
How To: Make your own greeting cards
Cardmaking is the perfect introduction to paper craft, it's quick, easy and great fun to create stunning results that will amaze your family and friends even with your first attempts!!


Cardmaking is the perfect introduction to paper craft, it's quick, easy and great fun to create stunning results that will amaze your family and friends even with your first attempts!!
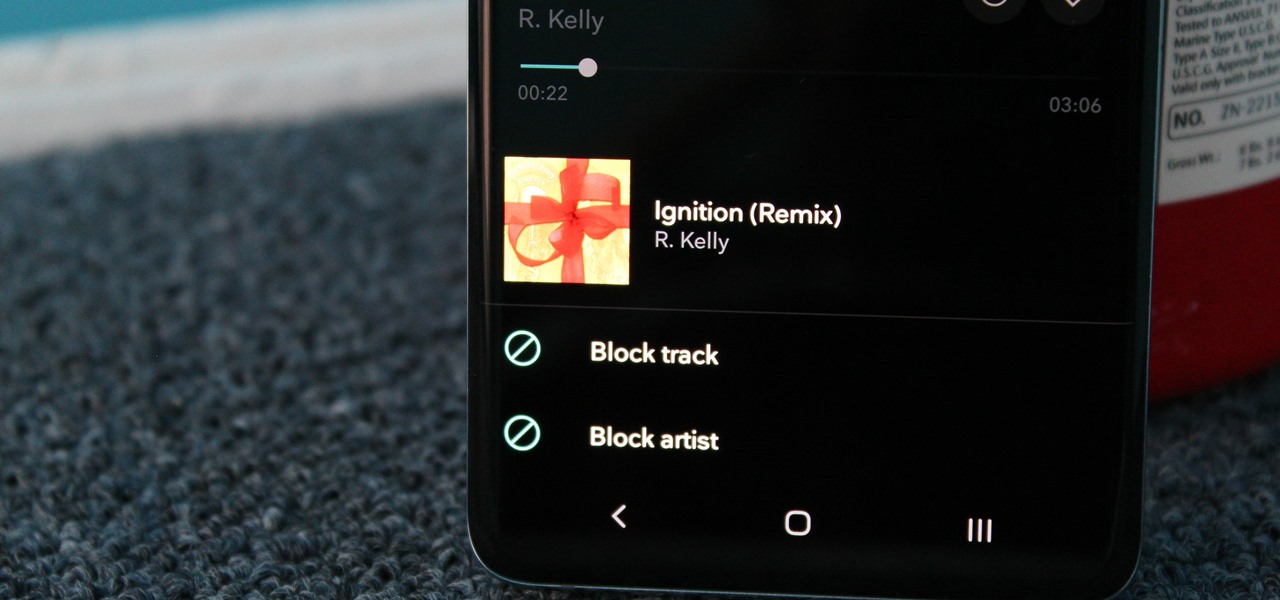
From XXXTentacion to R. Kelly, many artists have been accused of inappropriate actions, so some of us just don't want to hear their music anymore. However, each time streaming services attempt to ban such artists, they face heavy backlash. Recognizing this, Tidal decided to offer a different solution.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Face ID is possibly the iPhone X's make-it-or-break-it feature. Apple is asking previous iPhone owners to put a lot of faith into their home button replacement, and so far, the results seem pretty good. That is until CNN tested the security feature with identical twins.

A new dating advice site, WittyThumbs, launched today that lets users offer advice to others as well as seek it; the site combines that collaboration with advice from designated dating experts.

What companies do you think have a unique and compelling take on social media? Wendy's is certainly confident, to say the least. But Lufthansa Airlines is taking a different approach than most — and it seems to be working — as they give passengers a look behind the scenes through Snapchat Stories.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

Out of all of the "odd couple" food pairings you could imagine, this has got to be one of the outright weirdest.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

The Apple Watch may be a much simpler device than your iPhone, but that doesn't mean it's free of bugs, glitches, and crashes just like your other devices. A common problem that you'll run into is a frozen screen due to a malfunctioning app. While this can be frustrating, the solution can be as simple as a quick reboot.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

The volume is maxed out, but that doesn't stop me from hitting the volume key on my Nexus 7 in hopes that it will magically get louder. This happens to me everyday as I watch videos or play music. The simple fact is that a Nexus 7 tablet just doesn't get very loud. At least, not loud enough for me.

This is a how to video on how to remove a light that broke from a lamp. This is also easier than destroying a potato. Just be sure to please unplug the lamp before attempting this. Failure to do so can result in serious injury or death. Never allow children to perform this operation.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

The main objective is to defend your Obsidian temple while attempting to destroy the opponents. To do so a pickaxe will spawn 3m after you begin and every 3 minutes after that in the temple in the centre jungle.

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.
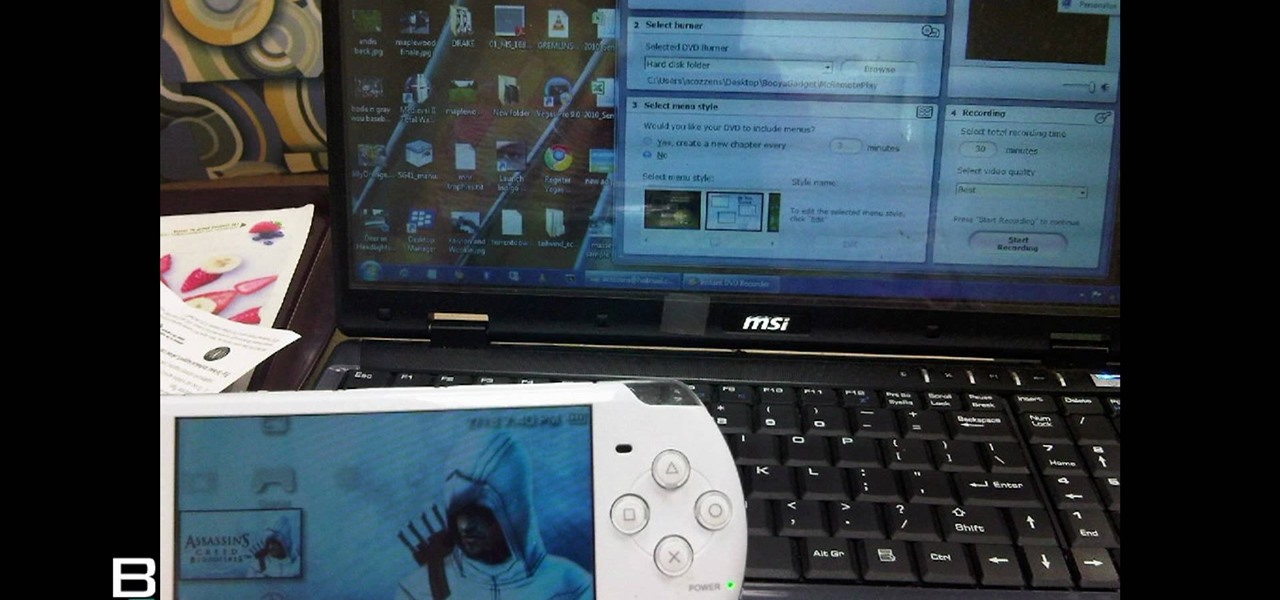
Play remotely with all your friends, stream videos and music from the Internet or even check your Facebook and email - all with your PSP. The PSP has Internet capability, but not every network will be available to you at all times. Here is how you can hack any wifi connection with your PSP.

Have you ever been in a situation when you needed to remember something real important, but you didn't have you didn't have your trusty cell phone or other electronic savior with you?
Tinkernut presents the Bluetooth headset hack! This video shows one of the vulnerabilities of some bluetooth headsets. To prevent this vulnerability, it's best to invest a little more money into a more secure headset and making sure your headset is turned off when not in use. You can find all of the links and scripts used in this video, as well as find answers to questions you may have at the link below:
So 2000 was a wash for an election year; we put up with W for four years, then what happened? 2004! Lost again!!! Diebold you just can't seem to fade.

This is a hack to create a Roomba covered in LEDs that will munch your dust. See how to do this cool mod for the Roomba, the robotic vacuum cleaner made by iRobot.

Few Bluetooth users realize that Bluetooth headsets can be hacked or otherwise exploited to a remote attacker the ability to record and inject audio through the headset while the device is not in an active call. SANS Institute author and senior instructor Joshua Wright demonstrates, and explains, the security vulnerability in this how-to. For more information, including step-by-step instructions on how you can replicate this hack yourself, take a look.

Kip Kay of Make Magazine will teach you how to turn welding goggles into infrared goggles with the hack he outlines in this how-to video. The entire project only costs $10. To replicate this hack at home and build your own pair of steampunk infrared goggles, follow along with the steps in this video tutorial. Just don't look at the sun!

This confectionery hacking how-to video demonstrates that, with an electric motor, juice lids, battery and sugar, you can make your own cotton candy machine. Don't wait for a carnival or fair to get your next taste of sweet, sweet cotton candy. Watch this video tutorial to see this hack in action and to learn how to build your own bottle-cap candy floss machine.

The 'One Small Hack for Man' achievement in Call of Duty: Black Ops is available if you own the Rezurrection DLC and requires you to hack anything within the game with the hacking device. Take a look at this guide from the Achievement Hunters to learn just how to unlock the achievement for your Xbox 360 gamer profile.
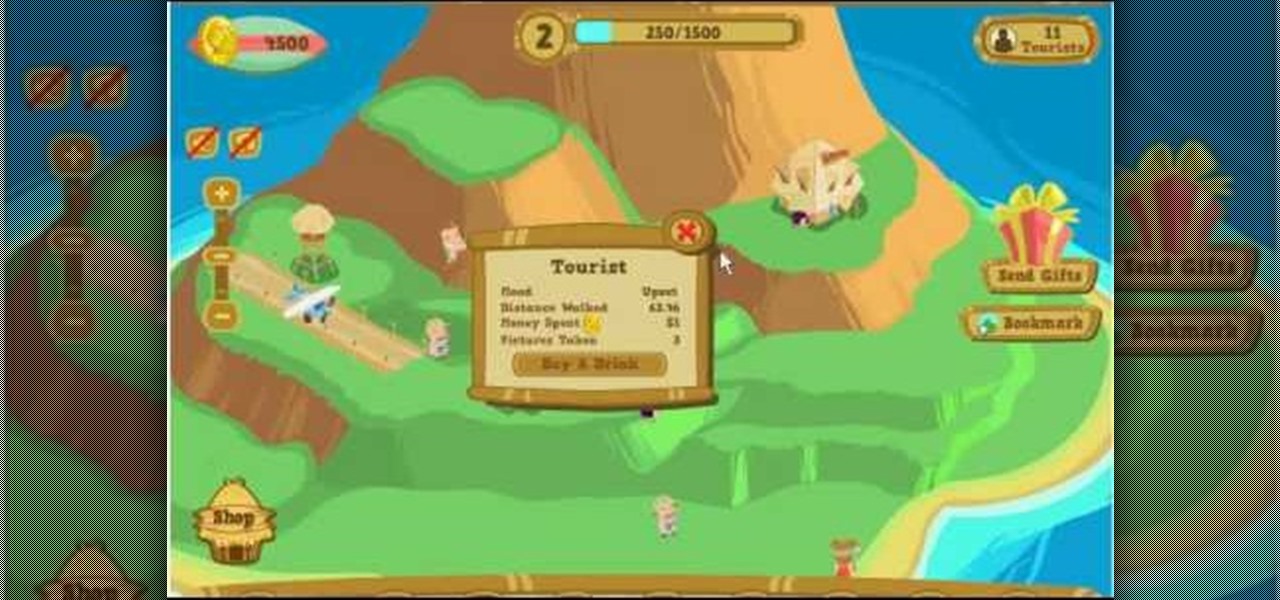
This is one of the best hacks for Happy Island, so make sure to try it out before it's patched! With Cheat Engine, it's easy to do this coin and experience hack.
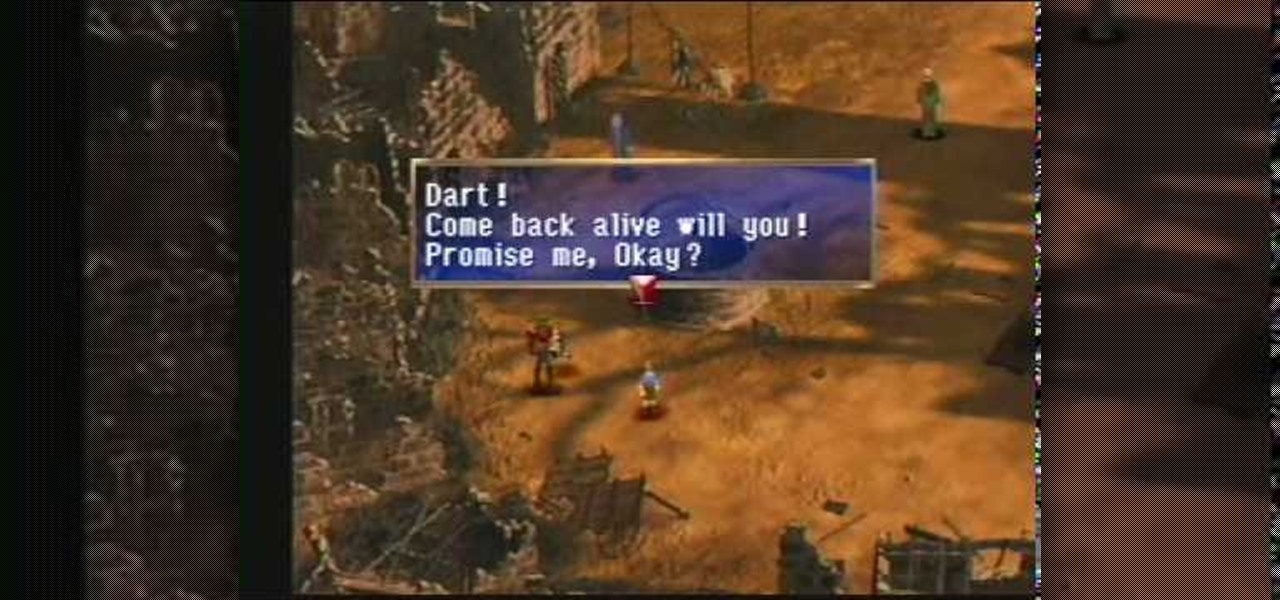
In Hellena Prison, save the King from his execution… save the day in this level of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are racing to the top of Hellena Prison to save King Albert from execution, they fight and defeat Fruegel, Lloyd steals the Moon Gem from Albert, Lavitz turns Dragoon in an attempt to help King Albert and gets slain, King Albert joins the party, they all go talk in Seles to where they travel to and explore the Bl...

Holidays such as Thanksgiving are doomsday for most garbage disposals due to clogs. If you're garbage disposal is clogged, check out this video to see some helpful tips on how to fix it.
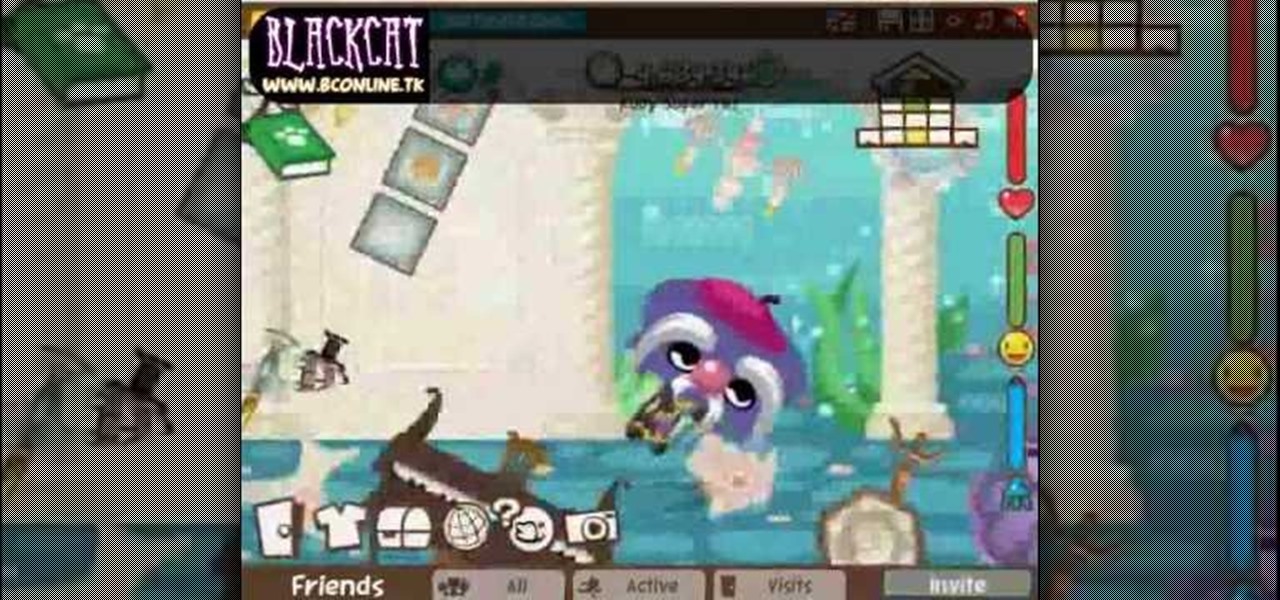
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack Pet Society: funky game cheat (09/27/09). Turn the game into funky mode!
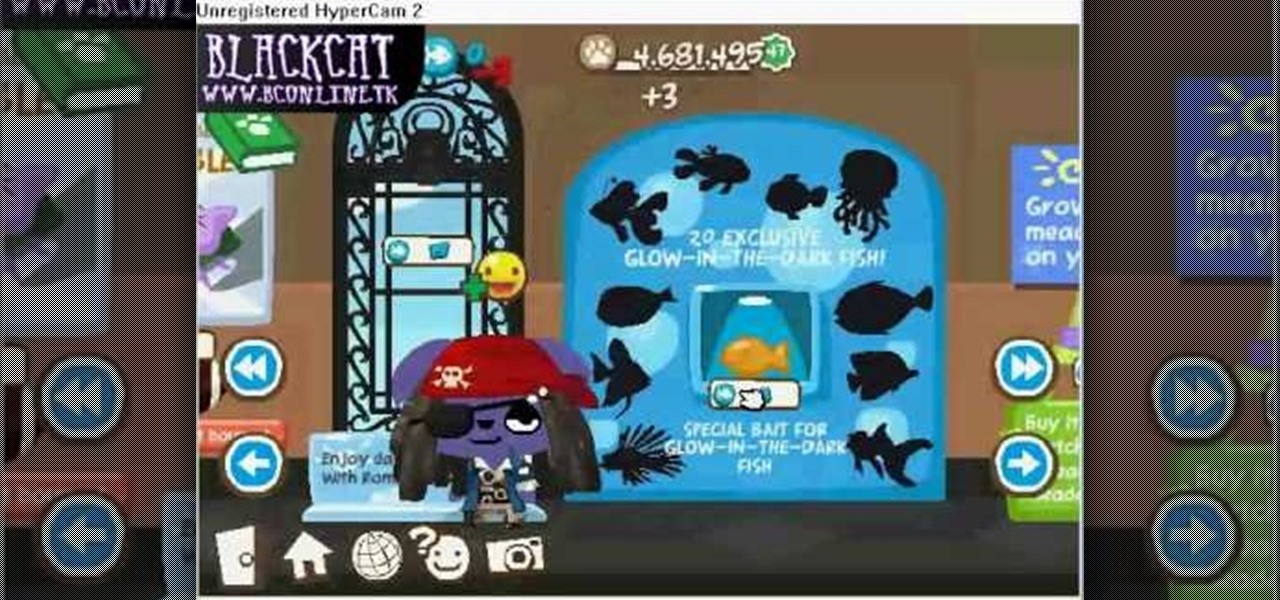
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack coins on Pet Society (09/23/09).

Self-injuring with knives or razor blades is a dangerous attempt at coping with problems like anger and anxiety. Learn how to get help and deal with your feelings more constructively.
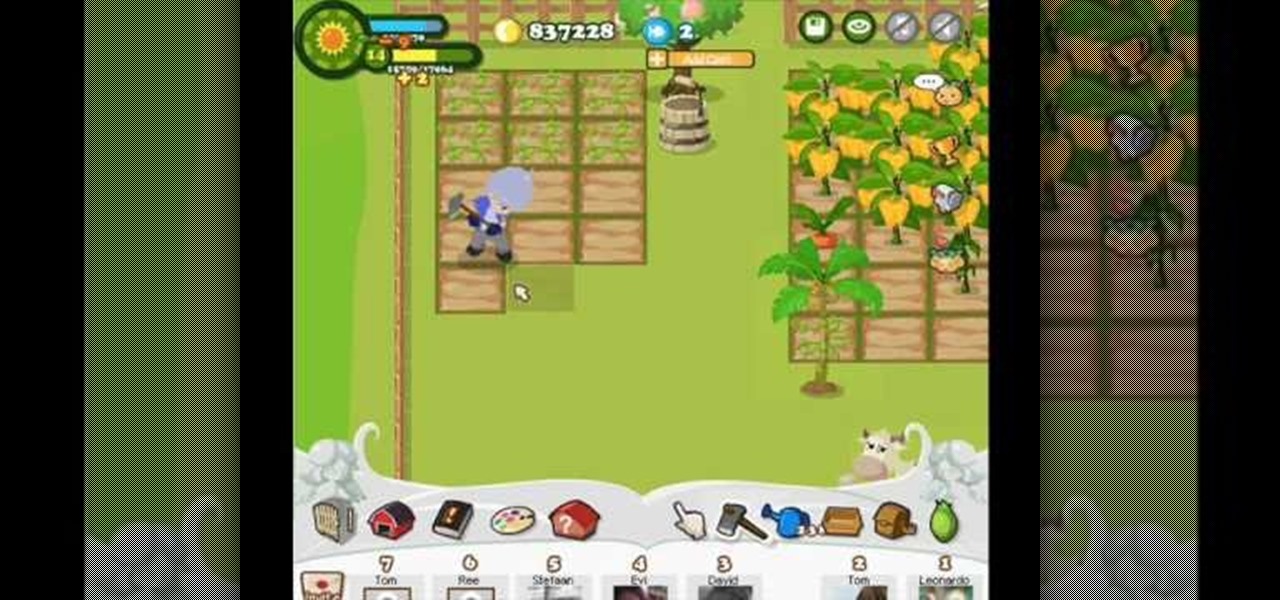
Country Story hacks, cheats, glitches. How to hack Country Story. Watch this video tutorial to learn how to plot hack Country Story on Facebook (08/22/09).

The Twilight Hack is currently the only safe, public way to enable homebrew on an unmodded Nintendo Wii. The Twilight Hack is achieved by playing a hacked game save for The Legend of Zelda: Twilight Princess which executes a homebrew application from an external SD card

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Citizen Engineer is an online video series about open source hardware, electronics, art and hacking by Limor (`Ladyada') Fried of Adafruit Industries & Phillip (`pt') Torrone of MAKE magazine.

How to hack and mod a Microsoft Zune Mp3 player and upgrade the hard drive to anywhere up to 100GB Part 1 of 2 - How to Hack a Microsoft Zune for a larger hard drive.
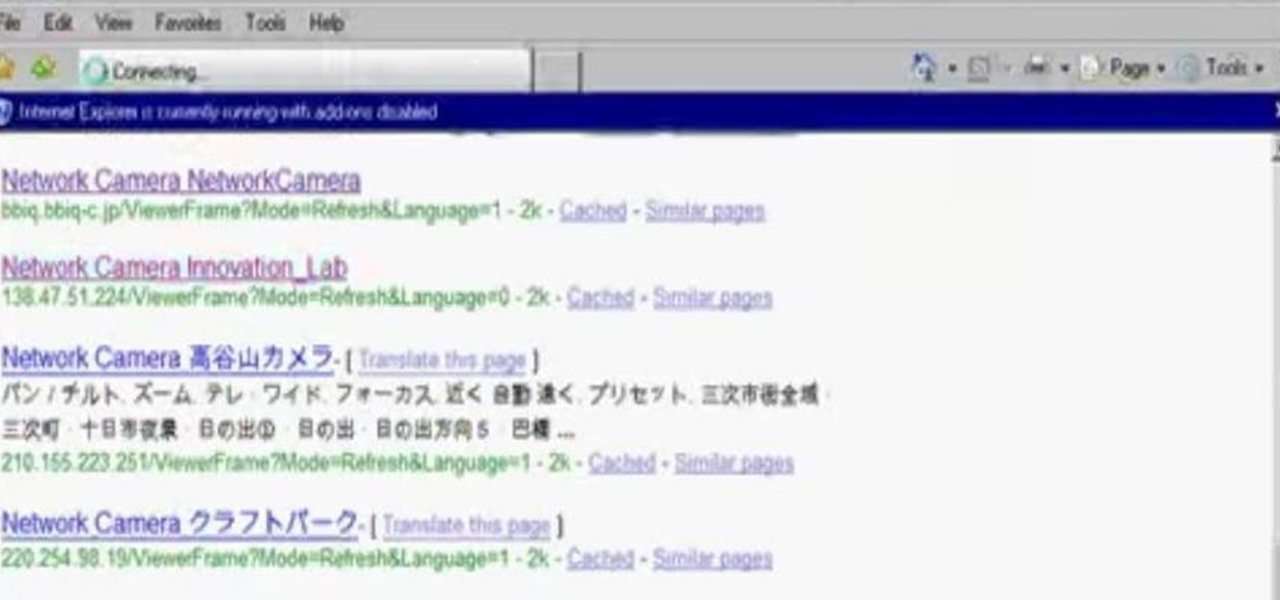
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!