Perhaps in tribute to the season premiere of Game of Thrones, Google Glass is demonstrating that what is dead may never die, as Alphabet's X (formerly Googlex) has revealed that the Enterprise Edition of the smart glasses are now available to businesses.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

Here is hijab style step by step guide for girls who don't know how to wear Hijab

It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

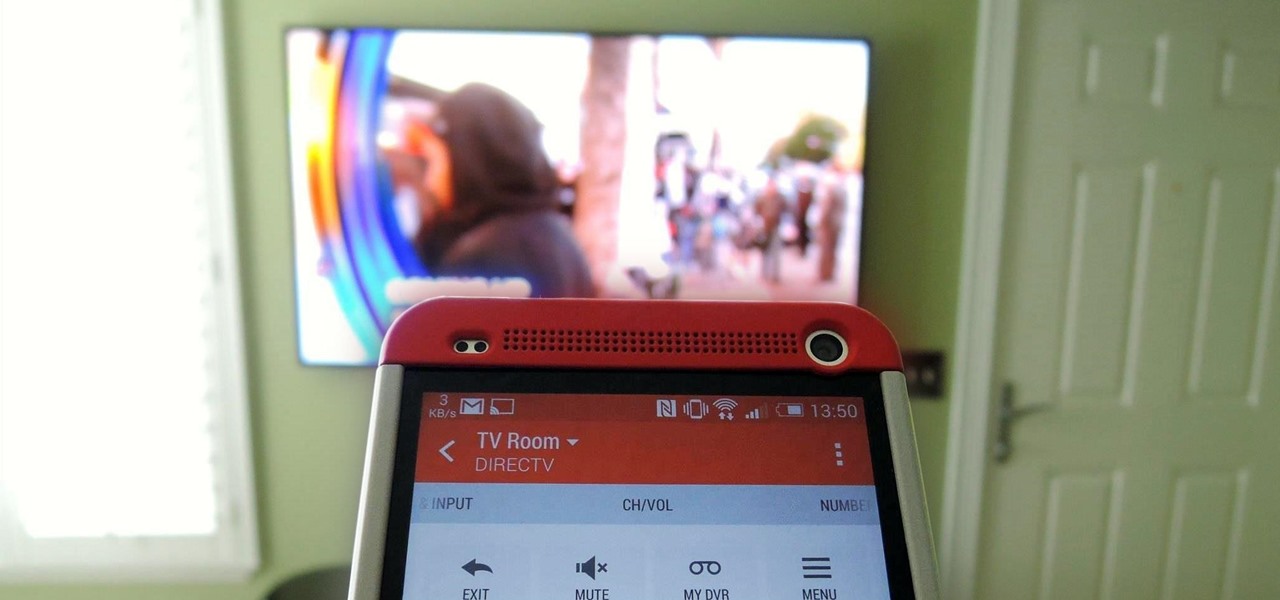
Let's face it, finding your remote, let alone finding something to watch, can take more time out of our days than we'd care to admit. There are remote locators and channel guides out there, but why use those when you have a perfectly good remote always on you—your HTC One. HTC put an IR blaster into their One and when it's coupled with their Sense TV app, it can make for one hell of a smart remote.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

I can't say that I'm a huge Tweeter, but I'm definitely a good follower. Having the ability to follow comedians, brands, and athletes helps me stay up to date on the things I'm interested in, and I appreciate being thrown a good joke every now and then.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

Jennifer Lopez, better known by her diva moniker J Lo, doesn't step foot out of her multistory mansion without a full face of makeup on, beautiful, voluminous curls, and her neck and hands dipped in diamonds.

Nicole Richie is the poster child of boho chic. Whether it's her wispy milkmaid braids, her flowy hippie dresses, or her arm full of bangles, she always looks effortlessly gamine.

In this tutorial, we learn how to unblock Facebook or MySpace at school or work. First, go to your start menu and run "services". After this window pops up, look for DNS client and then right click on it. Then, click "stop". After this, restart the browser that you are on with your computer. From here, type in the address of the website that you want to go to. It should not be working and you will be able to go onto the website without any problems! This is a great way to get past blocks your...

In this video, we learn how to download games with torrents. First, go online and download a client from uTorrent. Once you download and install this to your computer, you will be able to search for the torrents that you want. Go to: the Pirate Bay and you will see a search bar in the middle of the screen. Choose what you want to search for, then click on what you want to download. Once you double click this, it will give you an option where you want to download it. Chose uTorrent, then this ...

Whether you own a business or work for a company, you probably send out millions of emails every day corresponding with clients, PR, and whoever else you have to deal with. It's hard enough making sure you get around to all of them, but what's more is that even after you've finished composing the message you have to add your name, company name, phone, etc.

In this tutorial, we learn how to use Tarot cards and perform readings with Peter John. When you start to learn how to read cards to clients, you will first lay the cards out on the table. Then, the person who you are reading to will choose the cards from the pile. Depending on the card that they choose, you will read to them the description of what this card means. Then, you will delve deeper to tell them how it tells about their life and what their future will hold. After they are finished ...

In this video, we learn how to hack your Android phone. First, plug your phone into the USB to your computer. Now, search for telnet on your phone and install it onto your phone. Download this client to your phone from the Google Marketplace, then you can unplug your phone from the computer. Once this is installed, run this on your phone, then wait for it to load so it can hack your phone. When it is finished, your phone will be hacked and you can change the setting on it how you prefer. This...

In this tutorial, we learn how to do an auto damage appraisal. First make sure you have all your paperwork ready and lined up before you go to inspect the vehicle. When you have this done, the clients will be happier that you have everything ready to go and the claim is getting taken care of quicker. After you inspect the vehicle, write down all the notes about the vehicle and then calculate what the amount of damage is. Then, give a copy of the appraisal to the owner. After this, submit your...

Carole Gallesie from Creative Media Web shows viewers how to set up a new account in Microsoft Outlook Express. Express is preferred because it is a scaled-down version of the popular email client and it is easier to navigate. From your Windows desktop, go to the start menu, all programs, and click on outlook express. When the program opens, look at the top of the page for the "tools" menu, select accounts, add, and mail. The new account wizard will then appear and will walk you through setup...

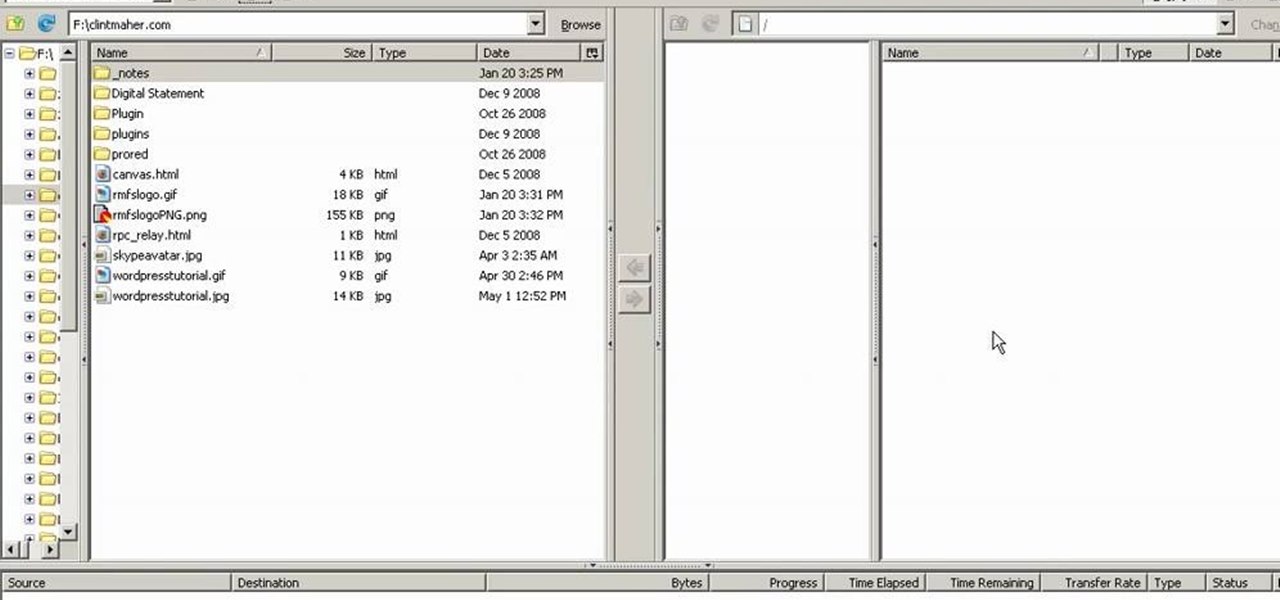
In this video, our author, atomicinteractive, shows use how to use Fetch FTP to upload a temporary webpage. Please make sure your directory has the html file. Please find your email with ftplogin information. This will also show login information for the control panel and creating alternate email addresses.

This is a video tutorial showing its audience how to install Super Nintendo onto an Ipod Touch or an IPhone. The first step is to open Cydia and click on packages. Scroll down and click on Open SSH, install the program and then open it. Then go to games and you can install the Super Nintendo application. Next install SSH Client on your computer and open it. Next plug your IPhone/IPod into your computer and transfer your Super Ninentdo game onto your IPhone/IPod. When you are finished transfer...

In this Computers & Programming video tutorial you will learn how to update websites from Firefox with the FireFTP add-on. Go to the Firefox add-ons page, search for FireFTP, add it to Firefox and install it. Restart Firefox to activate the add-on. Go to tools and click on FireFTP and that will open up a new tab with the FTP client. To configure the FTP to your account, create a new account by giving it a name. The host will be your domainname.com and use the login and the password for the ho...

Check out this awesome tip from CNET on getting FREE eBooks of the web and onto your Amazon Kindle for easy and cheap reading. They show you the exact process for getting free ebooks for your Kindle, so watch and learn. It's worth it!

Some data can be very confidential. In such case you need to encrypt the data so that it does not go into the wrong hands. There are lots of encryption software available to encrypt the data. But to use them first you need to install then and this can take lot of time. You can also use Windows built in compression client to encrypt information. To use this feature you need not install any software and it is a fairly simple process. So select a file that you want to encrypt, right click on it ...

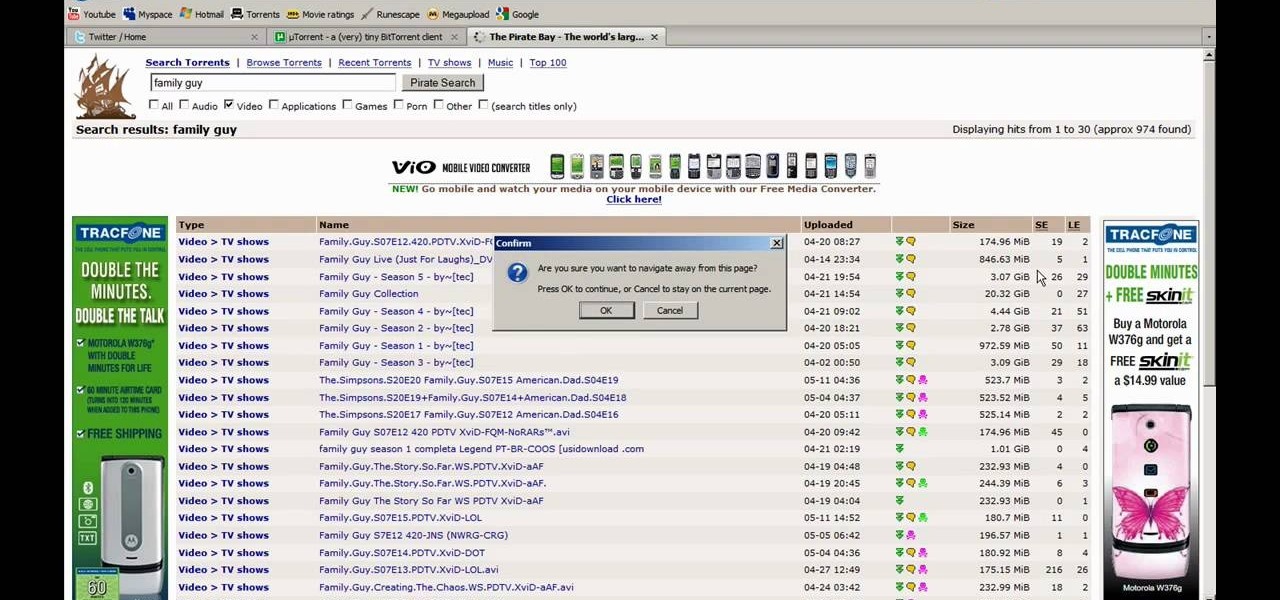
This video tutorial from JdudeTutorials presents how to download a torrent for the first time.To start, open your Internet browser. Browse to utorrent web page.Download and install uTorrent client version, suitable for your operating system (MacOS or Windows).Once you've installed application, browse to The Pirate Bay.This is the largest torrent source in the world.Check Video option under the search bar and type family guy (as an example).Click Enter. A list of torrents connected to family g...

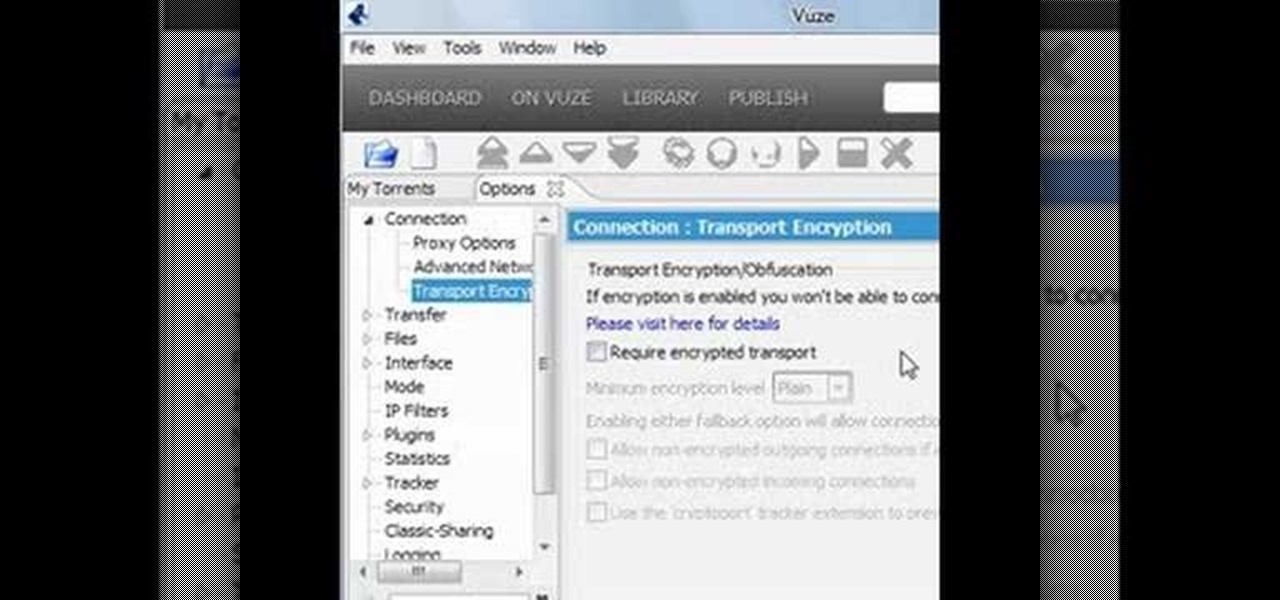
Torrents are a wonderful technology to share your files over the internet. If the data that you are sharing is confidential you may need to encrypt these files before sharing. To encrypt torrents in Azereus, go to tools and select options. From the left hand side menu select the connection option. Select the 'Transport Encryption' option from the connection sub menu. This section is intended for intermediate mode or higher and it is not available in beginner mode. So go to mode and select the...

Enabling Telnet in Windows Vista is a little bit more difficult than its predecessors but it still can be done. This video will demonstrate exactly how to enable Telnet in Windows 7 and Vista.

This is a presentation of how to face toughest interview questions. During most of the job interview, the interviewer is trying to find out your capabilities if the job. They want the client to explore why they want to be working here. They know that you want a job. But more specifically they need to know why you want to work in their firm and also your capabilities. So, you must be prepared to answer for this common question for most of the interviews. First of all you should understand why ...

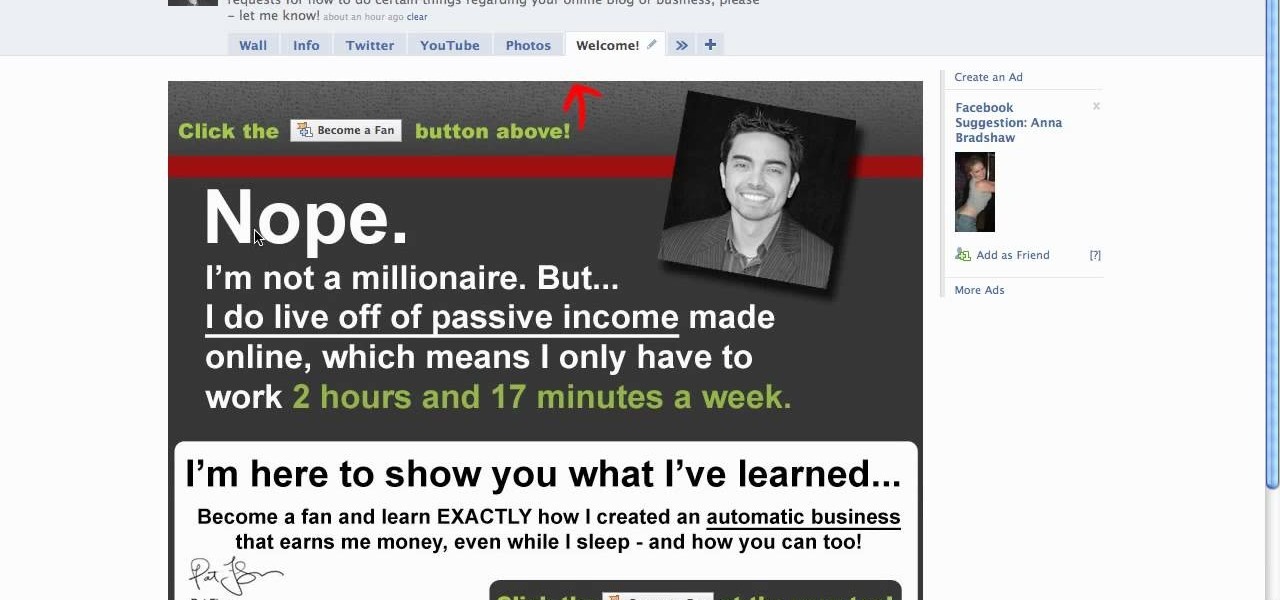
When people go to your Facebook page they are automatically sent to your wall. If you have a landing page you have an opportunity to: introduce who you are or what your business is about, have an opt-in area for a newsletter or email list, and give a call to action to become a fan! Learn how to use the Facebook application "Static FBML" to create an exciting and attractive landing page. This video contains everything you need to know to leave a lasting impression on your friends, colleagues, ...

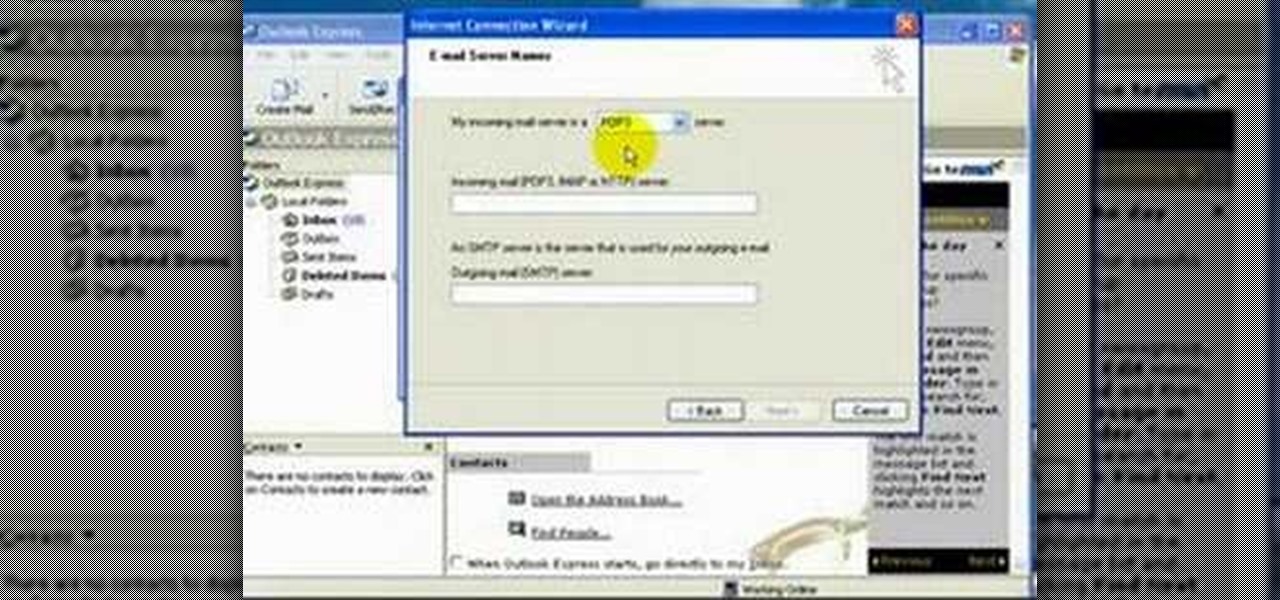
In this video, the instructor shows how to use Outlook Express in Windows XP. This software comes bundled with Microsoft Windows XP, which is a part of Microsoft Office package. Outlook is an e-mail client that allows you to view your e-mails on your computer without the help of any web interface to your mail host. To use Outlook Express, you need to configure it first. Open the Outlook Express program. Outlook will then take you through a wizard to help you to configure your email host. Ente...

Take advantage of this unique opportunity to prepare for the Advanced Certification exam in an interactive day long, live session with an Advanced Certified Pro advisor! Get a jump start on becoming a QuickBooks Advanced Certified Pro Advisor. Learn how advanced certification can help you grow your business and continue to improve your skills. You will understand what advanced certification is, why it is important to your practice and how it can benefit you and your clients. Learn how to effi...

This video shows us how to thread a sewing machine step by step. To thread a sewing machine: Place the presser foot in the upward position. Place a spool of thread on the spool holder. Traveling from the spool holder, across the top of the machine, look for a minimum of one thread guide. Insert the thread in the thread guide(s). Now look for a tension mechanism. Bring the thread downward to the tension mechanism, slip the thread between the metal disks of the tension mechanism, and travel bac...

Have you ever wondered how to make a brochure in Microsoft Word? Is your job requiring you to learn how to create a brochure in Microsoft Word? This tutorial will teach you step by step how to find templates online, transfer them into Word, and how to open the blank template in Word. This will enable you to create a successful brochure with a highly professional look to give to your clients. This step-by-step tutorial is guaranteed to tell you everything you need to know about creating brochu...

Are you a makeup artist with a messy makeup station? Many pro makeup artists are looking for the answer to the best set-up to achieve quick turn-over on brushes, specially when working with multiple clients or models. Koren from EnKoreMakeup shows us how he organizes his makeup brush station for hectic gigs with the mission to help!