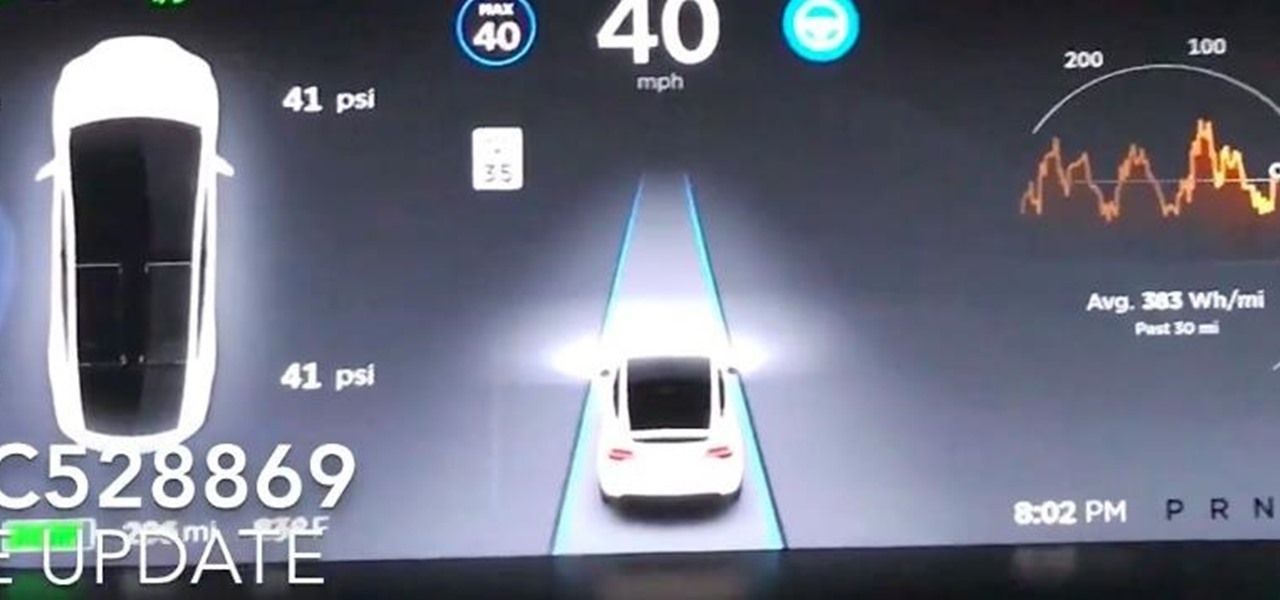
Some drivers give Tesla's Autopilot update released this week rave reviews, after version 8.1 has taken longer than expected to live up to Elon Musk's "smooth as silk" Tweet from earlier this year.

While it might be a little past its prime now, the running gag about Nokia phones never breaking was one of the internet's favorite jokes. "If you buy one," they would say, "you'll never need another phone again." I think if those users could see into the future, they'd change their tune, as the Nokia 6 is now available to preorder — and I'm guessing it would give any of Nokia's old bricks a run for their money.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

The Nokia 6 has been out since January, releasing in China before having a slow trickle of releases throughout the year. Despite announcing a global release, the United States never received a street date for the smartphone, and for all this time, Nokia has left us out to dry. Now, it seems, their phone could be on its way as the 6 has received its FCC certification.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

With all the hype surrounding the recent Galaxy S8 release, it can be easy to forget Samsung makes other smartphones. But let's be real here; $726 isn't cheap. If you're someone who doesn't want to drop that kind of cash on a smartphone — or who doesn't feel your device needs all the bells and whistles that come with Samsung's premium line — the new J3 Prime might be right for you.

In this Tuesday's Brief Reality report, there's a trio of stories from the healthcare world where augmented reality is helping out with surgical microscopes, asthma treatment, and other diagnostic and treatment tools. There's also something for all of you AR/VR storytellers out there.

The Galaxy S8, with all its new features, is shining in the news right now as one of the best phones of the year. However, users in the US may be at a disadvantage to those overseas, as it seems that the Snapdragon 835-powered S8 models underperform variants with Exynos processors in almost every category.

Last month, Google introduced the Family Link app. This app, much needed in a world where the average age of kids first getting a smartphone is just over 10 years old, allows parents to set some limits on their children's phone usage. However, the app premiered with one caveat: Both the parent and the child had to have an Android phone. Now, Google has updated the app so it works on iOS devices.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

In case we haven't beaten the '90s revival to death enough, now Nokia is coming back to the US market. The three Android midrange devices that made their debut at Mobile World Congress last month are set for a global release, meaning they will also make their way stateside.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

Matteo Pisani, CTO and co-founder of Remoria VR, has managed to do something the folks over at Google said couldn't be done for at least a couple of years. With a little bit of tinkering, Pisani was able get his Google Daydream VR headset and remote to work on an iOS device.

By default, Android limits your call history to the last 500 incoming, outgoing, or missed calls. When you reach this limit, older entries get trimmed off the bottom of the list and deleted forever. This isn't an issue with storage space, because even the biggest call logs only occupy mere kilobytes, so it's really just an artificial limit.

Ready to finally play some Pokémon on your HoloLens? Here is your chance! KennyWdev has released a video showing off his newest build of PokéLens, a Pokémon clone for the HoloLens similar to Pokémon GO. In the video, you get to see two Pokémon battle it out on what appears to be an office floor. Apparently, Pikachu is "super effective." This coincidentally appeared online the same day that another developer, Sky Zhou, showed off his Smash Brothers-style Pokémon game.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Google's new Pixel and Pixel XL smartphones are available for pre-order right now, but the general public won't start to get their hands on these devices for another week or two. Tech reporters got some hands-on time at Google's launch event on October 4th, but camera testing wasn't allowed, and the Wi-Fi coverage at the event was too flooded for real-world performance reviews.

People fear virtual reality will isolate us, but the right experience can prove it does the opposite.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

If not the future of computing in general, augmented, virtual, and mixed reality certainly will change the world of gaming. If you want to try your hand at shaping this evolved medium, the Unite Europe conference posted a talk that explains the first things you need to learn to develop holographic games.

The latest beta of the popular open-source media player VLC just hit the Windows Store, which means it not only runs on Windows 10 and Xbox One, but the HoloLens as well.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

The world's first cloud-oriented smartphone, Nextbit Robin, is now available to the masses via Amazon with free one-day shipping for Prime members.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Here's a not-so-well-kept secret about the food industry: retailers love to take your money. And one of the ways they do that is by dividing food into smaller sizes and charging more. Have you ever noticed that a container of precut, washed broccoli costs more than a head of broccoli with the same amount of florets and stems?

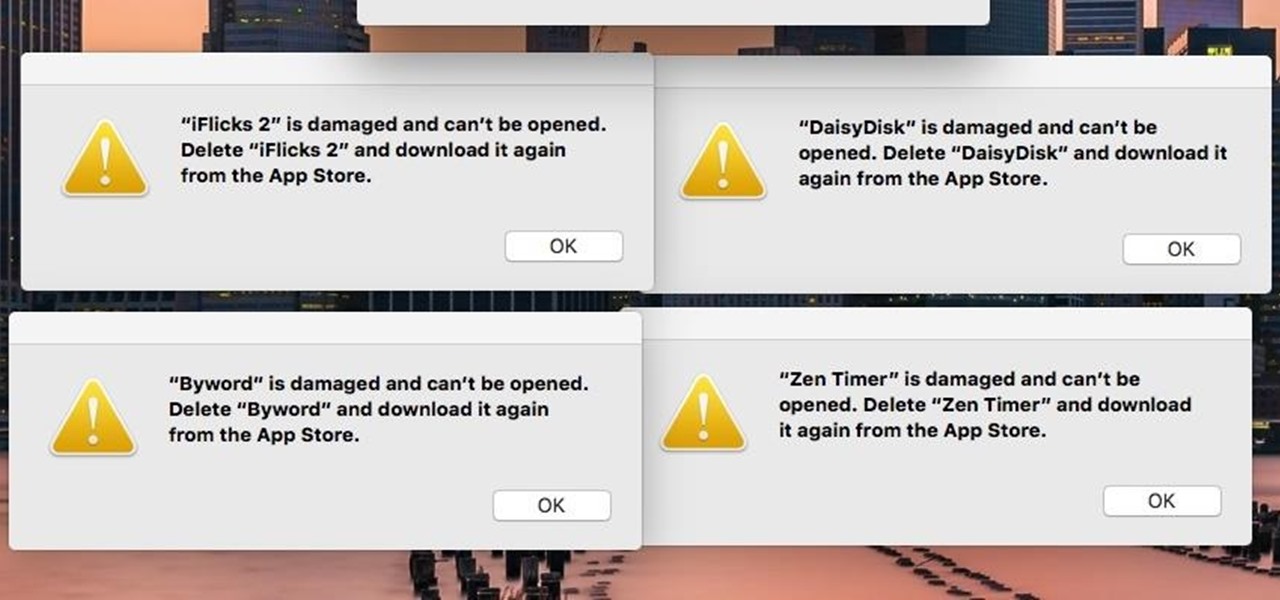
If you're seeing "damaged" apps on your Mac, you're not alone. A huge digital rights management blunder in Apple's Mac App Store on Wednesday, November 11th has rendered some apps unusable. When opening certain apps, the following message could be displayed: