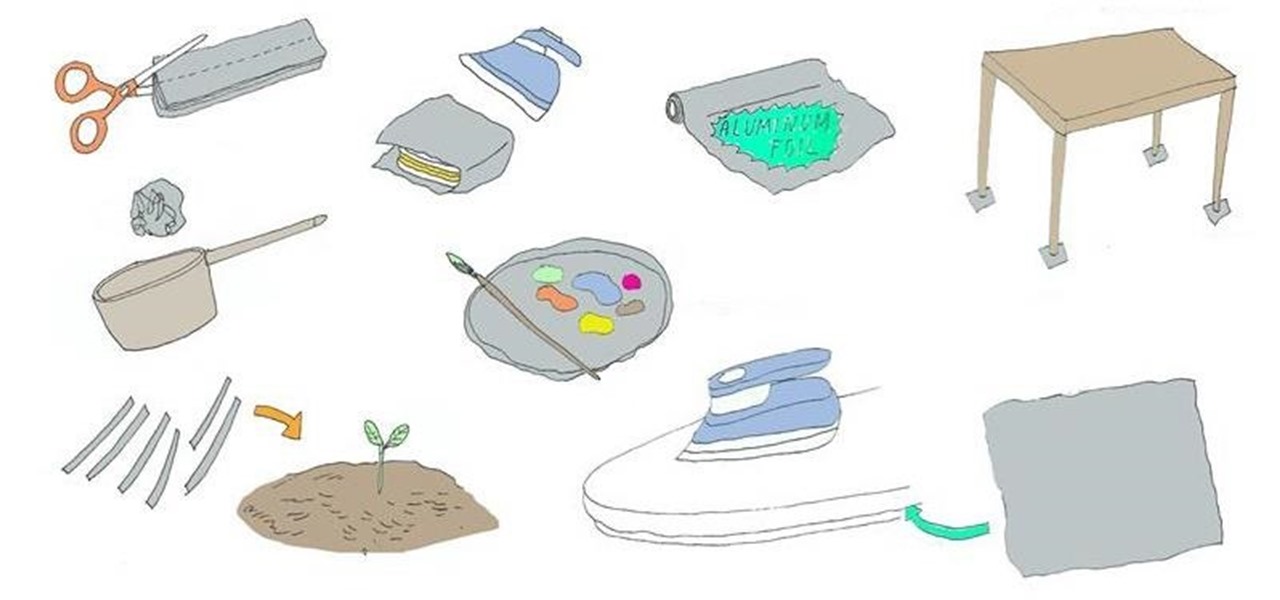
What to do when your motivation is running low and you absolutely don't want to do something that needs to get done? If nothing is working for you, hack your brain with the following techniques to motivate yourself.

It's hard to believe that a photo-sharing service could become as big as Instagram has. So big, in fact, that there are tons of websites, software, and products aimed at integrating it into our lives even more. Hell, you can even be Instagram for Halloween.

There are so many unpleasant things about flying. You have to wait in line after line, take off your shoes, belt, and jewelry, and somehow make sure your luggage stays intact. And then, once you've made it onto the plane, there are the awful movies that most airlines play—if you even get a movie.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

(We did not know about these, either...until we discovered these videos.) The fixed gear bike, also called a fixie, was designed for track racing in the velodrome. Working bike messengers brought them to the NYC, Tokyo, SF, London streets on account the cycles gave them far more control to maneuver the urban jungle. The Chinese acrobat peddling a bike with 18 contortionists wrapped around him, must have a fixie.

My idea is simple but, imo, funny. Have the gang have an all out laser tag war with running, diving, obstacles, the works, in a padded arena or outdoors. But each harness is connected to one of those flat tasers (the kind that looks almost like brass knuckles) pushed in their backs, or chest, or crotch (or all three if you prefer, each one connected to a different sensor: back shot is back shock, front shot is chest shock, head shots are crotch shocks). When you get shot you get shocked. It w...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

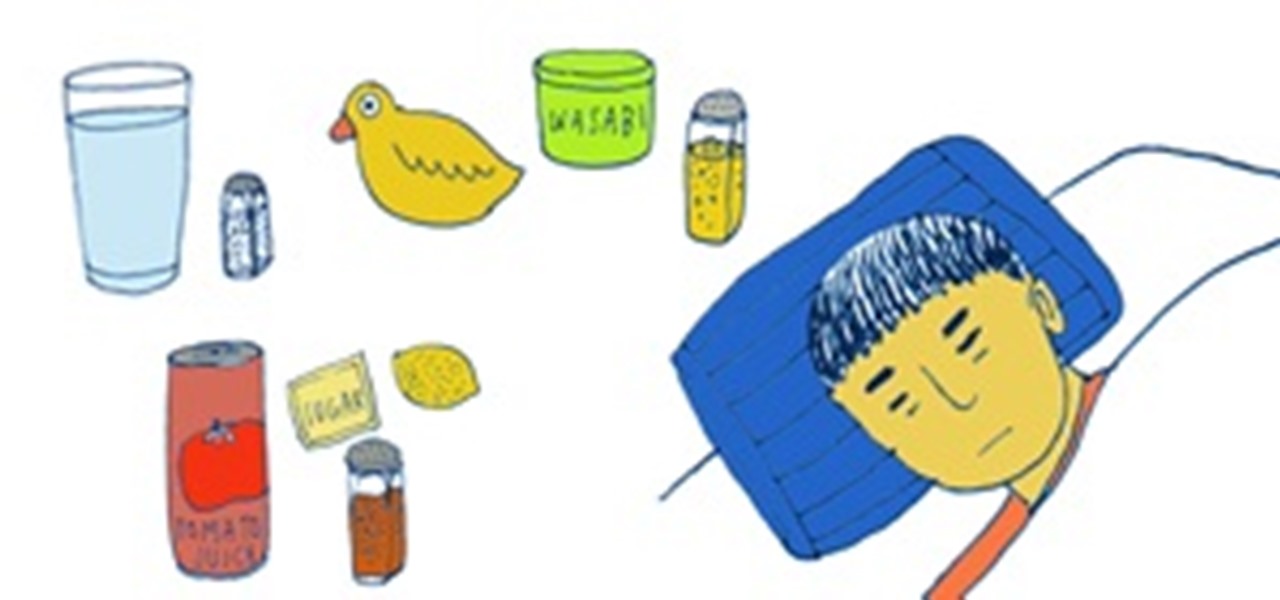
Unfortunately, many of us will be celebrating New Year's morning with a post-New Year's Eve party hangover. Avoid this common misfortune by taking some basic hangover-prevention precautions: eat a full meal before drinking, stay hydrated, and limit yourself to 1 to 2 drinks for every hour.

I've been pretty straight forward with my praise for Batman: Arkham City. But the thing I like most of all are all of the side missions in the game. One of the cooler, and darker, ones is entitled Identity Thief. No, you don't go after some nerd that hacks people's credit card information. You go after a psychopathic serial killer.

As far as cooking appliances go, rice cookers are pretty fabulous. All you have to do is add rice grains and water, press a button, and wait for the magic to happen. You don't have to worry about the food burning or the pot boiling over. But what if you can apply those same lazy steps to cook other things, too?

Gina Kometani posted such a cool tip to the community corkboard, I had to illustrate it!

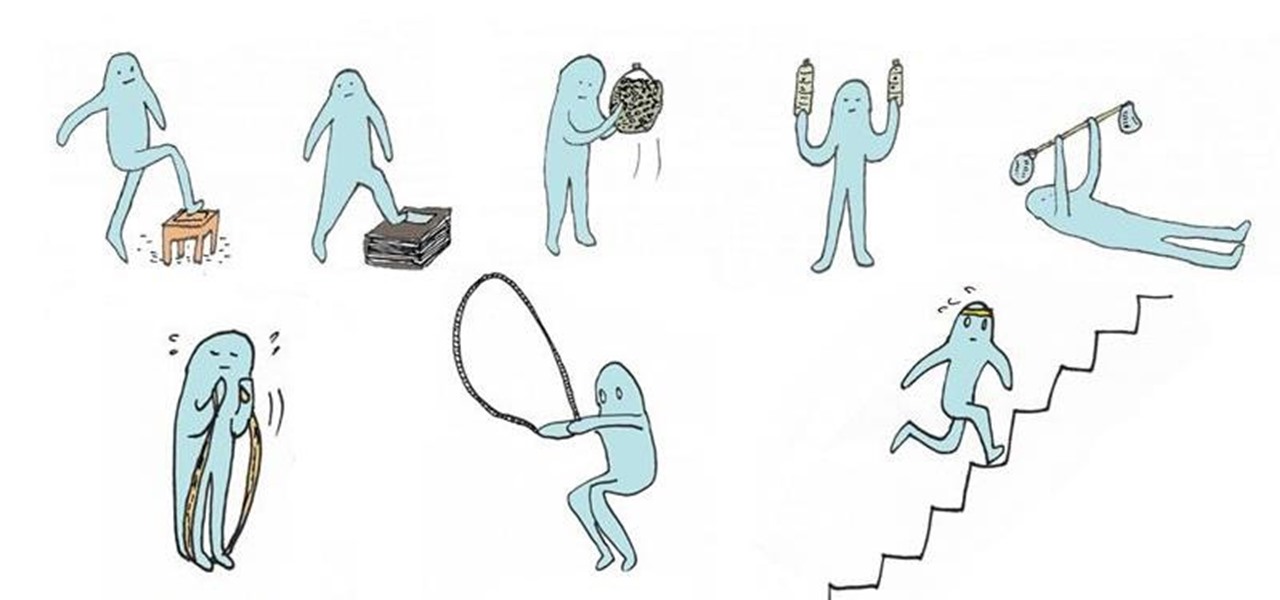
Work it without breaking the bank—with a couple of household items and a little ingenuity, you can transform your old junk into effective gym equipment for both cardiovascular workouts and strength training within the comforts of your own home.

Backtrack 5 is a Security Essentials Backtrack is a suite of tools to help with Penetration of any Network, Unix, Linux, or Microsoft Based. Backtrack 5 is good for WEP & WPA hacking and penetration testing.

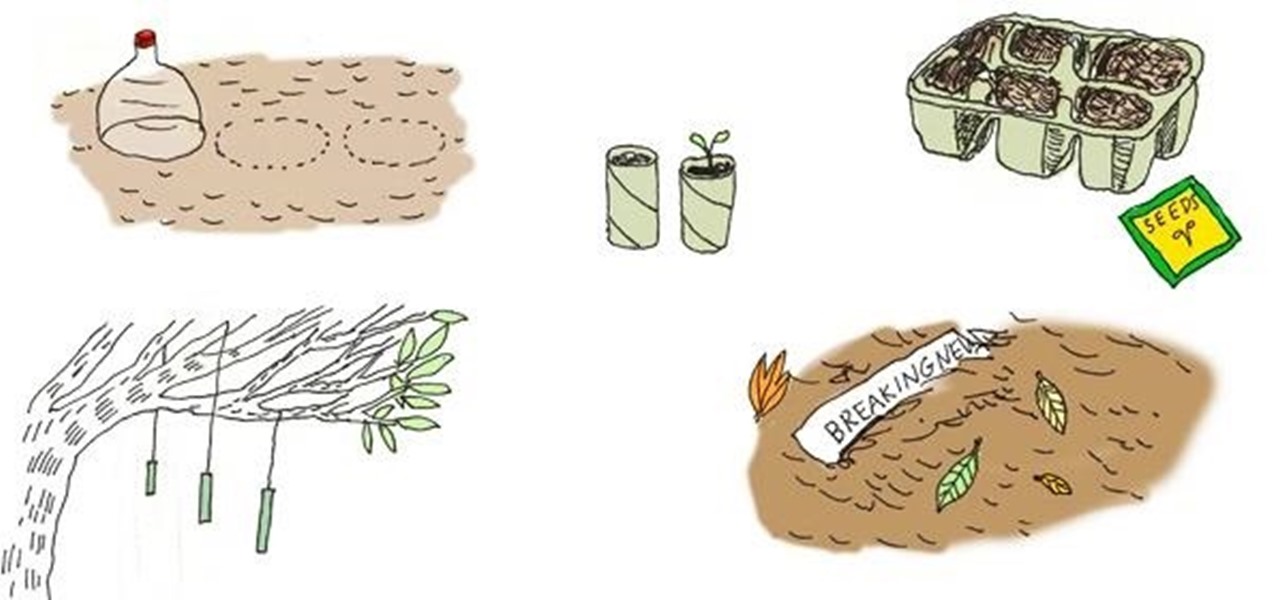
If you've got a knack for gardening and an inclination for recycling, then you need to know about these six garden hacks. Some of the trash inside your bathroom and kitchen is actually garden gold, so get your recycling hats on.

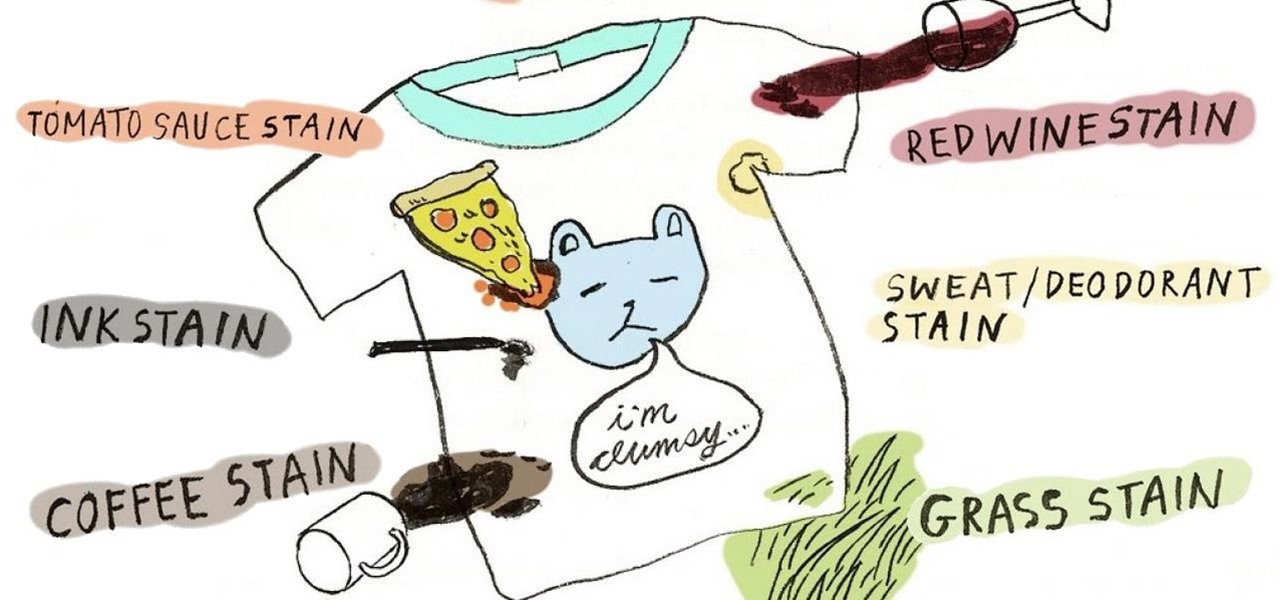
What do you do when you accidentally stain your favorite article of clothing with coffee, red wine, or pasta sauce? If you aren't within immediate reach of laundry detergent or commercial stain removers, you can use many common household staples such as baking soda and white vinegar to remove the offending stains right away—sometimes even better than their commercial counterparts.

It turns out that the silver crinkly material traditionally used for wrapping leftovers and making funny hats to block out messages from extraterrestrial beings is pretty darn useful for a number of other random but handy tasks, such as sharpening your scissors and keeping bugs away from your vegetable garden. What can aluminum foil not do? Seriously.
Unless you avoid the news entirely, you've almost certainly heard about the hacking sprees that have been taking place over the past several weeks. Tens of thousands of usernames, passwords and email addresses have been released online for anyone to download. Thankfully, it seems that one kind soul has put all that compromised info to good use.

For the low cost of a bag of zip ties, you can easily survive any Snowpocalypses this winter by blizzard-proofing your bicycle tires. Says the MacGyver behind the ingenious hack, Fritz Rice of the Dutch Bike Co.:

Here's another cool hack using the Kinect, albeit one beyond the reach of most of us. Some students, staff, and professors at MIT have developed "hand detection" software using the Kinect's motion sensor. Below is a demonstration of this software. It recalls Tom Cruise's iconic scenes from the movie Minority Report.

Screw gaming, let's get to the serious stuff! Here's an amazing video of a Kinect hack that lets one see what its camera sees - in 3D.

You don't have to go the boring route with Christmas lights this year. Try hacking them, or better yet see if you can replicate this Tron-themed optical illusion made by WonderHowTo favorite Brusspup. Good luck... looks like it took some serious time and patience to get it right. More from Brusspup:

The iPhone and iPod touch are nearly identical devices, especially now that Apple has added a front-facing camera to the iPod touch. All that's missing is the phone part. With the help of Lifehacker and apps like Skype and Line2, you can save some money by turning your iPod Touch into an iPhone, without the need to jailbreak.

Life-giving internal organs! Usually, they're a convenience. Not so when making a convincing see-through Portal costume, however. Happily, Ben Heck has a devised an LCD-based hack that will permit you to tunnel through your belly without discomfort. Interested in vanishing your viscera? A full video guide follows below. Previously, HowTo: Top 10 DIY Nerdtastic Halloween Costumes.

Though only just released, the official Skype client for Android has already been unlocked. Thanks to xeudoxus of DroidForums.net, American Android users may now do what their European counterparts have been able to do all along: make free Skype-to-Skype voice calls over 3G.

Outside of being one of YouTube's most revered beauty gurus, Michelle Phan is resourceful to say the least. Kitty litter. Hot chocolate. Tomatoes. Aspirin. Eggs. Ice.
Check out this amazing use of AR via Wired http://theleakinyourhometown.wordpress.com/

Brusspup once again blows my mind (see previously below). His latest project is an extremely well executed animation, using a grid of tea candles to represent classic video games.

Via WonderHowTo World, Cinematography: Aerial photography company perspectiveAerials has captured incredible 360° footage of the Gulf of Mexico oil spill. The team launched their custom built Canon 5D Mark II aerial drone (see video two in the gallery below for a demonstration) from their boat in the middle of the Gulf of Mexico:

Well, only if you also happen to have an ARM powered LEGO Speedcuber device. Promotional video by maker David Gilday for ARM Ltd. With the help of the Android, the machine cracks the Rubik's Cube in 25 seconds (compare to LEGO Mindstorms solvers' 4 seconds.... or the human record of 7 seconds). Previously, Wow-Worthy Hack: Android Running on iPhone.

Congrats to MuscleNerd, the first to jailbreak the almighty iPad. Via DVICE:

Internet culture loves many things, but there are two web crazes in particular that always grab my attention: the notoriously addictive facebook game, Farmville, and the insane art of cake decorating.

Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject.

Magic Leap has some seriously awesome tech behind their augmented reality vision, and has made it a point to add a ton of adrenaline into the industry with a revolutionary focus on 3D layering. Today, they gave the public another glance at how they go about it. The image above displays the complete setup that Magic Leap uses to accurately capture someone's entire facial structure. The associated caption to this image reads: "This is where we study the 22 bones & 43 muscles of the face & head."

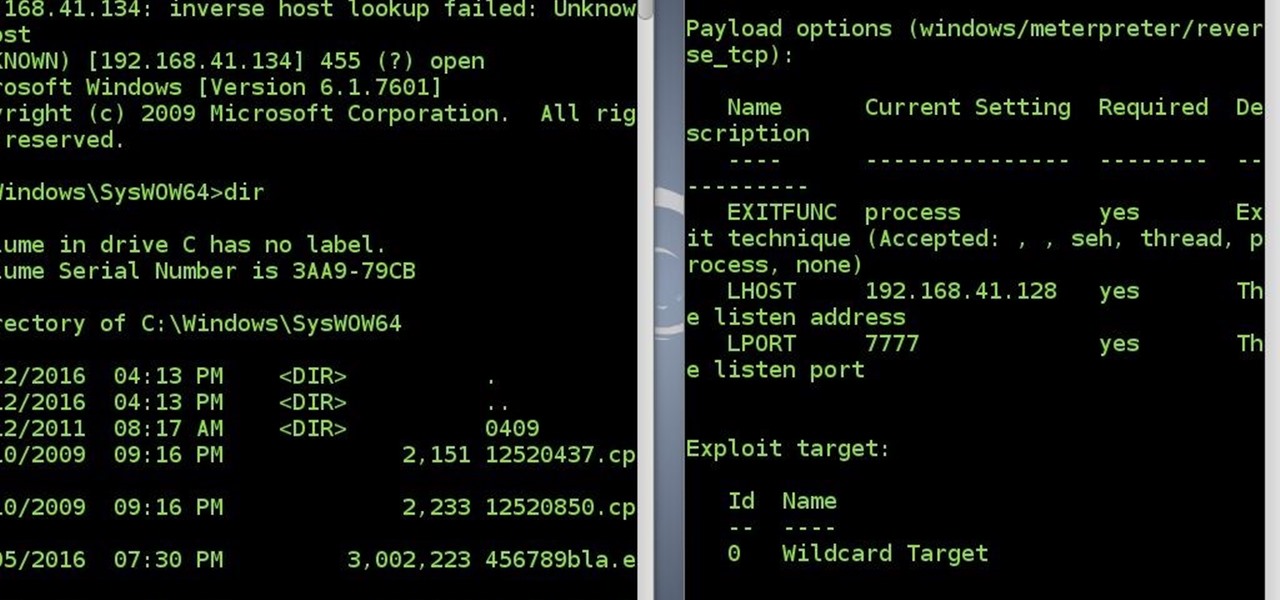
After a long time I succeed to reconnect to victim's system without a touch(the victim did not click the app again)

In an effort to prevent drones from being hacked, DARPA has been developing an "unhackable system," and seems to think they're almost there. The development team "proved" mathematically that their kernel was unhackable, and they hope to use it for more than just drones (power grids, cars, phones, pacemakers, etc.).

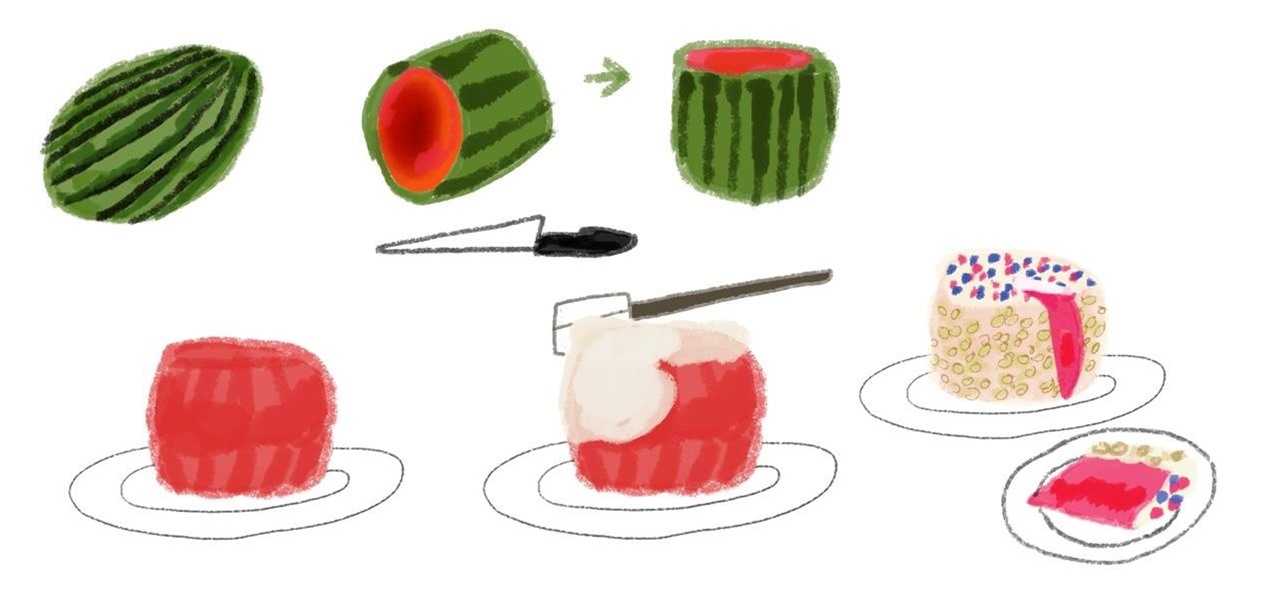
When it is too hot to use an oven but you want to have a dessert for a summer party, you can very easily make your own no-bake cake out of watermelon, whipped cream, chopped almonds, and fresh fruit.