Augmented reality seems to come into its own in museums, where audiences are ready and willing to try out new immersive tech. Now, that tech-powered palette is about to get a little larger.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.
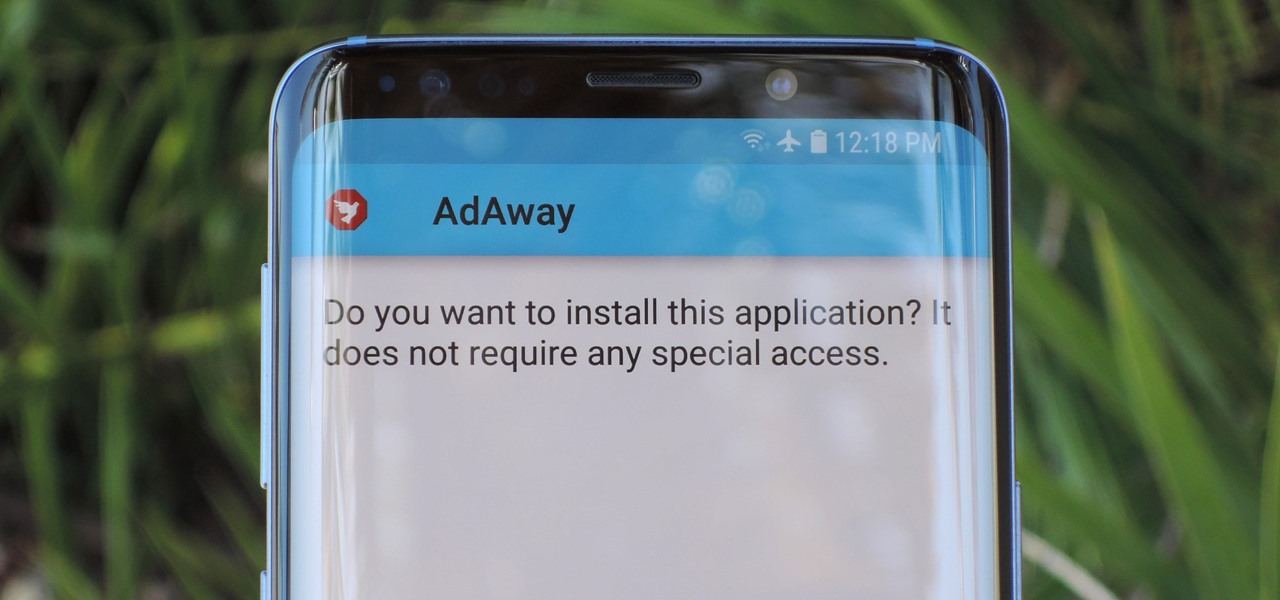
Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.
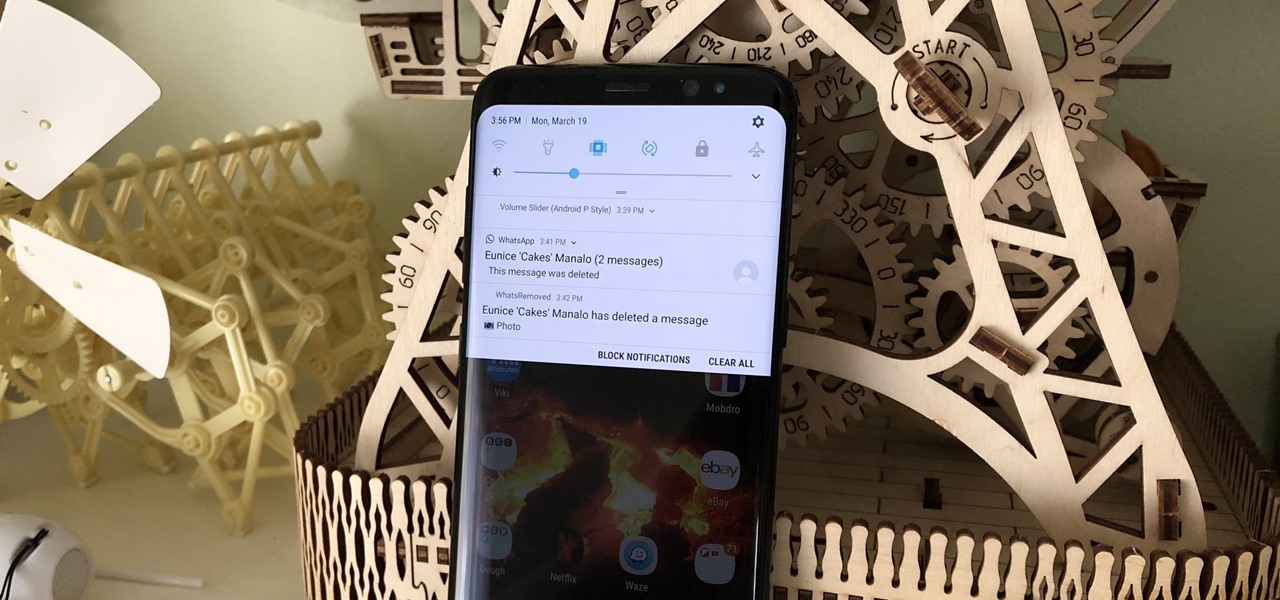
To help keep potential drama at bay, WhatsApp lets you delete questionable messages before the other person even sees them. If you're on the receiving end and you're curious about the deleted text, however, there's an Android app that lets you view erased messages.

Since its introduction, the Bixby button has been a big point of contention among Galaxy fans. Many view the dedicated button as a wasted opportunity, which they argue could be put to better use if Samsung would let them use it for other commands. Thanks to an awesome app, you'll be able to remap the Bixby button on your Galaxy S9 to perform almost any function.

The beta firmware for OnePlus devices lets you record calls from the stock Oxygen OS dialer, but this feature is never included in official updates. This is likely due to legal issues with recording calls in some jurisdictions, but thankfully, there's a way to get this feature without having to run beta software.

Depending on your device, when you lower your brightness slider all the way to the minimum, it may still emit a considerable amount of light. This is because manufacturers have the option of setting a minimum brightness value, and while 1 would be the true minimum brightness that your display is capable of, some have set is as high as 5 or even 10.

Over a billion people use WhatsApp, which makes it the most popular standalone messaging service out there. But if you're one of the many people whose group of friends relies on WhatsApp for all communication, chances are, you have several years-long messaging threads with all sorts of random pictures and GIFs cluttering up the place.

Several Samsung phones have a feature that turns the screen black and white when the battery is getting low. This takes advantage of the AMOLED display in these devices, because unlike red, green, and blue pixels, no battery power is used to display black pixels on this type of screen.

When Android Nougat is released sometime this fall (or sooner), a new feature called "Quick Reply" will allow users to respond to incoming text messages directly from the notification. It will definitely be nice to carry on a conversation without leaving the screen you're currently viewing, but unfortunately, most of us won't get that Android Nougat update for quite some time.

The Google Now gesture included in the Google Now Launcher and on Nexus devices isn't something I regularly utilize, and you might not either. There is a way to disable it, which is a good idea if you were executing it accidentally, but what's even better than disabling it? Repurposing it!

If you've ever used a custom ROM on one of your devices, chances are it had a built-in feature that allowed you to kill any app by long-pressing the back button. This function comes in handy quite often, especially in situations where an app is acting up, since it stops all associated processes and clears the app from memory.

Electrical sockets are often taken for granted. It's not until one of them breaks or stops working and our laptops won't turn on that we truly have a crisis (mostly over lost internet time).

These days you can get a car tailored with special gangster rims, headlights, and sound systems, but one of the features of a standard car we all take for granted is power windows. Before those, all we had were frustrating crank-up windows that always got stuck if we didn't add enough elbow grease.

Dear the future Mrs. Brand: Can we be you? You're hot, one of the boys, can rock an olie like no one's business on the skateboard, are a ginormously popular pop star, and you're super funny and intelligent.

Cooking chicken tonight for dinner? It may be a dinnertime staple in your home, but you're probably used to store-bought chickens that you store in the freezer. Well, sometimes the best tasting poultry comes from the chickens with their heads still attached… well, at least before you behead it. We're talking fresh meat here, not Kentucky Fried Chicken.

Learn how to make an e-mail server on your home computer to host your own web page and webmail service by following the steps outlined in this video tutorial. You will need a web server, an e-mail server, and a webmail interface. For the server, the most common program is WampServer, which you will need to download. Run through the installation process and grant the program access to your fire. Click on the new icon on your desktop and click Put Online and then Start All Services. This will g...

Your Galaxy's lock screen already lets you know there's no SIM card installed if it's missing on your device, so there's really no need to have a persistent icon for it on the status bar. If you want to hide the pesky symbol and accompanying notification for good, there's a nifty app you need to check out right now.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

Up until now, enabling full-time Immersive Mode on an Android device has been a tedious task which required you to run individual ADB commands each time you wanted to toggle it on or off. This was a shame, too, since Immersive Mode helps reclaim lots of screen real estate by auto-hiding your navigation and status bars.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

Normally, your sound settings only let you change up a few of the sounds on your device—generally your ringtone and default notification sound. While some developers include the option to choose custom notification sounds within their app's settings, most of the time you are left with an ambiguous ringer for everything—not very helpful for identifying what app that alert just came from.

In this next tutorial, you'll be finding out how to perform a terminal double hack in the game. This is pretty difficult to achieve, but will give youa shot at double credits.

This is a video games tutorial where you will learn how to connect your Nintendo Wii to the Internet wirelessly. Select ‘Wii’ and then ‘Wii settings’ menu and choose ‘internet’ and ‘connection settings’. You have three settings to choose from. Choose any one and then select ‘wireless connection’ -> ‘Nintendo Wi-Fi USB connection’. Install the Nintendo Wi-Fi USB connector software on your PC and then insert the Nintendo Wi-Fi USB connector into your PC. Choose ‘next’ to continue. Use the regis...

In this video tutorial the instructor shows how to enable usage rights for Adobe reader. She begins by showing a multiple page PDF which can be viewed by anyone having a Acrobat reader. She goes to advance menu and chooses the option of expand features in Adobe reader. She says that by granting these rights in Adobe 9, we can let other people write into the forms of the document, comment it and even sign the document. Now she applies the features and saves the document to the desktop. Now she...

This is a walkthrough of Halo Wars so you can beat it before your friends do. This is the first chapter of Halo Wars for XBOX 360. Check it out, a cheat walkthrough from Mahalo Gaming.

Check out this Halo Wars walkthrough. It will help you beat Halo Wars before all of your friends. This is a 3 part series for XBOX 360 from Mahalo Gaming.

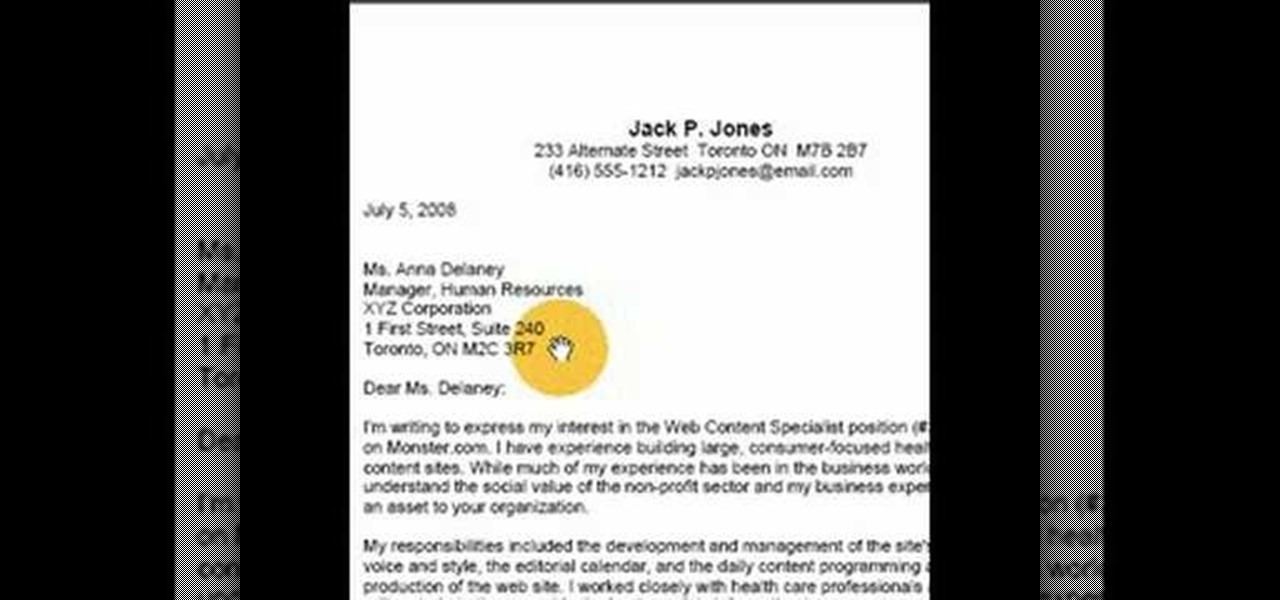
This video goes over cover letter formats, specifically in Full Block Style. Cover Letters accompany resumes in job applications. They should be sent ahead of the resume. They go over your experience, desires and objectives. The cover letter is important to both employers and employees. A human resources or HR department often receives thousands of letters that it must review before granting a job candidate a job interview or even reading their resume. This is a LIAD Production for World of W...

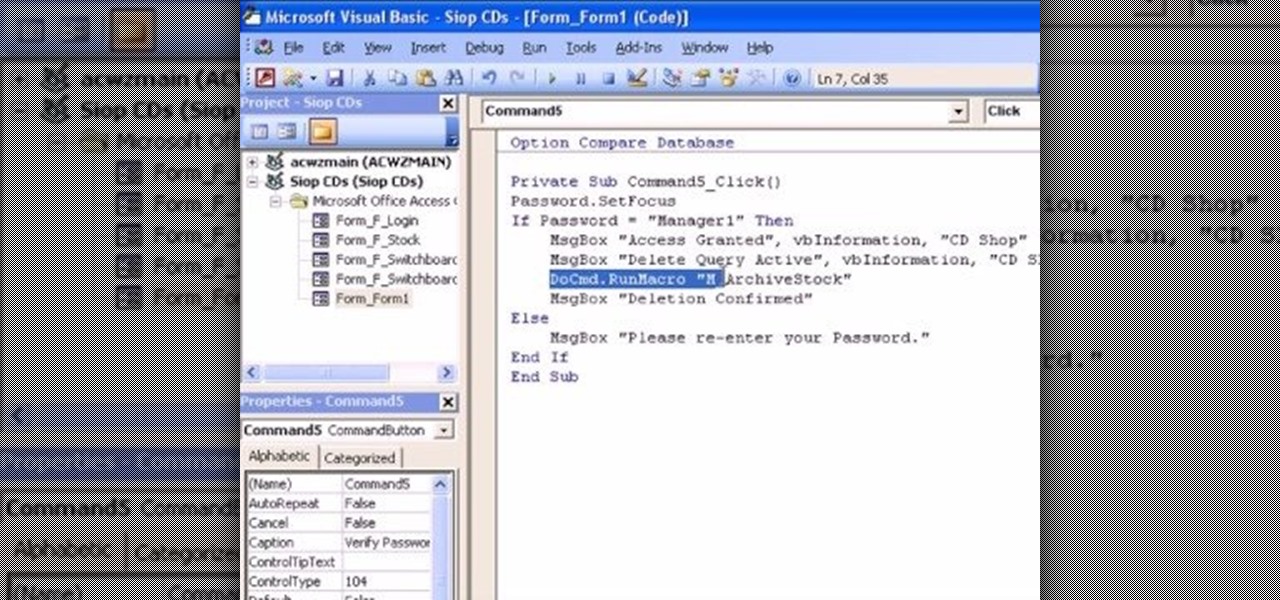
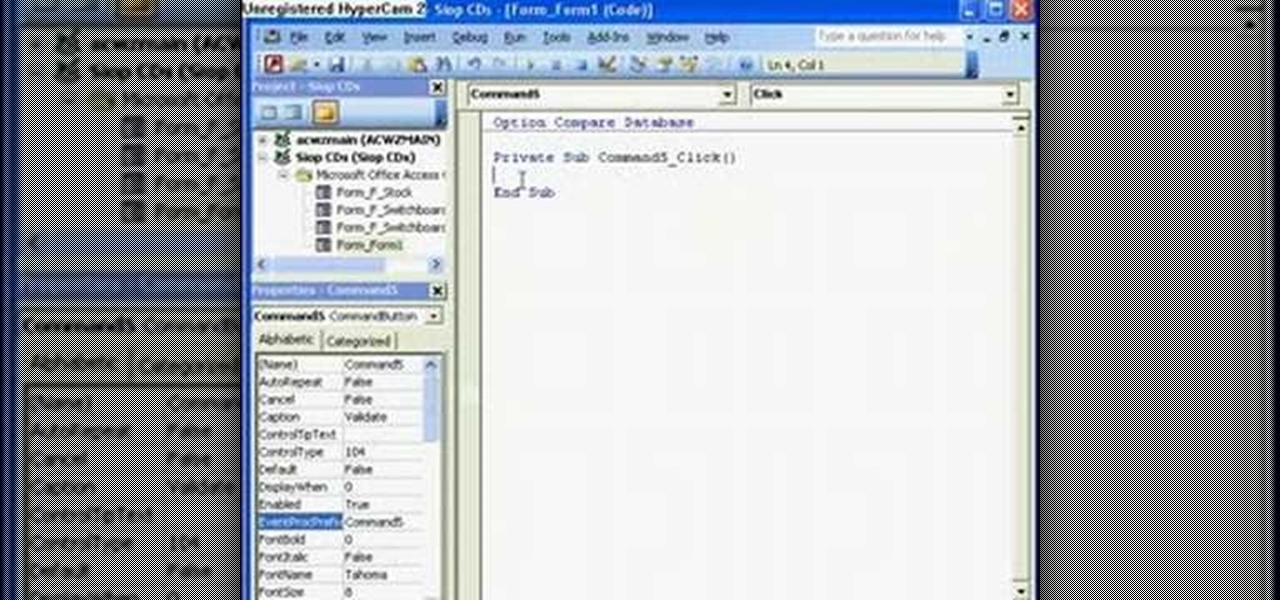
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn how to force a password to be entered in order to run a query.

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a login form and password protecting your database.

The sun-drenched people of Phoenix can now sign up to ride in an automated car, for free, courtesy of Waymo. The Alphabet affiliate announced its "early ride program," which will (hopefully) demonstrate how self-driving cars will fit into people's everyday lives. Highlighting a challenge Nissan CEO Carlos Ghosn has spoken about that faces the driverless industry.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the ‘Start’ button and then click on ‘Run’. In the small window, type in ‘cmd.exe’; this then opens a black window. Then type in ‘ping’ and the website; this gives you an address that you type in directly to your web browser, granting you access to a normally blocked website. This comes in very handy when you are in such locations like schoo...

In this scientific video tutorial, undergraduate students in a forensic chemistry lab demonstrate a forensic DNA test to catch a criminal. Learn how to perform a forensic DNA test! Just like in CSI.

In this scientific video tutorial, undergraduate students in a forensic chemistry lab demonstrate how to perform gunshot residue analysis (GSR). Learn how to perform gun shot residue analysis (GSR)! Just like in CSI.

In this scientific video tutorial, undergraduate students in a forensic chemistry lab demonstrate how to use a comparison microscope for bullet and bullet casing comparisons, and color developments tests for impression marking enhancement (such as for filed-off serial numbers). Learn how to perform ballistics comparisons! Just like in CSI.

In this scientific video tutorial, undergraduate students in a forensic chemistry lab demonstrate how to develop fingerprints using a variety of methods: Cyanoacrylate (superglue) fuming, dusting, and iodine fuming. Learn how to dust for fingerprints, just like on CSI.

Make your gadgets magnetically controlled with everyday things. People often take for granted the common items and devices they use in everyday life. Looks can be deceiving. It's not what things appear to be, it's what they can become.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.