Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

Eggs are a staple food for most Americans, which is no surprise, considering how necessary they are in savory and sweet recipes alike. On their own, they're usually not too eggs-citing. However, these clever egg hacks will make your egg-making easier, more fun, and more interesting.
T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

You know how when you finish a bag of potato chips, Cheetos, or some other glorious savory junk food snack, there's always some bits and crumbs in the bottom of the bag? And you know how you pour those into your mouth, making sure to get every last speck of dust, because it's the most delicious part?

The Galaxy S6 Edge comes with a useful feature called Information stream that allows you to view quick tidbits of info with a quick back-and-forth swipe on the edge of your display while the screen is off. Apparently, Samsung left the door open for third-party plugins to use this feature, and now we're starting to see an influx of useful additions.

Customization helps your device stand out from the rest, and that sentiment is no different when it comes to the Apple Watch. Unlike every other Apple device before it, the Watch allows you to customize the information that appears on the UI—without the need for any jailbreaking.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

The Apple Watch may be a much simpler device than your iPhone, but that doesn't mean it's free of bugs, glitches, and crashes just like your other devices. A common problem that you'll run into is a frozen screen due to a malfunctioning app. While this can be frustrating, the solution can be as simple as a quick reboot.

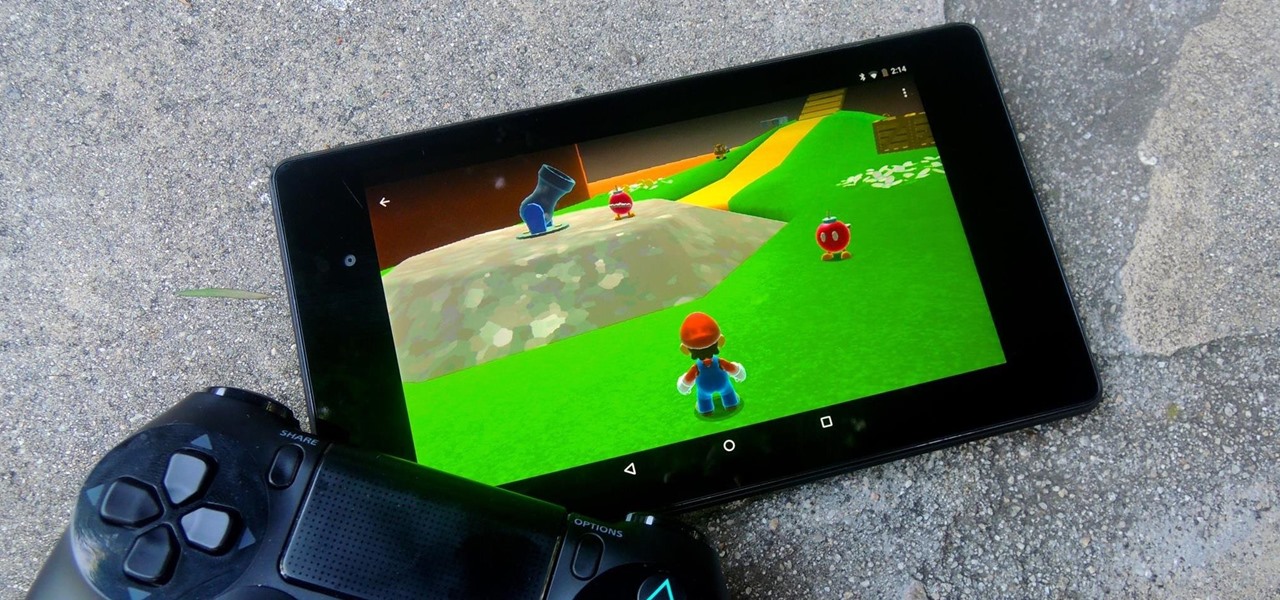
If you're jonesing to play some Super Mario Run on your Android phone, you might not be able to get your fix for some time—at least, until Nintendo figures out the best way to keep piracy down and security high. But if you can't wait for the first official appearance of Mario on Android, we've got the next best thing...

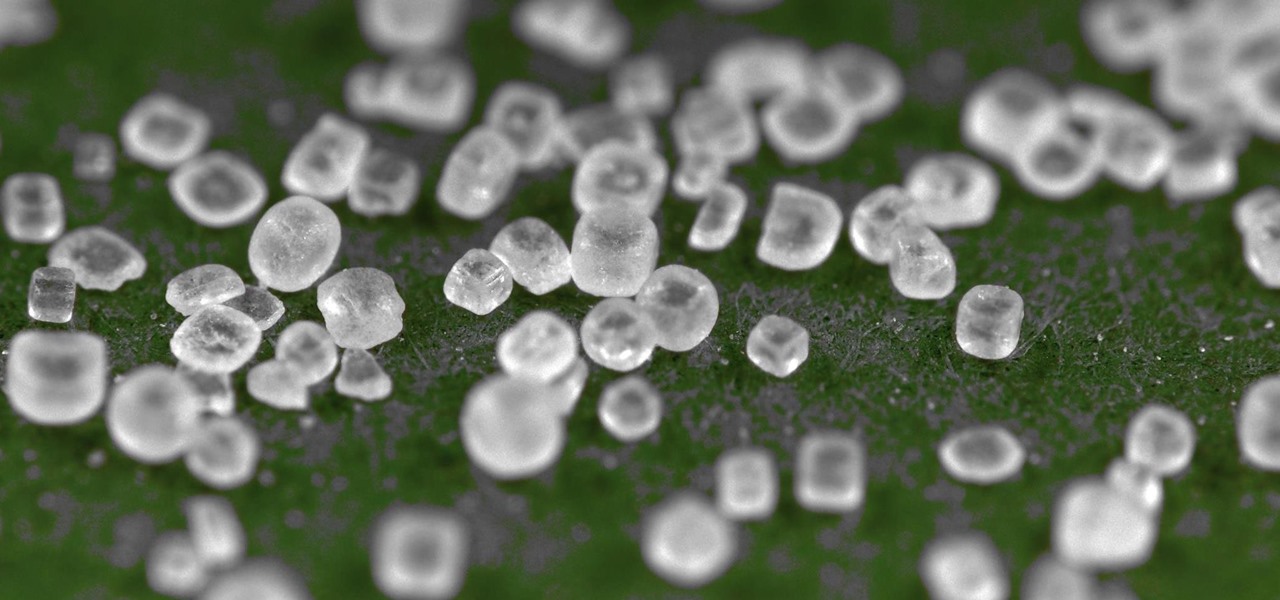
Salt is one of my favorite ingredients, by far, and also one of the most overlooked foods in the kitchen. This is probably due to the fact that it's an essential component of almost any recipe; because salt is a necessity, it's easy to forget how dynamic and versatile it can be as well.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Step 1: Introduction: Hello! Hackers

There are a few ways to successfully cheat on a test without getting caught, Here's one of them! Like most, office and school supplies will be needed. For this one though all you pretty much need is an eraser. By the time you're done with this hack, you'll be getting straight As for sure.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

Who says you have to cook on Thanksgiving? If you need a break, have surprise guests in town, or simply don't want to be in the kitchen cooking all day long, never fear: you have options.

In my opinion, the greatest food hacks are the ones that help you cut way, way down on dishwashing. That's especially true when it comes to baked goods, which usually involves dirtying up a couple of mixing bowls, measuring cups and spoons, some kind of stirring implement, and the baking pan itself.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Impress your friends with this simple yet great way to serve a watermelon. Perfect for parties. You'll never create triangle-shaped slices of watermelon ever again with this hack. You only need a watermelon (could also work with other melons), a sharp knife, a cutting board, and some friends!

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitchen cabinets to your bicycle can be improved with some Sugru and a little creativity, and gadgets are no exception. Here are 10 of the coolest hacks to fix or upgrade your smartphone, tablet, or camera.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Here's a list of the lifehacks shown in this video: Banana Foil

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

For most people, the battery life on a DSLR is more than sufficient, but if you want to do a really long exposure or time-lapse, one charge might not last long enough to get the shot you want. You can always connect it to an extension cord to charge while you shoot, but that can be really annoying to work around.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Want to learn how to build a robot out of Snap Circuits? I'll show you how to combine Snap Circuits parts from three different sets (the Snap Circuits rover, Snap Circuits Micro, and the Snap Circuits motion detector) to make a simple programmable motion activated robot. For a complete step-by-step build of the robot, visit my project at Instructables: http://www.instructables.com/id/Hack-the-Snap-Circuits-Rover/

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

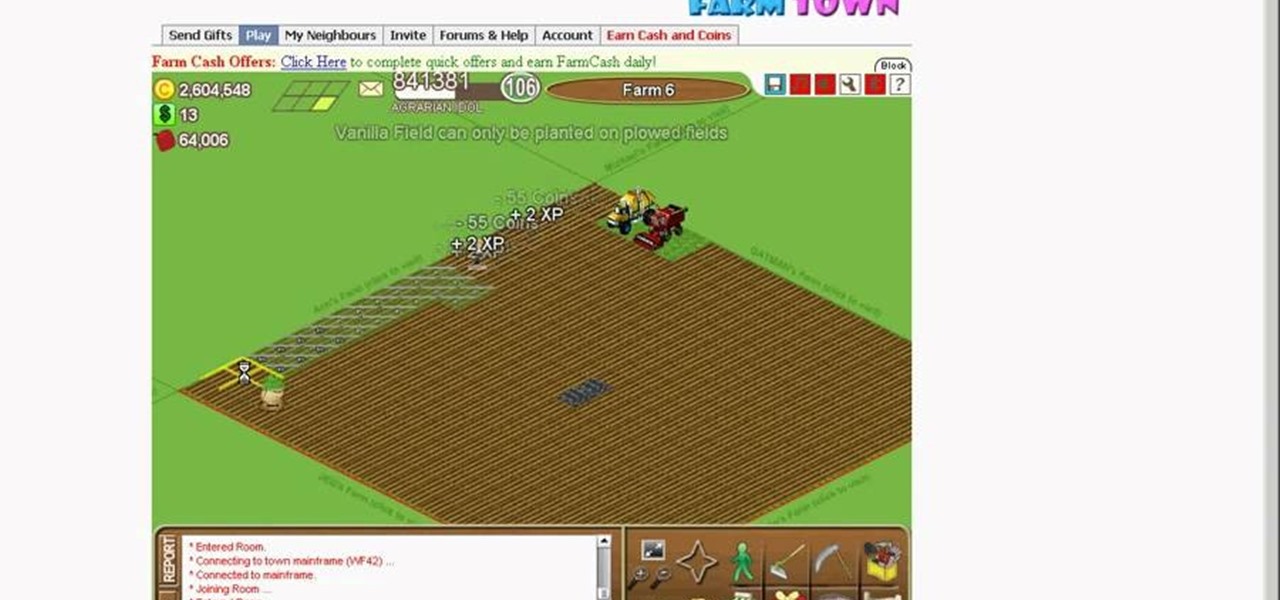
By overlapping your Farmtown crops, you can up the production output for your fields. There's a bit of a trick to being able to layer your crops in such a way that the game will allow. However, you can still manage to accomplish this without having to resort to cheat codes, mods or hacking the game. Just follow along with this tutorial - you can even keep your accessories like flowers and bird baths! Put your longest growing crop on the bottom.

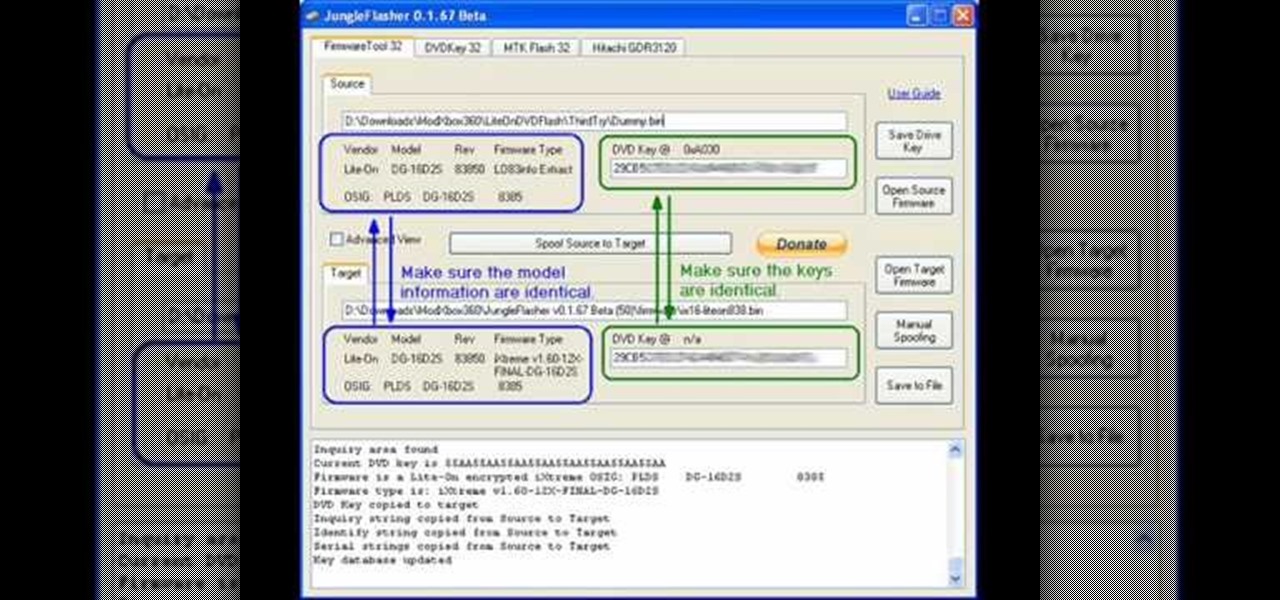
If you're tired of paying $60 for new XBox 360 games or waiting years for them to get cheaper, you should probably mod you system. This will allow you to play burned copies of games for free (no time to get into the moral implications here). The first step in that process is flashing your disc drive and installing custom firmware on it that will recognize your burned game discs. This video will show you how to flash the Lite-On drive used in many XBox 360's. If you don't have the Lite-On driv...

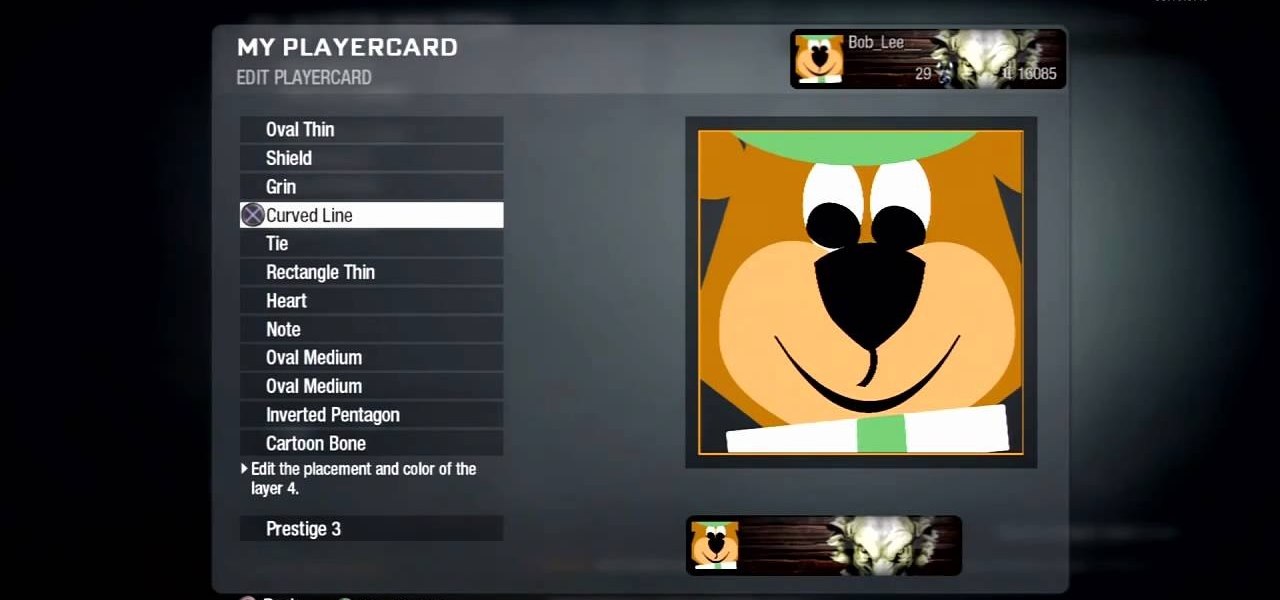
Are you smarter than the average bear? Show the world by using Yogi Bear as your Black Ops playercard emblem. This clip will teach you everything you'll need to know to draw a custom Homer Simpson emblem in the Call of Duty: Black Ops Emblem Editor.

Unlock the "Closer Analysis: Hidden Intel" trophy in Call of Duty: Black Ops! This achievement is won by finding the hidden intelligence documents in Missions 1, 2 & 4.