"Buy low and sell high" is great advice, but how do you accomplish it? While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

Over half of all Americans have listened to at least one podcast, and that number is growing every year. With over one million podcasts and 30 million episodes in existence, there's no end to discovering new voices expounding on a range of topics.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

On the surface, Instagram is pretty intuitive, so you might think that you already know everything there is to know about using it on your iPhone or Android phone. But this photo and video-sharing app is constantly adding new features, some of which don't make the press releases. Even if you're an Instagram guru, chances are you've missed one of these hidden goodies.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

Less than two months since unveiling Project North Star, Leap Motion has released the reference design that will allow developers, makers, and even manufacturers to build their own augmented reality headsets based on Leap Motion's work.

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

While millions eagerly await the stable Android 8.0 release for the Galaxy S8, the beta is already in the wild and readily available. Notable improvements include notification channels and the revamped Samsung keyboard. One aspect often overlooked are new customization options, a huge part of Android. Let's take a look at what's new for customization on the S8's home screen in Oreo.

With a pair of new APIs and low-latency media servers, Twilio's Programmable Video platform could soon help ARKit and ARCore app developers build shared AR experiences between multiple users.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

In an early morning blog post, Microsoft announced the expansion of the Microsoft HoloLens Agency Readiness Partner Program. This announcement comes on the tail of an expanded HoloLens release over the last few months to many countries outside the initial US and Canada.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

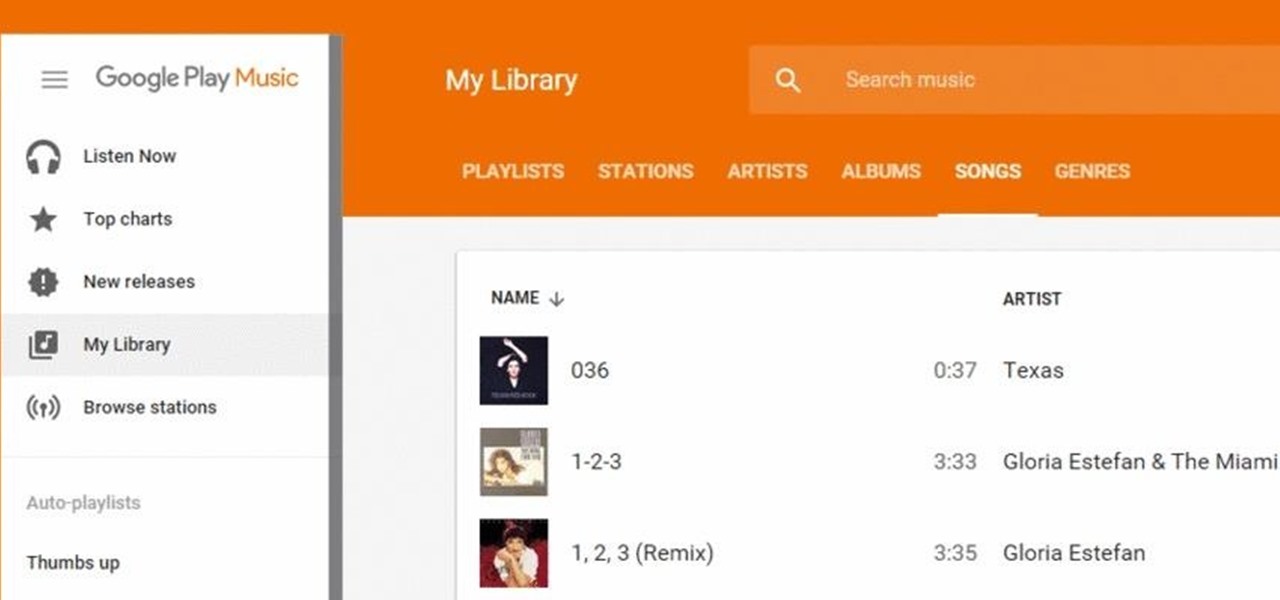
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

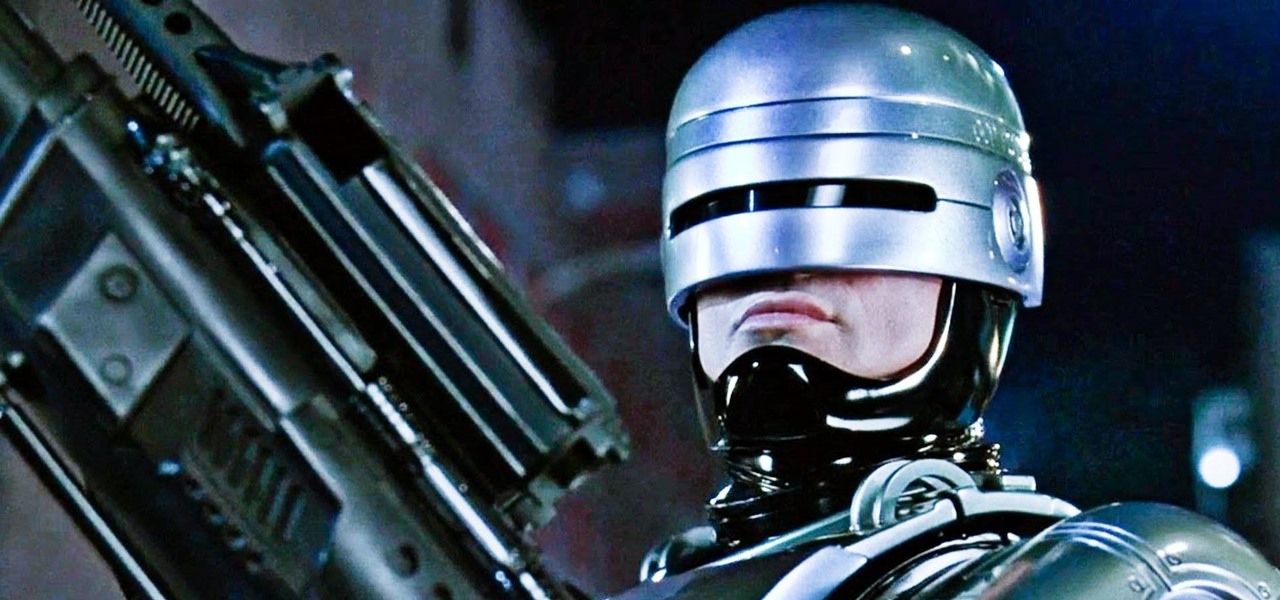
"Dead or alive, you're coming with me!" That iconic quote from the 1987 movie RoboCop was repeated by kids like me for years. The 2014 reboot introduced the baddest robot-cop on the planet to new audiences worldwide. While it didn't live up to the amazingly high expectations set by its predecessors, RoboCop 2014 did show off some newly upgraded gear. The modern look is cool and all, but rolling to a party rocking the 1987 helmet with the retro visor cannot be beat. With Halloween coming up, i...

There's a never-ending selection of app launchers that want a permanent spot on your Android device. While some keep the stock-Android look with beefed-up versions of Google's launcher, Blur is relatively new on the scene, with a unique approach to app management that sets it apart.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Creating awesomely messy slops of DIY slime and curdled fake blood isn't something new—we even have guides on making Dr. Seuss-friendly Oobleck and the radioactive green ooze that created my childhood favorite Teenage Mutant Ninja Turtles (minus the radioactive part, of course).

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

Video: . How to Stop Shrinkage with Shea Butter & the Banding Method!

American Horror Story might just be the craziest TV shows out there, with its absurd plot twists, creepy, over-the-top characters, and wicked storyline. It's gained a cult following ever since the first season, Murder House, and has even earned some Emmys along the way.

If you're new to Android phones, one of the first things you've probably noticed is how notification alerts differs from Apple devices, especially in regards to getting a text message.

In a previous softModder tutorial, we installed CyanogenMod on our HTC Ones to approximate the look and feel of the Google Edition HTC One. Unfortunately, this rendered Beats and HTC's ImageChip (among other things) useless.

UPS offers a four-step guide to prepare packages for shipping. These instructions include shipping advice on packaging materials and proper labeling that can help items arrive safely and on time. And when you are ready to ship, UPS Internet Shipping guides you through the required address fields. Packaging solutions made easy. That’s logistics.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

Last week, Google updated the YouTube layout to be more in tune with other Google properties. One thing that's different is the new, more Google+ look of your YouTube homepage. Though some may like the change, some definitely do not. Also new is the "Guide" on the left side when you're watching a YouTube video. for you folks looking to get back to the normal YouTube layout, it's as easy as copying and pasting some code into your browser.

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

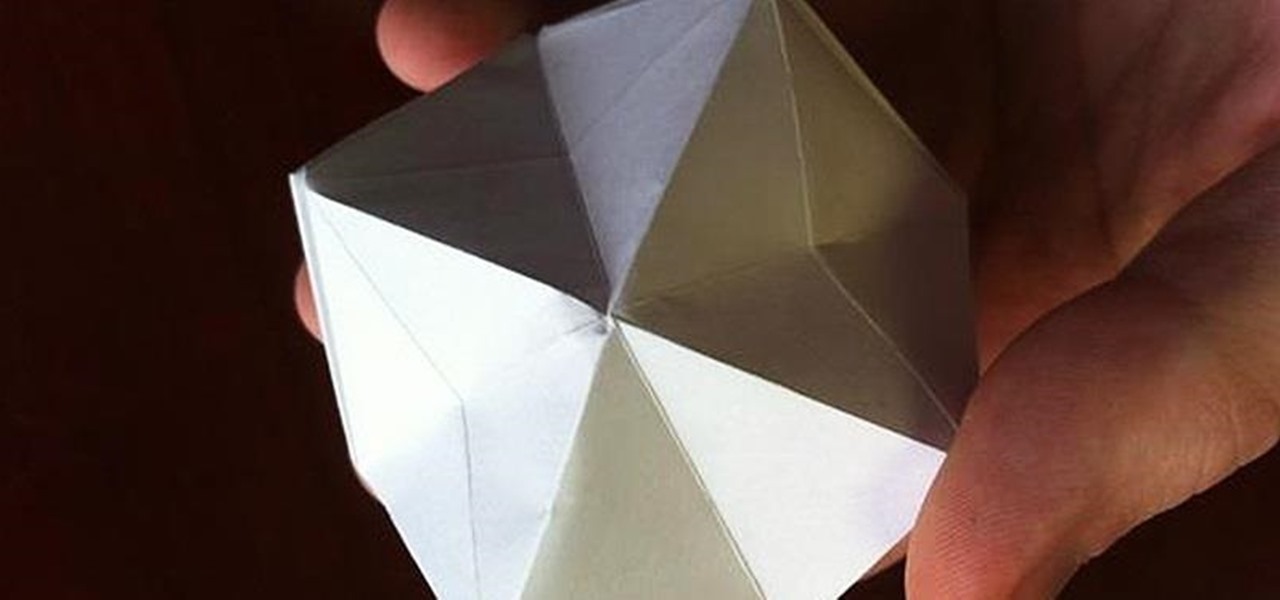
One of the most popular and basic origami geometric shapes is the "water bomb," which is a simple inflated cube. With a few extra folds and only a minor shift in approach, a more complex geometric shape can be achieved.

Welcome... the the final mission of Dragon Age 2. You initiate it by reading the letter The Last Straw on Hawke's desk. But before you do that, you should complete any sidequest you still want to do because the game is officially over after this. This video series will guide you through the quest, and this guide from the creators of this video should fill in the gaps.

'The Deep Roads Expedition' is the exciting conclusion of Act 1 of Dragon Age 2, and this excellent walkthrough of it runs to nine separate videos. Worry not, friends, it in very enjoyable and well-made viewing that will teach you everything you could ever possibly want to know about this quest. It is a strategy guide among strategy guides.

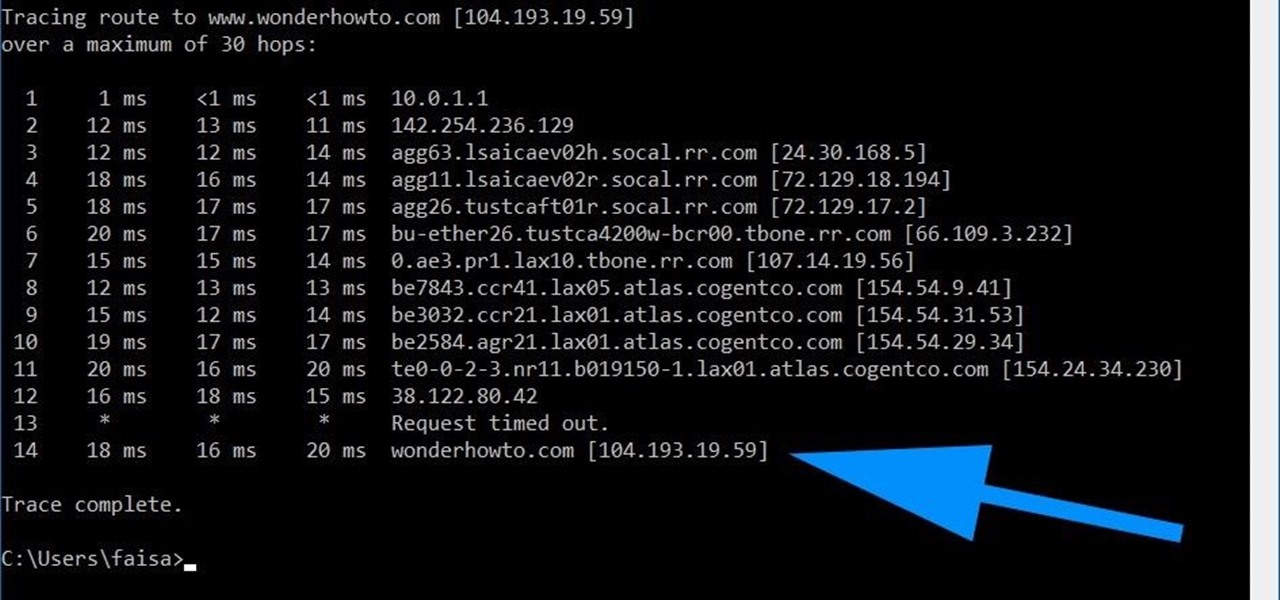
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

The Minecraft 1.9 pre-release is out, and Jeb has recently tweeted a link to version 2 of the 1.9 pre-release. If you're interested in downloading and installing it, take a look at this guide to learn how to update your Minecraft to the 1.9 pre-release.