
Home Hack: Silence a Leaky Faucet With a String
Yep, it's that easy. From Re-Nest: "To quiet the sound of a leaky faucet, simply tie a string around the neck of the faucet and allow it to catch the drips on the way down.


Yep, it's that easy. From Re-Nest: "To quiet the sound of a leaky faucet, simply tie a string around the neck of the faucet and allow it to catch the drips on the way down.

It won't be much trouble getting a decent police sketch if Andrew Salomone decides to knock off a liquor store.

Do you want to hack your PS3? Are you tired of different videos sending you all over the place to find all of the necessary steps? Look no further. This three-part video offers detailed, step-by-step instructions for hacking your PSP, including making a Pandora's battery, a magic memory stick, and actually loading the custom stuff onto the PSP. Extend the life of your PSP in spite of its lack of software support!

Via WonderHowTo World, Cinematography: Lozzless demonstrates how to make a diy cheap macro lens with working aperture for his Canon 5D Mark II, coined the "SuperMacro".

Sean Stiegemeier has captured absolutely beautiful timelapse footage documenting the eruption of the Eyjafjallajökull volcano in Iceland:
This clip shows you how to buy items in FarmVille without spending your precious coins. In another word, no coins will be subtracted from your balance. It's a pretty cool hack, you will have unlimited coins.

This hacking how-to video focuses on the art of lock picking in less than half a minute. It will teach you the mechanics of cylindrical lock so that you will be able to take advantage of the lock's poor design without any lockpick skills. Follow along with this hack tutorial to learn how to open any cylindrical bike lock in thirty seconds or less. Open any cylindrical bike lock in 30 seconds or less.

The Galaxy S9's new wallpapers look fantastic, but you don't need to buy one to know that. Whether you have an iPhone X or a Pixel 2, Samsung's updated wallpaper library is yours for the taking, thanks to an S9 system dump released today.

The rumors were confirmed today at WWDC, Amazon Prime is coming to the TV app on the iPhone. This app will allow users to stream their favorite Amazon Prime shows including Bosch, Mozart in the Jungle, Catastrophe, Transparent, and more.
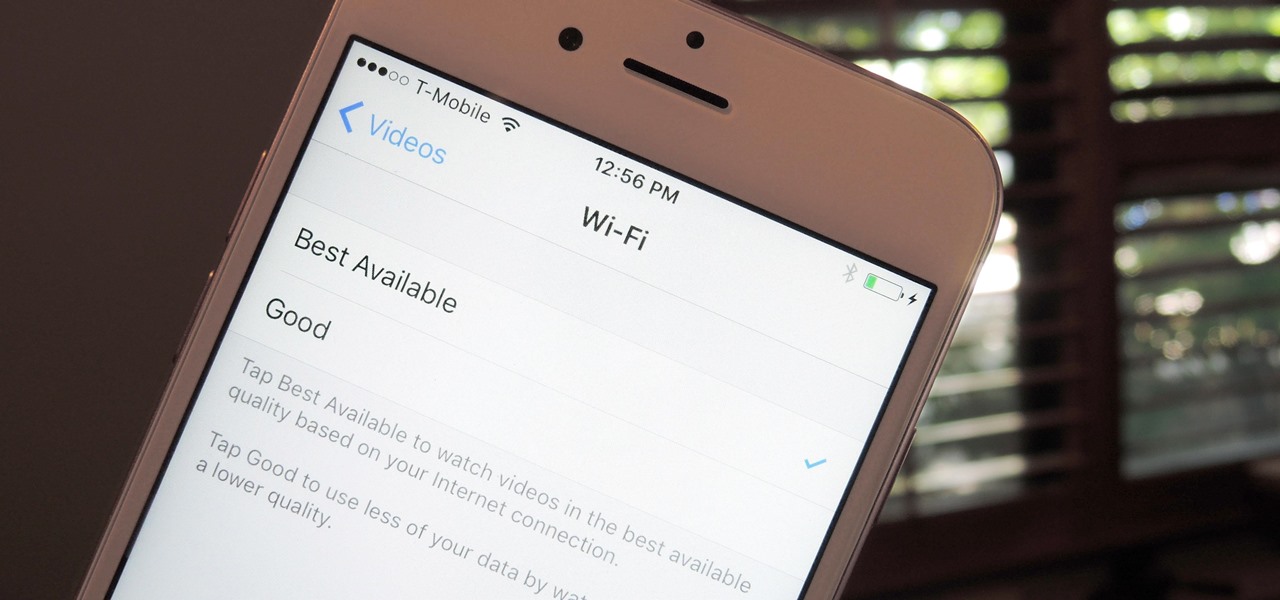
If you're watching videos over Wi-Fi on your iPad, iPhone, or iPod touch, iOS 10 lets you adjust the quality for when you want to save data or need help watching a movie or TV show on a poor connection.

The Nextbit Robin, the world's first cloud-oriented smartphone, is on sale at Amazon for $299 plus tax, a savings of $100. You'll have to act quick though, as the deal only runs through May 10th while supplies last. Nextbit Robin, an unlocked SIM phone, was just updated last week, and now runs Android Marshmallow 6.0.1. It also has a unique storage system, with 100 GB of cloud space, as well as 32 GB of built-in storage. You can snag it in midnight or mint colors. Amazon Prime members will al...

HTC is developing the latest Nexus phones for Google, according to a recent tweet from Evan Blass, a well-known phone leaker. Blass reported that the new Nexus phones will run Android N, and are being referred to as the M1 and S1. Android Police backed up Blass's tweet and added that a source told them the new handsets will be named "Marlin" and "Sailfish."
Hi everyone! This is my first How To. Before we start you need to have a Facebook account (of course) and...this only works with your Facebook friends (so if you're looking for someone's mail on Facebook but you're not friends this won't work)

Apple just released the latest developer preview of OS X 10.11 El Capitan, currently in its sixth beta. While this latest build mostly deals with tiny improvements and bug fixes, it also includes a brand new breathtaking wallpaper of the El Capitan rock formation in Yosemite National Park.

Functioning as an extension of your iPhone, the Apple Watch makes monitoring and receiving notifications convenient with just a glance, leaving your iPhone in your purse or pocket. But just like on your iPhone, these notifications can begin to stack up, so let's show you the one-touch method for clearing them all at once.
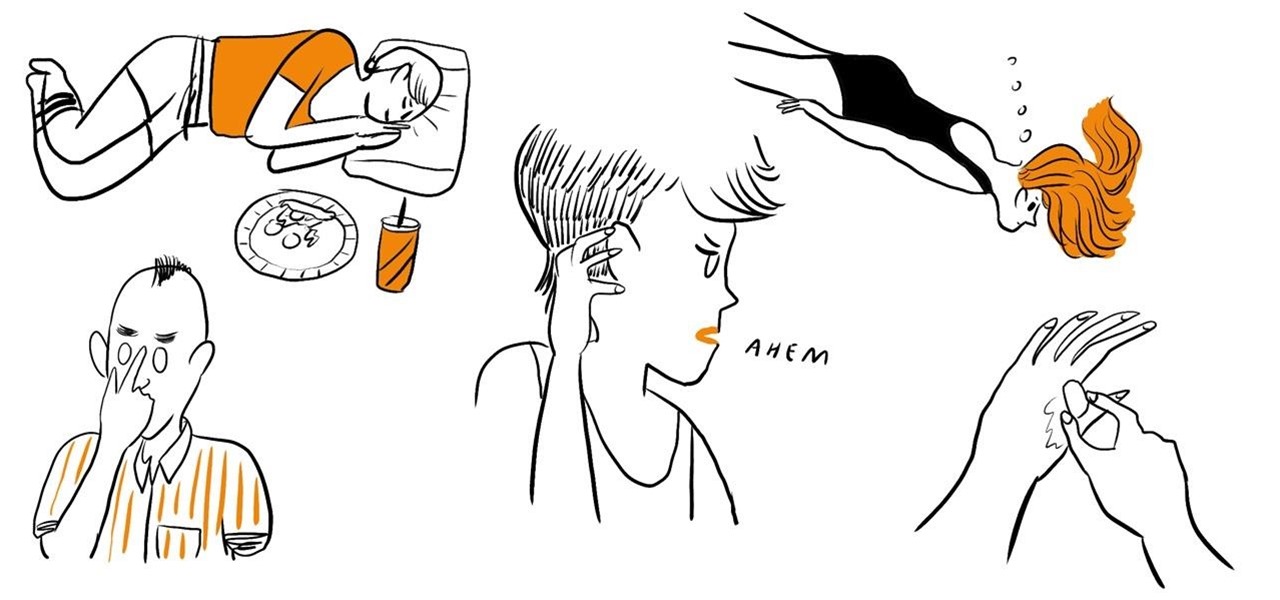
If you need to relieve an itch in your throat, you can try getting rid of it by scratching your ear. Or if you accidentally give yourself brain freeze while eating ice cream, you can press your tongue against the roof of your mouth and cover as much as surface area as possible to make the pain go away.

Hello again my fellow hackers. I've come to give you some hope for hacking. As we know there are a lot of exploits out in the world and there are websites you can find them on.
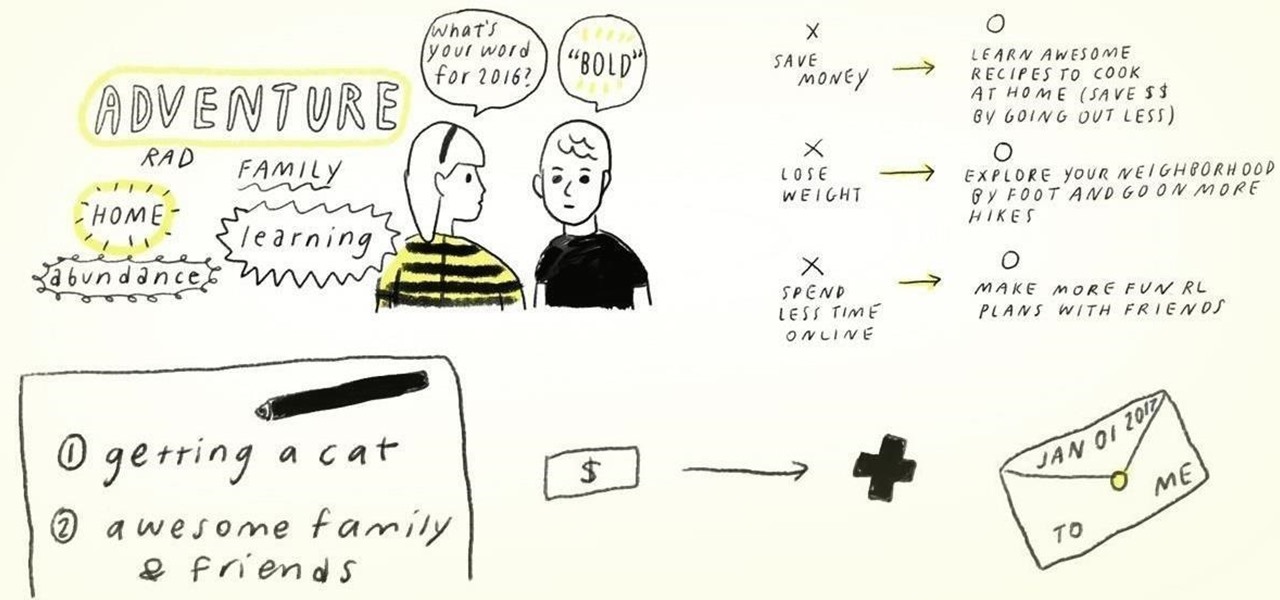
Statistics show that only 8% of New Year's resolutions on January 1st actually get fulfilled. While you can certainly take advantage of some mind hacks to increase the probability of succeeding at your January resolutions for the rest of the year, setting killjoy goals and signing up for a gym membership are not the only ways to ring in the new year.
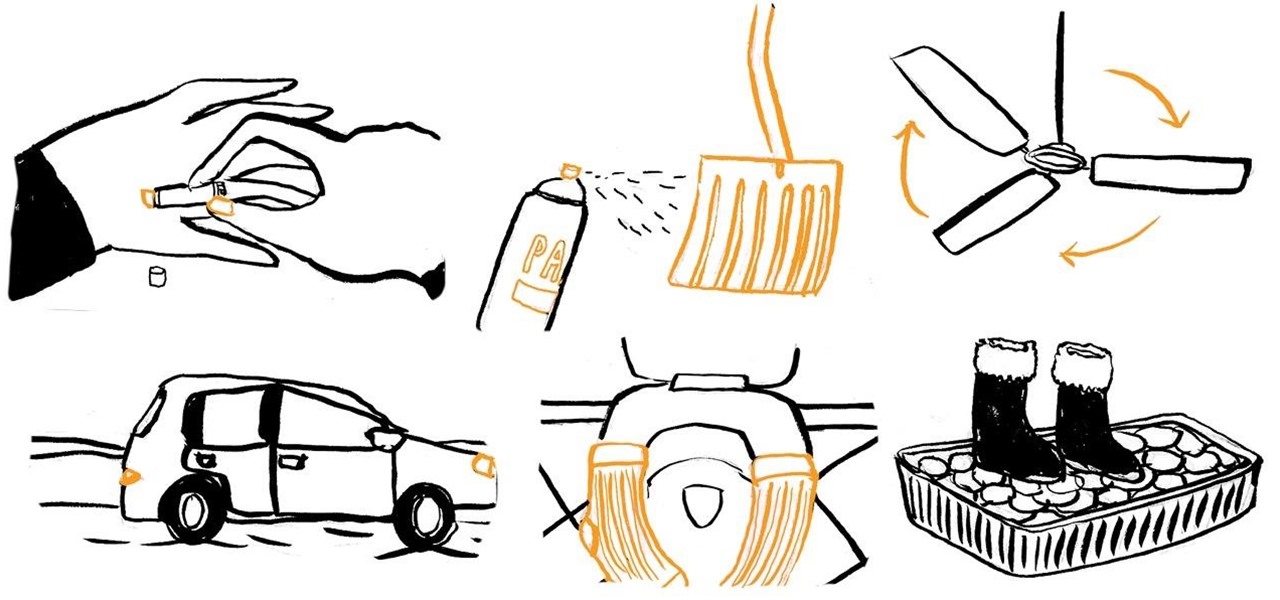
Turn on the ceiling fan indoors during the cold winter season. Though it may seem counterintuitive, spinning the blades clockwise on a low setting actually recirculates warmer air trapped near the ceiling towards the floor.
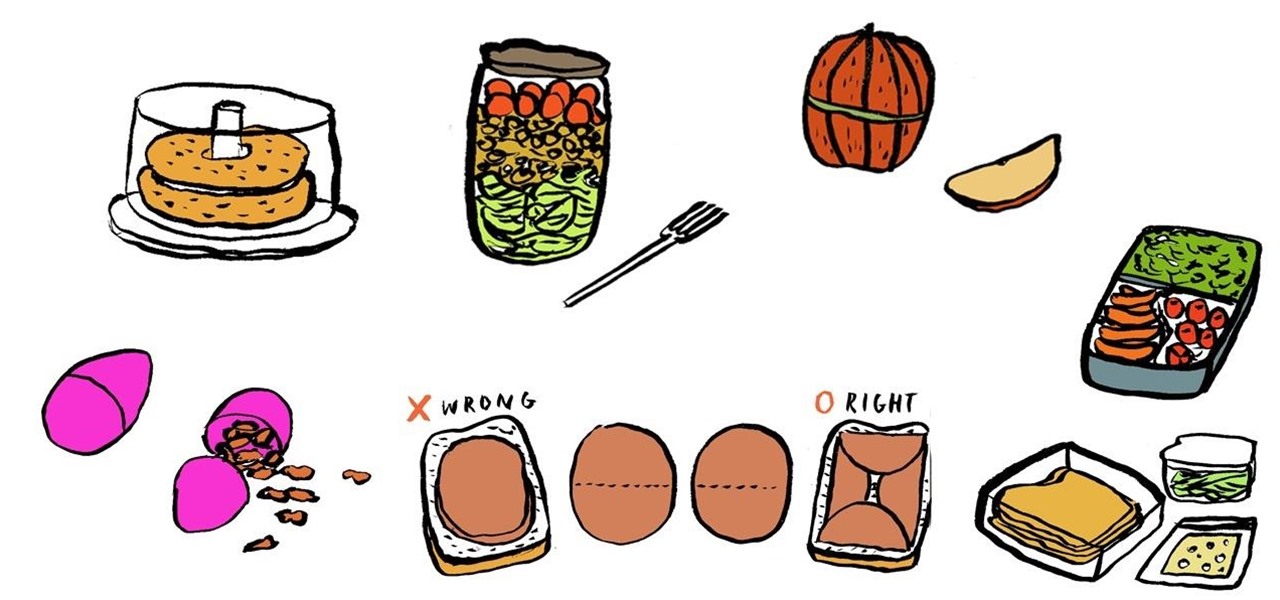
Bringing your lunch to work doesn't always have to involve boring brown paper bags and plastic ziplocks.

You've all probably heard about Apple's attempts to thwart iPhone 4 users from opening up their own devices, thanks to their sly maneuvers in switching out everyone's screws with those funky pentalobular screws. But one thing Apple will never learn— they will never have complete control. Where there's a will, there's a way. And if someone wants to fix their own iPhone or modify it slightly, they're going to do it, regardless of what screws bind it together.

Ikea Hacker features a nice Ikea mod: Romain turns the Ivar side unit into a camera dolly. "A few days ago, I found out that the Ivar 'wooden ladder' was perfect to use it as rails for my cinema dolly! I can now make some nice sequence shots with this 18€ accessory from Ikea."

Candy machine hacks are so popular now, one might think it's easier to get candy from a vending machine than from a ... baby.

Store bought Nerf guns don't always achieve the velocity necessary for an effective assault. Zach Scott's solution: mod the toy. Known for his fantastic cat videos, Zach claims this hack increases trajectory by at least 25%! Every bit counts when you're in an all out foam war.

This gives a variety of cheat codes for Grand Theft Auto IV. Follow this and learn how to hack GTA 4 for the PS3. Cheat at GTA IV.

Learn a harmless hack to access and control other peoples' webcams with a simple Google search. Access and control web cameras with Google.

As the image above suggests, it takes expertise (and perhaps sleuth) to actually hack into somebody's facebook account. But to steal a friend's password? If you're lucky, a simple mind game will do the trick. Read and learn:

This hour-long hacking tutorial looks at the Nmap security scanner. In particular, this Nmap tutorial looks at port scanning concepts, TCP three way handshake, stealth scans, idle scans, bounce scans, version detection, OS detection, NSE/LUA scripting and firewall logs. To get started using Nmap, watch this video tutorial. Use the Nmap security tool.

Learn a hack to access the command (cmd) prompt in Windows if it has been blocked. Get onto the Windows CMD if it is blocked.

Since the release of Microsoft's Kinect, there's been no shortage of useful and fun hacks. In the past, we've seen the Kinect modded for things like x-ray vision, World of WarCraft gameplay, air guitar and 3D video. And now there's even a use for all of you MineCraft gamers!
3,000 soldiers to serve in Africa next year A brigade will deploy to Africa next year in a pilot program that assigns brigades on a rotational basis to regions around the globe, the Army announced in May.
Ron Paul Republicans take over Nevada GOP

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.
In a bombshell revelation of the depth of the food police state that now exists in LA County, California, NaturalNews has learned that the LA County health department has unleashed door-to-door raw milk confiscation teams to threaten and intimidate raw dairy customers into surrendering raw milk products they legally purchased and own.
Word out of Idaho is that the Ron Paul bloc in the Gem State’s GOP, perhaps encouraged by recent events at the Nevada and Maine state Republican conventions, plans to attempt a similar strategy.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

You're hellbent on taking over the world, but one race of robotic minions isn't enough for you. With your hexapod robots acting as your ground forces, it's only natural to take to the skies. These cardboard quadcopters are the perfect air force for you. Combined, you are mere steps away from starting your evil takeover. Now you just need some water bots. The cardboard flying quadcopters are built around the MultiWii platform with the twin power of Processing and Arduino, so they are actually ...

In this article, I'll show you how you can make your very own bullet/shell bottle opener. All you need is a .50 caliber deactivated round and some workshop tools!

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

This is the first thing I have ever built for a weekly challenge. I am a big sci-fi fan so I just had to jump in on this one.