To say we're a nation of coffee-lovers is putting it mildly. Americans consume 400 million cups of joe in one day alone, but how well do we actually know our morning BFF? We know it comes from a bean, and that more coffee drinks exist than there are ways to skin a pig, but what else?

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

Biting into a perfectly ripe mango is living proof of nature's goodness. The flesh is at once creamy, smooth, tart, and sweet. Plus they're incredibly good for you.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.
Videos are great for catching fleeting moments, and photos are insanely easy to share with anyone, but how can you get the best of both worlds?
Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left these two aesthetic features hidden away. Luckily, with root, you can easily enable them with just a few quick edits.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

If you're a Febreze fanatic, you're well aware that the "odor eliminator" can be pretty pricey, and that's reason enough to stop buying it.

While we've already covered several good ways to tame the itch of a mosquito bite, you're much better off preventing them from biting in the first place than dealing with the itchy aftermath.

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.

As you may have noticed, many of our tutorials cover topics that require you to have root access. When your phone is rooted, backing up apps doesn't require you to connect to your computer, and installing custom ROMs lets you get more useful settings. Rooting also lets you get rid of the Sense-style menus and status bar, and even upgrade to a newer version of Android.

If you've ever stumbled through Pinterest's boards, you'd know that Pinners have quite a penchant for aesthetically beautiful desserts. You can find a whole spectrum of "huh?" recipes, from pumpkin zebra cheesecake to sorbet terrine with plum compote.

The newest firmware update for Android, Jelly Bean 4.1.1, has been out for a while now, but not every device has gotten it yet (some never will). One popular device that has recently gotten it is the Samsung Galaxy S III, only they'll be pushing the update out overseas during the next couple weeks, with the UK already seeing Jelly Bean from the cellular provider Three (if you're on Three, see how to update your device here). Unfortunately, stateside users will have to wait a bit longer. There...

Even if you're not a hipster with your own self-sufficient garden, making your own edibles at home can be pretty cool. And while it's obviously easier to pick up a bottle of 7-Up at the store, there's something undoubtedly fun about making your own. For those addicted to their fizzy drinks, DIY soda is a great way to save some cash and make their drinks healthier with natural flavors and sweeteners, instead of something like corn syrup or aspartame.

If you have a smartphone with a good camera, chances are you don't think it's good enough. There's always something that can better with your mobile pics, and for me, that something is closeup shots.

Mud cake might not sound very good but it sure tastes great. Try out this fun cake for a birthday, a party or just because. This mix of rich chocolate, nuts and a fluffy marshmallow top is sure to brighten any day.

Put your imagination into solid form by working with clay. Now all you need is the clay. No need to buy it at the store when you can make all the clay you like at home. Clay is a fun medium for adults and kids to work in.

How to Decompress an Archive File.

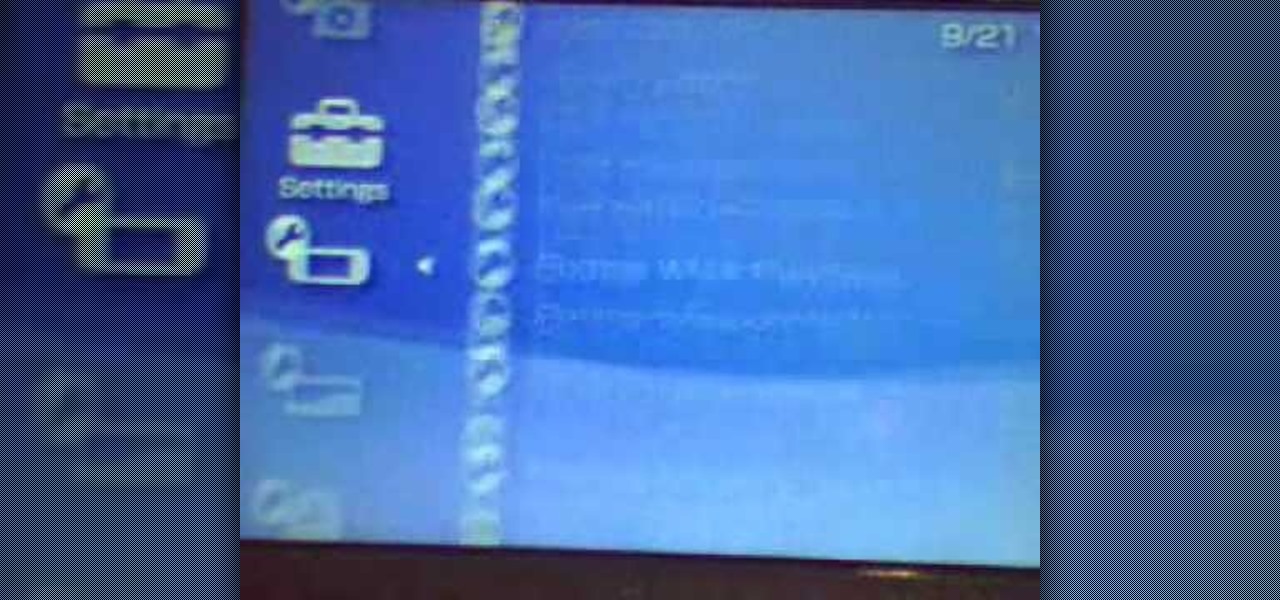
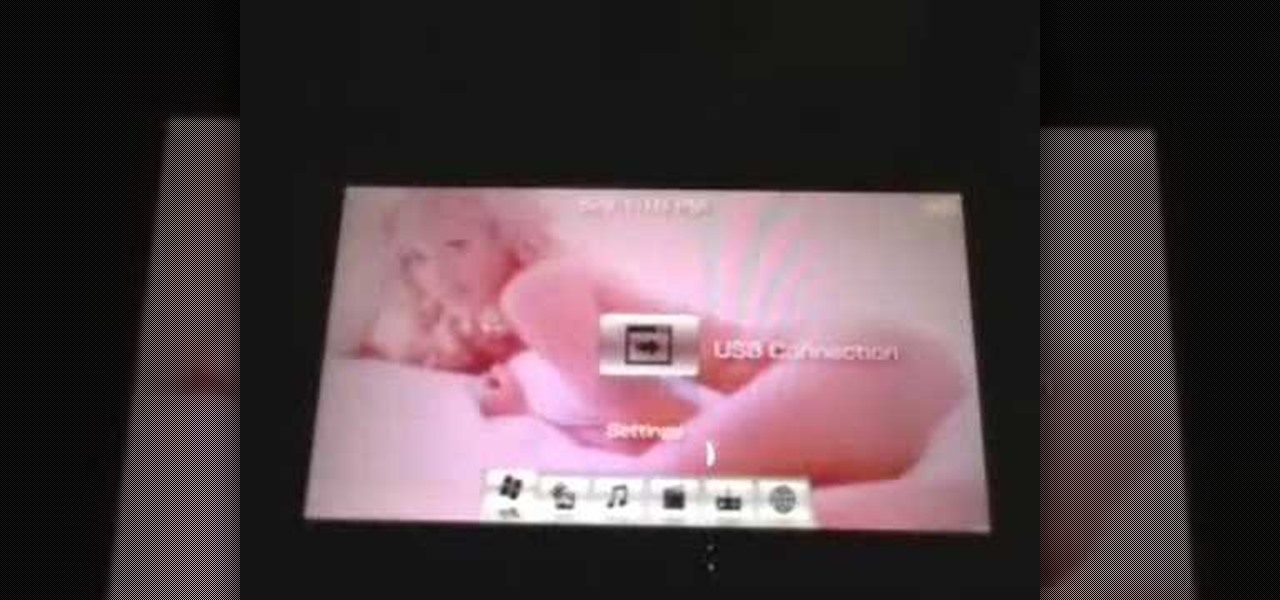
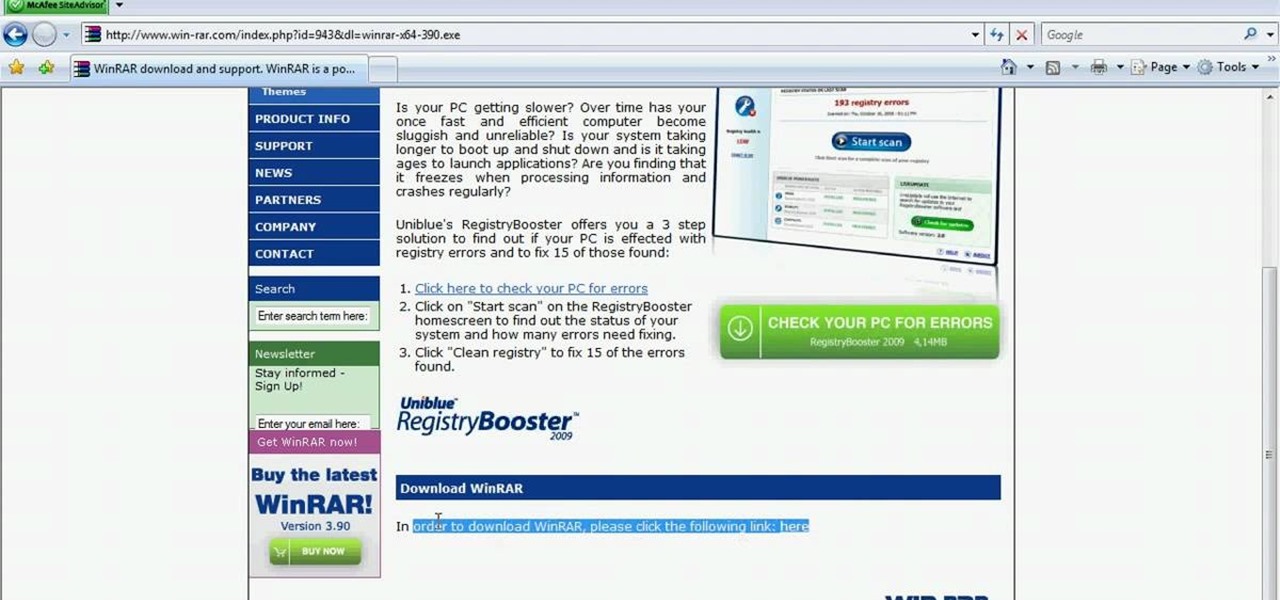
This walk-through video tutorial shows you how to install the Netfront on your PSP. First open your browser and download Netfront from the link provided in the description. After the download is completed extract the files from the compressed folder using winrar as shown. (If you haven't got winrar use the link in the description to download it.) After the extraction place the folder in the PSP game folder as shown and disconnect the PSP. Start the PSP go to the game menu and launch Netfront ...

The team at blackhead no more demonstrates how to quickly and easily remove stubborn blackheads from the nose, using a unique product called BLAKhead Masque. If you've ever had acne like this, this video can help you. BLAKhead Masque is applied much like any other facial mask, hardens like a wax and extracts your blackheads much the same way as waxing body hair, without the painful hair pulling process. This product works on both men and women, and can make life easier for those with this typ...

If you’re having trouble getting games on your memory stick, this video will walk you through the steps of just what you will need to do to compress files onto a thumb drive. There are a variety of steps you will have to follow and you’ll have to have a little bit of time to wait for your game to compress but the effort is well worth it.

In this video tutorial, viewers learn how to unzip .rar files using Winrar program. Begin by opening your internet browser and download the program from the link in the video description. Wait for the time to pass and click Download. Select 32 bit or 64 bit, depending on your computer. Open the file and install the program by following the instructions. Once it's installed, select the file that you want to unzip. Right-click on the file and select Extract All Files. This video will benefit th...

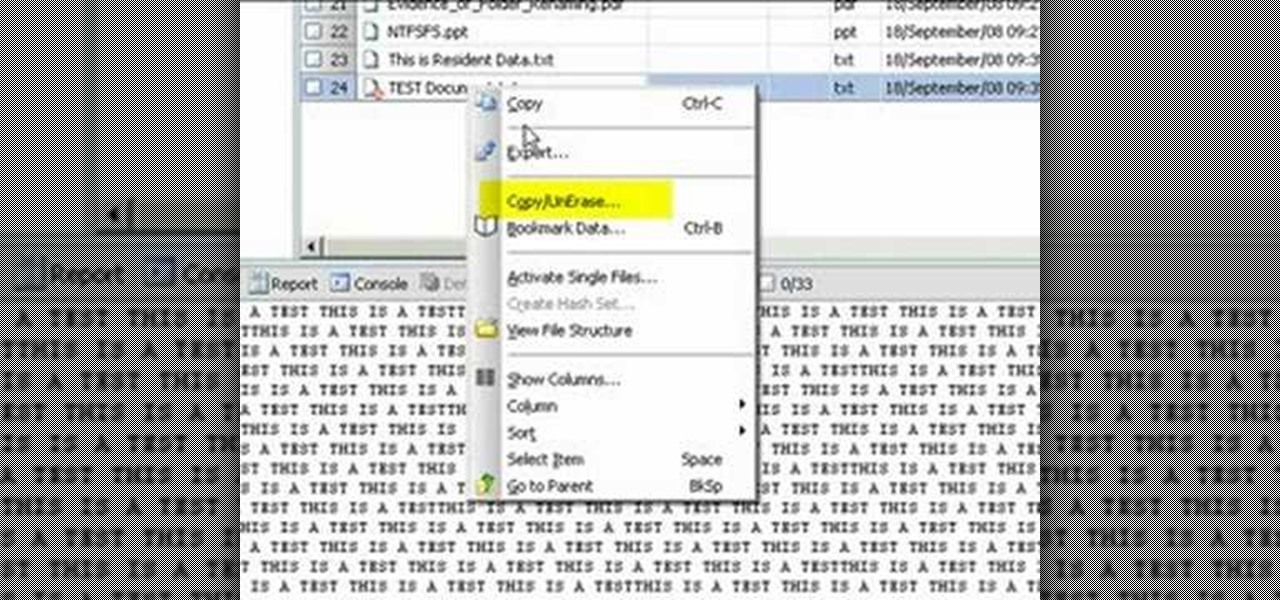
Use Encase to open the drive after the document has been deleted. The deleted file will show up in the program and will have a red circle with a line through it showing that it was previously deleted. The window on the bottom of the screen will show the document context so you can verify that it is the correct one. Right click on the file and click 'copy/unerase' to restore the document. Down in the bottom right hand corner you will see the progression of the copying to the chosen file destin...

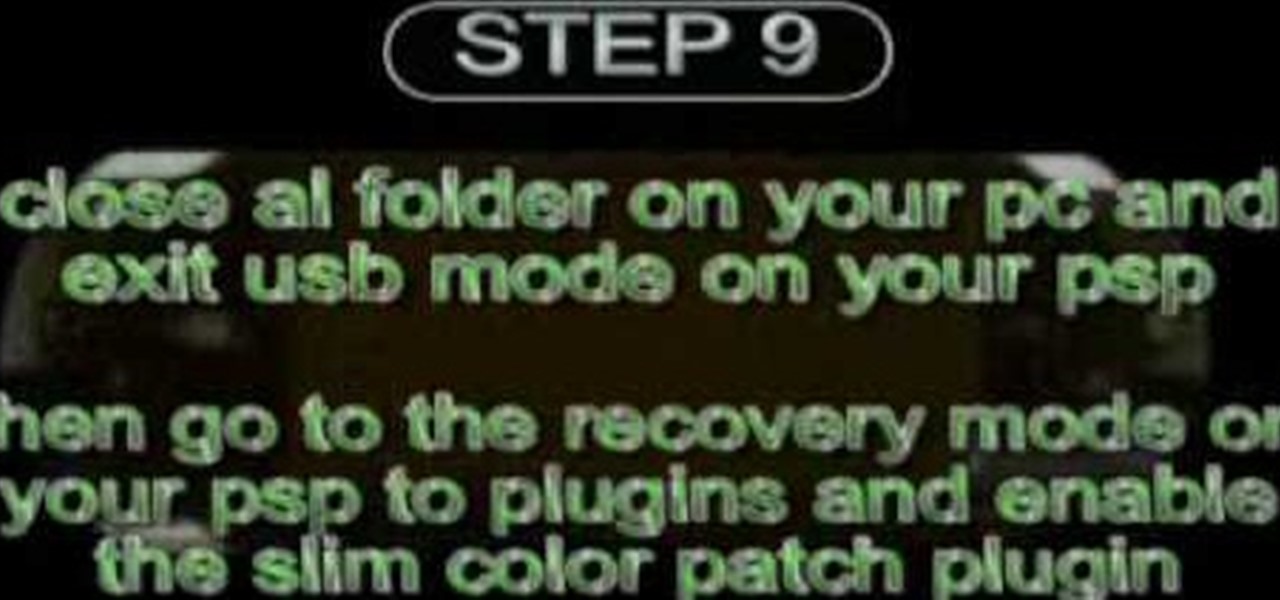
This video will show you how to install the slim color patch plug-in for slim colors on the PSP Fat. With this plug-in you can use 27 of 30 backgrounds at PSP Color Themes. To install the plug-in just use the following instructions: Download the Slim color patch plug-in pack. Unzip the slim color patch file and extract the files like in the video. Enter the recovery mode on your PSP, go to Advanced and enable USB Flash0. Follow the next instruction until you successfully install the plug-in t...

This video focuses on how to do long division. She starts by dividing 1548 by 26, going incrementally between each value. She first take 26 into the first three numbers of 1548 (154) and gets 5, then takes the remainder of 24 (154-130) and brings down the 8 to get 248. She then divides 248 by 26 to get 9 with a remainder of 14. She then goes into some detail as to how to extract the decimal from the remainder by continuing the long division and adding zeros to the end of the divisor. At the e...

Vincentwiliamphilips teaches you how to install the ultimate vshmenu plug-in on a PlayStation Portable. This is an improved version of the vshmenu plug-in, with added features. You download the needed file, called Ultimate VSH Menu v2.00 for 5.00m33-6. Open the file and extract vshmenu.prx and the vsh text file to your desktop. Connect your PlayStation Portable to your computer. You will then see the root of your memory stick. Put the vshmenu.prx in your seplugins folder. If you don't have on...

You can easily remove audio from videos in the Photos app on your iPhone, but the same cannot be said about removing video and just keeping the audio track. However, another stock Apple app can help extract the sound clip, and it barely takes any work to set it up.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.