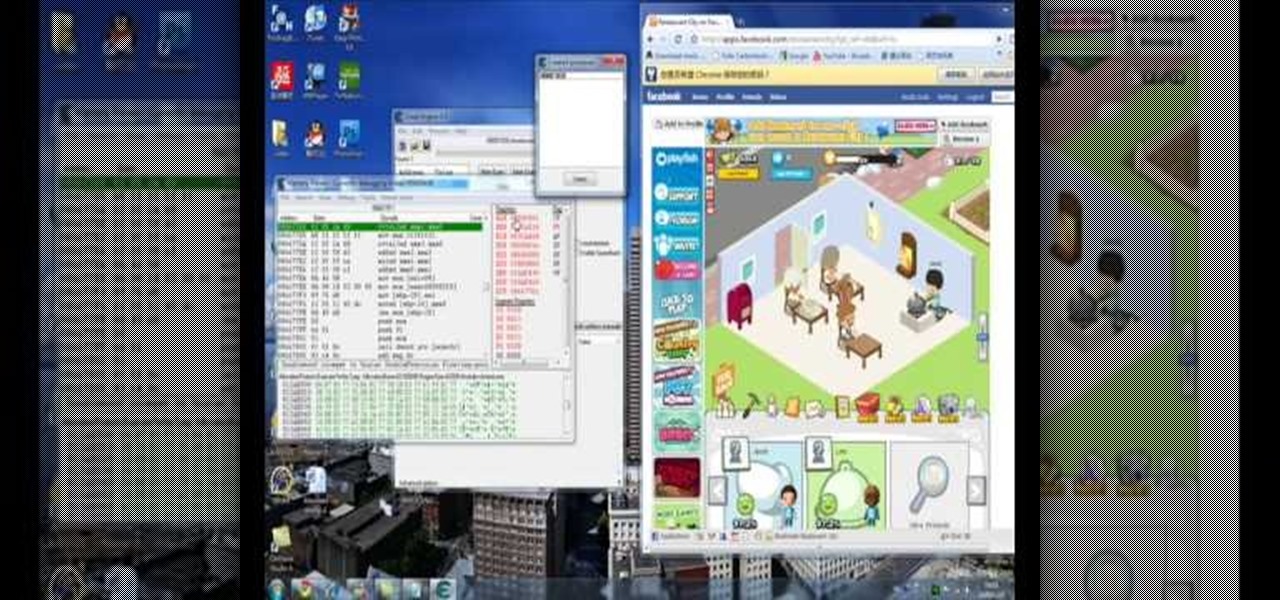
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

Hacking RC is easy with Piaps Restaurant City Hack! Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to cheat Restaurant City with Piaip's Hack (11/08/09). See how to download, install and run Piap's Restaurant City Hack v.1.13 or 1.12.

This isn't your Soccer 101 tutorial. Created by Real Madrid C.F. and Portugal soccer player Christiano Ronaldo, the Ronaldo chop is a dazzling trick that involves flicking the ball with his back leg past his opponent before running on to make a goal.

Hall Of Famer Ozzie Smith, one of the greatest shortstops of all time, joins Harold (also a multi-Gold Glove winner) for skills and drills! This is an official MLB instructional drill on infield drills and plays. Run infield drills with Ozzie Smith.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Even three years after its initial release, Niantic's Pokémon GO is still going strong. If you're an Android user still on the hunt for your city's latest Pokémon haul, however, you'll want to listen up — Niantic is cutting support for aging Android devices, meaning soon your dream of catching 'em all may be coming to an end.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.
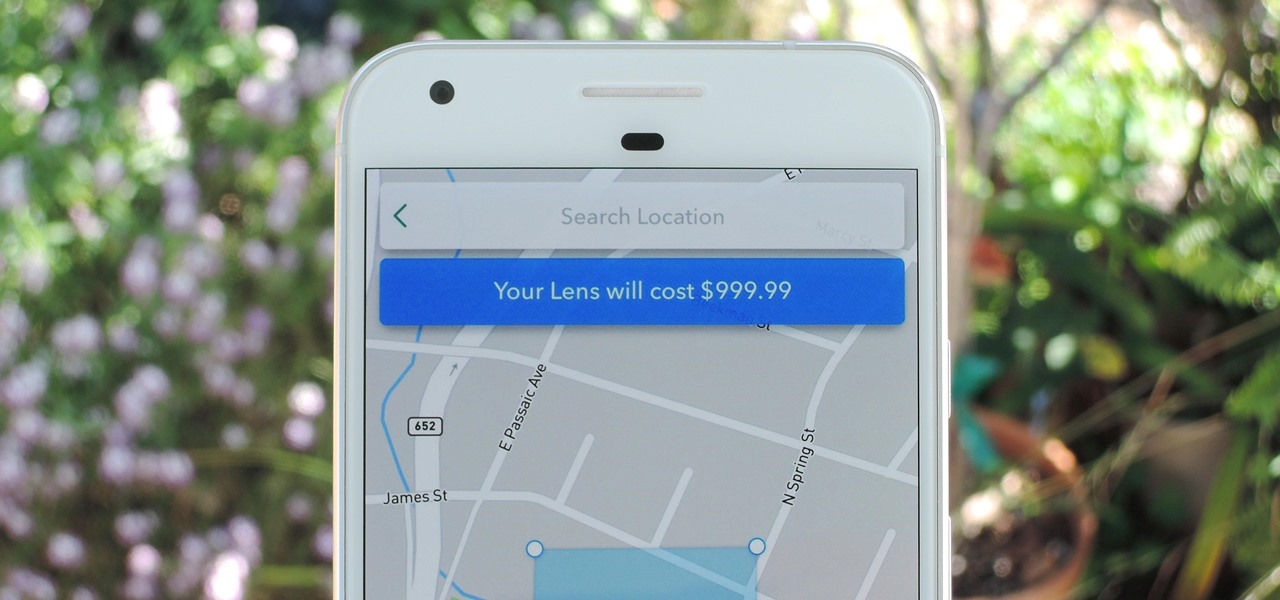
Snapchat just rolled out a feature that lets you create custom Filters and Lenses. While the average Geofilter won't run you more than a few bucks, it's not that hard to exponentially jack up the price. Amazingly enough, Snapchat's latest attempt to monetize their platform can ultimately cost you as much as $999.99. Ignore the penny, let's call that a cool grand.

Coming into this year's Consumer Electronics Show (CES), the common sentiment among observers was that this was expected to be the big year for augmented reality.
With beta testing coming to a close, it's quite likely we will see the stable Android Oreo OTA roll out for the Galaxy S8 in late January. Yesterday, a Reddit user posted a link to an official Oreo OTA build for the Galaxy S8. We've already detailed everything that's new in this stable build. Now, let's take a look at how you can install the update on your device.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.
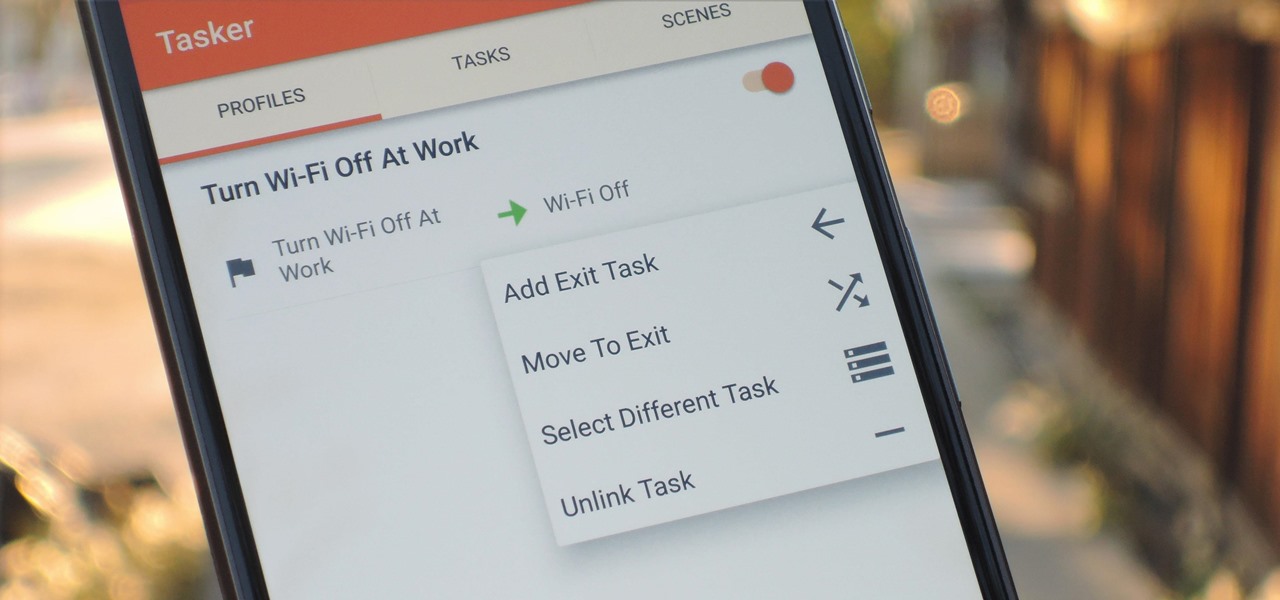
When you create a profile in Tasker, it will run a task as soon as all of the conditions in your profile are met. But what happens when the profile's conditions stop being met? By default, nothing will happen, but if you create an exit task, the automation tool will run that instead.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.
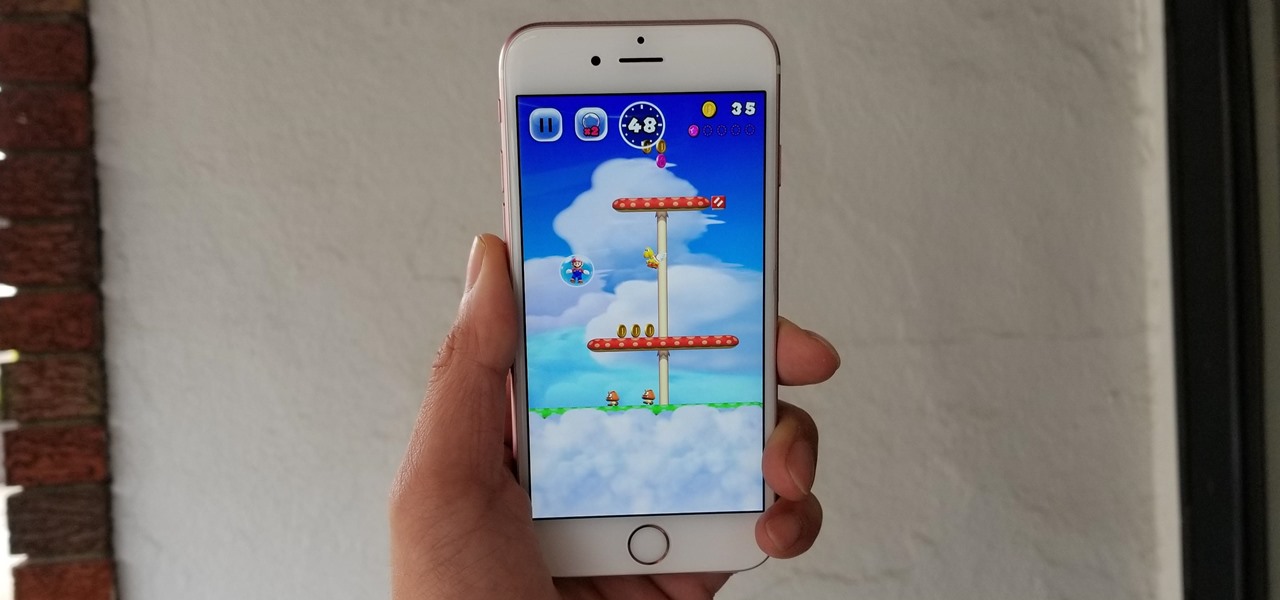
Bubbles serve as extra lives to help you get through both Tour and Toad Rally modes in Super Mario Run. Even better, they let you rewind back to pick up any items that were missed. But unbeknownst to many, you can activate a bubble even if you haven't gotten knocked out yet.
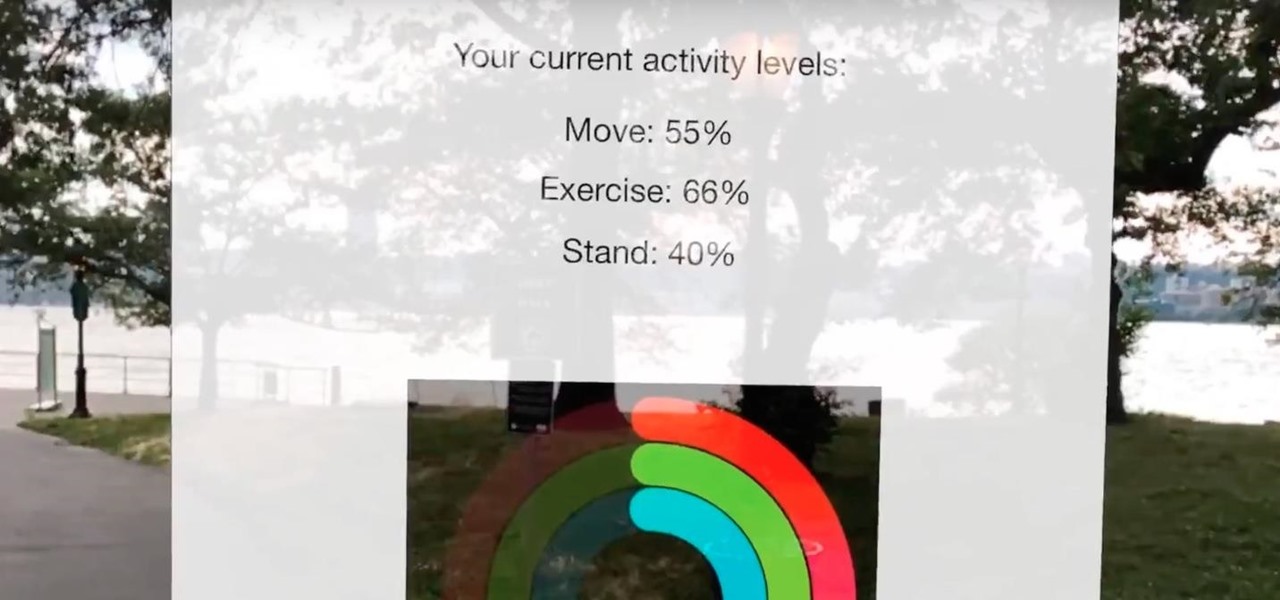
When people work out, they want to get the absolute most out of their routine. Going on a run is great exercise, but finding an optimal route that works best for you can be difficult. Luckily, Apple's ARKit has the capability to make it much easier to get the most out of your workout.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.
In the past, some of Google's Nexus devices have had root methods even before the phones hit shelves. The Google Pixel and Pixel XL are basically Nexus devices from a software standpoint, so why have we gone more than a week since release without a working root method or custom recovery?

A developer from a firm named Tendigi came up with a way to run Android Marshmallow 6.0.1 on an iPhone 6 Plus, and it's pretty awesome. The hack is the brainchild of Nick Lee, who had previously installed Windows 95 on an Apple Watch, and you can see it in action below.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series
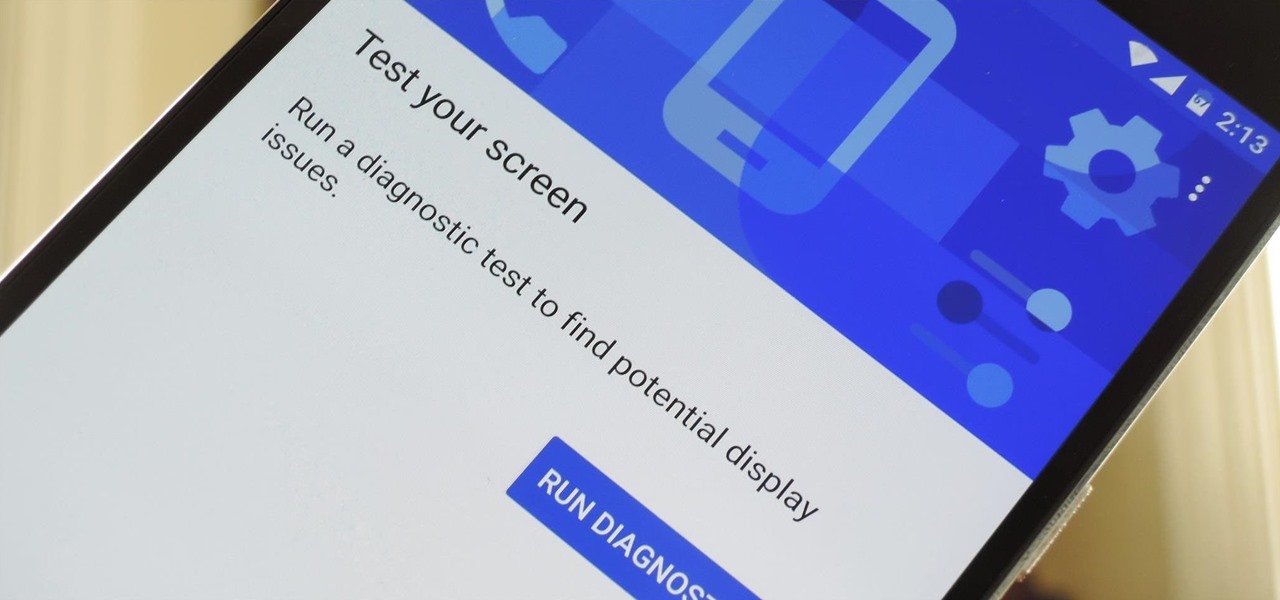
Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.