Blizzard's Hearthstone was a rousing success with more than 10 million downloads on the Google Play Store. Not taking things lying down, Bethesda, the creator of The Elder Scrolls, has come up with a card game based off its popular fantasy franchise. The Elder Scrolls: Legends is now out in the wild, though, officially only available for select Android tablets. But with a little creativity, there's a way to game the system and play Legends on any Android device. The Elder Scrolls: Legends is ...

Facebook is aware that Snapchat is killing the social media game amongst the youths, which makes sense, because in 2017, video is king in social media currency. Facebook has continually shown that Mark Zuckerberg and crew seem to think the best strategy to keep up is to simply copy them.
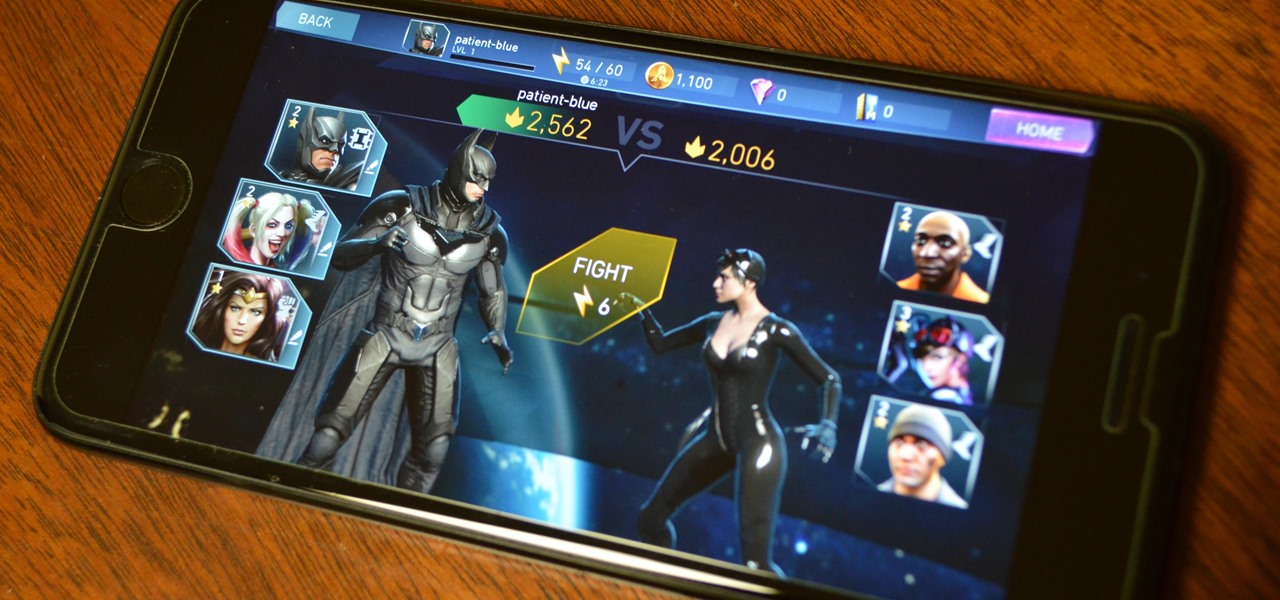
Based in the DC Universe, Injustice: Gods Among Us was a runaway success on the iOS App Store, generating enough downloads to rival its console-based iteration in terms of popularity. But now, the sequel to this long-running game, Injustice 2, is finally out in the wild, as it was soft-launched in the Philippines this past February.

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

With the Game Developers Conference (GDC) in San Fransisco just a few weeks away, Microsoft Senior Program Manager Vlad Kolesnikov has announced via Channel9 (Microsoft's developer news outlet) that not only will new low-cost virtual reality headsets be coming in March to developers, but that they will be at GDC, too.

Being able to take screenshots on Android isn't something we were always able to do. It was added to stock Android in Ice Cream Sandwich 4.0 (Gingerbread 2.3, if you were a Samsung TouchWiz user) as a simple full screen screenshot, and that's the way it's remained ever since—until now.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

We like to have a variety of cupcakes on hand when we're entertaining, but we don't want to spend too much time making separate recipes. No one has the time or the money for that—especially when you're hosting and you've got a bevy of other dishes to prepare.

We love a good bowl of punch just as much as the next partygoer. But you don't want to be the one to make his or her way to the bowl after all the ice melts and turns that beautiful beverage into a watery wasteland.

Sometimes the idea of cooking fish, especially for a group of guests, can be intimidating. There's the fear of the fish not cooking right, or sticking to the pan or grill. And even if you cook it right and the fish doesn't stick, you're left with the inevitable fishy-smelling cleanup. Not fun!

Step aside, Heinz: there's a new ketchup in town. Beetroot ketchup is the rising star of condiments. It's a vibrant, earthy, and sweet topping for summer BBQ burgers and grilled hot dogs, as well as a pretty un-beet-able dip for French fries. There's no corn syrup, it's paleo-friendly, and the beets give it a bright, bold flavor like no other sauce you have ever tasted.

Ah, the sensation of that first bite of sorbet in the heat of summertime: icy, refreshing, decadent in flavor and texture. We love sorbet almost as much as we love ice cream, and making it at home is actually pretty simple. Most recipes call for just water, sugar, and a base fruit of some sort (like strawberries or watermelon).

We've both had a fondness for pancakes since we were kids; The way the smells of syrup and warm batter permeated the kitchen and lingered for hours drove us crazy—and still does.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

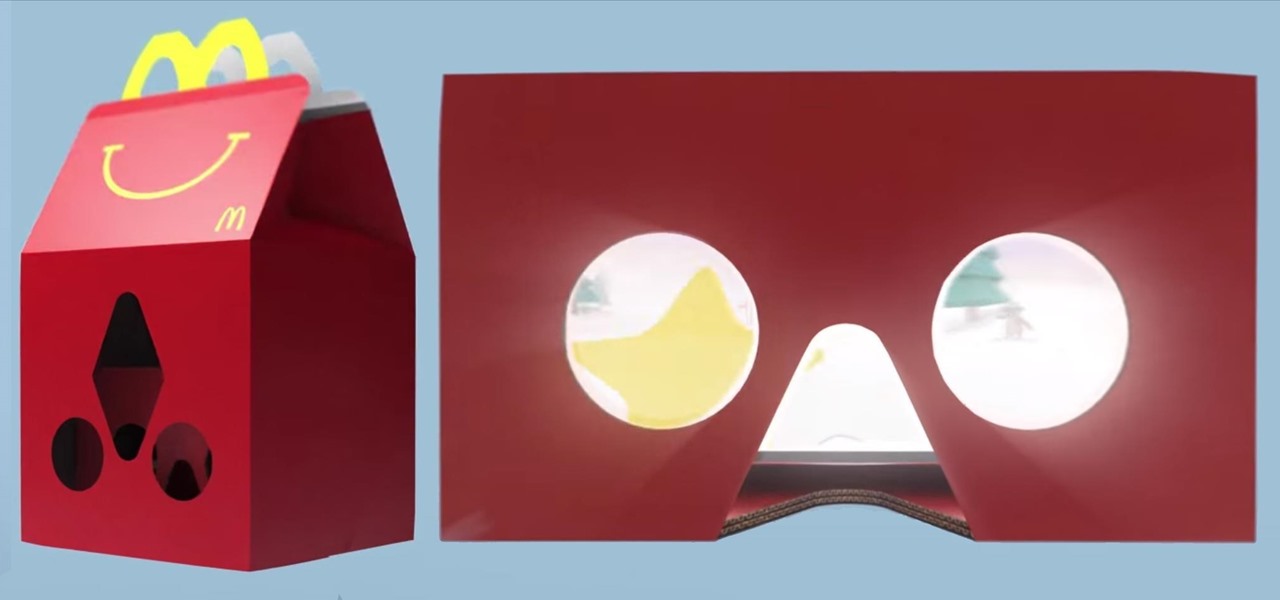
Another day, another company hopping on the virtual reality bandwagon. Today, it's fast food behemoth McDonald's, which is testing limited edition Happy Meal boxes that you can turn into a VR headset by punching out a couple holes and tearing along a few perforated seams. The resulting headset is a lot like Google Cardboard, with the lingering scent of fry grease.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Unquestionably, one of the best parts of Hanukkah is the prevalence of latkes during the 8-day celebration. But even the most dedicated spud fanatic can get a little "latke'd out" as the week drags on. Here are some alternative preparations for latkes that will give you some variety in your celebratory food choices throughout the Hanukkah season.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

There's only one day that can top the aftermath of Easter and its copious amounts of leftover candy, and that is November — the day after Halloween. As you come down from your sugar rush and realize you now own more chocolate than your stomach can physically hold in one sitting ... fear not! Here are several ways to turn your Halloween chocolate into delicious snacks and desserts that you can enjoy at your leisure.

If you own an iPad 2, a 3rd or 4th generation model, or original iPad mini, then you won't be able to utilize the new multitasking elements introduced in iOS 9. Although many iPads can use the Slide Over and Picture-in-Picture features, only the iPad Air 2, iPad mini 4, and iPad Pro have the ability to perform Split View.

At first glance, caviar doesn't seem overly appealing to the masses; not very many people would be willing to spend upwards of $1,000 on a tiny spoonful of salty sturgeon eggs from the Caspian Sea. Caviar truly is the ultimate symbol of luxury and fine dining.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

My French press is one of the most important tools in my kitchen. It's indispensable, and it's no small exaggeration when I say that I use it on a daily basis thanks to my coffee addiction. However, it gets used for a lot more than just my morning cuppa (and my second morning cuppa, and my late morning cuppa, and my... well, you get the picture).

Theming is one of the many facets of Android that gives it a leg up on its iOS competition. With the right home launcher and icon theme, you can completely change the look and feel of your device in just a few minutes.

If you ever need to spice up a party, drinking games can really get things started quickly. The objectives are generally to complete tasks or challenges, but it's really all a thinly-veiled excuse for increasing everyone's alcohol intake in a hurry while testing levels of inebriation.

To be twentysomething is an awkward time for entertaining. As we graduate college and begin to work in “the real world,” there is a yearning to transition from keg parties into dinner soirées. However, though the desire is there, often the bank account is not. Here are some ways to do in the kitchen what twentysomethings do best: fake it until you make it. (In other words, host a fabulous dinner party for four and still be able to make rent this month!)

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

The increased sophistication of smartphones and apps have allowed us the luxury to never leave our homes. Everything from coffee to food to dry cleaning can be delivered straight to your door without ever leaving your couch, which can can be a godsend during the winter months when you'd rather not risk leaving your warm bed. But during the summer, you gotta ditch the comforter and go enjoy outdoors.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Independence Day is right around the corner, and that means three things: fireworks, cold beer, and great food. I always love to cook festive foods for the Fourth of July, and I don't just mean the classics, like grilled chicken and brats. I mean foods that celebrate the Stars and Stripes: foods that are red, white, and blue.

Other than salt, there's no ingredient that's as big a kitchen staple as olive oil. And just like salt, there are a million little known uses for it.