Apple just released the latest developer preview of OS X 10.11 El Capitan, currently in its sixth beta. While this latest build mostly deals with tiny improvements and bug fixes, it also includes a brand new breathtaking wallpaper of the El Capitan rock formation in Yosemite National Park.

Functioning as an extension of your iPhone, the Apple Watch makes monitoring and receiving notifications convenient with just a glance, leaving your iPhone in your purse or pocket. But just like on your iPhone, these notifications can begin to stack up, so let's show you the one-touch method for clearing them all at once.
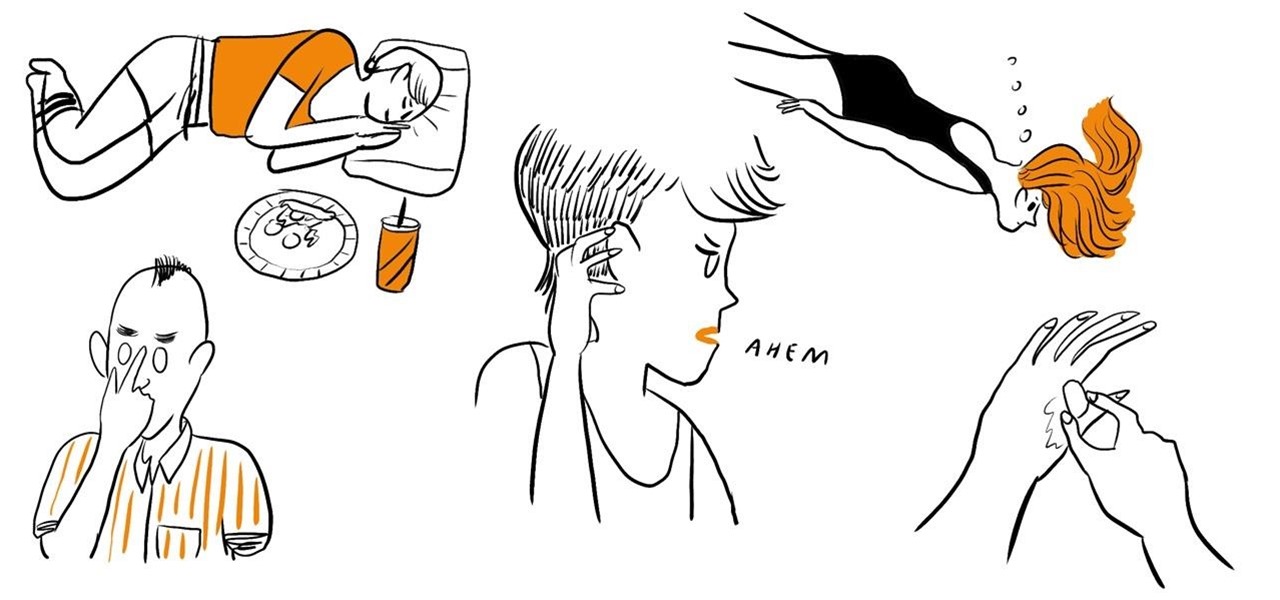
If you need to relieve an itch in your throat, you can try getting rid of it by scratching your ear. Or if you accidentally give yourself brain freeze while eating ice cream, you can press your tongue against the roof of your mouth and cover as much as surface area as possible to make the pain go away.

Hello again my fellow hackers. I've come to give you some hope for hacking. As we know there are a lot of exploits out in the world and there are websites you can find them on.
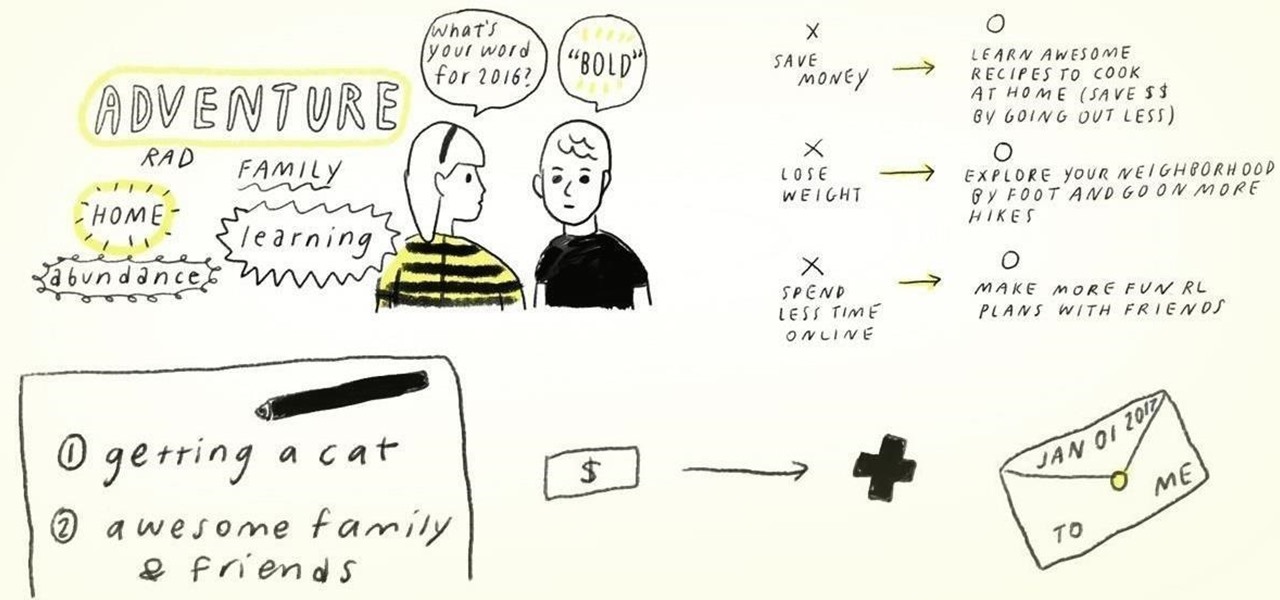
Statistics show that only 8% of New Year's resolutions on January 1st actually get fulfilled. While you can certainly take advantage of some mind hacks to increase the probability of succeeding at your January resolutions for the rest of the year, setting killjoy goals and signing up for a gym membership are not the only ways to ring in the new year.
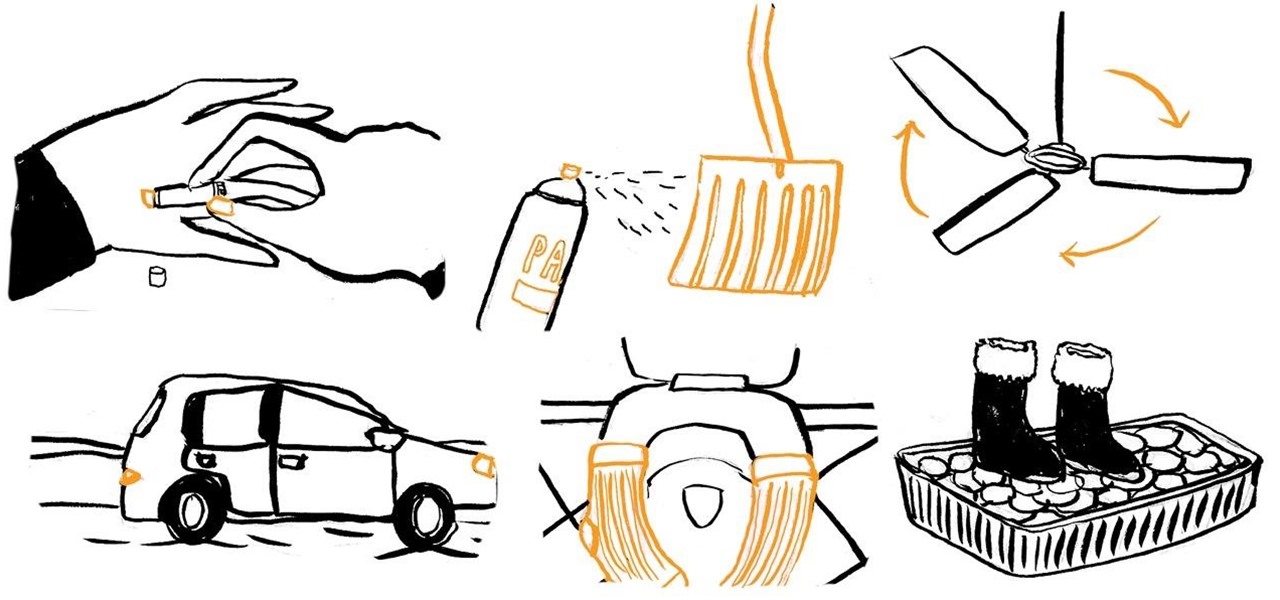
Turn on the ceiling fan indoors during the cold winter season. Though it may seem counterintuitive, spinning the blades clockwise on a low setting actually recirculates warmer air trapped near the ceiling towards the floor.

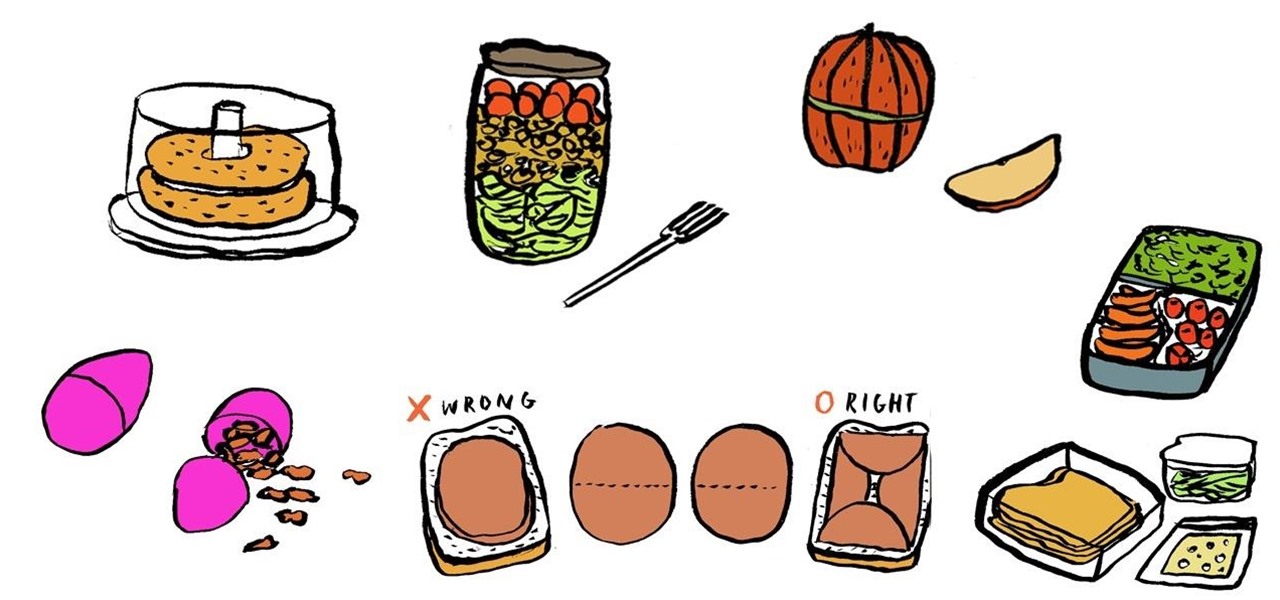
Bringing your lunch to work doesn't always have to involve boring brown paper bags and plastic ziplocks.

Ikea Hacker features a nice Ikea mod: Romain turns the Ivar side unit into a camera dolly. "A few days ago, I found out that the Ivar 'wooden ladder' was perfect to use it as rails for my cinema dolly! I can now make some nice sequence shots with this 18€ accessory from Ikea."

Candy machine hacks are so popular now, one might think it's easier to get candy from a vending machine than from a ... baby.

Store bought Nerf guns don't always achieve the velocity necessary for an effective assault. Zach Scott's solution: mod the toy. Known for his fantastic cat videos, Zach claims this hack increases trajectory by at least 25%! Every bit counts when you're in an all out foam war.

This gives a variety of cheat codes for Grand Theft Auto IV. Follow this and learn how to hack GTA 4 for the PS3. Cheat at GTA IV.

Learn a harmless hack to access and control other peoples' webcams with a simple Google search. Access and control web cameras with Google.

When choosing a security system for the office, Billy Chasen decided to ditch the traditional lock & key barricade for something a little more 21st century. He hacked together a device that uses a web server, servo motor and some parts from Home Depot to enable locking & unlocking via text message. Chasen maintains a list which gives access to green lit office workers, who enter by simply texting "lock" or "unlock"... and voilà, open sesame.

That Kinect you bought for your Xbox 360? More than just a game controller, it's a bonafide hologram generator! In the clip below, UC Davis researcher Dr. Oliver Kreylos demos the process. The fun stuff begins at the :44 mark. Kreylos explains, "By combining the color and the depth image captured by the Microsoft Kinect, one can project the color image back out into space and create a 'holographic' representation of the persons or objects that were captured."

Jonathan Guberman of Site 3 coLaboratory hackerspace in Toronto has created an Arduino-controlled mechanical typewriter that can type on its own, detect what is being typed on it, and run text-based interactive fiction games such as the classic (and to most, all but forgotten) Zork. Guberman says:

What do you get when a musician (who also happens to be a pyromaniac) has too much time on his hands? A WonderHowTo hero and mastermind behind the hack of the ages.

Hack N Mod offers an incredibly simple cell phone camera mod that delivers striking results. All you need is a lens from an old DVD player and you can magnify your zoom by five times.

Hacked Gadgets recently featured Csaba Bleuer's LED wave display, a device that projects LED messages midair. Bleuer had also previously created a similar device that spins on a fan motor.

John Cornwell is a God among men. Even Letterman thinks so. As well as every beer drinker. John hacked his mini refrigerator into what he calls the "Beer Launching Fridge":

Instructables member Mike Galloway has constructed his own private planetarium: a fiber optic starfield ceiling for his newborn baby.

Need to be undercover? Well, make yourself impossible to photograph. Get some infrared LEDs. They're undetectable to the human eye, but that's not the case with cameras. Wire them to the brim of your hat and you've got instant invisibility to any camera -- paparazzi, Big Brother or otherwise.

Here's a DIY dream. Solar-power, recycled bottles, snap'n'go toy car! Simple. How easy to transform trash into toys.

One of the many reasons Circuit City should go out of business is their sale of ridiculously expensive cables, wire and cords. The secret to the industry of Monster Cables is that it is unnecessary and ineffective. Gold-plated or otherwise, Monster's $100 cables are not intrinsically better than the cheaper versions they're stocked next to. Don't believe us?

As the image above suggests, it takes expertise (and perhaps sleuth) to actually hack into somebody's facebook account. But to steal a friend's password? If you're lucky, a simple mind game will do the trick. Read and learn:

This hour-long hacking tutorial looks at the Nmap security scanner. In particular, this Nmap tutorial looks at port scanning concepts, TCP three way handshake, stealth scans, idle scans, bounce scans, version detection, OS detection, NSE/LUA scripting and firewall logs. To get started using Nmap, watch this video tutorial. Use the Nmap security tool.

Learn a hack to access the command (cmd) prompt in Windows if it has been blocked. Get onto the Windows CMD if it is blocked.

If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Weekend Homework". We all know that this time of year is busy for everyone, but that didn't stop occupytheweb otw from creating a great article in his continuing "Hack Like a Pro" series.

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer installed already. If you are young and just starting out, this may be hard for you to manage with your current salary. If you have no washer and dryer, the only alternative is the laundromat.

The days of entering left, right, left, right, up, down, up, down, a, b to cheat your way through a video game are long gone. With achievements and trophies in existence, game developers have, for the most part, removed cheats from video games.

With the rather large success of the Community Byte activities, both programming and HackThisSite, I have decided to continue to do both activities every session! With that said, when programming sessions occur, they will be lead by Sol Gates in Gobby. Also, the programming mission will no longer be to code a tool, we have changed it to be even more "noob friendly". This means that instead of coding a tool, you will be walked through puzzles and challenges that must be solved by coding a scri...

For as much money as they've made from North American video game audiences over the years, Japanese game developers don't seem to have very much faith in them. Dozens of great titles from their 40 years in the industry have appeared in Japan and across Europe, oftentimes even in English. But they never make it over to America, like Mother 3, Last Window: Midnight Promise, Dragon Force 2, and Tobal No. 2 (that one didn't even hit Europe).

There's a lot of talk going around about Google's new social network and how it's heavily influenced by Facebook, but truth be told, how could they build Google+ without taking a note

When the New York Times paywall first went up, there was a whole lot of balking. The idea seemed egregious to most, and the digerati's overwhelming conclusion was that the system would fail. But interestingly enough, there is speculation that the NYT is actually experiencing an increase in their print subscriptions, which according to Business Insider founder Henry Blodgett, is due to users feeling less guilt over buying the print media if, after all, the digital version is no longer free.

When the much buzzed Facebook profile page redesign was released back in December, French artist and co-director of ad agency La Bande Originale Alexandre Oudin came up with an innovative way to maximize the visual possibilities of the page. His clever "hack" created a ripple effect of copycats across the web.

This past Tuesday, Amazon pushed a big software update to Kindle users the world over. While the update introduces a host of great new features—secondary page numbers that allow readers to reference real-world editions, for example—, it also takes something away. What?
Warnings this only for educational use i dont take responsiblety for any use of this article if you want to use this for use at a school plz contact me at sebzy4@hotmail.com hi im a computer enginer/programmer (NOT games) but i am good at hacking and i want to help. notise that this is just a help site not hacking site but this will help firstimers