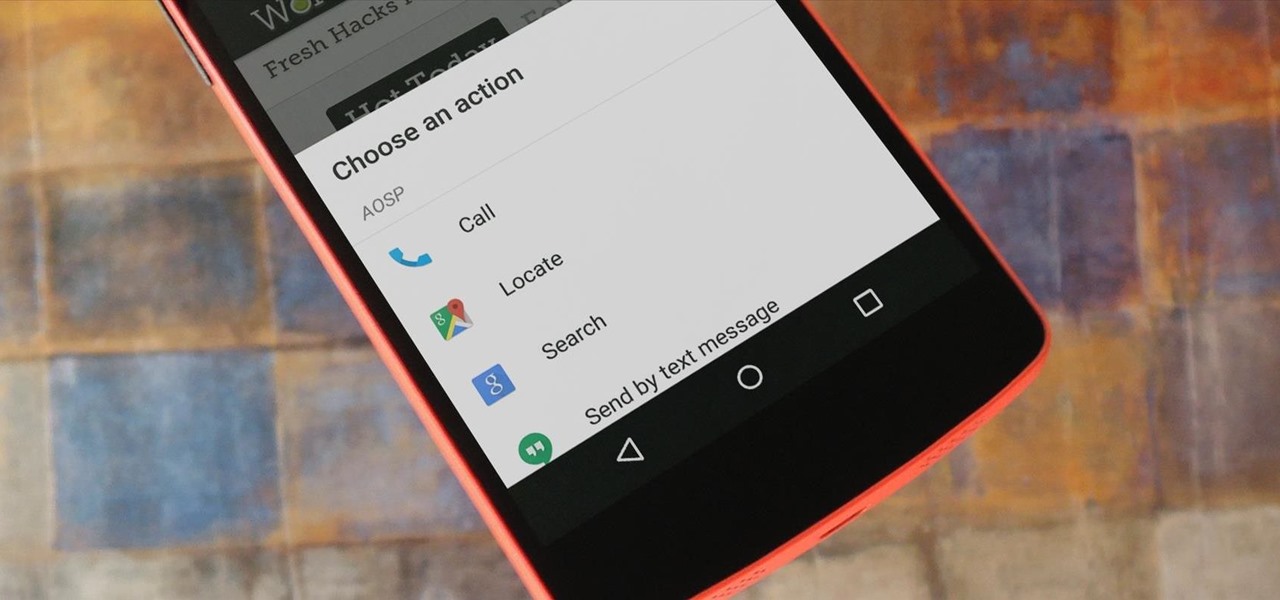
The buttons on most Android devices are laid out (from left to right) in a Back, Home, Recent Apps format. Samsung is the lone exception to this rule, which flip-flops them, so this can make for an inconsistent experience if you own multiple Android devices.
Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

There are a lot of frustrations when you're dealing with cramped living quarters, but you can do a lot of good cooking in your tiny kitchen if you make the most of your space. These storage hacks will make it easy to cook delicious meals, no matter how limited your square footage.

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).
The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

For the most part, when you're copying text on your Android device, it's because you intend on pasting it into a different app than the one you're currently using. For instance, you might be looking at a posting on Craigslist. So you copy the seller's phone number, then head to your home screen, switch over to your phone app, paste it into your dialer, and finally make the call.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

I always over-order when I call in for pizza delivery, because I love having leftover pizza. Because there's so much flavor packed into the sauce, cheese, and whatever toppings you've ordered, pizza adds flavor to salads, cocktails, and can even act as the base to a quiche. Press it into a waffle iron to make a pizza panini, cut it into triangles and make the best Bloody Mary ever, or use it as the base for a lively quiche.

Whether you live in foggy California or icy Massachusetts, you've more than likely struggled with a cloudy, vision-impairing window that makes even the shortest commute impossible.

As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.

Welcome back, my nascent hackers!

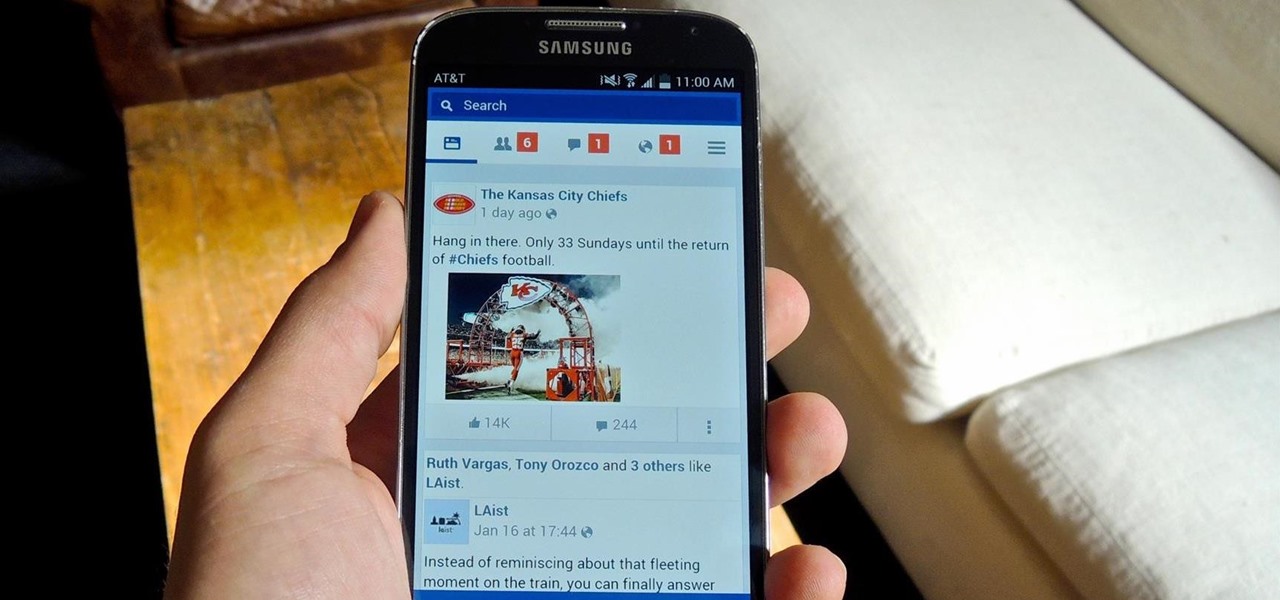
As one of the most frequently used and popular applications available, Facebook is now attempting to be a little more considerate for those Android users that don't have a bleeding-edge device or fast data connections.

Bow down, peasants: your gingerbread house just got owned. By whom? Martha Stewart, of course. The lifestyle guru has constructed elaborate gingerbread buildings in the past, but this year PBS asked her to build a gingerbread reproduction of Downton Abbey, in honor of the show's fifth season coming to PBS starting Jan. 4th, 2015. (PS: For those of you in the UK, the fifth season's Christmas special will be airing on Dec. 25th, 2014.) The materials included 11 batches of gingerbread, 16 cups o...

If you have ever attempted to mix and shape your own meatballs or burger patties, you may have endured bits of meat continuously and stubbornly sticking to your hands. This can make shaping more challenging than it should be.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Reminding a spouse or roommate to pick up some last-minute groceries is typically done with a quick message that can easily go unnoticed or unseen. Your feeble attempt of a reminder won't work unless it's conveniently sent at the right moment, like when they're on their way home. Chances are, you'll forget to text them and they'll forget the earlier reminder you sent.

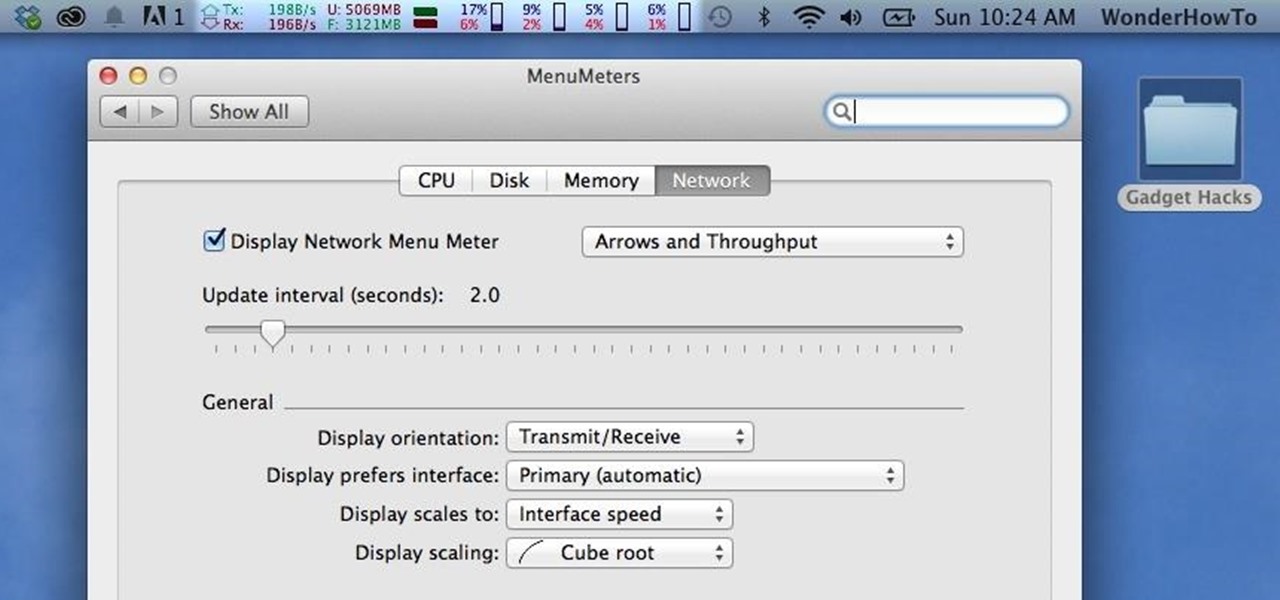
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

Despite what some in the tech-world would like you to believe, iOS isn't totally locked down, free from user customization. Take your home screen, for example. Not only can you change your app icons and move them wherever you'd like, you can actually choose to hide them all. If you have a wallpaper that's just begging to be shown off, this trick is for you.

Personality is something we're constantly attempting to inject into our lives, whether it be the car we drive or clothing we wear—and our mobile devices are no exception.

If you ever wanted to communicate with friends without having to deal with those pesky essentials like words and phrases, have no fear, Emoj.li is here!

Imagine this: You're driving on the freeway in Canada, enjoying the view and sipping Tim Horton's, when all of the sudden you see something out of the corner of your eye. You expect it to be a moose, obviously, but instead you see a robot with his thumb hitched up. So, after insuring that you didn't accidentally take some hallucinogens a few miles back, do you pick it up?

Peeling apples is pure grunt work, especially if you have a recipe that calls for a lot of 'em, like apple pie. You can make this task go by much more quickly if you use something from your tool box—your literal tool box, that is.

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

Since picking up your first crayon, chances are you've had a favorite, or dominant, hand. That hand gets you through the day, taking care of everything from writing to eating. If you've ever been forced to rely on your "wrong hand", you know how uncomfortable and unwieldy it feels.

Just like some of its popular puzzle predecessors, 2048 is an extremely simple yet insanely addicting game that pits you against a slew of blocks, to be configured into increasing sums with fervid, high-paced moves. If you have yet to play it, check out either the iOS (by Ketchapp) or Android (by Estoty) versions of the game. Due to its overwhelming popularity, dev TalkLittle has ported the puzzle game as 2048 for Chromecast (available for Android only), which lets you play the game solo or b...

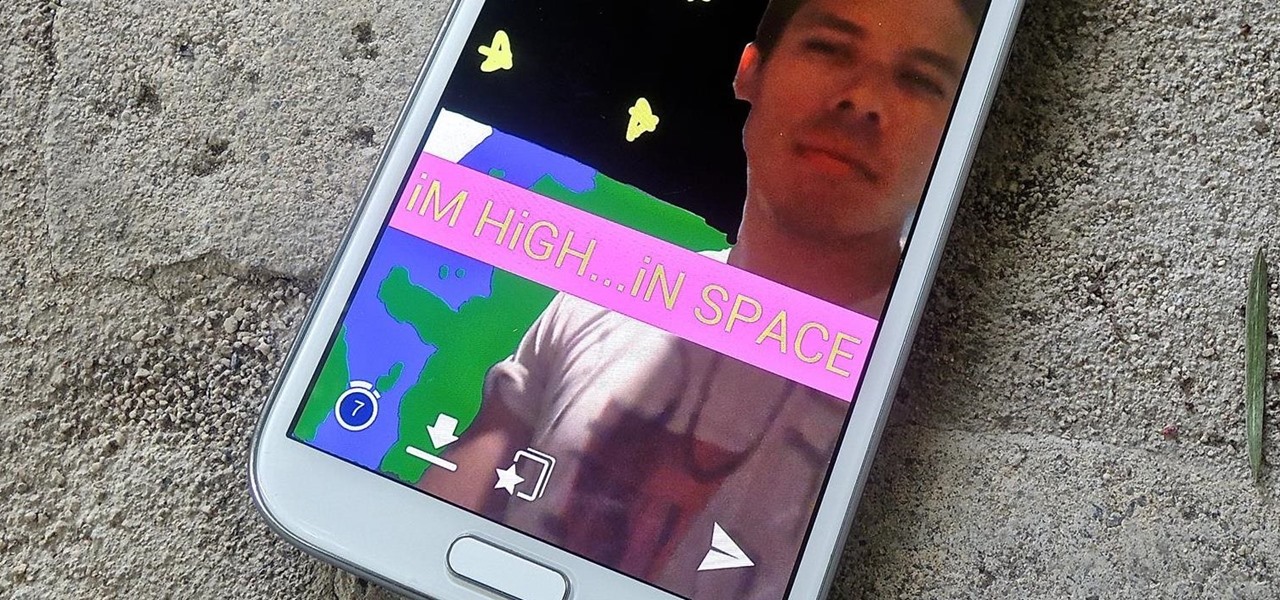
In an attempt to keep things simple, Snapchat has a limited amount of editing features, made up of "smart" photo filters, drawing pens, and special text captions. If you want more editing capabilities, you'll be pleased to know there's a way, no thanks to Snapchat, but you will need to be rooted.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

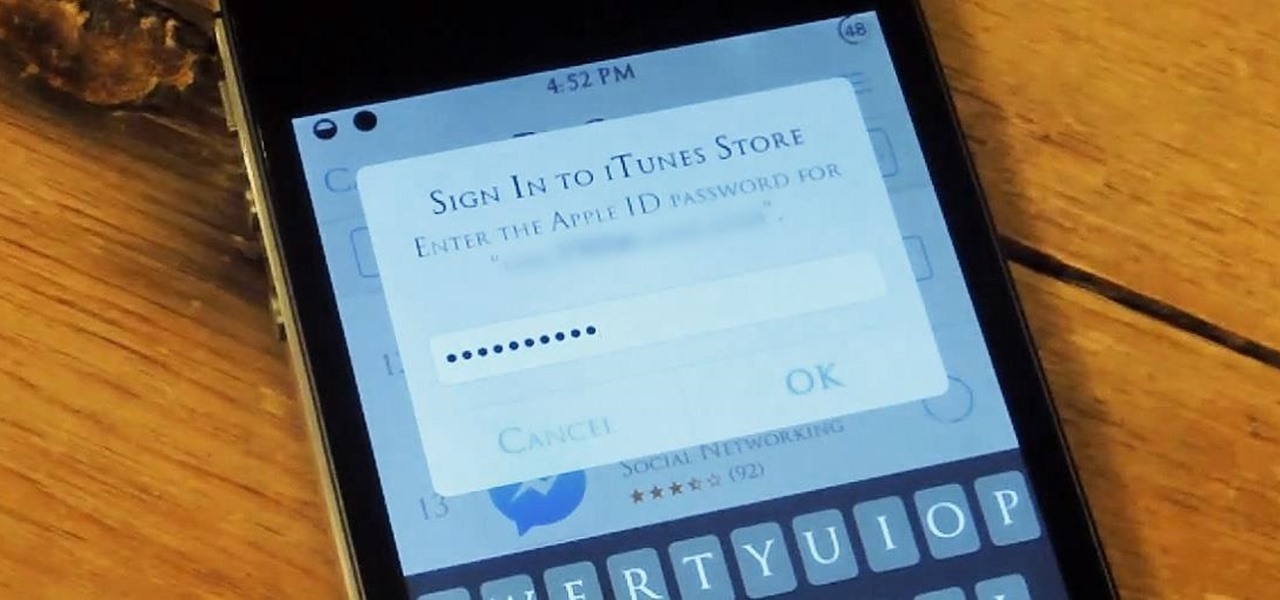
I hate typing in my password every time I want to install an application on my iPhone. My fat fingers make it so that I rarely get it correct the first time. If you're like my mom, you might not even remember it. Keyboard shortcuts are not a viable option either, since they are disabled for passwords.

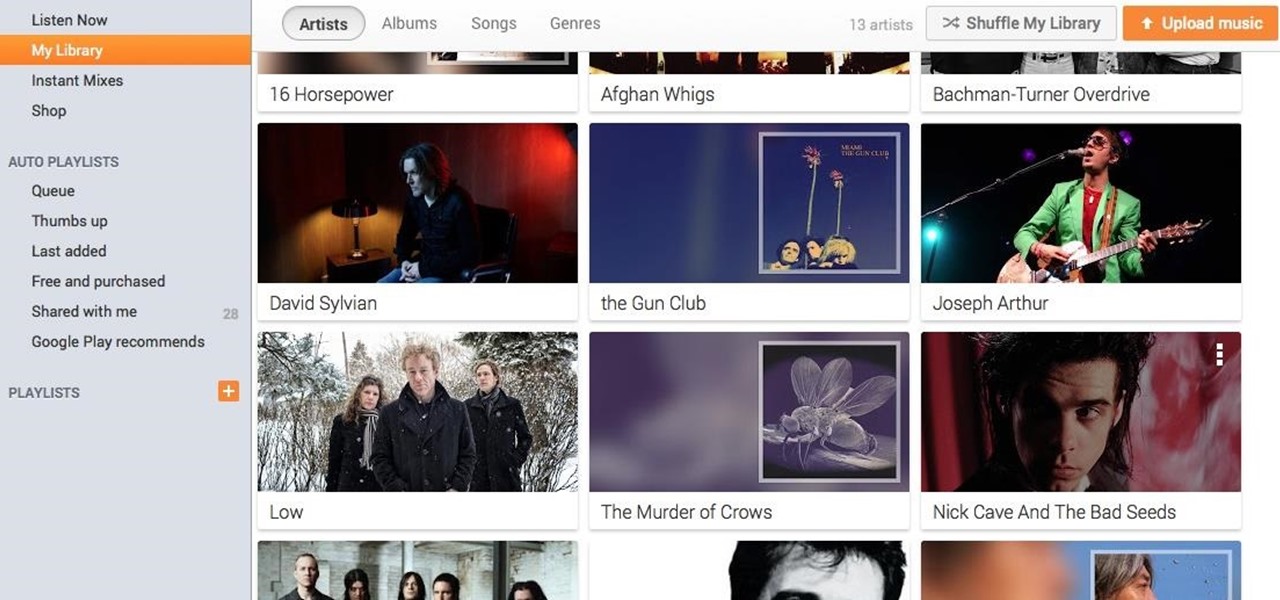
If you're a user of Google Play Music, but not a fan of being relegated to a browser tab, I've got you covered. Developer Sajid Anwar has created a desktop client for Google's music service, but since he made no attempt to hide logos and trademarks, it may not be long before the app vanishes completely. So get it while it's hot...and before Google takes it down.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Why can't Thanksgiving be a celebration of fireworks, too? This year, it can be with an innocent looking pumpkin pie that erupts an insane fountain of flames and fire! In fact, the pie filling is actually a flammable mixture of sugar and potassium nitrate, which was made using the same process as my DIY smoke flares with fuses.

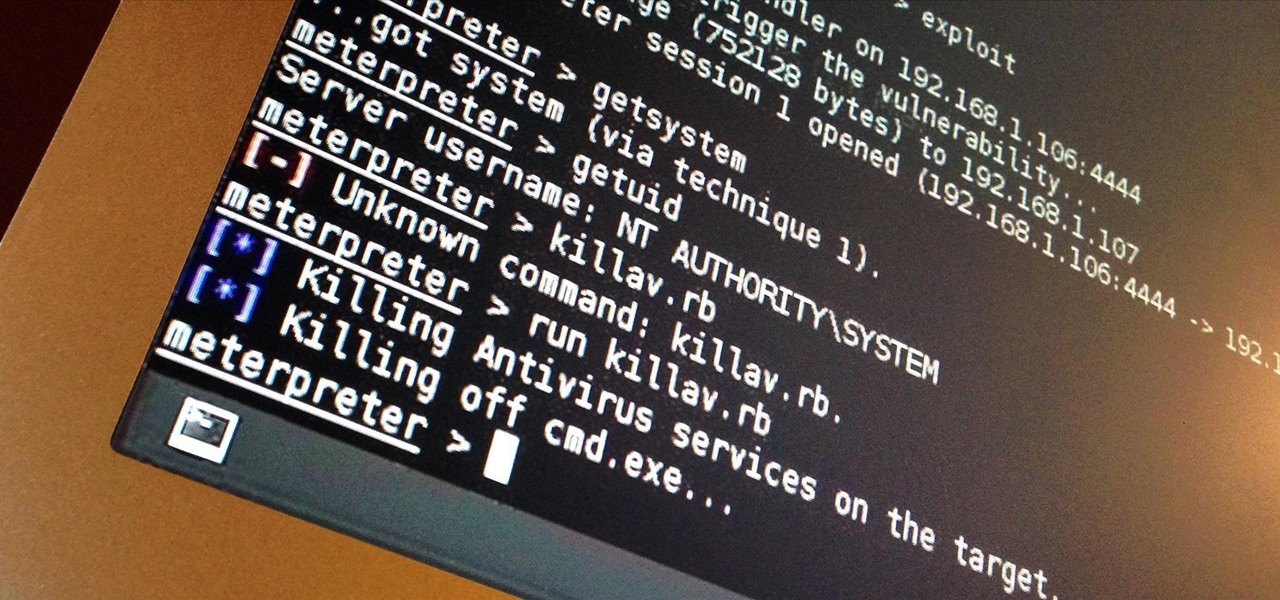
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!