Roughly six months after emerging from stealth, AR cloud company 6D.ai is now ready for public consumption, and it has a big name partner to help it kick off its platform.

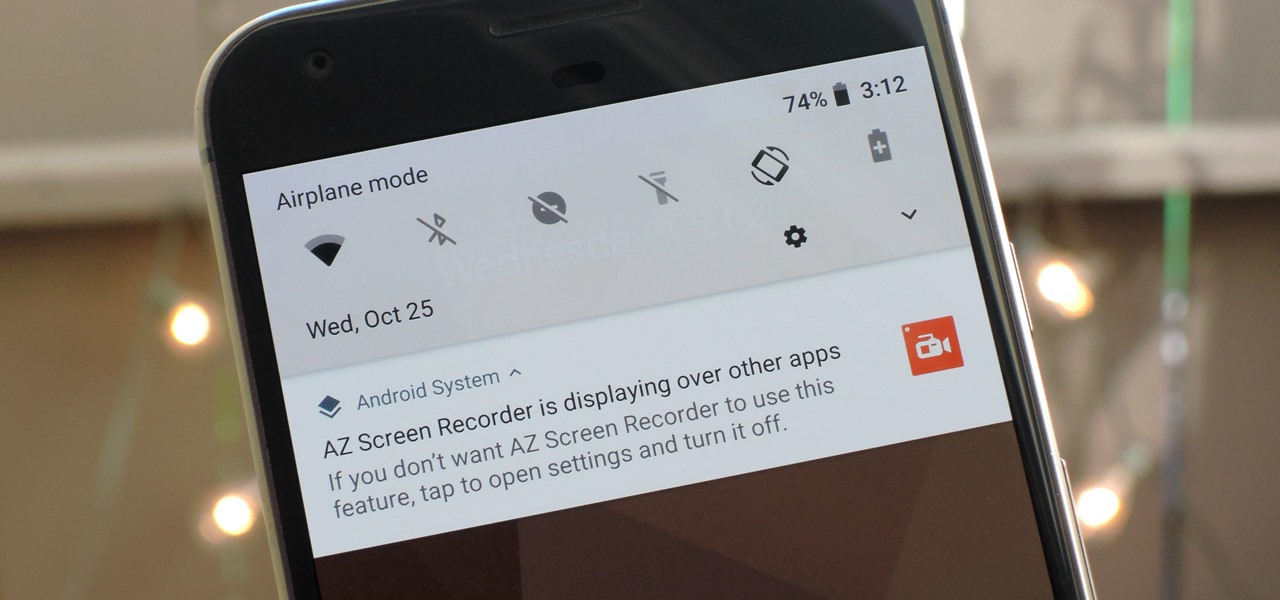
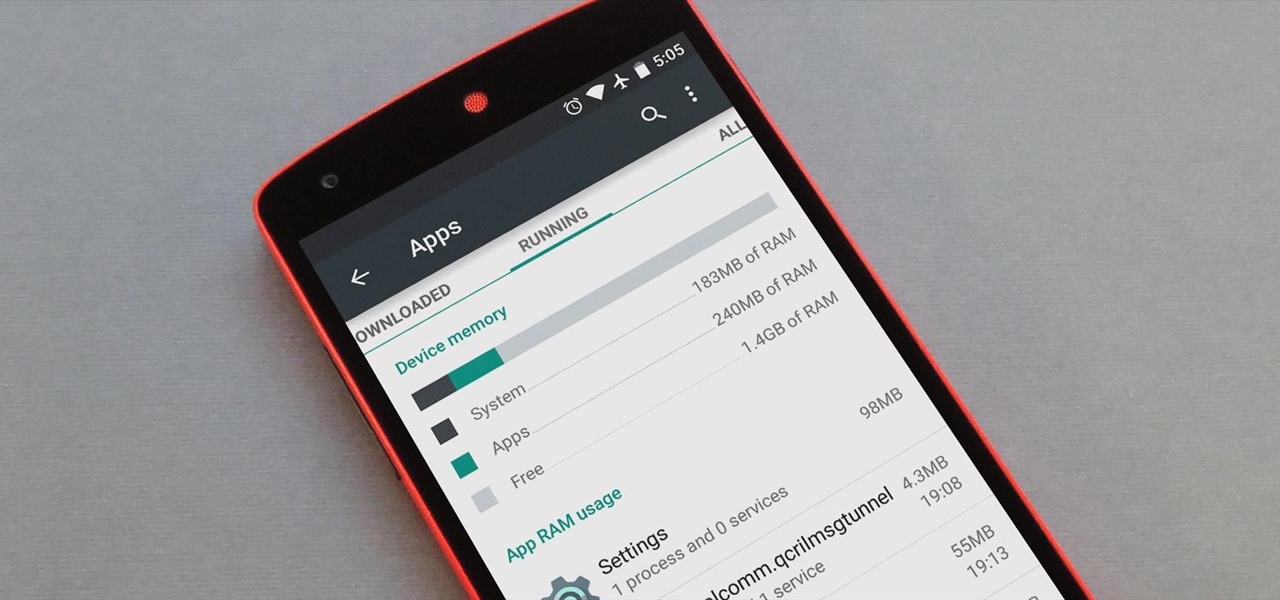
All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

One of Android 8.0's central themes was battery improvements. Google implemented background restrictions and a few other under-the-hood changes, but the biggest battery-saving measure was almost user-hostile: A static notification that tells you when any of your apps are running in the background.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

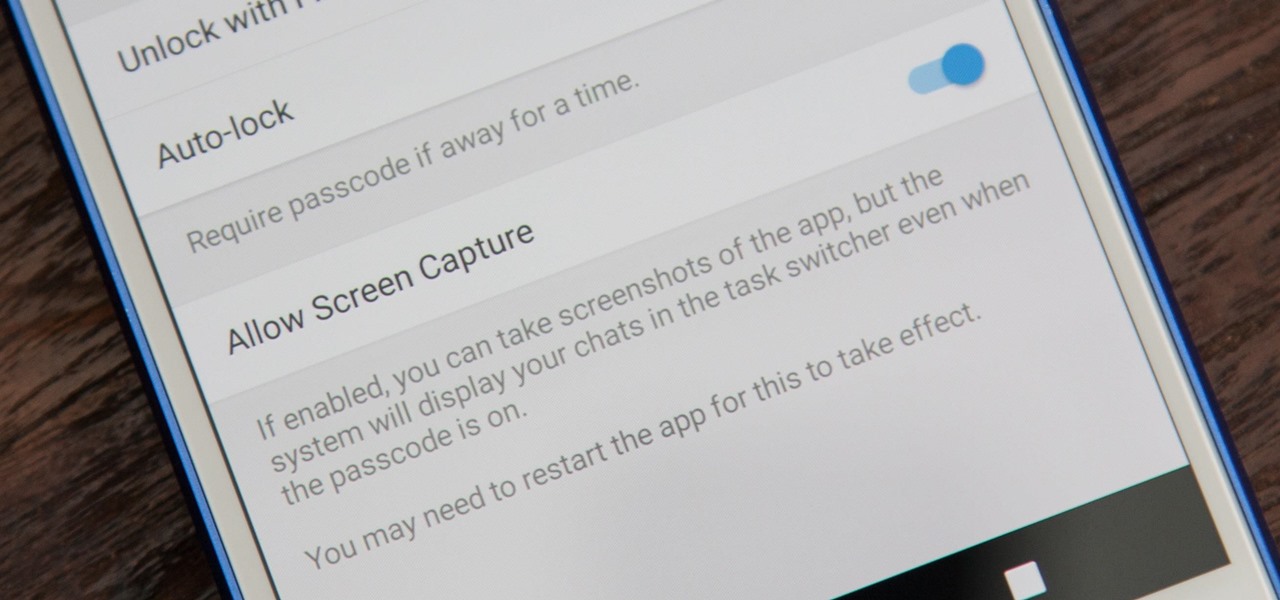
While it's easy enough to take a screenshot of an end-to-end encrypted Telegram chat thread using an iPhone, it's an entirely different story on Android phones. Telegram disables screenshots for Secret Chats by default on Android, and not everyone can turn it on.

Final Fantasy XV, the latest release in the long-running Final Fantasy franchise, has been a massive success, shipping around 6 million copies worldwide in less than two months. Final Fantasy XV: A New Empire is a mobile game based off this popular console iteration, and has surfaced in New Zealand for download.

Jam City's Panda Pop was a great success that helped millions of users waste vast amounts of precious time with its bubble-popping panda cuddliness. Not wanting to mess with success, Jam City has now simply re-skinned the game to feature all the beloved characters from Charles Schultz's timeless Peanuts universe, complete with its relaxing soundtrack and a new name—Snoopy Pop.

Video: . This video will show you how to connect the positive and ground wire on the battery of your RV or camping trailer.

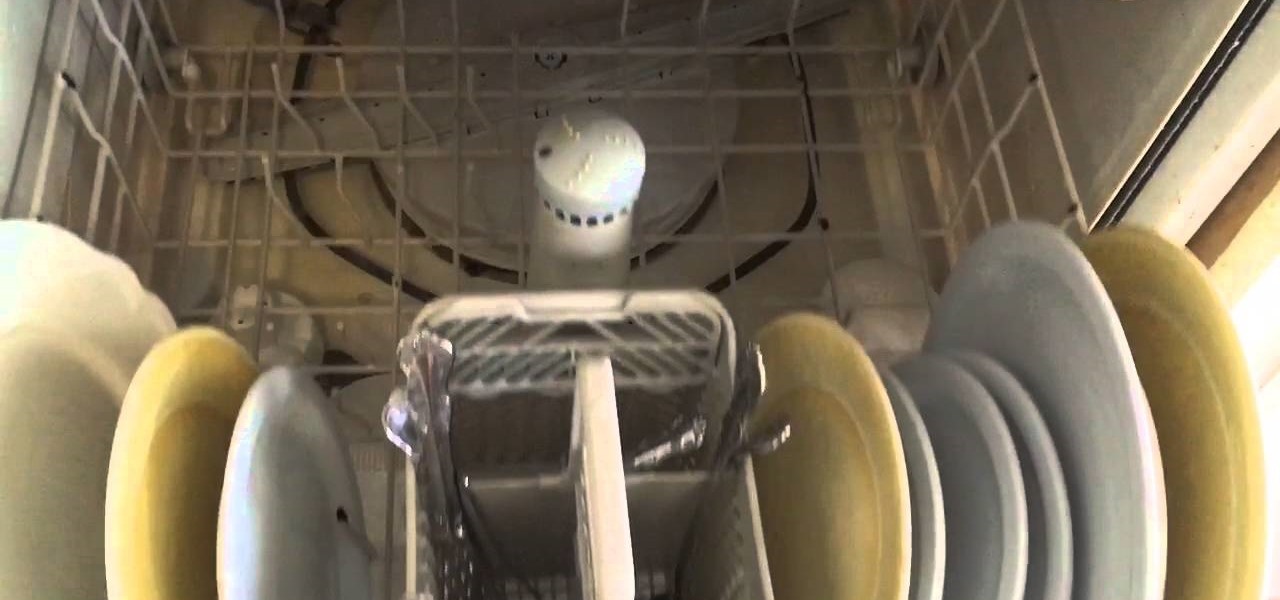
This video will show you what to look for if you dishwasher stops turning on or filling with water.

Let me share some great information on stair climbing and how it can provide many health benefits. Burn more calories stair climbing that jogging or running. See how in the video. If you enjoy the video and would like to see more, please hit the subscribe button. I hope this helps!!

Hello NullByte! This will be my first How To series.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

This ship is over 4 ft. long with many moving parts all run from a live steam engine. There are two videos, one more detailed about the story and one blog showing how it was built. Hope you enjoy.

Android version 5.0 Lollipop introduced a ton of changes to the OS—and of course with new features, there's always a new set of bugs. One of the biggest bugs of all was a massive memory leak caused by the new screen-off animation, which loaded its assets into memory but never cleared them away.

As is the case with most software updates, Android 5.0 brought changes that were viewed by users as somewhat positive and somewhat negative. This generally happens because we're accustomed to the old way of doing things, and changes, no matter how useful, can slow us down.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

When Yosemite was released, a more detailed boot screen came to your Mac. So now, just like on Apple's mobile devices, you will see a loading bar telling you how far into the startup process you are. Apple also decided to add a black version of this boot screen to newer Macs, leaving those of us who purchased a computer before 2011 out of the loop.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

Linux may not be the most popular consumer operating system out there, but what it lacks in consumer app variety, it definitely makes up for in flexibility and security. And if you've ever tinkered with a Linux distro, you know how easy they are to install—most of the time, I skip standard installation and boot directly from a CD.

This video will show you handy tips and tricks about Google search engine. These tips will help you to speed up your computing or browsing experience. This video contains tricks like Search by location, Filter image search, how to see sites that aren't online, movies running in a city theaters etc. This video is the 2nd part of the serial. You could also watch the part 1 here vimeo.com/104089915.

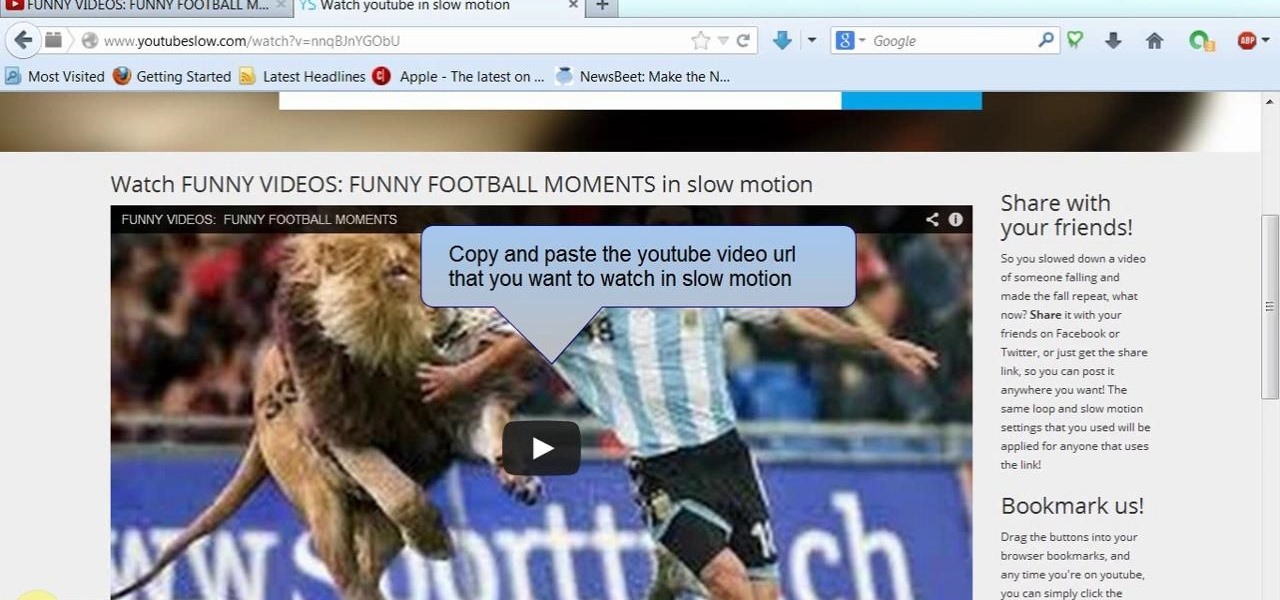
This video will show you how to watch YouTube video in slow motion as compared to normal speed. You could reduce the speed of a YouTube video to .25, .50. You could also make a video run faster than normal speed. So please watch the video and employ it in your computer.

A full run down of how to grow all the crops in minecraft Video: .

Video: . Ever had a bad hair day and didn't know what to do with it? This video shows you how to quickly do something cute with your hair especially if you're running out of time.

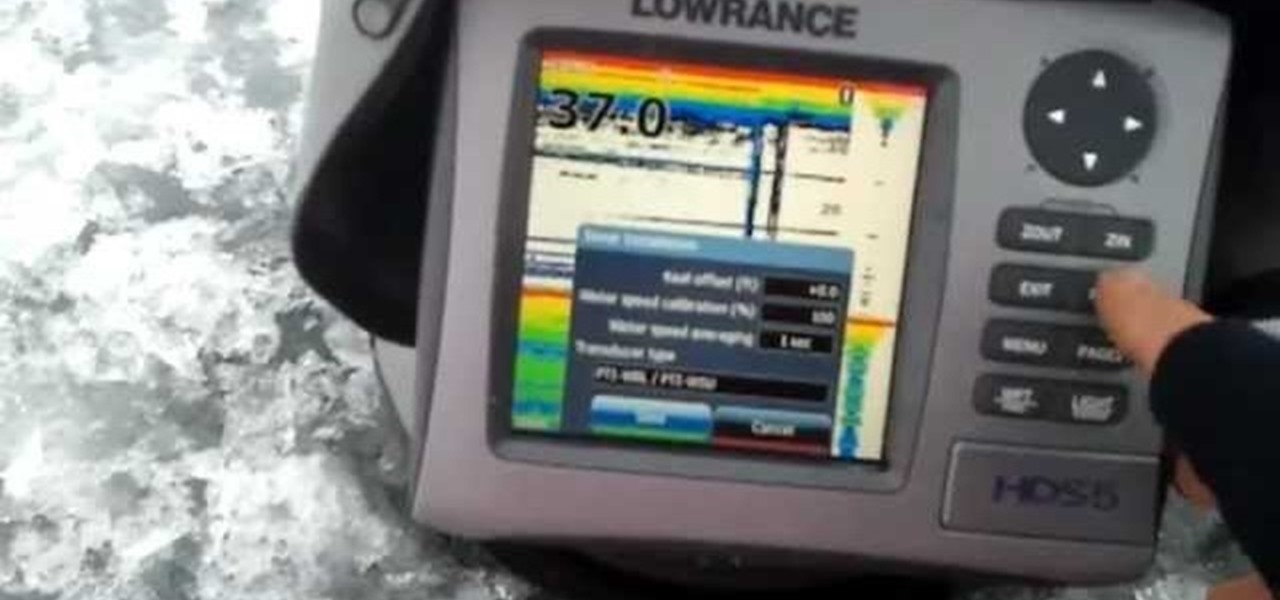
Video: . This video shows you how to set up your Lowrance unit to optimize it for ice fishing. This will also apply to Lowrance Elite and Mark series units as well as the X-67c Ice Machine.

With AirPlay for iOS, Chromecast Screen Mirroring, and even third-party PC-pairing apps to play around with, getting your devices to interconnect could not be any easier than it is today.

Not much work goes into setting up this pen prank. You will however need to get some party snaps and you will be loading the pen with a one or two.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Here's a quick easy way to quiet down a loud squeaky hamster, mouse or gerbil wheel. This will enable you to finally sleep at night!

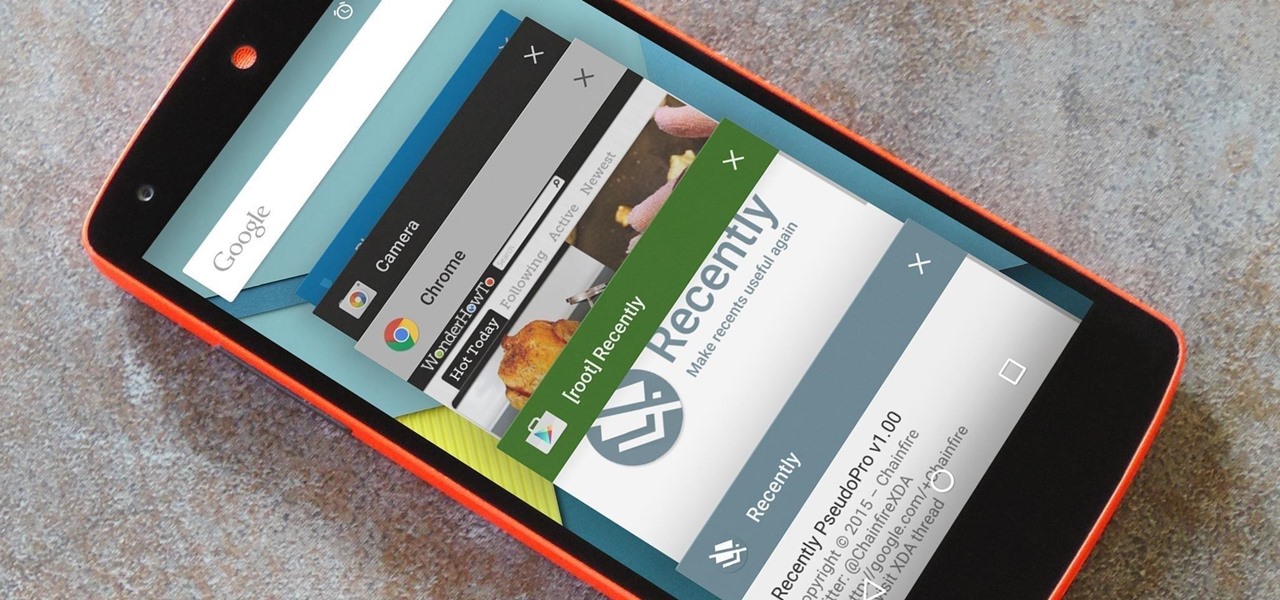
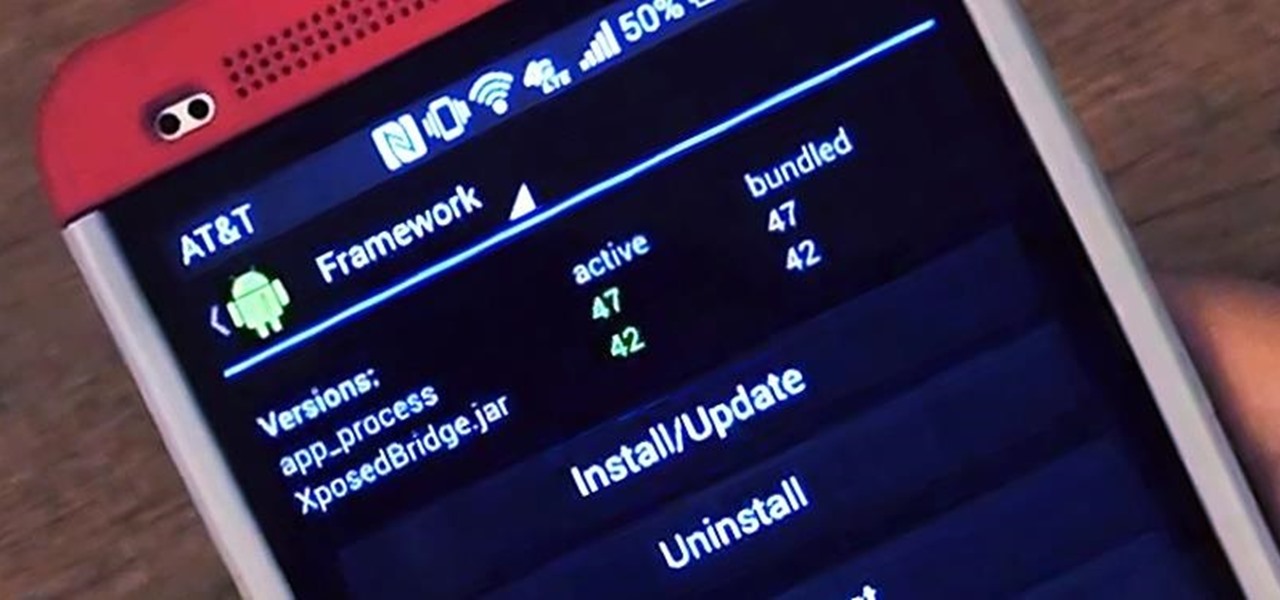
There are plenty of ways to customize your stock HTC One (or any Android device), from playing retro games to adding rotating live wallpapers. But to get the most out of your device, you need root access.

Is the water dripping or running in your bathtub shower? This video will show you how to remove and replace the shower valve stem and also how to replace the seal that on it. Usually the seal deteriorated over time causing your shower to leak.

This video will show you how to bleed the air out of the burner oil line on your furnace if you run out of oil. Shown on a Carlin EZPro burner, Weil Mclain Gold boiler. Also would work on most burners the same way including a Beckett.