
How To: Hack Fish World EXP (12/05/09)
sorry for no music youtube blocked it i should put a temp music. Cheat engine download link: www.cheatengine.org


sorry for no music youtube blocked it i should put a temp music. Cheat engine download link: www.cheatengine.org
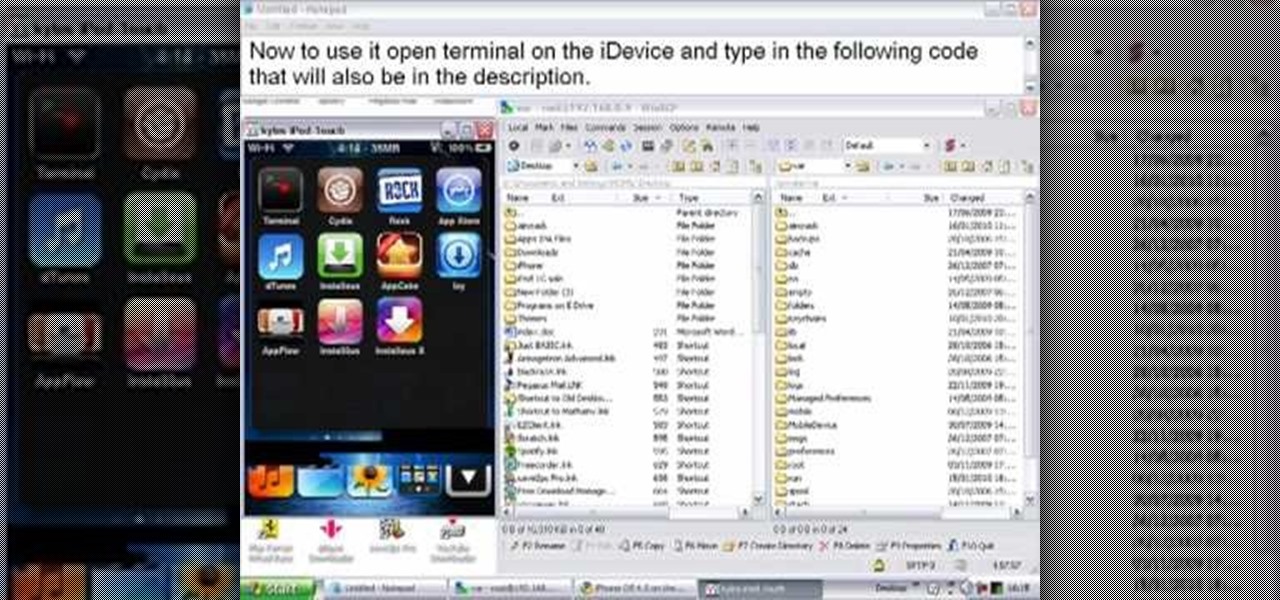
Learn how to install Aircrack on your iPhone to hack into almost any WiFi network. First download Aircrack from iHackMyi, then follow these steps:
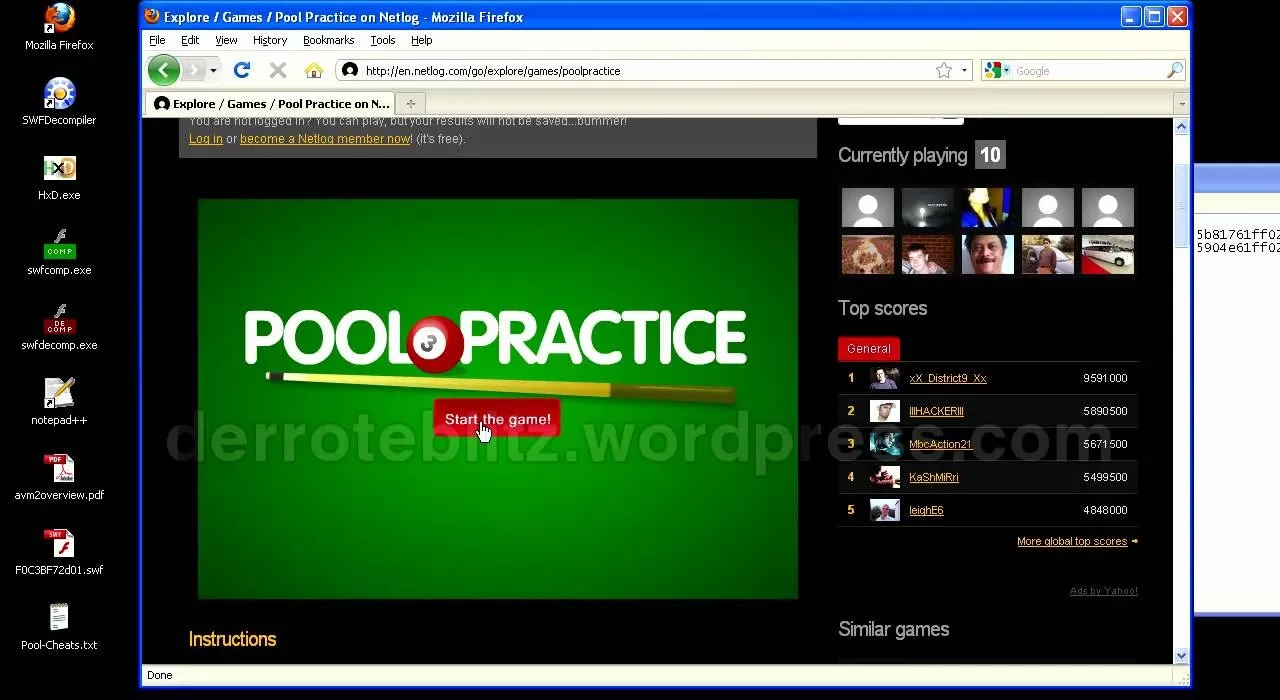
You want to know how to get extreme scores in the flash game Pool Practice? This is how. Watch this video tutorial to learn how to cheat in the flash game Pool Practice (01/01/10).

Know where the Dojo in the Courtyard is on Club Penguin? Then did you know you can walk on top of it? It's a cool little glitch that you can without getting banned from Club Penguin or anything like that. It's just a simple Club Penguin glitch.

FarmVille hacks, cheats, glitches! FarmVille is the hottest application on Facebook which lets members manage a virtual farm by planting, growing, and harvesting crops, trees, and livestock. Grow delicious fruits and vegetables and raise adorable animals on your very own farm!

Worried about not being able to get Cydia on the 3.0 firmware? Never fear! Hackers are here! Check out this video to learn how to jailbreak your iPhone using redsnow to get Cydia. With Cydia, a whole world of iPhone and iTouch hacks and cracks are at your fingertips!
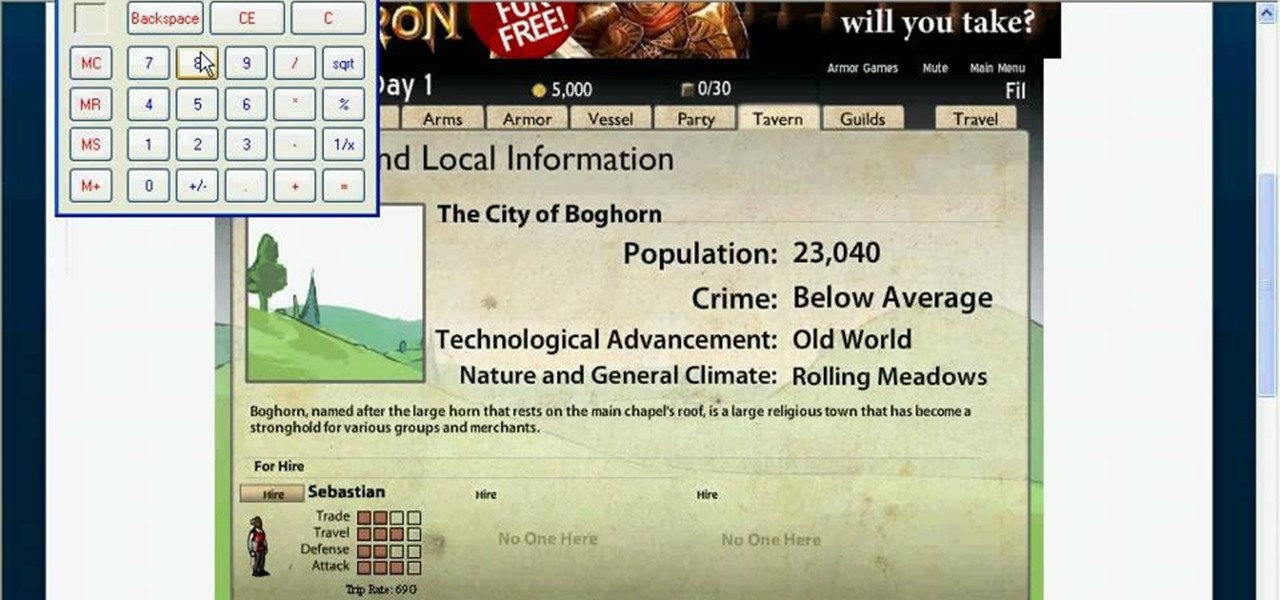
Frontier is a flash game from Armor Games. Learn how to hack Frontier with tricks and cheats. Watch this video tutorial to learn how to be rich on Frontier with Cheat Engine (09/13/09). See how to get an infinite amount of gold on Frontier.
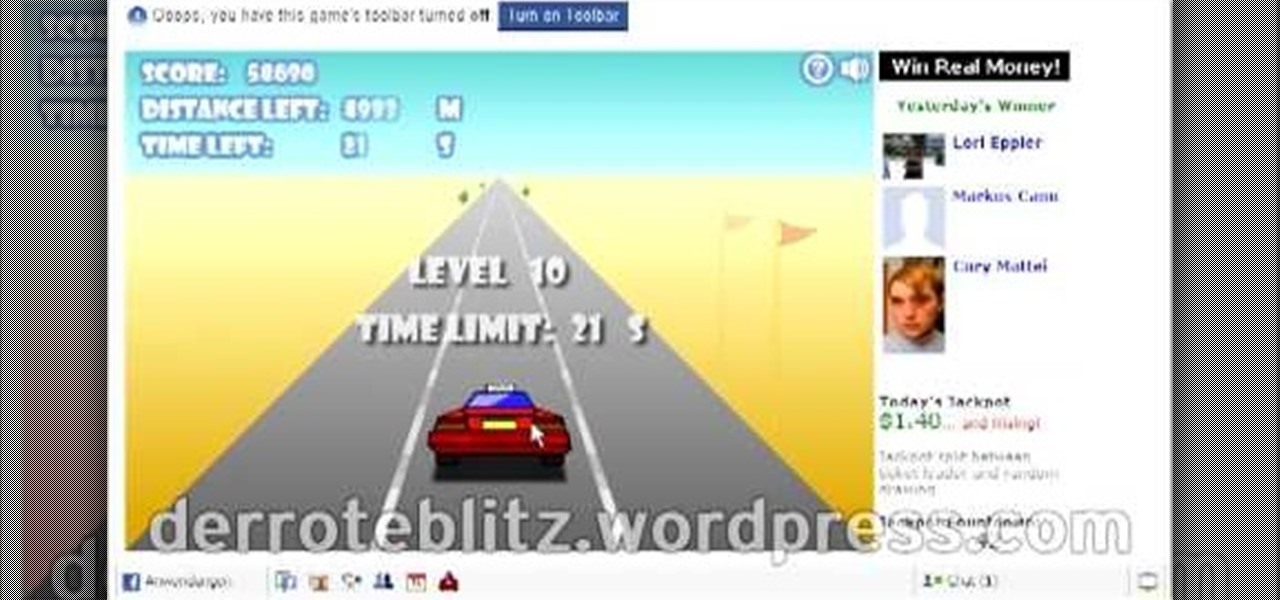
Crazy Taxi is a Facebook game that allows you to drive crazy in a cab. Watch this video tutorial to learn how to cheat and remove the traffic on Crazy Taxi (08/17/09).
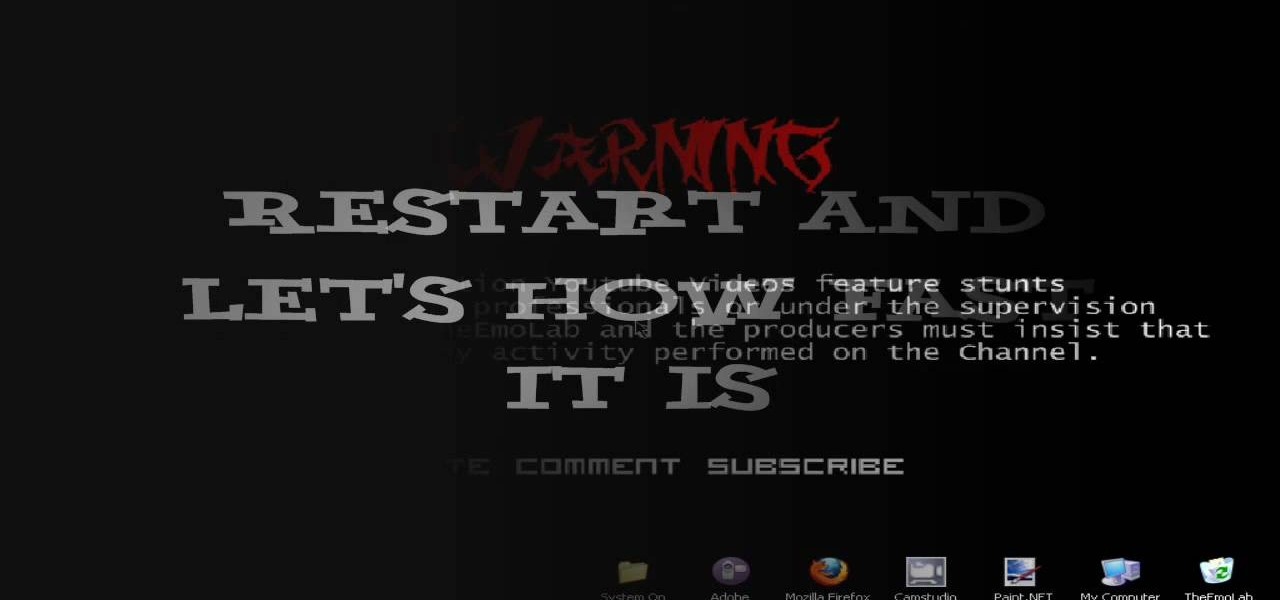
Check out this cool hack from The Emo Lab. This video tutorial will show you how to speed up Internet Explorer!
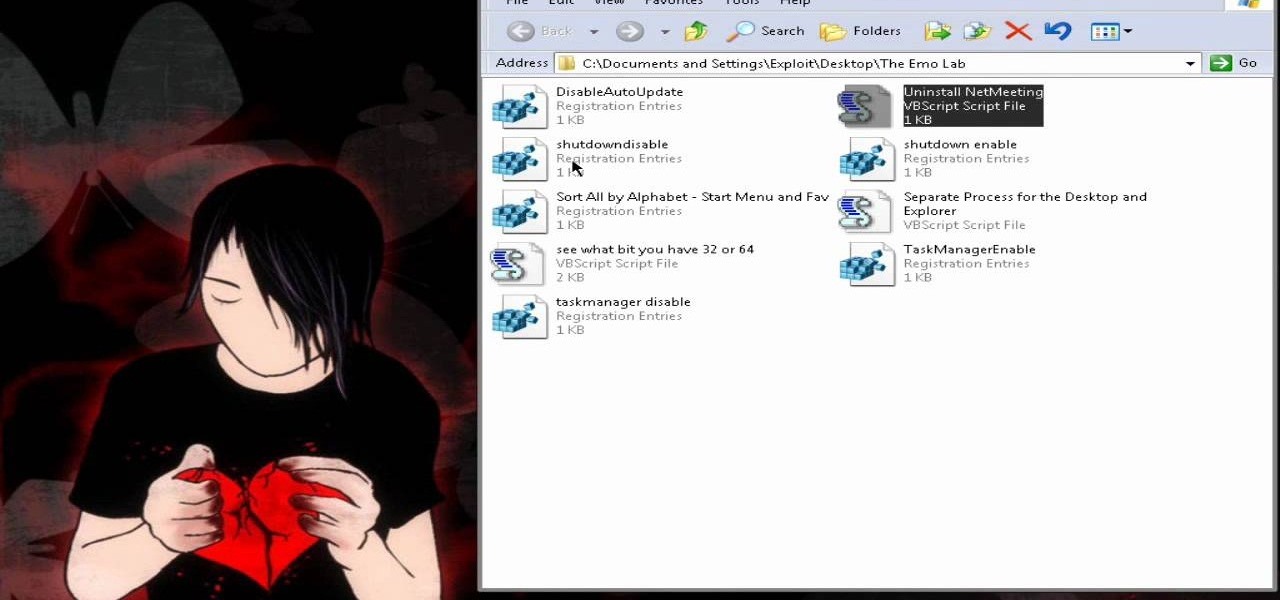
Check out this cool hack from The Emo Lab. This video tutorial will show you how to boost performance in Window XP!

Watch this great cooking video on how to cook Indian shrimp biryana, which is a Goan rice dish. If you’re tired of the same old biryanis, try this Goan-inspired recipe for shrimp (prawn) biriani. With the creaminess of coconut milk and freshness of mint, it’s the perfect combination!
How to play Facebook's Farm Town. Description of the app on Facebook:

Not a great lock picker? Well, get some help figuring out how to break into padlocks and high security locks -- check out this video tutorial on how to open locks with comb picks. Comb picks are one of the best ways to hack into these common everyday padlocks. It's not a foolproof way to pick locks, but it's great when it works.

This is a really simple video guide on how to install Hackintosh OSx86 (Mac OS X) on a PC. OSx86 is a portmanteau of OS X and x86, a so-called collaborative hacking project to run Mac OS X computer operating system on a non-Apple brand personal computer, with x86 architecture processors.

Sparky is a wireless, web-based video-chat robot from the Gomi Style crew. You can learn how to make your own Autonomous Telepresence robot using spare computer parts, some old toys and a bit of custom software (that we provide at gomistyle.com). This robot is operated with a Make controller circuit board. Sparky is a retired electric wheel chair with a monitor as a head.

This cheese cutting tip is for optimal enjoyment and minimal crumb. Avoid massive hacking; slice the cheese up like a pro for your guests. Watch this how to video to learn how to cut hard cheese.

This fuel conservation tutorial will teach you a simple hack that will battle $4 a gallon, with magnets. Learn how to boost gas mileage and increase fuel economy by installing fuel line magnets in your vehicle.

Looking for a new plugin for your PSP? Watch this video to learn how to listen to music on your Playstation portable while playing games. This hack requires custom firmware 3.90m33 or higher on your PSP.

This video will teach you the basics of payphone phreaking. Pay phone phraking involves doing various pranks and hacks to pay phones.

This how to video has whole food recommendations for relieving depression from a nutritional and herbal perspective. Watch and learn how simple it is to prevent and beat depression with a wide variety of fruit, vegetables, and whole grains. Avoid caffeine and make an attempt to incorporate leafy greens into a diet.
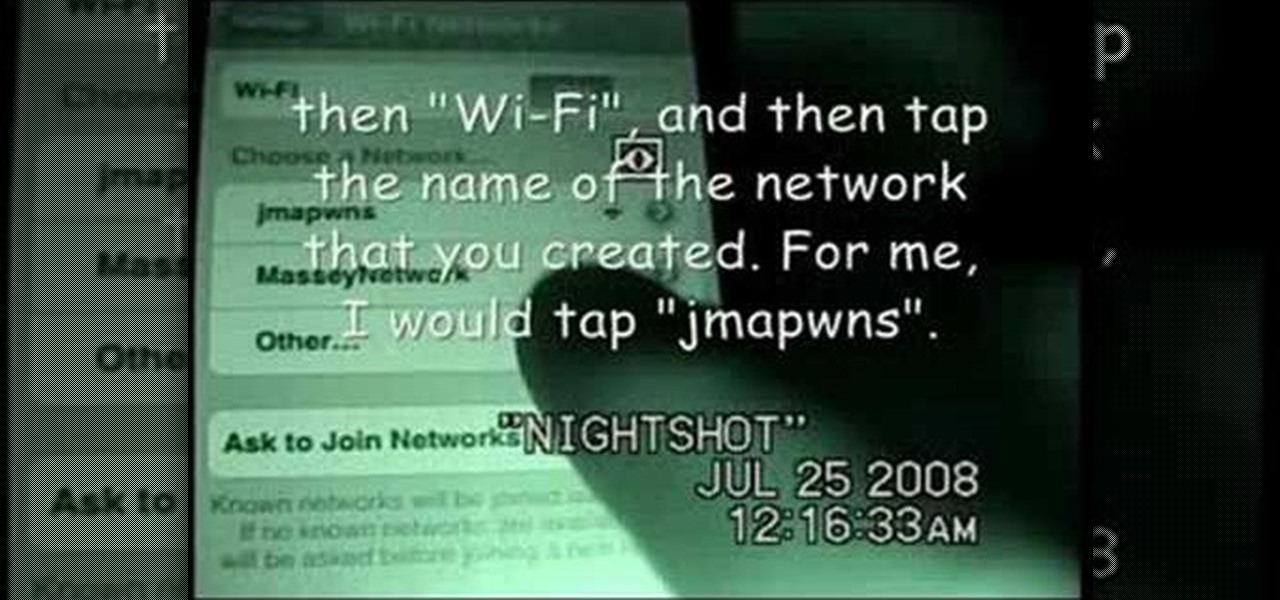
This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration steps required to properly tether an iPhone 3G in Windows XP so that you can use its EDGE or 3G internet connection on your PC, for free.

This video teaches you how to do a back flip on a swing. Doing back flips can be dangerous so make sure you are supervised by a professional before attempting to this on your own.
If you are having trouble getting your hotmail on your iTouch, check out this video. It's safe and easy, without giving somebody your personal info. This is the 32GB version, but it should work for all iTouches as well as the iPhone.

Get tips from this video to learn how to fillet a hack fish. You need an extremely sharp knife to cut it. Start at the head and turn the knife around.

This video shows you how to make an elevator go directly to your floor while skipping all other floors.

Big Tony the plumber shows you how to install an ice maker kit. You can go to any home center to buy an ice maker kit. You need a little hack saw and a couple of wrenches.
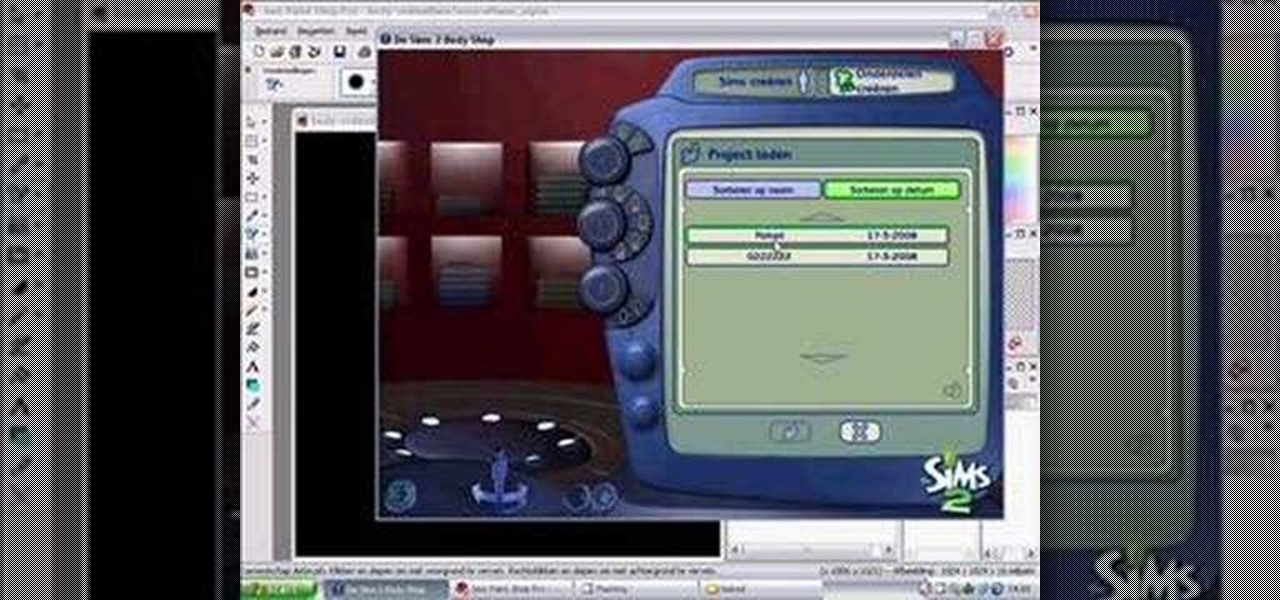
Here's a hack to make your sims look naked in The Sims 2 game.
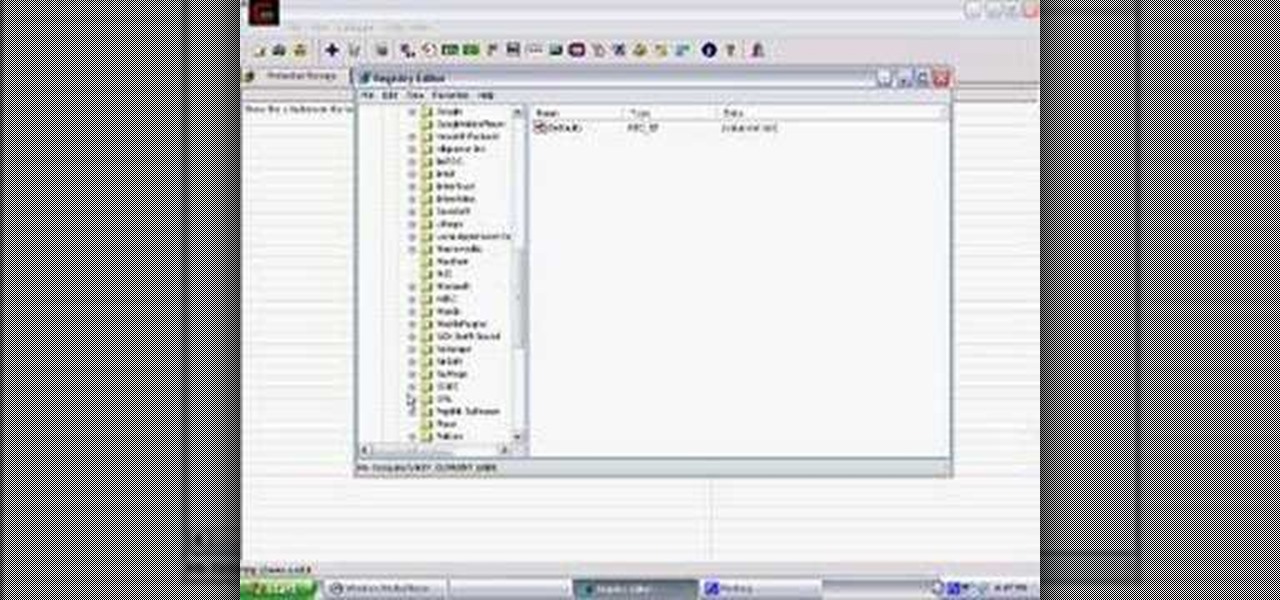
Hack a network computer by decoding Virtual Network Computing (VNC) hex passwords with Cain.
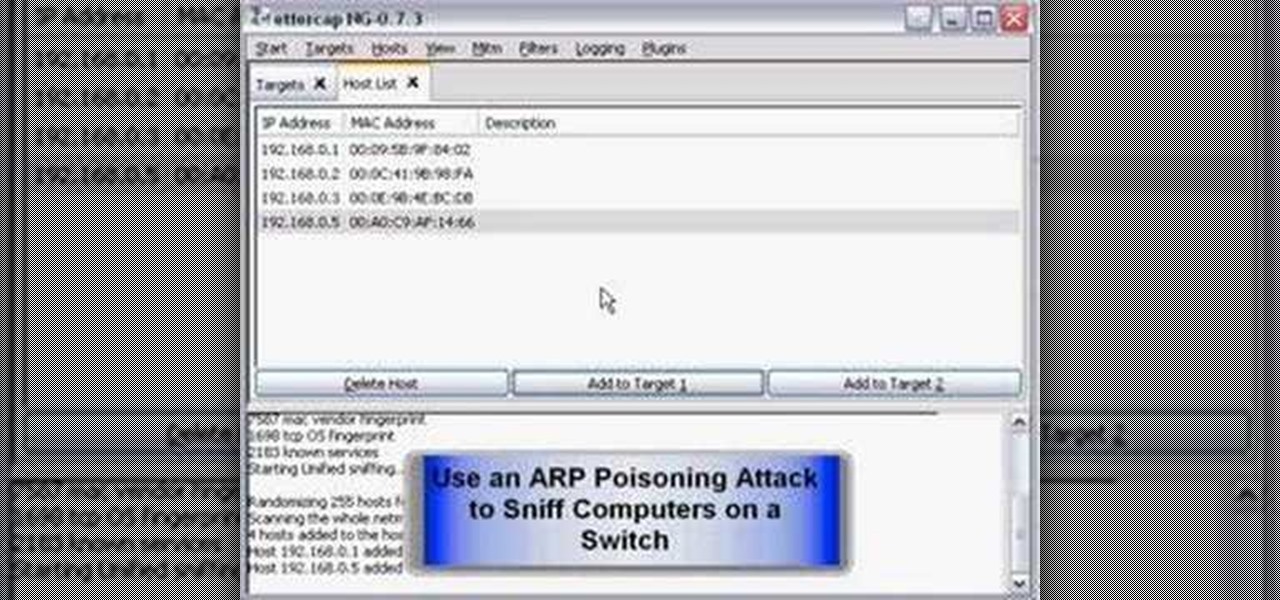
How to hack a network by sniffing passwords with Ettercap software.

This hack will let you play as Giant Donkey Kong!!!

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.
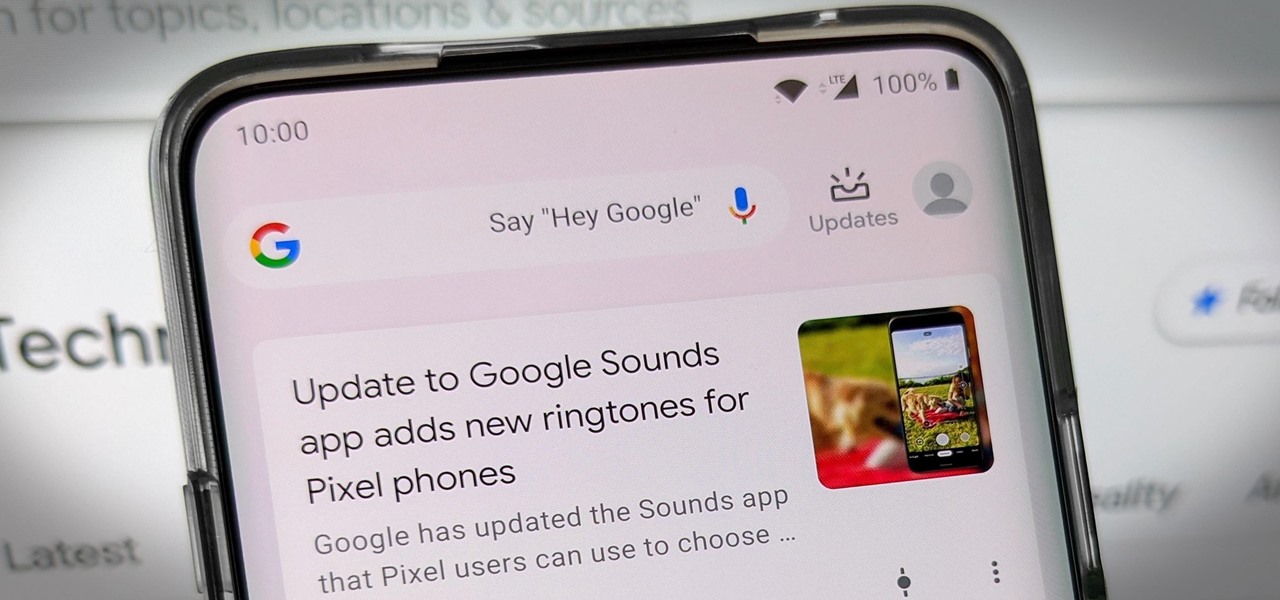
Pixels and other near-stock Android phones have the Google Feed baked into their home screen, but sadly, the default OnePlus Launcher doesn't. Even more disappointing is the fact that the OnePlus Launcher actually has the Google Feed code built into it, but it's not activated. Let's change that.
Low Power Mode (LPM) decreases the amount of battery your iPhone uses by disabling background app refreshing and automatic downloads, locking your screen after 30 seconds, and more. While it's only meant to be used temporarily, if you're struggling with battery life, you may want to enable LPM permanently.
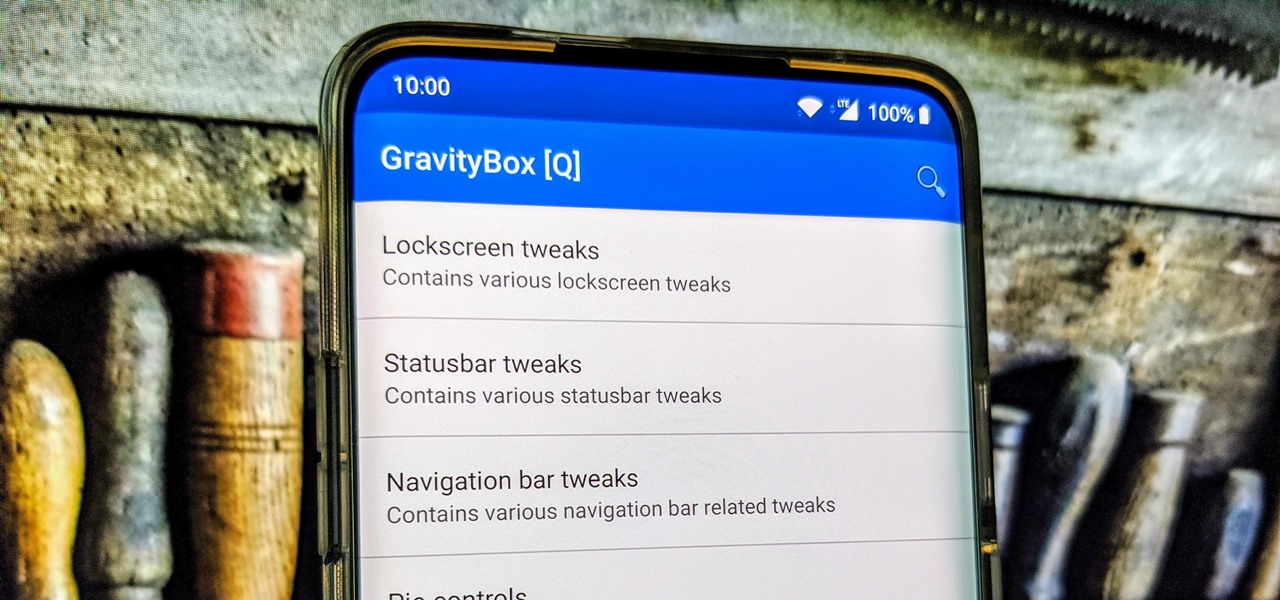
GravityBox is a name that many know as the module to rule them all when it comes to customizing your Android device. Ask any of the longtime modding pros, and they'll tell you about the good old days during the Xposed era. The community was booming and full of great ideas, and there were never any shortages of fun modules to try. Thankfully, it still lives on even years later.

If reaching up to access Camera controls like the flash, HDR, and timer wasn't bad enough, it's gotten a lot more tedious on recent iPhones like the X, XS, and 11 series thanks to their tall displays. If you have a jailbroken iPhone, however, you can easily fix this issue using a free tweak.
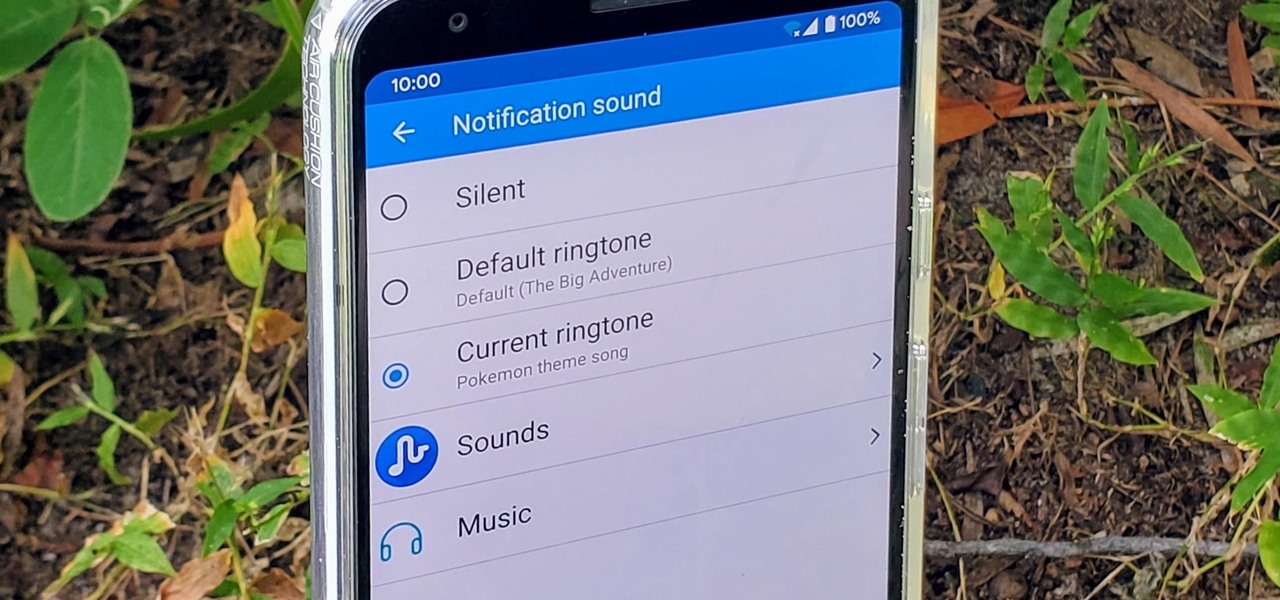
Have you ever walked around in public and heard the same handful of default ringtones over and over again? How do these people know who's calling without looking first? It's tough to tell when they all sound the same, but there is something crafty you can do to help with that. Using a different ringtone for certain contacts will allow you to differentiate between them instantly.