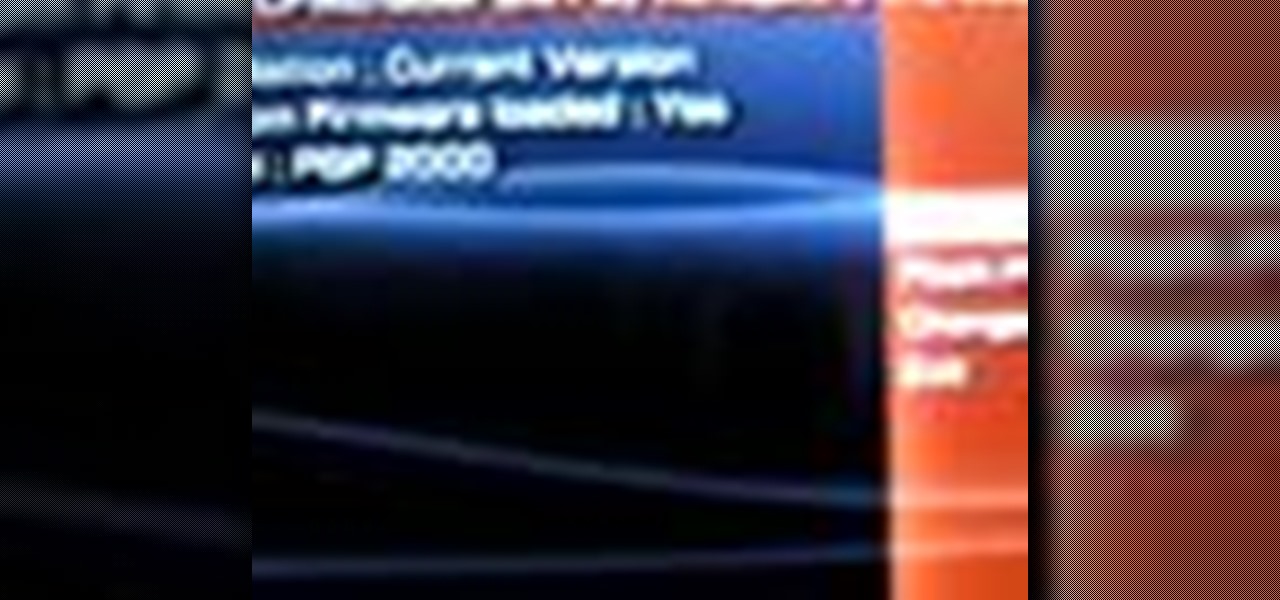
How To: Hack A PSP 2000 TA-88 V3 and PSP 3000
This is a tutorial on how to hack your PSP 2000 that has a TA-88 V3 Motherboard and PSP 3000 using ChickHEN R2 and CFWenabler 3.51.


This is a tutorial on how to hack your PSP 2000 that has a TA-88 V3 Motherboard and PSP 3000 using ChickHEN R2 and CFWenabler 3.51.
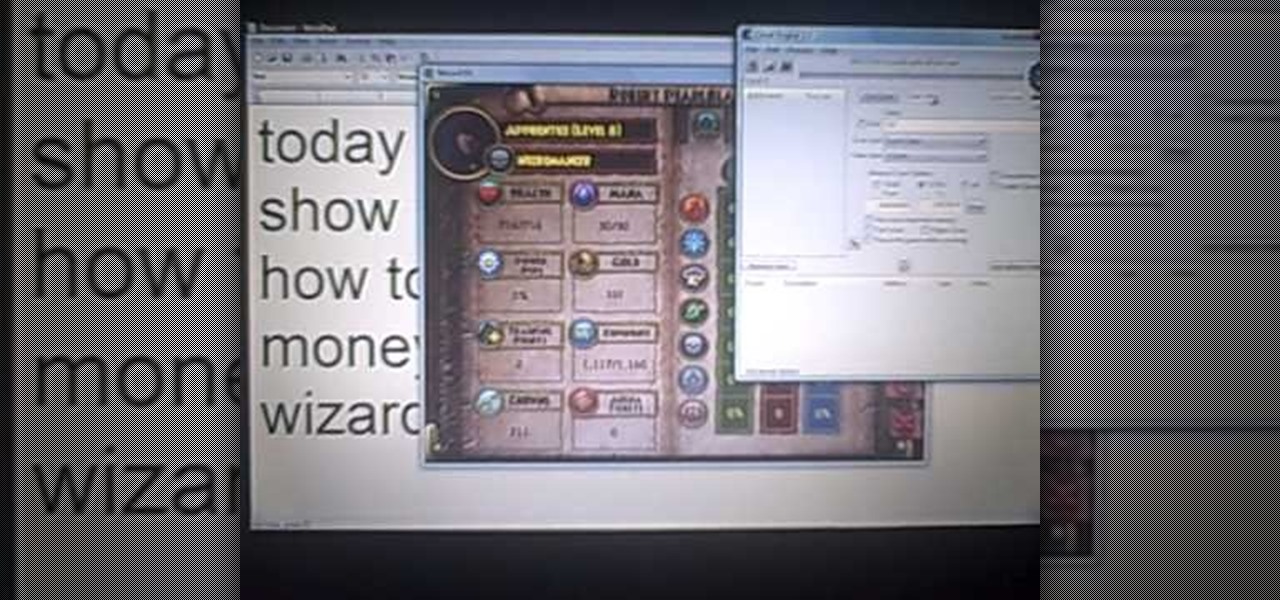
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 money with Cheat Engine (09/27/09).
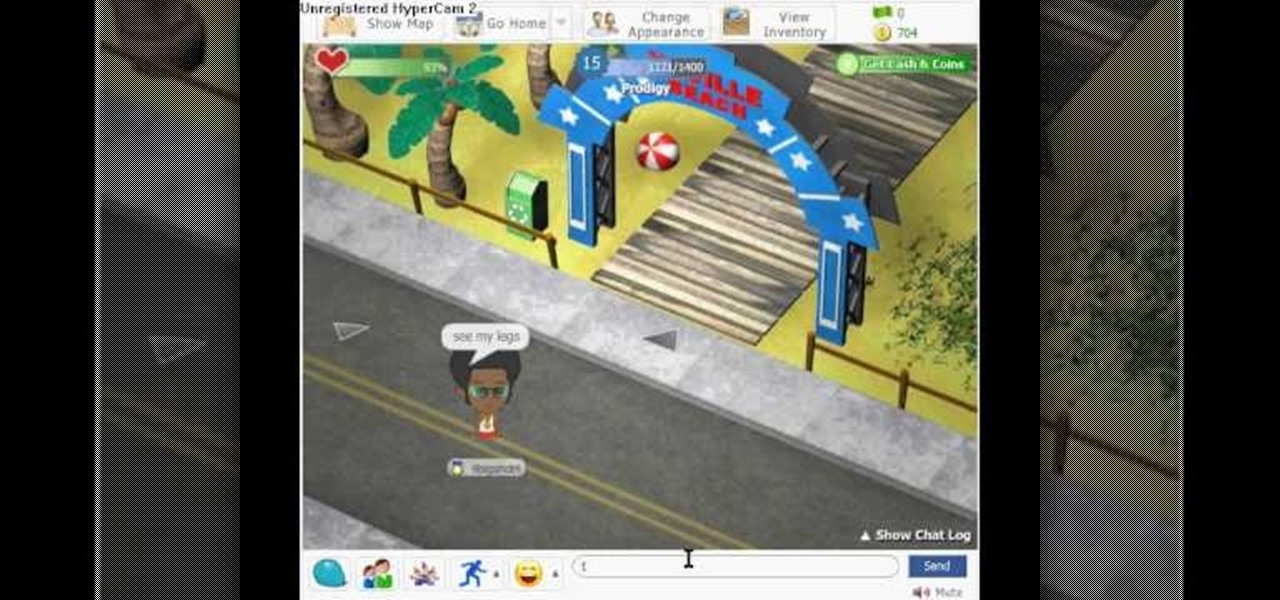
How to hack Yoville! Yoville cheats, tricks, hacks. Watch this video tutorial to learn how to fill water balloons faster in Yoville (09/06/09).
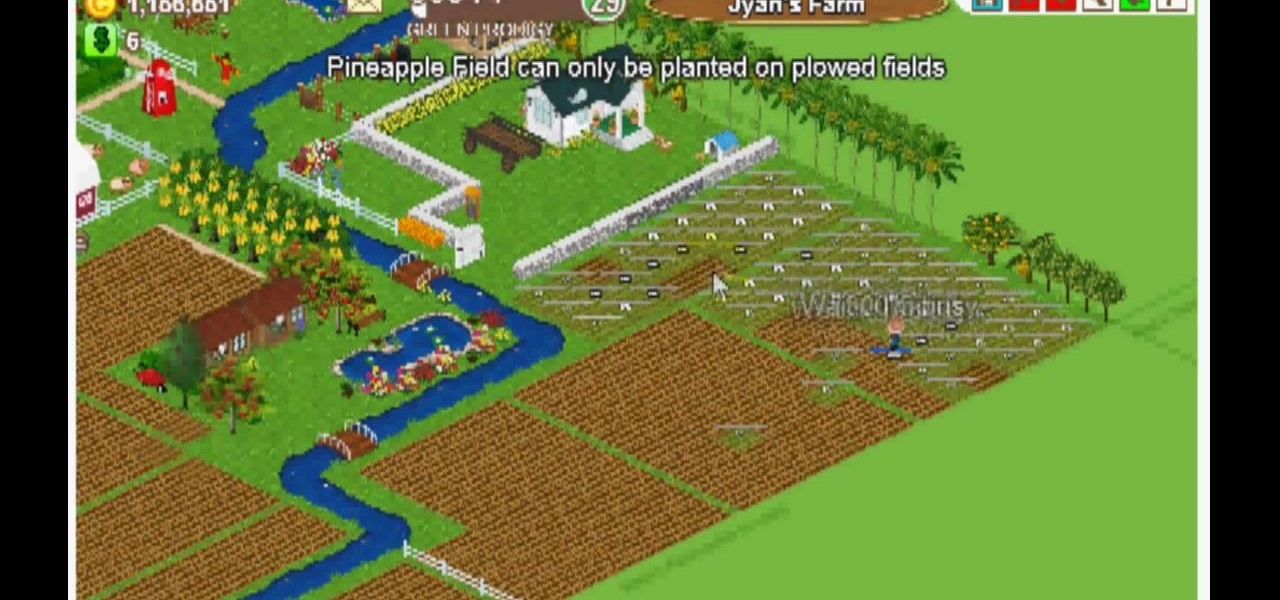
Farm Town hacks, cheats, glitches. How to hack Farm Town. Watch this video tutorial to learn how to save time plowing, speeding, and harvesting in Farm Town (09/09/09). You can click on the field a lot faster than your avatar can do them. Skip waiting for the avatar and complete your work faster.
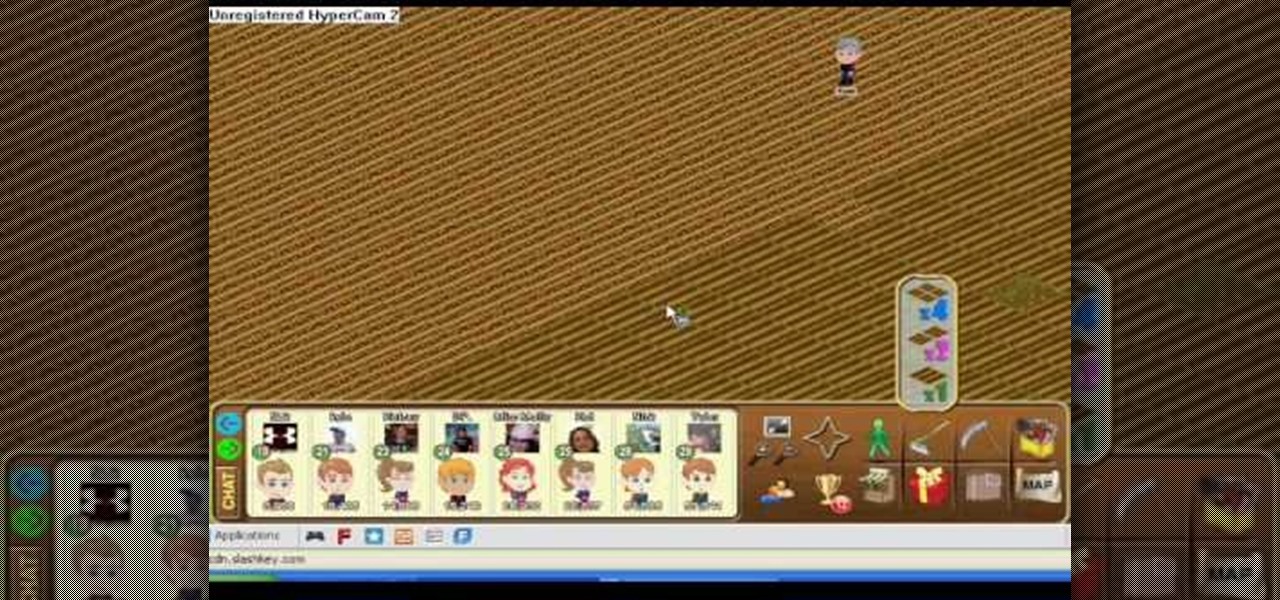
Farm Town hacks, cheats, glitches. How to hack Farm Town. Watch this video tutorial to learn how to speed plant (glitch) in Farm Town (09/01/09). This helps you plow and seed a little faster!
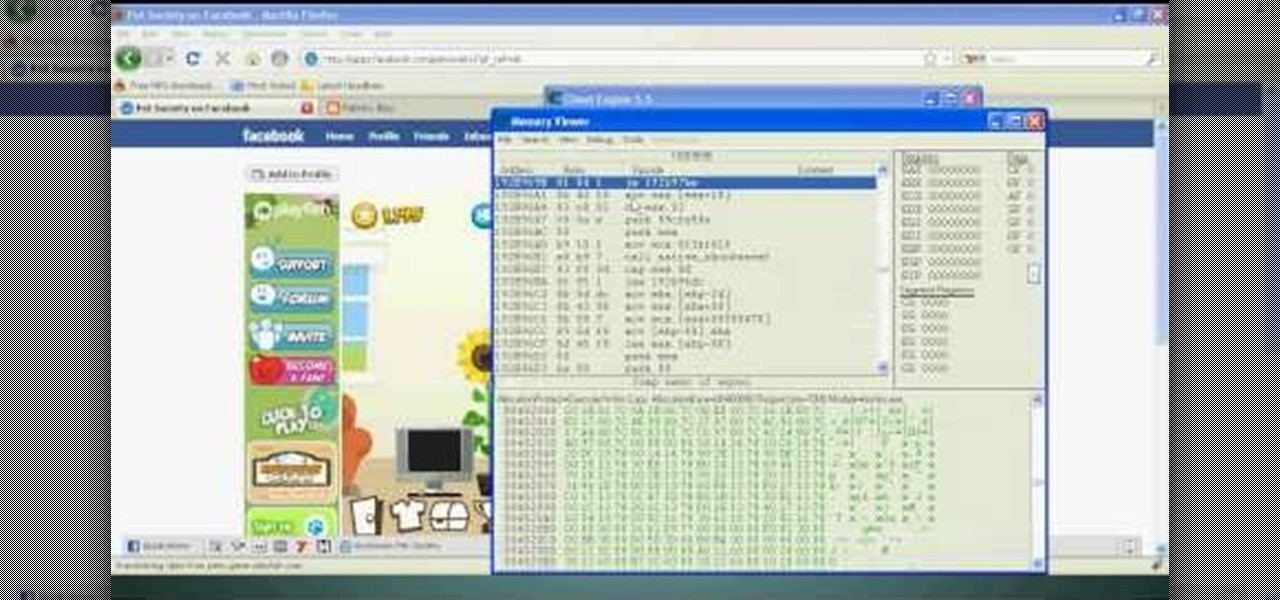
you will need :firefox , cheat engine 5.5 and adobe flash player 9.0 and you can get them from : http://www.mozilla.com

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to do a multi-cheat on Bejeweled Blitz.
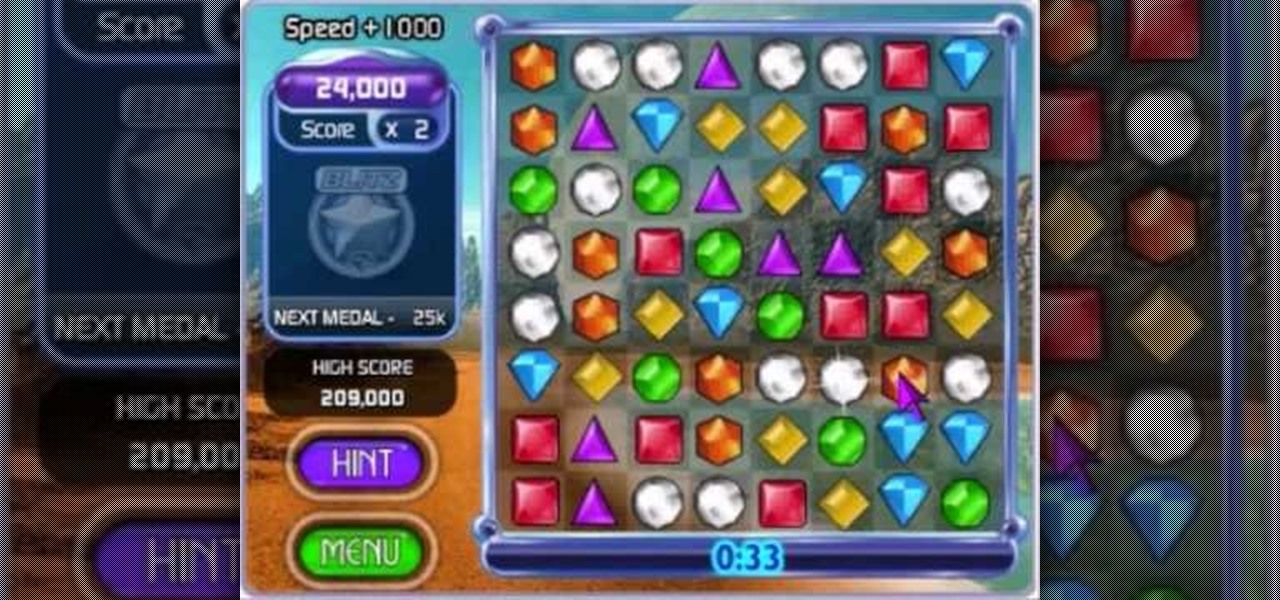
Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to master Bejeweled Blitz on Facebook. Score more points!

How to hack Yoville! Yoville cheats, tricks, hacks. Yoville is a game that can be played on Facebook or MySpace. In the words of Yoville's Facebook app, YoVille is a world where you can buy new clothes for your player, purchase items for your apartment, go to work, and meet new friends. Yoville is a city building simulation game.

How to hack Yoville! Yoville cheats, tricks, hacks. Yoville is a game that can be played on Facebook or MySpace. In the words of Yoville's Facebook app, YoVille is a world where you can buy new clothes for your player, purchase items for your apartment, go to work, and meet new friends. Yoville is a city building simulation game.

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to get a panther (wolf) in MyBrute (06/12/09). The panther (often called a wolf) is the strongest pet in the game. See how to get it and never lose again!
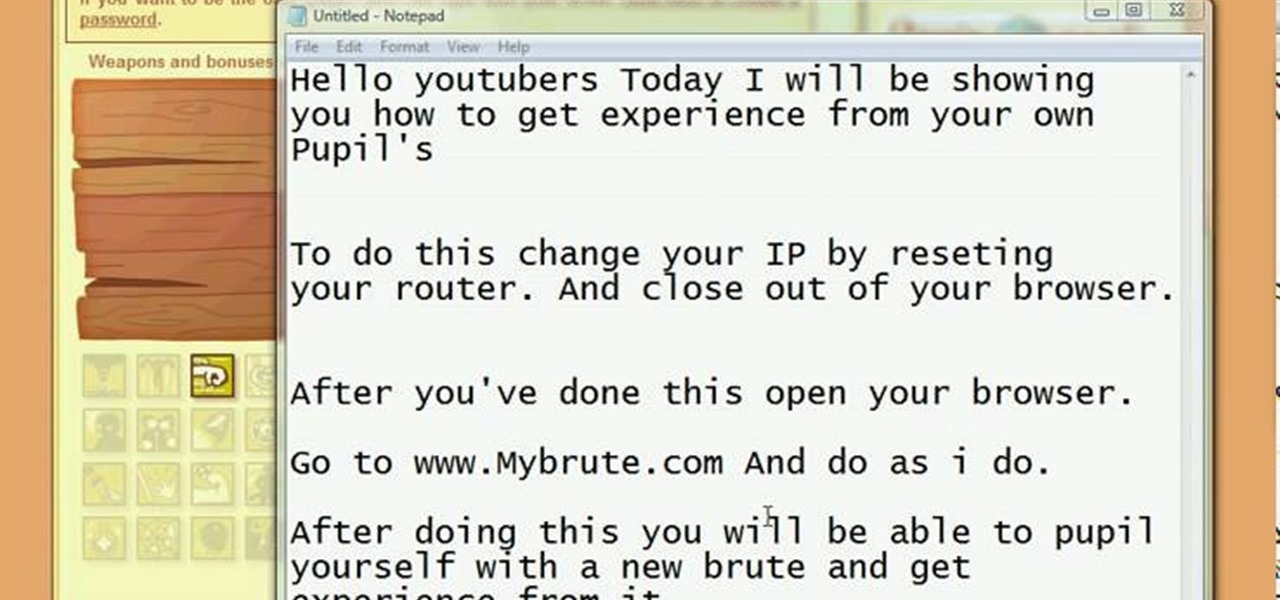
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. This video game tutorial will show you how to get experience from a MyBrute pupil glitch (05/24/09). This is a glitch so you get experience from your own pupils.
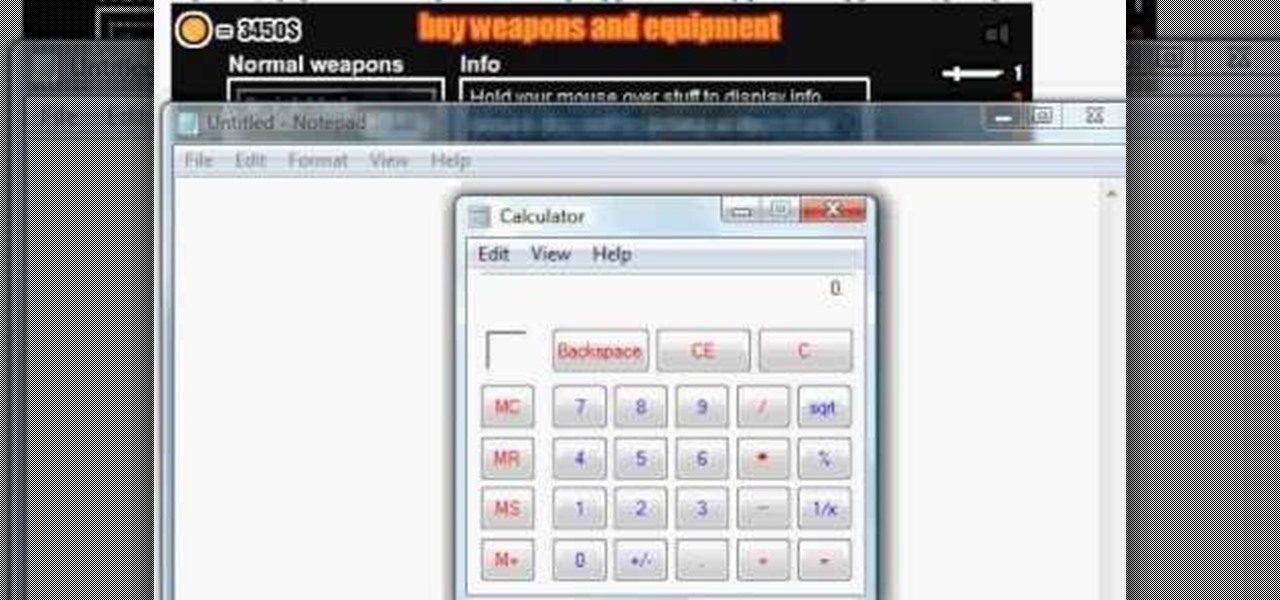
Ever wonder how so many people can blow you away at all of those Facebook games or other flash games? Well, there secret isn't good play, it's cheating... it's hacking... it's Cheat Engine.
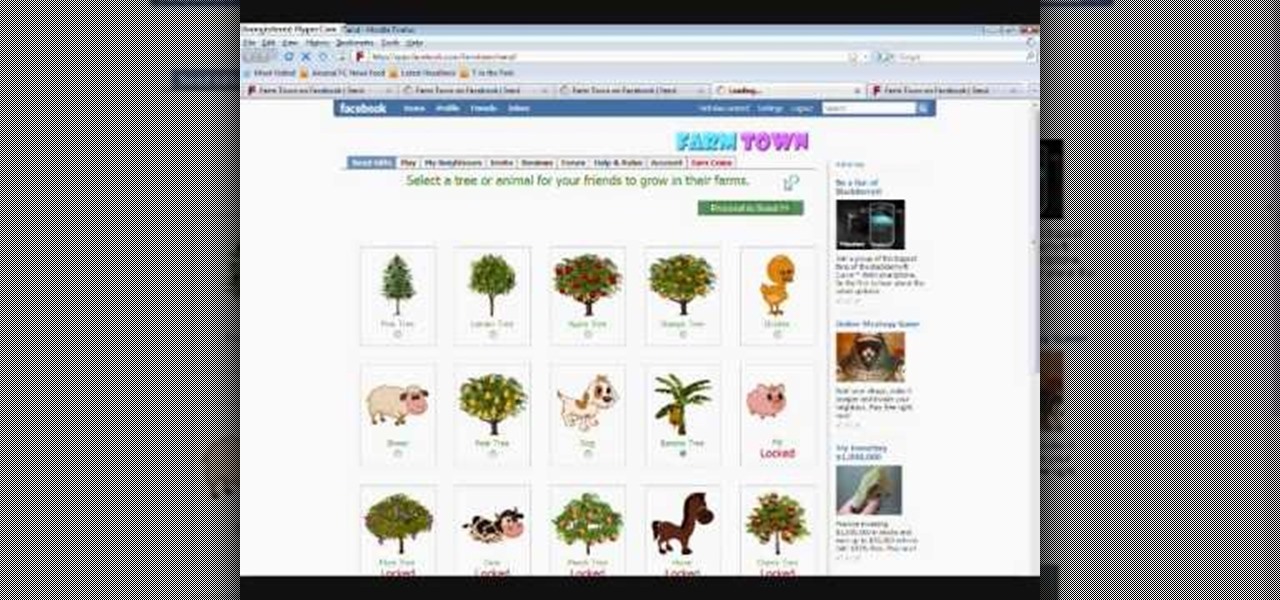
Cheat Farm Town for unlimited gifts. Farm Town hacks, cheats, glitches. How to hack Farm Town. Description of the app on Facebook:

Get into a menu in the Coke machine. This video offers the code for hacking into a Coke machine menu. This may not work for every machine, but should work for some.
VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.
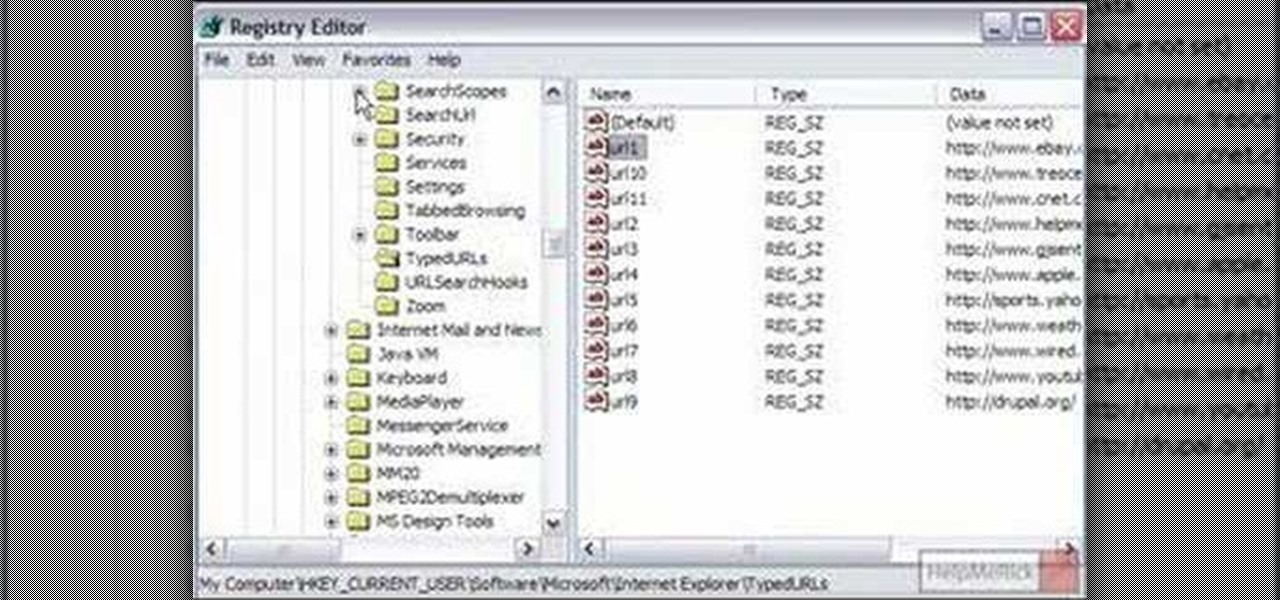
Ever wondered how to go about deleting individual entries from the Internet Explorer address bar? While it's possible, it's not particularly easy. You can do it all at once by purging your entire history through Internet Options or you can hack your Windows registry. For more information, or to try this hack for yourself, take a look!

Check out this instructional video to learn how to hack a prop ghost to fly continuously for your Halloween display.

This video tutorial is how to do the Chuck Norris Google hack. You don't find Chuck Norris, he finds you.

Follow these step by step instructions to learn how to hack a vending machine, giving you two Cokes for the price of one. You and your friends will love this cool vending machine con. Never go thirsty again. Just check out this instructional video and start hacking vending. Machines nowadays are SO smart that they know you haven't received your drink and give your money back. Humans nowadays are SO smart that we can make ourselves not receive drinks we paid for, get our money back, and then b...

Don't buy those $100+ laser pointers. Watch this video, and for under $50 you can make your own that is capable of burning, popping balloons, and cutting things!

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

One of the coolest things about Android is the massive development community behind it. These developers keep on cooking up new things even after official support has stopped for an older device. It breathes new life into somewhat forgotten devices, which is always great news. With Android 10 out, it's time to see what phones will get the custom ROM treatment.
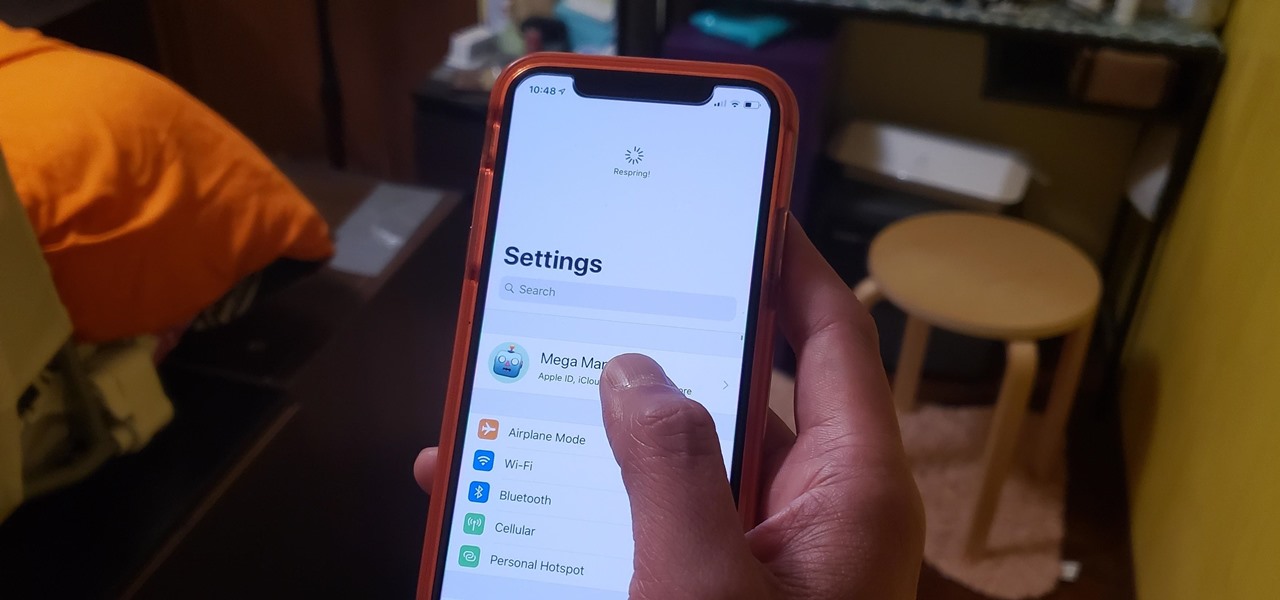
Restarting your iPhone can cure software glitches, but it should only be done as a last resort if your device has a semi-tethered jailbreak, because it will disable any tweaks you've applied. Luckily, your jailbroken iPhone has a faster alternative to rebooting to help you troubleshoot and make changes on the fly.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

It's an exciting time to be an Apple fan. Monday saw not only a major announcement of new Apple services and subscriptions but also the official release of iOS 12.2. If you're a beta tester, you probably watched 12.2's evolution over the last two months. Well, get ready to do it all over again — Apple just released the first developer beta for iOS 12.3 today, Wednesday, March 27.
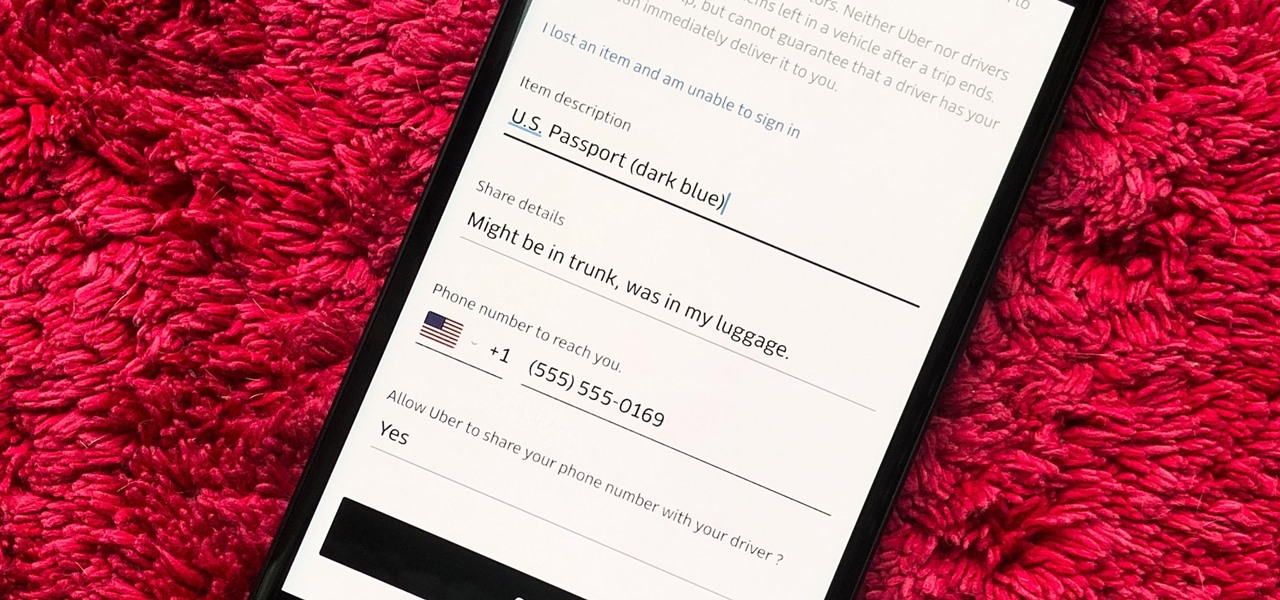
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and contact Uber directly if none of that works. But we're here to help make this process as easy as possible for you.
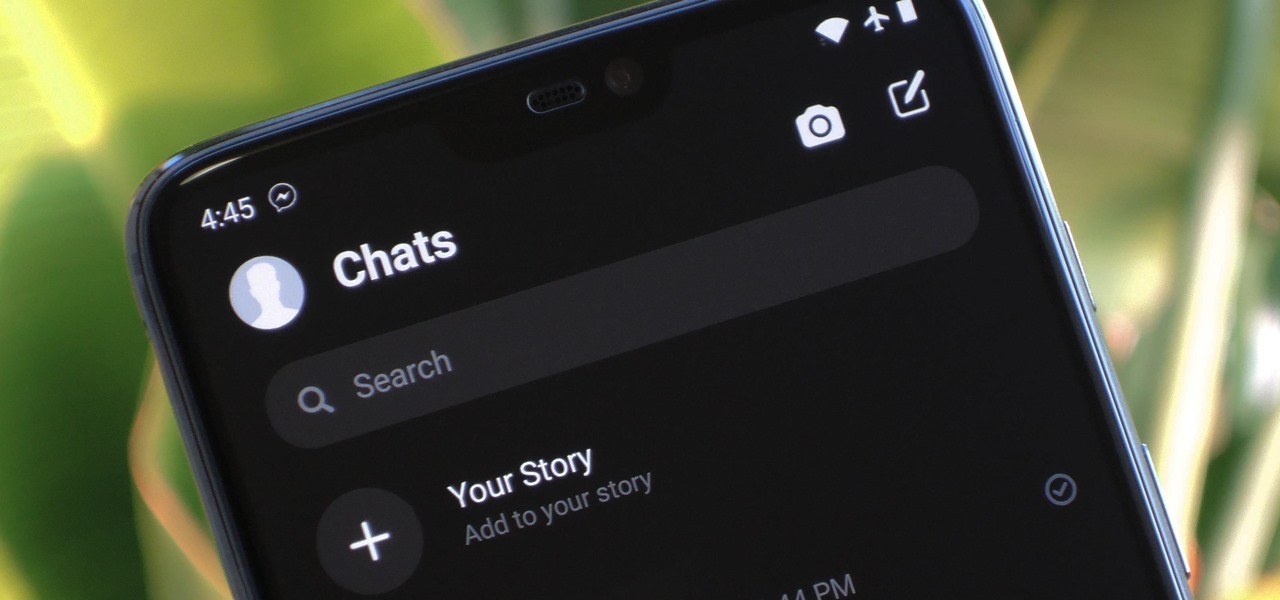
Facebook has a new dark mode for Messenger, and it's a true OLED black theme. It's was hidden away in earlier versions and you needed to either run a root hack or send a moon emoji to activate it — but now, you can enable dark mode by toggling a simple switch in Facebook Messenger's settings.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.
Thanks to Samsung's One UI, we can now experience firsthand what Android 9.0 Pie has to offer flagship Galaxy devices like the Note 9, S9, and S8. Perhaps one of the best features is something we've all been clamoring for: a system-wide dark theme that gives numerous apps and UI elements a custom look without having to resort to using a third-party theme.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.