A Pakistani lawyer who represents victims of U.S. drone strikes has been forced to cancel a trip to the United States after the U.S. government failed to grant him a visa. Shahzad Akbar was scheduled to speak later this month at an International Drone Summit in Washington, D.C. Akbar is co-founder of the Pakistani human rights organization, Foundation for Fundamental Rights. He filed the first case in Pakistan on behalf of family members of civilian victims.

News in a nutshell: Iran Boosting enrichment efforts

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. There are many ways to get around in Minecraft, from boats to mine carts, but did you know that you can travel even faster on foot? That's right, by creating a running track, players can run at super speeds! Not only is it the single fastest way to travel, it's easy to build as well. No redstone wires required.

As of right now, Guinness World Records claims that the highest human flight with a rocket belt is 152 feet, accomplished by Eric Scott in 2004. But they may need to update their records soon thanks to Martin Aircraft Company in New Zealand, whose Martin Jetpack finally showed the world it can fly—really fly.

Area 51 is the most secretive military base in the United States, a base that U.S. government officials to this day still barely acknowledge because of its top secret development and testing of experimental aircraft and weapons systems. But a slew of Cold War-era documents have finally been declassified, and National Geographic has discovered a rather low-tech method the military used to hide its high-tech prototypes.

If you're not familiar with the animations of Jan Švankmajer, you're in for quite a trip. The Czech artist and filmmaker is known for his metaphorical, captivatingly surreal stop-motion and claymation films, and is God to many (including talents such as Tim Burton, Terry Gilliam and the Brothers Quay).

A radical art group of Russian political pranksters, who go by the name of Voina, have delivered a giant "Up Yours!" to the Russian government... in the form of a 213-foot-tall penis.

This is a follow up to my last post on watching games in 3D. My main concern (because apparently I'm something of a technical snob, since no one else I went with considered it an issue), was that I perceived a lack of definition for a theater presentation.

Sprinytting isn't just running to your maximum level. There is technique to maximize your runs, gain speed and get the best workout possible. This video show you exactly how to improve your sprinting technique.

For jumpstyle dances Melbourne Shuffle and Running Man, don't worry about hand movements yet. Just get your feet right and then the hand movements come after. Next comes spins.

Watch this video to learn how to work with PEX piping. Steps:

This tutorial shows you how to make a vegas style sign where lightbulbs turn on and off in sequence around the outside of a shape. Using simple photoshop files, create an animated billboard of a T. Create a "running lights" effect in After Effects.

Instagram is addicting — and that's done on purpose. To stop your Instagram habits, your smartphone likely has a built-in feature to curb the daily usage of a particular app, like Apple's Screen Time for iOS and Google's Digital Wellbeing for Android. But you don't need to mess with those complicated settings when Instagram itself can help you get some of your life back.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

Not every app is designed well. With nearly 3 million apps on the Play Store and countless more that you can sideload from other sources, there are bound to be a few stinkers. And many of them do a terrible job using RAM.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Alternate US history is the go-to move for hot new cable and streaming shows, from HBO's Watchmen to Hulu's The Handmaid's Tale, reimagining how things might have turned out is an endless well of narrative inspiration.

The UK has officially exited the European Union, completing the long and tumultuous Brexit story and putting the storied nation once again on its own on the international stage.

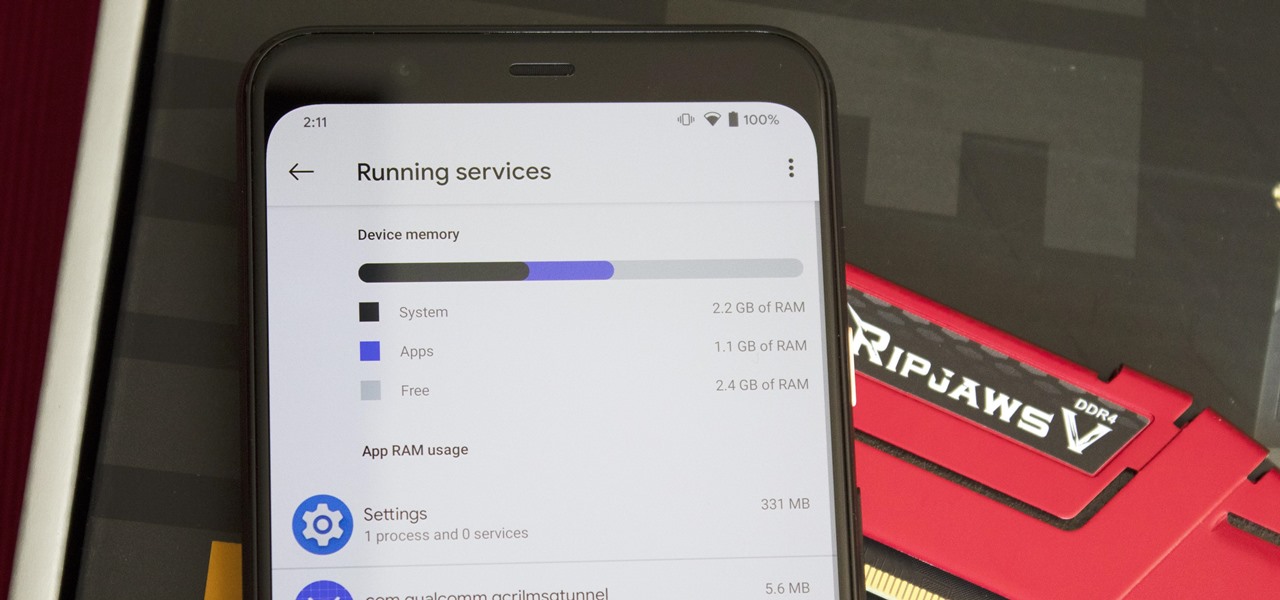
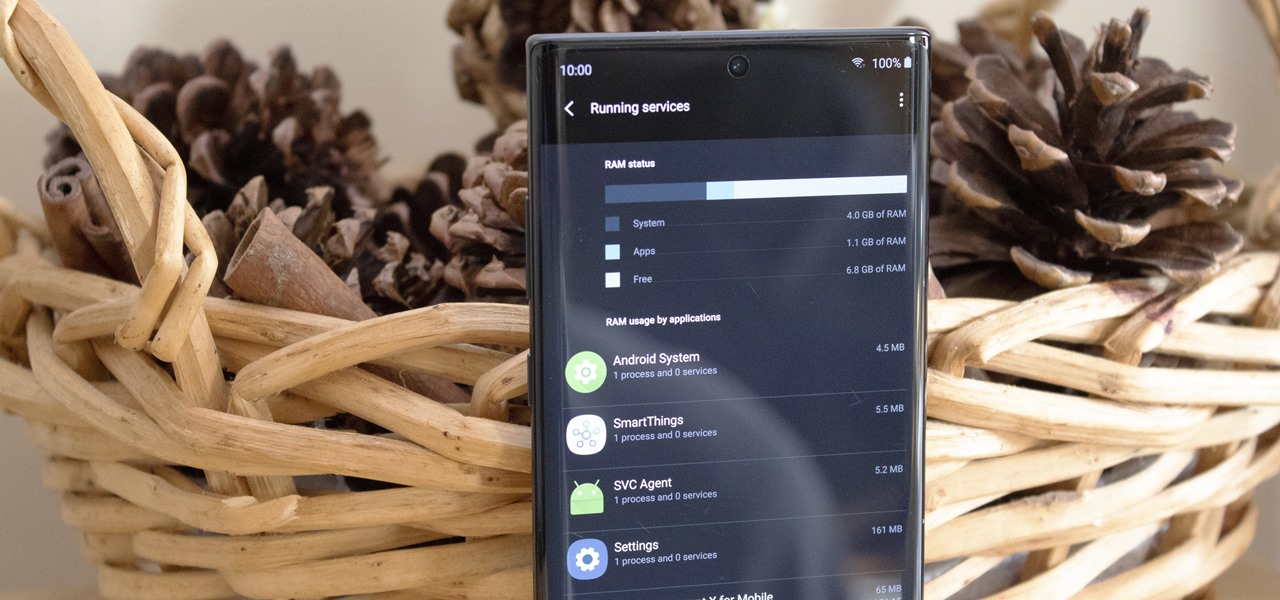
There are phones nowadays with 12 gigs of RAM, but they'll cost you well over a grand. The majority of Android devices have much less memory — I'd wager most have less than 4 GB. And with the system taking up around 2 GB, that leaves user-installed apps little room to breathe.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

While Elon Musk is in Los Angeles showing off the future of personal transport via the Cybertruck, another, unaffiliated group is taking one of his most popular ideas to market, with augmented reality as a key part of the plan.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Augmented reality can be more than simply a way to enhance navigation, or superimpose virtual sunglasses onto your face. It can also be a platform for shining a light on important social issues.

As Microsoft works toward fulfilling its $480 million contract to supply modified HoloLens 2 headsets to the US Army, Airbus is preparing to supply advanced augmented reality apps for the device.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

The wildfires that spread across Northern California for two weeks in November were among the deadliest and most destructive in the state's history. Ultimately, the incident claimed 85 lives, and hundreds of people are still missing in the wake of the disaster, which impacted over 154,000 acres of land.

To punch up the launch of its new podcast, USA Today has created an augmented reality experience to introduce listeners to the story of corruption in Chicago.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

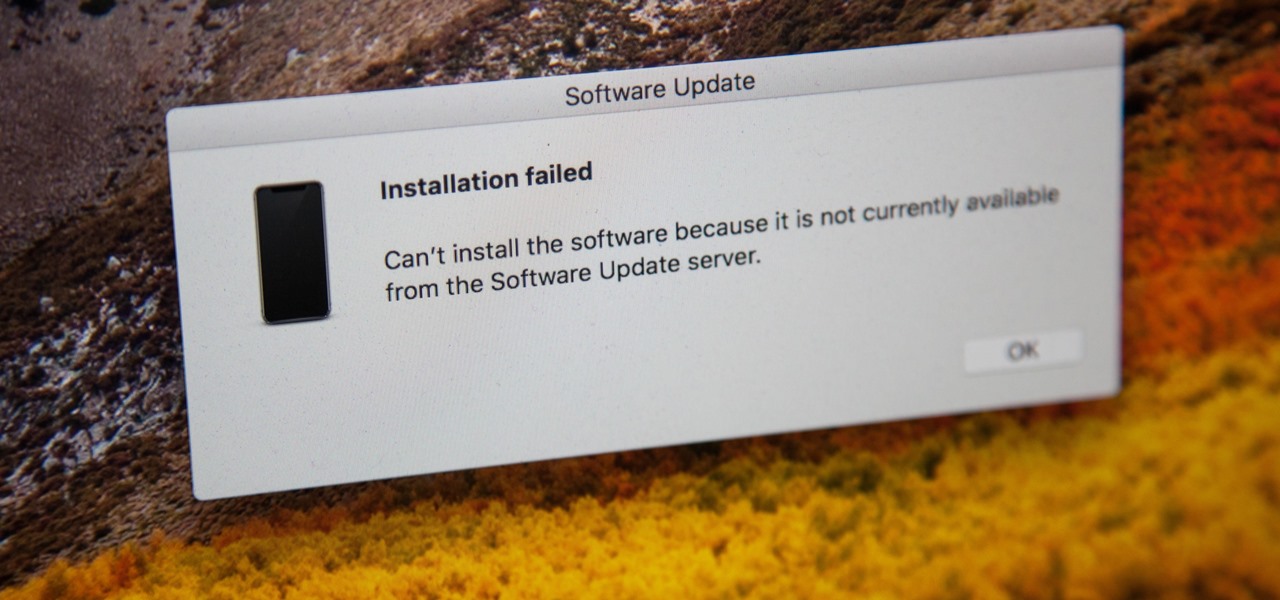
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

When Google first announced Android Oreo (Go edition), many believed these devices would be focused more on developing countries. However, thanks to ZTE, we'll be getting Android Go stateside, so US customers on even the tightest of budgets can still enjoy the convenience of a smartphone.

From its official launch back in September, iOS 11 has been equal parts revered as it has been criticized. Even with all the great, new features we've come to expect from a major iOS update, plenty of bugs and glitches have forced users to overlook the positives. Perhaps that is why, four months later, 25% of iPhone owners are still running iOS 10.3 or earlier.

Update 10/14: Developer paphonb has added rootless Google Now integration to the leaked Pixel 2 launcher, so now, anyone running Android Nougat or Oreo can get the full Pixel 2 home screen experience. For those running Lollipop or Marshmallow, we've left the unaltered leaked version linked out below, but we've added a new link for the tweaked version with Google Now integration.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.