Just yesterday, Google announced that it is banning all apps that contain any form of lock screen ads. Today, they posted a list of the Best Apps of 2017 for the Play Store. Given the new policy of cracking down on apps with advertisements on the lock screen, you wouldn't expect to see one of those in the list of top apps. Unfortunately, that's exactly what happened — Google is promoting obvious adware in their list of best apps.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

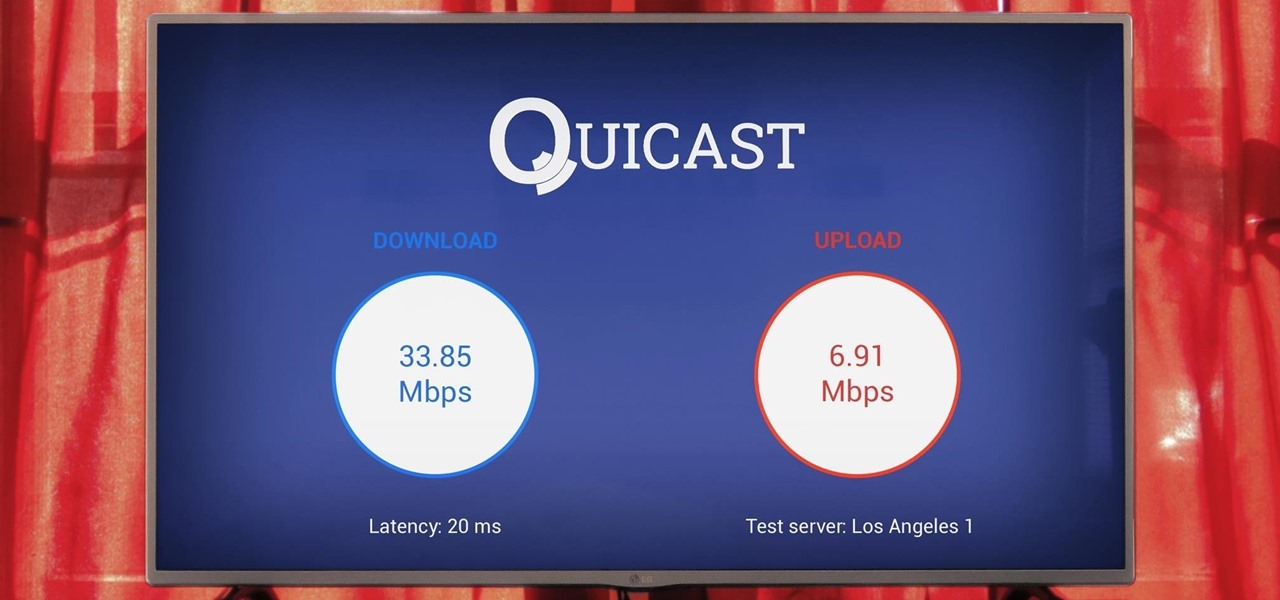
A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.
We've been running the Essential Oreo Beta on our PH-1 over the past week and compiling a list of important changes. If you're interested in getting the Beta yourself, we even put together a quick guide on how to do that. Now that we've ran down the best new features, let's take a look at all of the bugs and performance issues in Android 8.0.

The release of Into the Dead 2 has given fans of the zombie bashing genre a fresh game to enjoy, but it's also given us the opportunity to revisit our roundup for the best free action games for mobile. Not only did it replace its predecessor in our charts, it managed to surpass it. Here's what made the game shine through.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Though not quite as agile as the world famous plump plumber Mario, Toad, the lovable fungus, is still one of the most fun characters to use while playing Super Mario Run. Thankfully, he is also by far the easiest character to unlock in the game, requiring no special tasks to complete.

Supercell's highly anticipated Brawl Stars has soft launched in Canada, with gamers worldwide salivating at the prospect of a full debut around the corner. Unbeknownst to many, this game can be played on your iPhone right now, regardless of where you live.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

The latest iteration of the gaming classic, The Sims, has arrived as a soft launch for both iOS and Android in Brazil. Aptly named The Sims Mobile, this free-to-play game seems to be very faithful to the PC-based version that won it so much acclaim. There are plenty of things to do in The Sims Mobile besides the usual home and character customization, and the game also lets you interact with real life friends to fully experience its virtual world together. Maintaining relationships, whether r...

Prison Architect, the BAFTA winner for the Best Persistent Game in 2016, has finally soft launched on iOS. Originally a PC game, Prison Architect lets you build and maintain a maximum security prison. Comparable to running a small city, the game has you manage an ever-expanding correctional facility and contend not only with violent offenders and ever-present prospect of a chaotic riot, but also more mundane affairs like balancing the prison's budget and employee payroll. In addition to the s...

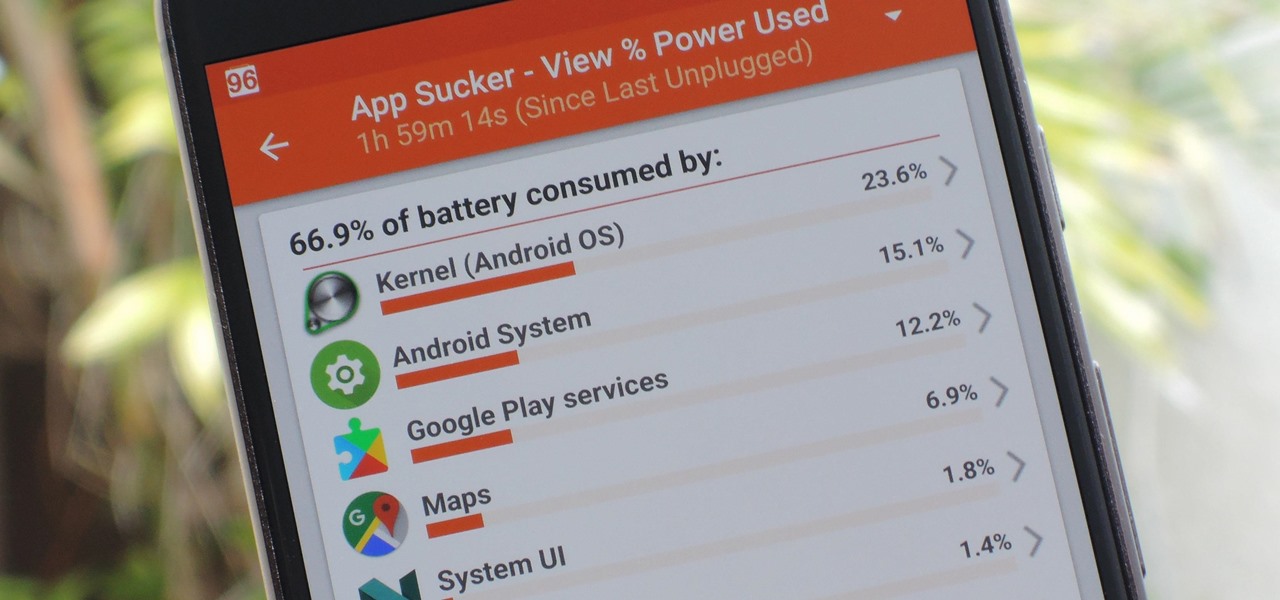
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.

Fans of rhythm tap games and traditional one-on-one fighters finally have something to bring them closer together. DuelBeats, a fighting game that lets you perform moves by tapping to the beat of a song, has been released as a soft launch for both iOS and Android in New Zealand, Australia, and Singapore. Just because the game is exclusive to those regions doesn't mean we can't try it out for ourselves, and with a little hackery, it's entirely possible to do so.

It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

The Autobots and Decepticons are back as Transformers: Forged to Fight has soft-launched for both iOS and Android. Help Optimus Prime fight corrupted Transformers one on one to save them from their ruthless overlords, and have them join your cause, regardless of which side they're on. Collect, control, and level up unique robots from the entire Transformers universe, including the classic TV animated series, movies, comics, and toys.

A new Windows Insider Preview, version 15055, was released on Friday, March 10. Along with the normal collection of bug fixes and new features came a secret addition to the Mixed Reality Portal in the update. Windows Mixed Reality, along with Cortana, can now teach you how to use the platform, and, hopefully, usher in with it some understanding of what mixed reality is.

Anybody who was around in the '80s and '90s associates Sony with music still to this day, thanks to their wildly successful Walkman brand. And that's not even mentioning their major label record company. Indeed, the Tokyo-based electronics maker/media conglomerate has music embedded in its DNA, and that's certainly noticeable in the stock Music app included with their Xperia phones.

DAQRI, a company mostly known for its odd but fun-looking industrial Smart Helmet, unveiled their new Smart Glasses product at CES 2017. Their smartglasses look like a strange attempt to answer the Microsoft HoloLens, and the price tag of $4,995 for the developer's edition reinforces that notion.

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

Thanks to Project-Infrared, there's now a pretty straightforward way to add motion tracking to the HoloLens: Connect it to a Kinect.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

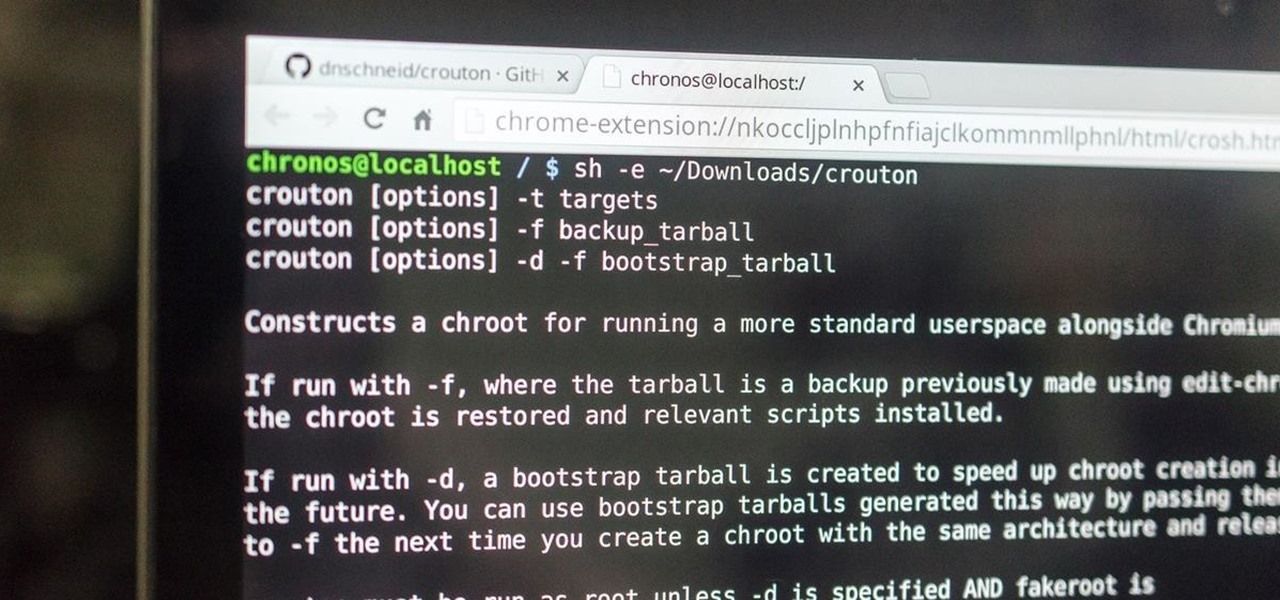
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.