In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on a Microsoft SQL Server (or SQL Server Express.) See how easy it is to obtain a shell in a Microsoft SQL database with this how-to.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.
Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

This video is useful if you ever play games on your smartphone and wish to be able to play more than solitaire. Follow this video hack, and you'll be able to get all those Atari classics right on your phone for free.
You can learn how to hack a DVD player and then you will be able to watch a DVD from any region in the world. After changing the region code, you can purchase less expensive DVD's.

Cheat Engine is a pervasive program that will attach to your browser when you play web games, and let you hack into the games and cheat. This tutorial focuses on the free web game Dragon Fable, and shows you how to use Cheat Engine to hack the game.

Gaia Hollywood is a virtual Hollywood created for the game Gaia Online. Hacking it is a snap using the steps provided. Be sure to get WPE Pro before you proceed. Have fun as you hack Gaia Hollywood accounts!

Want more gold? How about more skill points? You may need them in the game Acruz. But how do you get more, more, more? Well, with Cheat Engine, you can get more gold and skill points, with no real hassle.

Want to learn about hacking Plock? You've come to the right video. Using Cheat Engine to hack Plock, you can do just about anything.

See how to hack the flash game Jetman, which you can play on Facebook. This Jetman cheat will give you top score using Cheat Engine.

Enjoy tons of money in Pet Society! But the only way to do so is by cheating… with Cheat Engine. If you've never heard of Cheat Engine, then you're missing out on tons of easy hacks.

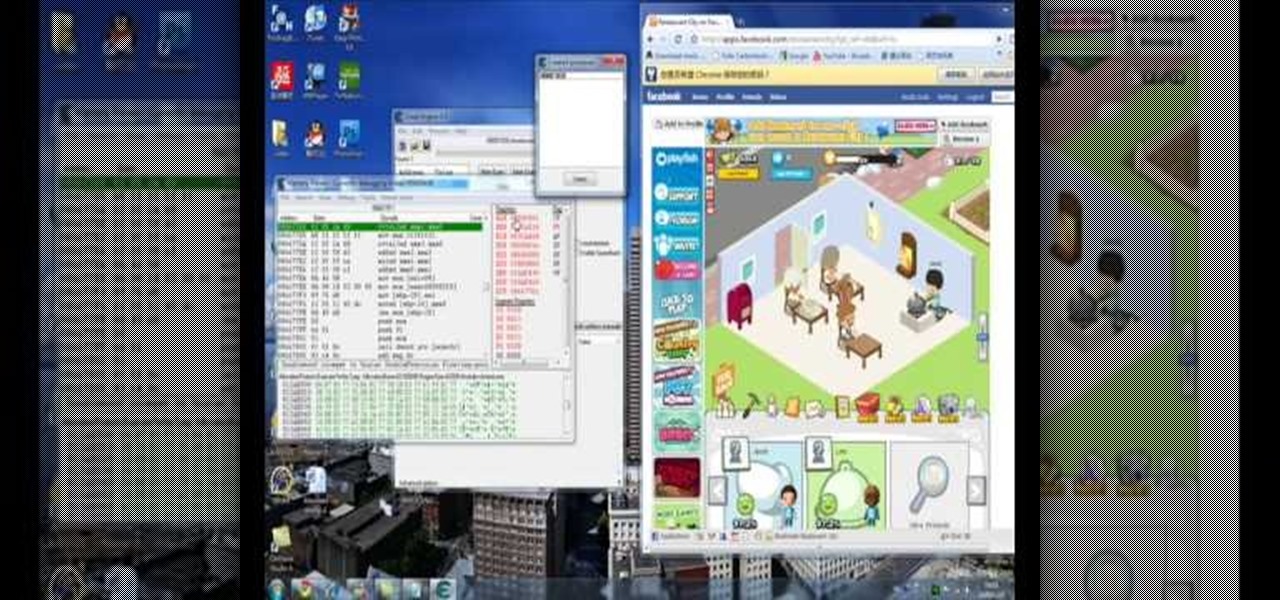
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

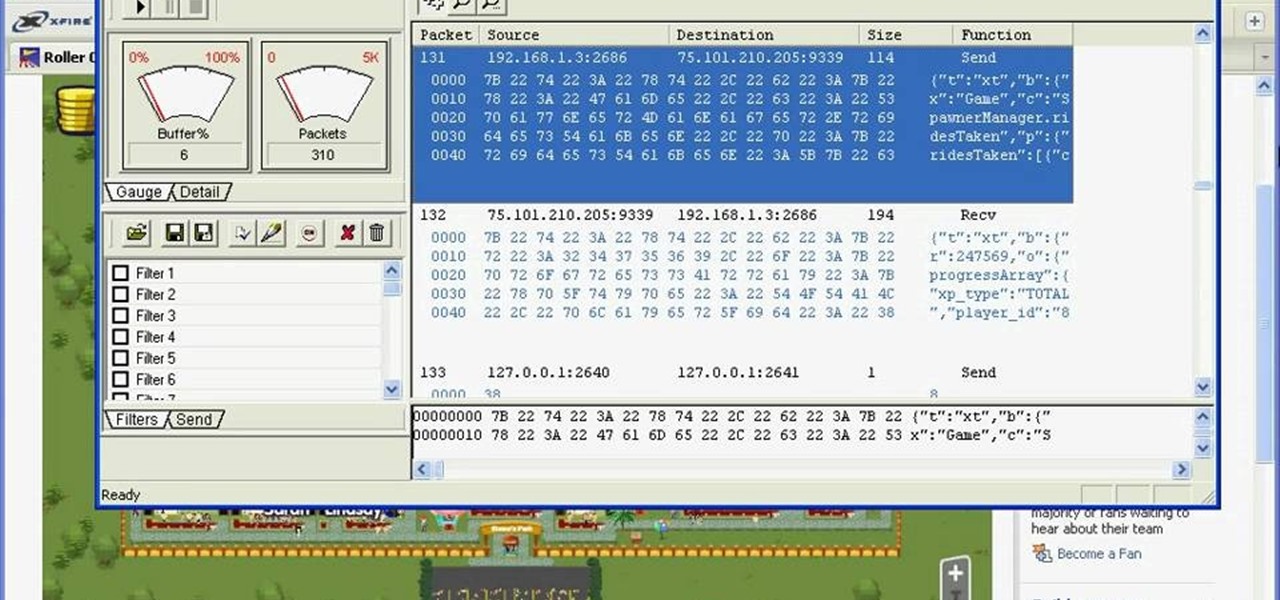
Get more money on RCK than you ever could imagine… get higher levels than you ever though possible… hack your way into success on Roller Coaster Kingdom. You just need WPE Pro. Download WPE Pro now.

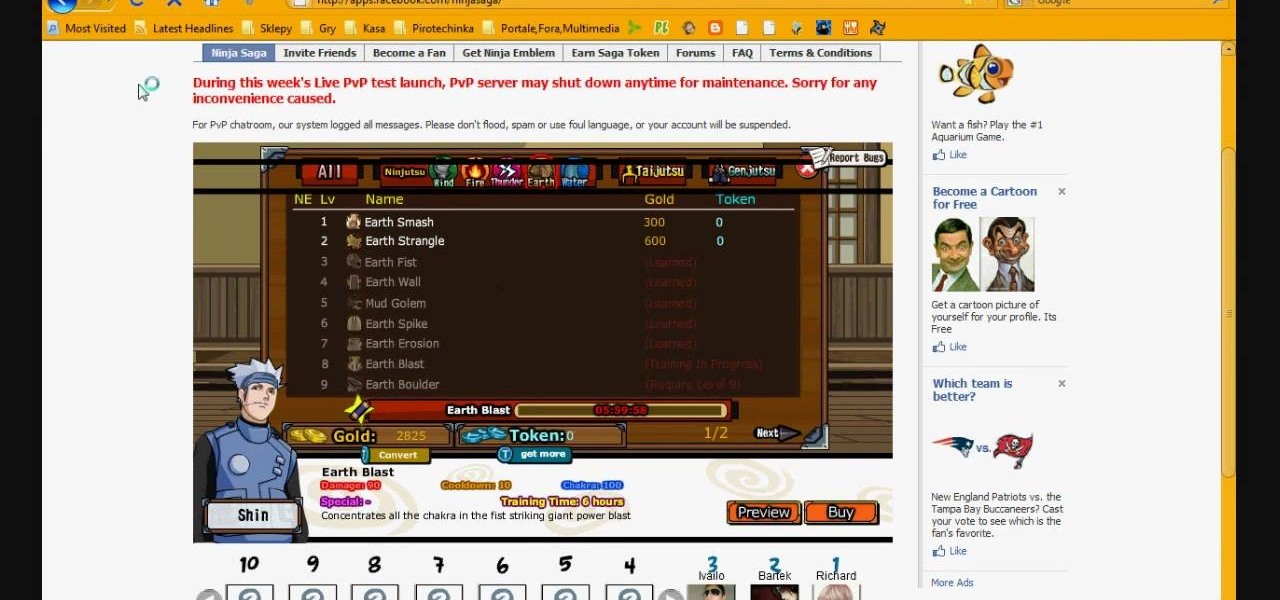
Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack Ninja Saga skills (10/25/09). Download Cheat Engine.

Hacking RC is easy with Piaps Restaurant City Hack! Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to cheat Restaurant City with Piaip's Hack (11/08/09). See how to download, install and run Piap's Restaurant City Hack v.1.13 or 1.12.

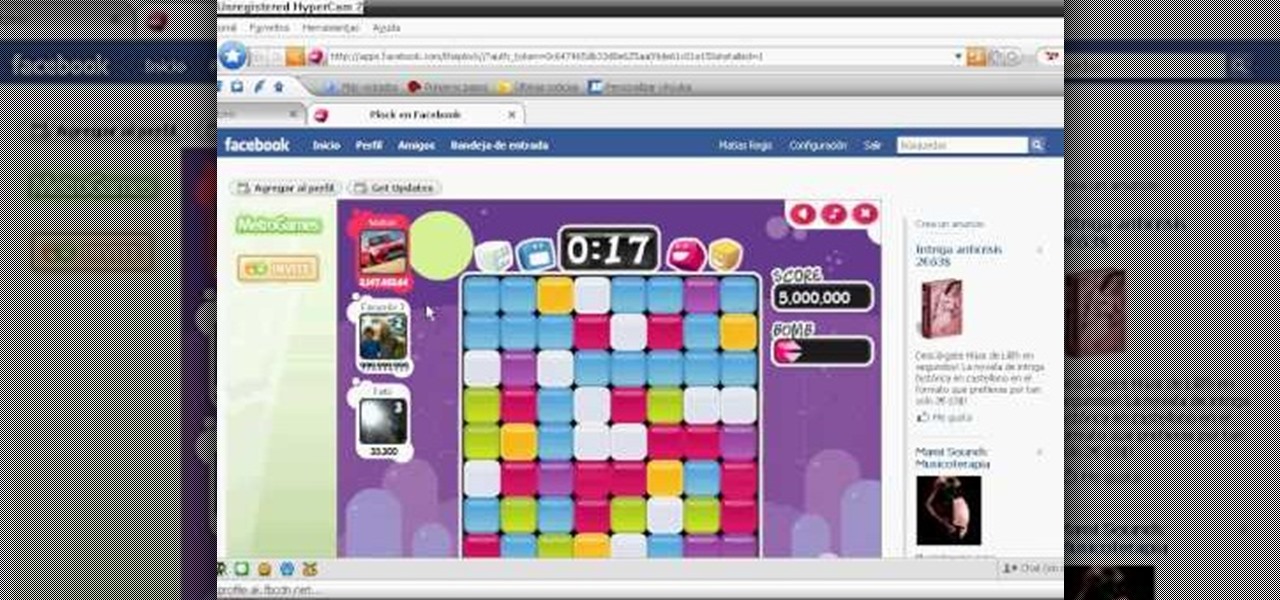
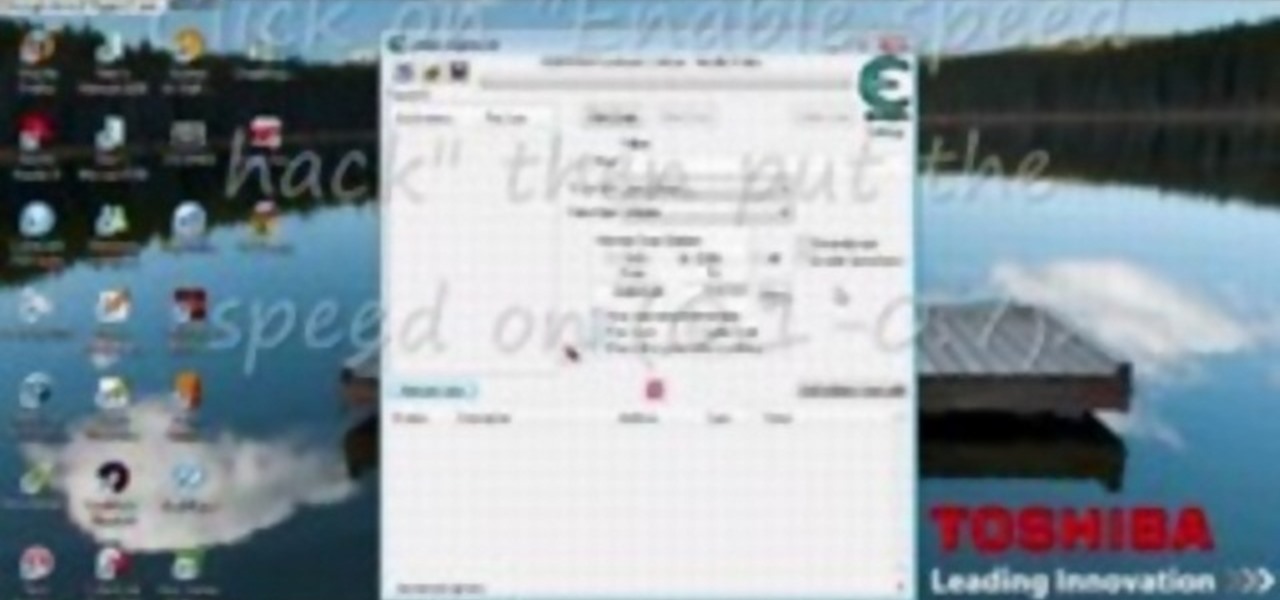
Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to hack speed and time in Bejeweled Blitz (09/20/09). It does speed down the way the jewels move but t helps to get a really high score.

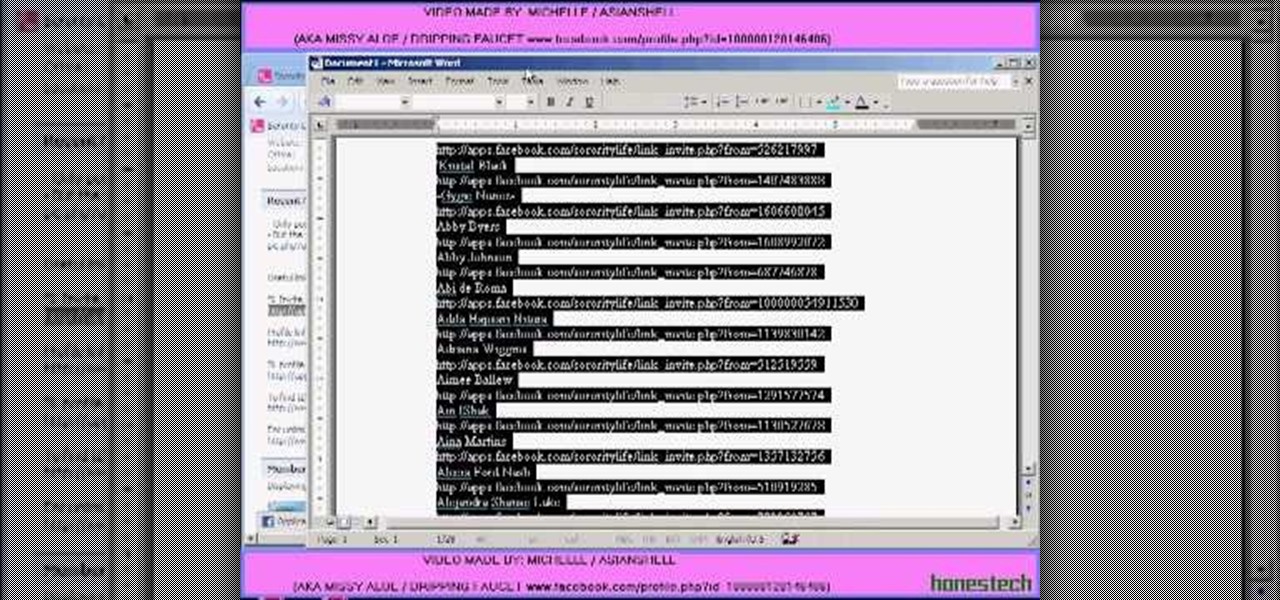
Sorority Life hacks, cheats, glitches. How to hack Sorority Life. Watch this video tutorial to learn how to hack unlimited invites in Sorority Girls (08/16/09).

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack black skin in MyBrute (08/13/09).

Life is too short to go hunting for information all the time. Fortunately, you can have Mozilla Firefox bring information by using extensions and simple search box hacks. In this video tutorial, you'll learn how to use both. For more, and to get started using extensions and search box hacks in Mozilla Firefox yourself, take a look!

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

The Google Phone app is one of the best dialers for Android today, especially with all of the unique and exciting features it brings to the table. Unfortunately, without owning a Pixel phone, you are unable to officially download the app, making a modified version your only option. However, this version of Google Phone is missing a few key features, such as spam protection and business search.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

The holidays are here, which means a slew of new smartphones are set to be gifted to loved ones in the spirit of giving. Of course, a great case to compliment and protect that precious flagship is a must, regardless of whether it's a OnePlus 6T, iPhone XS, or Galaxy Note 9. And while quality cases usually come with a hefty price tag, there are plenty of Black Friday deals to keep you from going broke.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

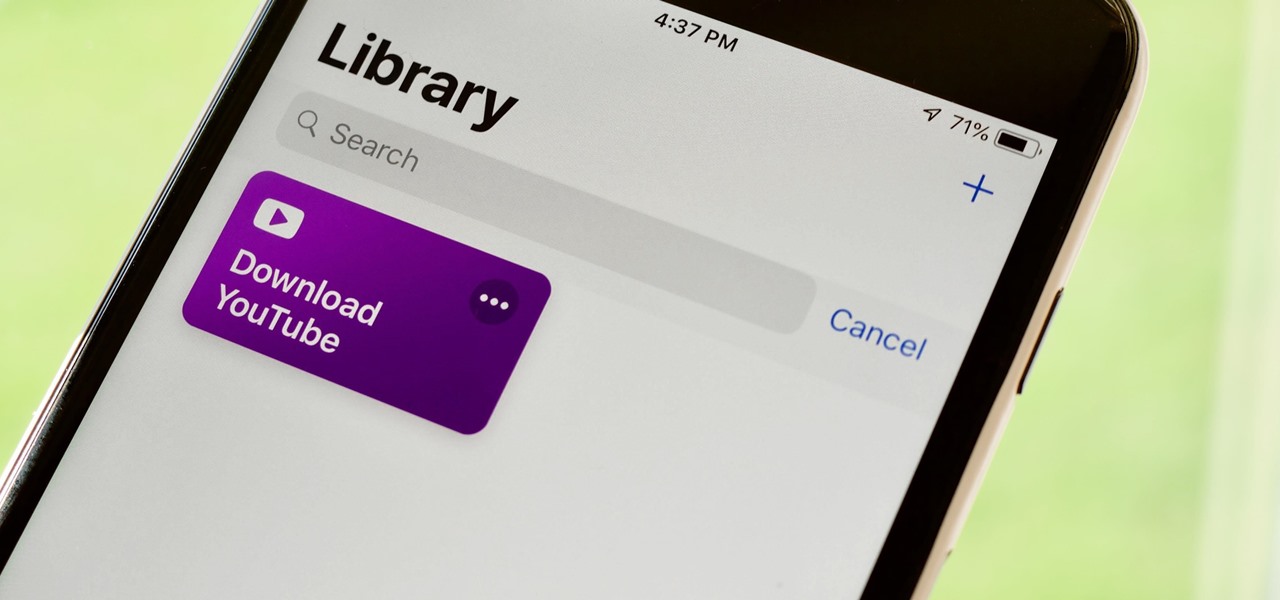
If you've ever wanted to download YouTube videos directly to your iPhone, there's an easy solution — just update to iOS 12 and install Apple's new Shortcuts app. With the Workflow-replacement app, you can add a shortcut that lets you download any YouTube video you want, without needing to jailbreak or use shady third-party tools.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

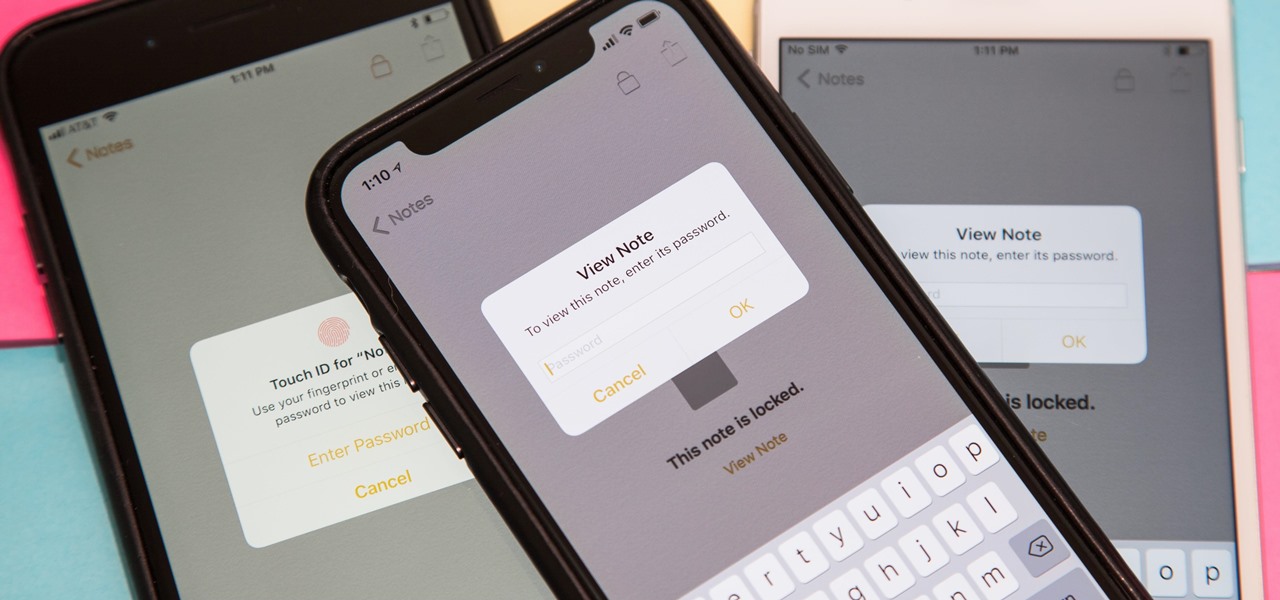
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feeling of sunscreen, there are other ways you can protect your skin by increasing your sun tolerance. Your diet actually has a lot to do with how easily you burn, so by getting enough of a few key nutrients, you can decrease ...

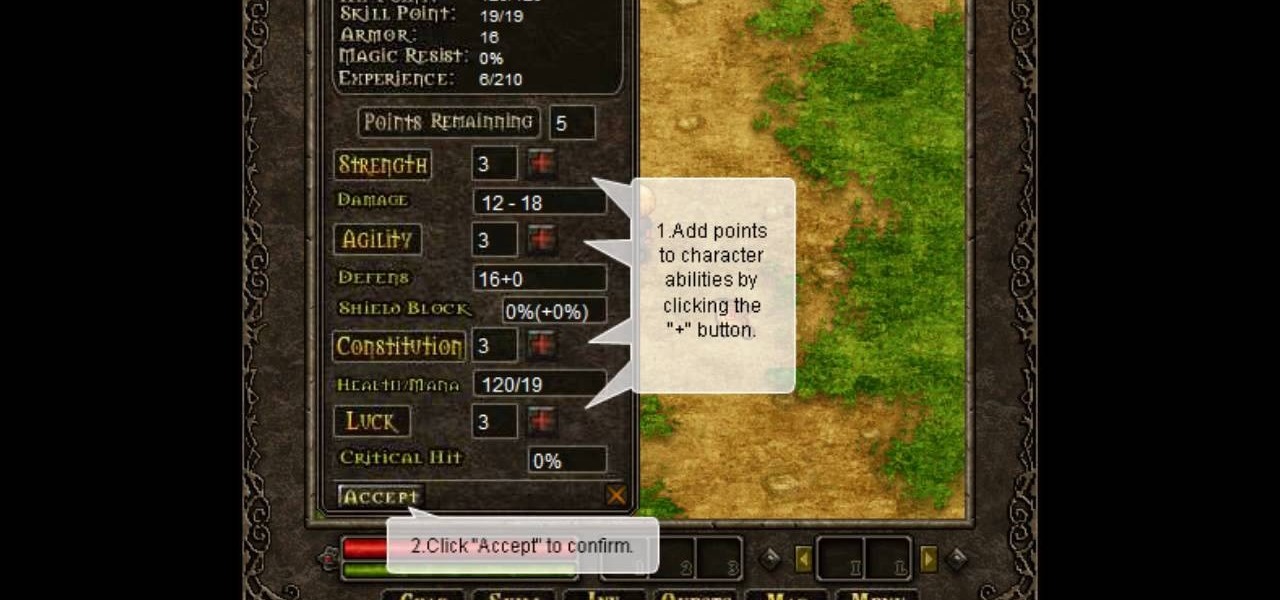
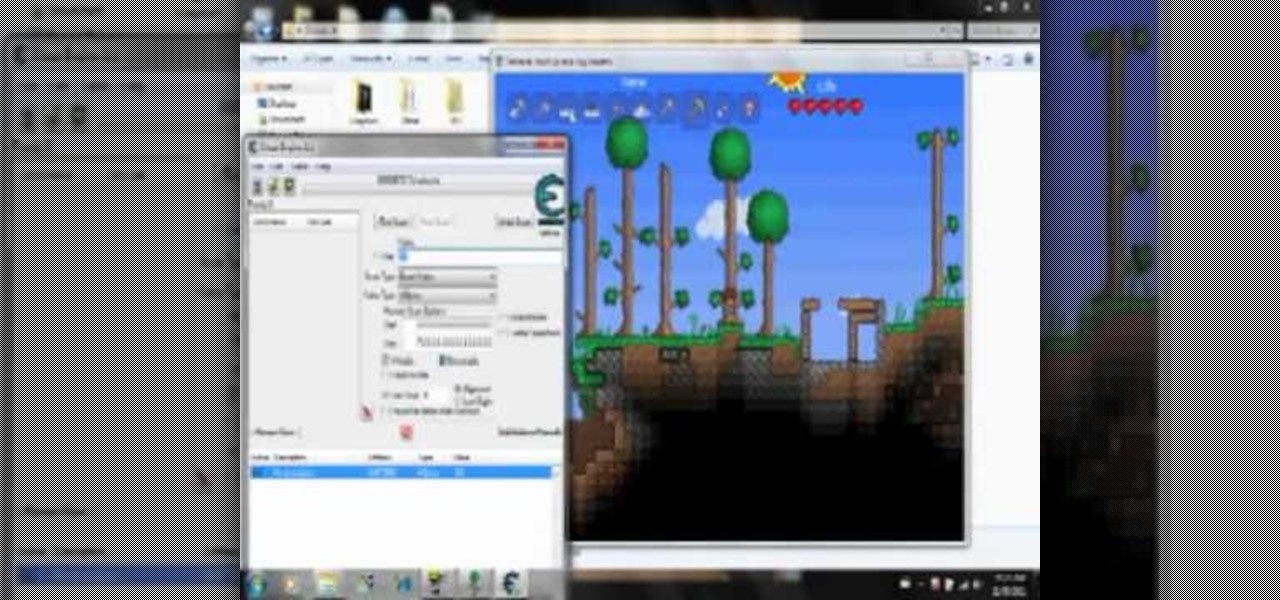
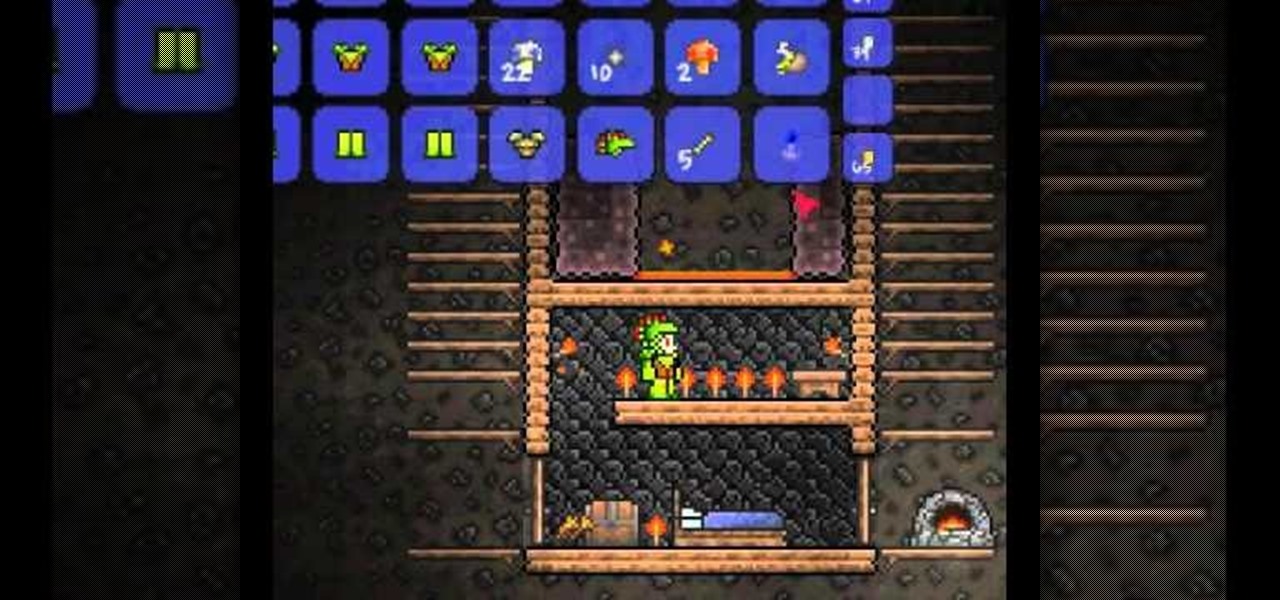
Wouldn't it be great to have unlimited health and mana? How about as much of whatever item you want, whenever you want? If that sounds like something you might be interested in, then check out this video to learn how to hack Terraria.

Check out this video to learn how to hack your Nintendo Wii by installing the Homebrew channel. This video will take you through all of the steps required to install the Homebrew channel to get access to Homebrew channel apps. Download Hackmii and Bannerbomb before you start.

Tired of the game turning off your Underground Jungle lava trap? Watch this video and learn how to exploit the game so that it turns back time, allowing you to earn more gold and platinum. Put this Terraria hack to use.

Are you tired of keeping all the music on your mp3 player to yourself? Share it with the world by hooking your mp3 player up to a radio and using the speakers for output. This simple radio hack of connecting a capacitor to the potensiometer will bring you endless hours of music enjoyment.