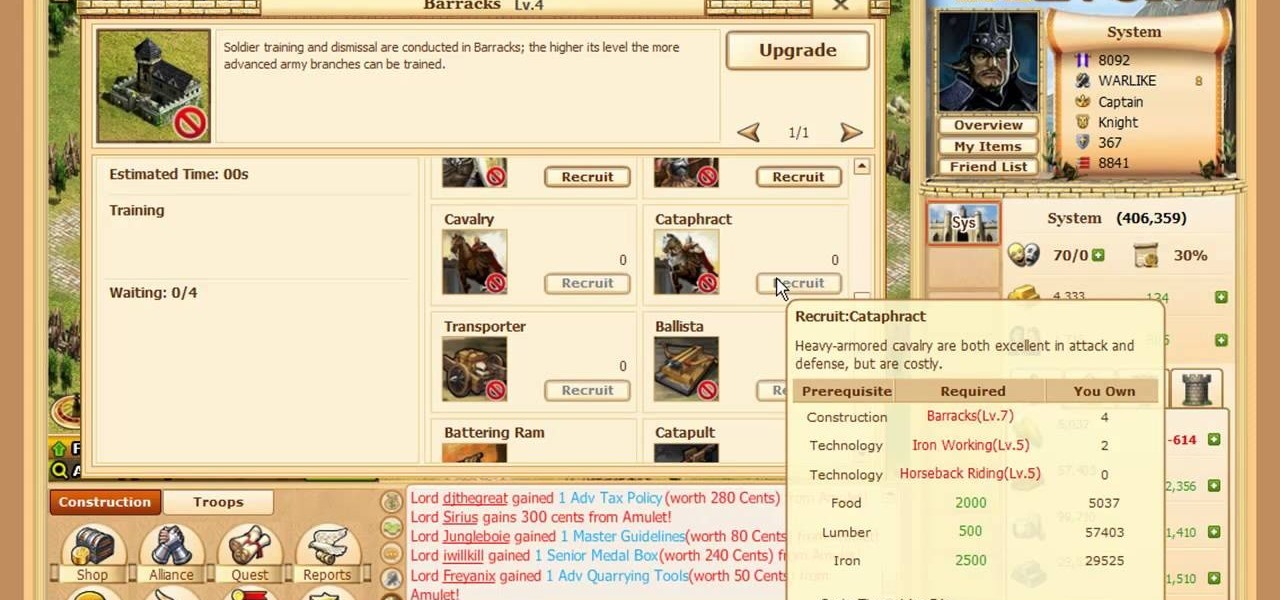
Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play Evony - Combat Unit: Cataphract. See exactly what the game Evony is!
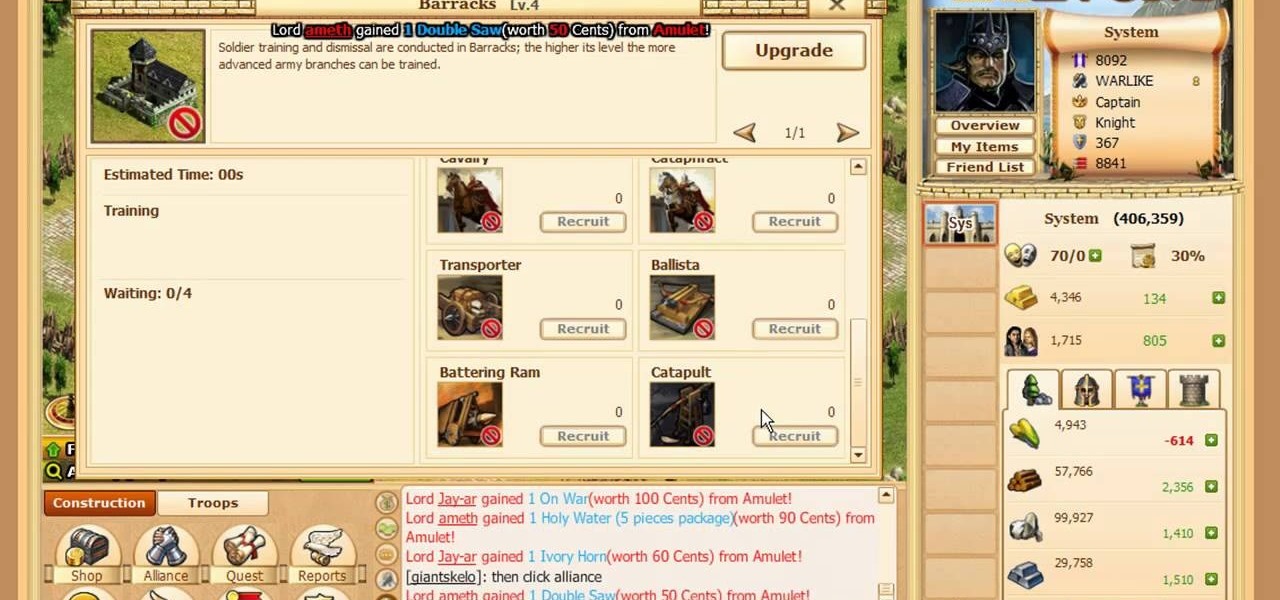
Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play Evony - Combat Unit: Catapult. See exactly what the game Evony is!
Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play Evony - troop upkeep and farming NPCS. See exactly what the game Evony is!
Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play Evony - Ballistas vs NPC. See exactly what the game Evony is!

A cool prank to play on a friend lies in your fridge... a soda can. Get out your Coke or Pepsi can, or any other soda can, and open it up. Now, wouldn't it be cool if you could close it again, without raising suspicion?
A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

To hack into Google images follow the following steps. You will first need to open a new internet browser window and go to Google, then load their images website. Next type into the search bar your image query and press search. Once you have gotten your search results paste the following code into your address bar:

This is a great glitch to help improve your planting and harvesting in FarmVille. Believe it or not, the fastest way to do this is to simply trap yourself. That's it.

Spice up your farm in FarmVille! Make your farm appear to be 3D with this sweet trick. This video tutorial shows how to stack hay bales and hedges in FarmVille (01/07/10). If you're getting bored with the rather flat look of Farm Ville, this trick will show you how to make what appears to be hills. Using these, you can make your farm truly unique! Watch the video for details.

Every once in a while, you will have a lot of work to do in FarmVille, and a lot of space to cover. Use the fullscreen option to make life easier and see more at once.

Proud of the progress you've made in FarmVille? Take a photo within the game, and share it directly with all your friends!

Arranging fences can be a hassle if FarmVille. Once you understand the basics, however, you will be creating elaborate fence layouts in no time!

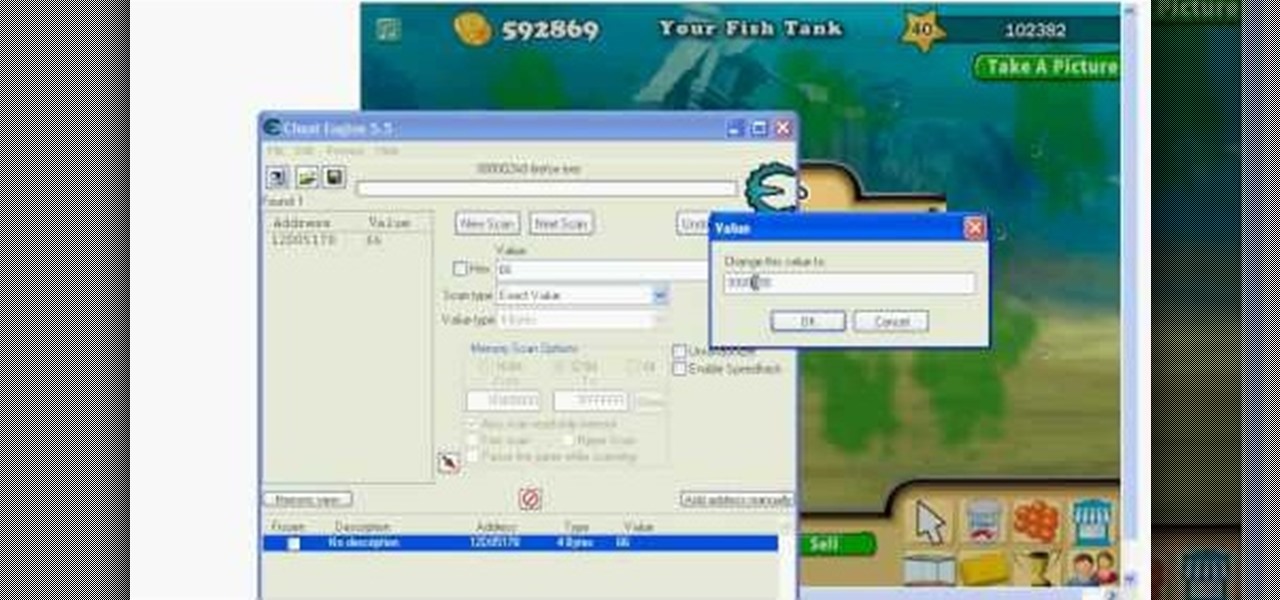
This Facebook Fish World cheat will give you more money by selling money… wait, what? Yep, sell and earn more coins in Fish World with Cheat Engine.

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video game tutorial to learn how to auto clean plates with glitches in Restaurant City (06/05/09). you basically just click "redecorate" and save. That's it.

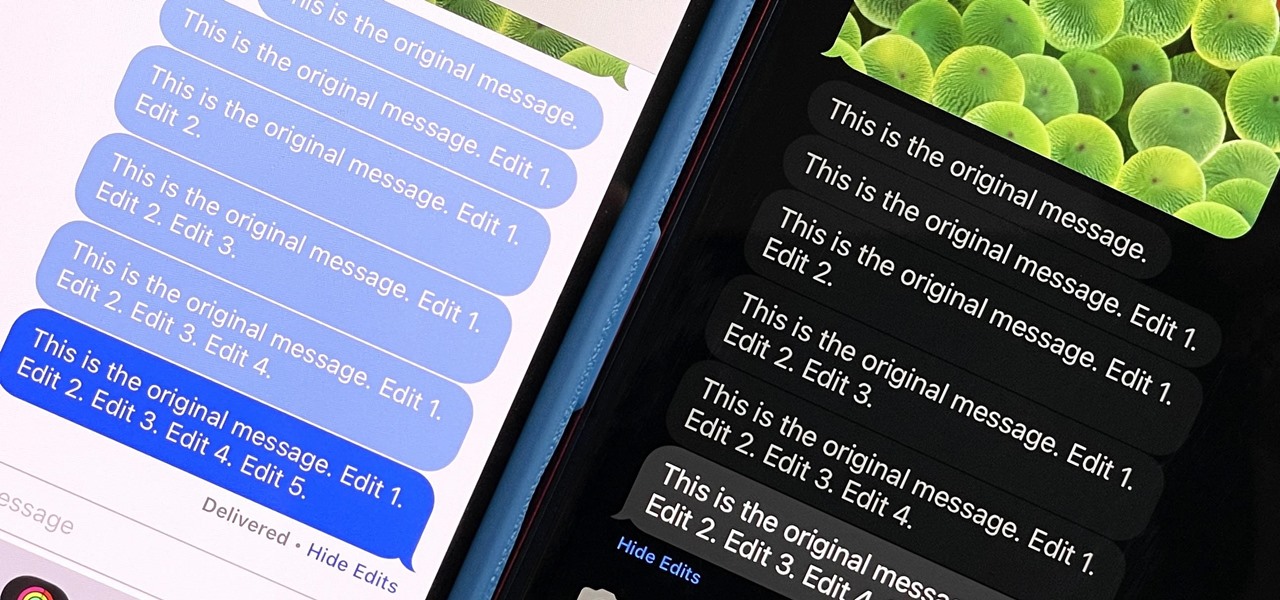
Apple's controversial iMessage-editing feature in iOS 16, iPadOS 16, and macOS 13 Ventura is now less likely to be abused by malicious users.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

If you're an avid programmer or developer, your time is likely spent creating apps and perhaps the occasional website. And while these go-to coding endeavors are exciting and occasionally lucrative, more and more coding pros are turning to careers in cybersecurity and ethical hacking — thanks to the high pay, flexibility, and unparalleled opportunities.

Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensuring that no one else can access your private chats.

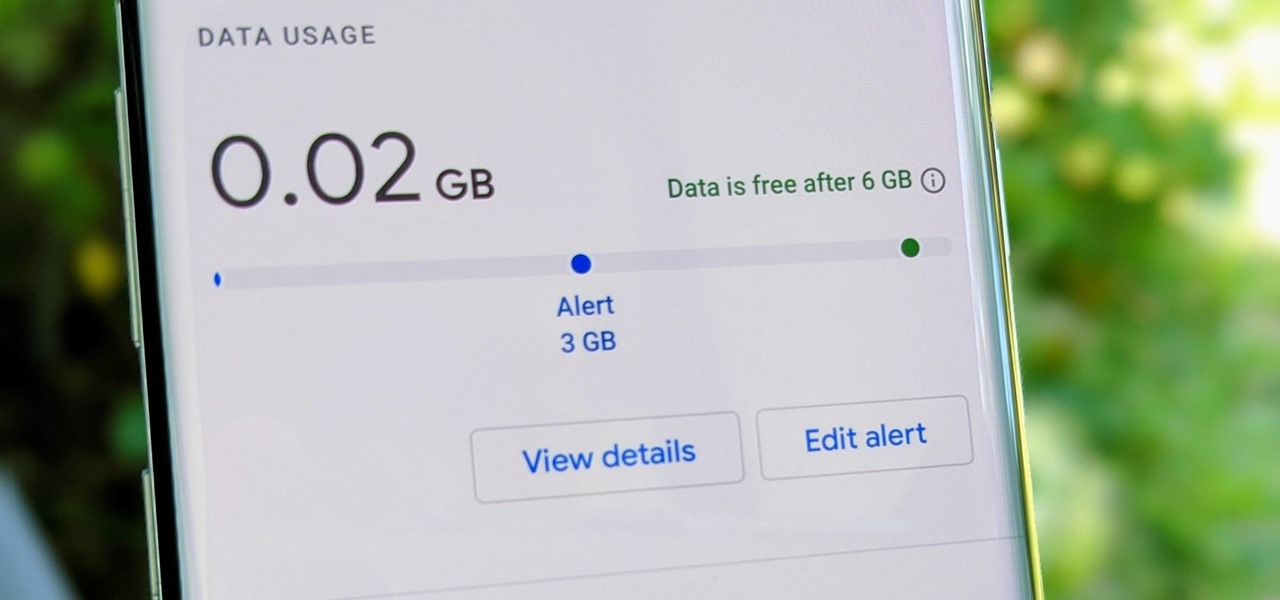
Google Fi Is a great wireless carrier alternative and can be quite beneficial when used correctly. If you don't require much data, you can easily get away with a $30 or less bill. However, if you wanted to crank out more data during your current billing cycle, there's a setting you should use to keep your data in check.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

It is a scary time to be alive. As states start to ease back shelter-in-place restrictions, the new world you're entering is still unsafe. With a vaccine months away, your best bet is to follow CDC guidelines and use the tools at your disposal.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Even though Samsung has features like the always-on display, you still might miss some notifications now that the alert LED is gone. But baked in One UI is the ability to turn the rear camera flash into a notification LED. Any incoming alerts or calls will cause the camera LED to blink, so you won't miss a thing.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

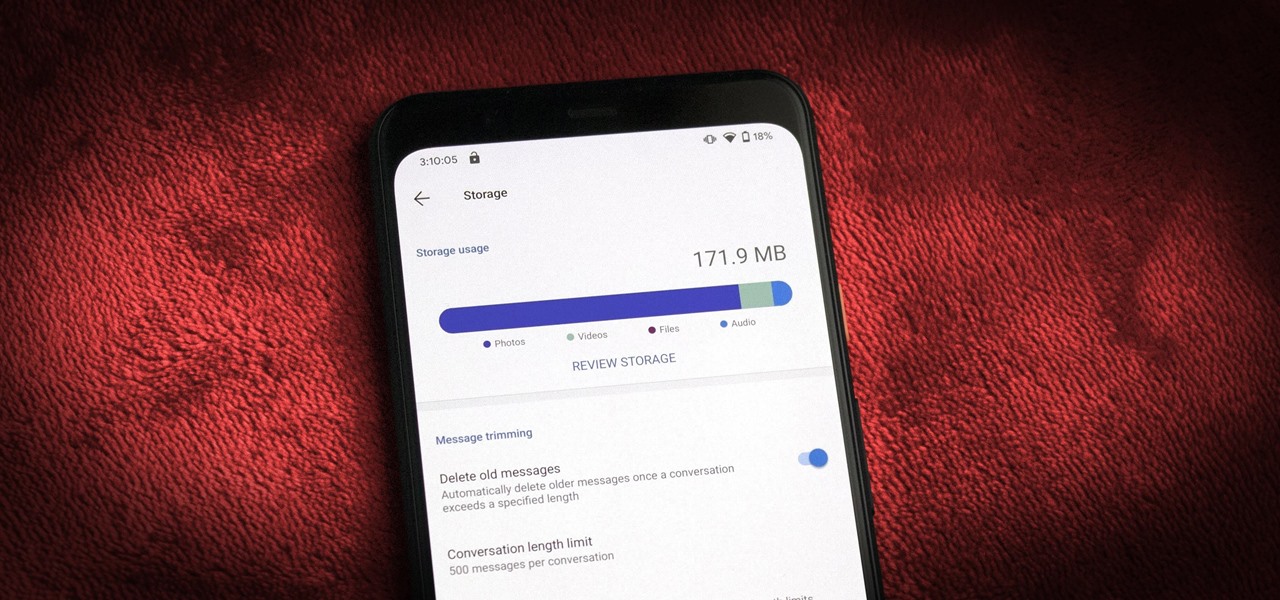
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

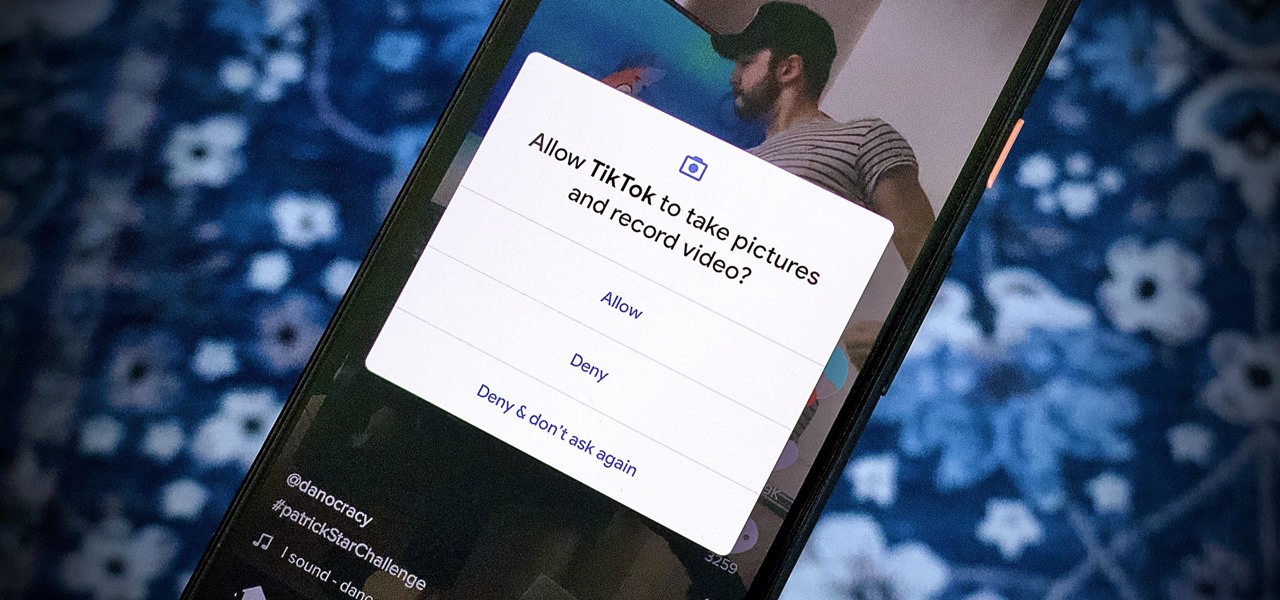
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

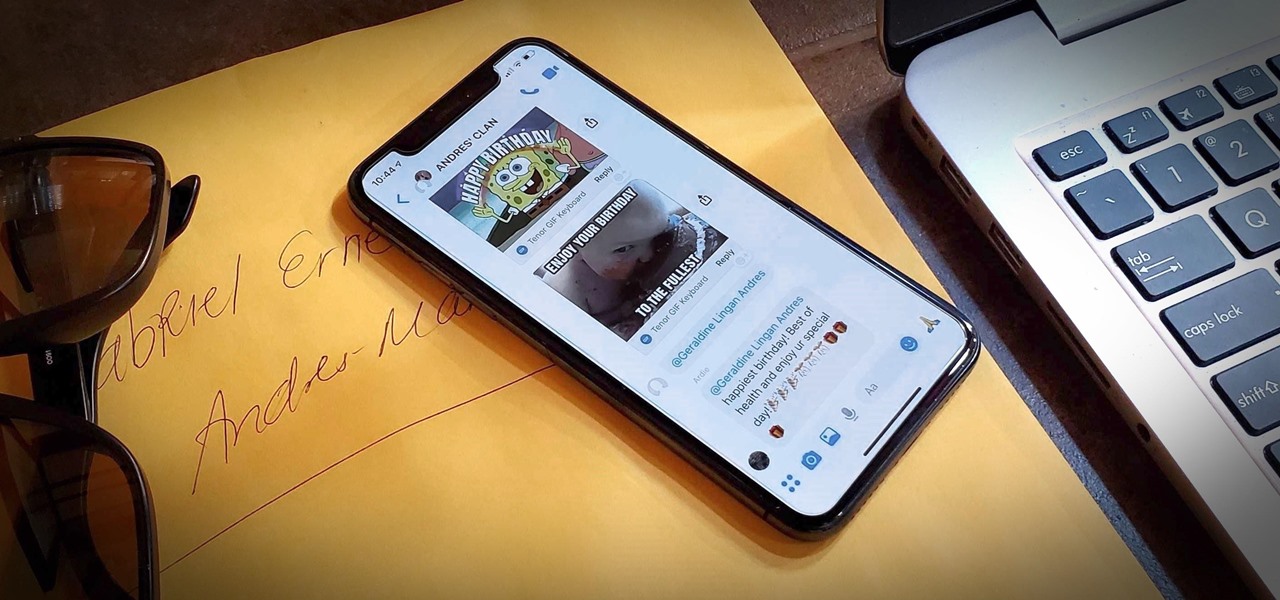
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?

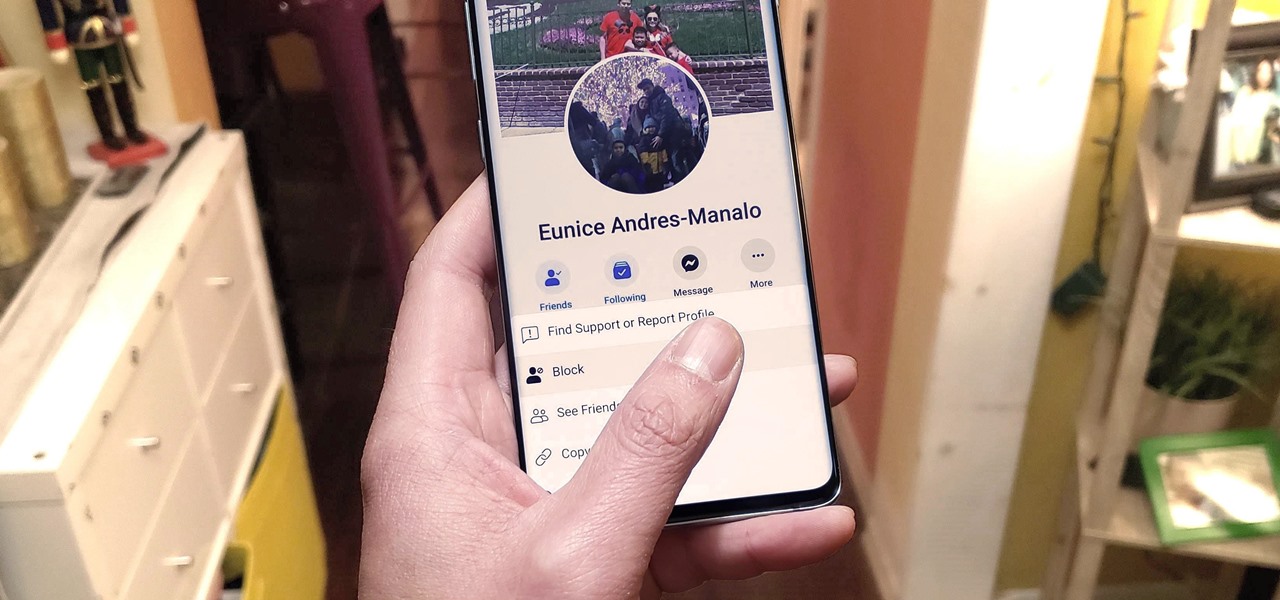
It's easy to block a person or a website from appearing in your Facebook feed, but it isn't as easy to undo that. Thankfully, there are still ways to unblock people directly from your phone.

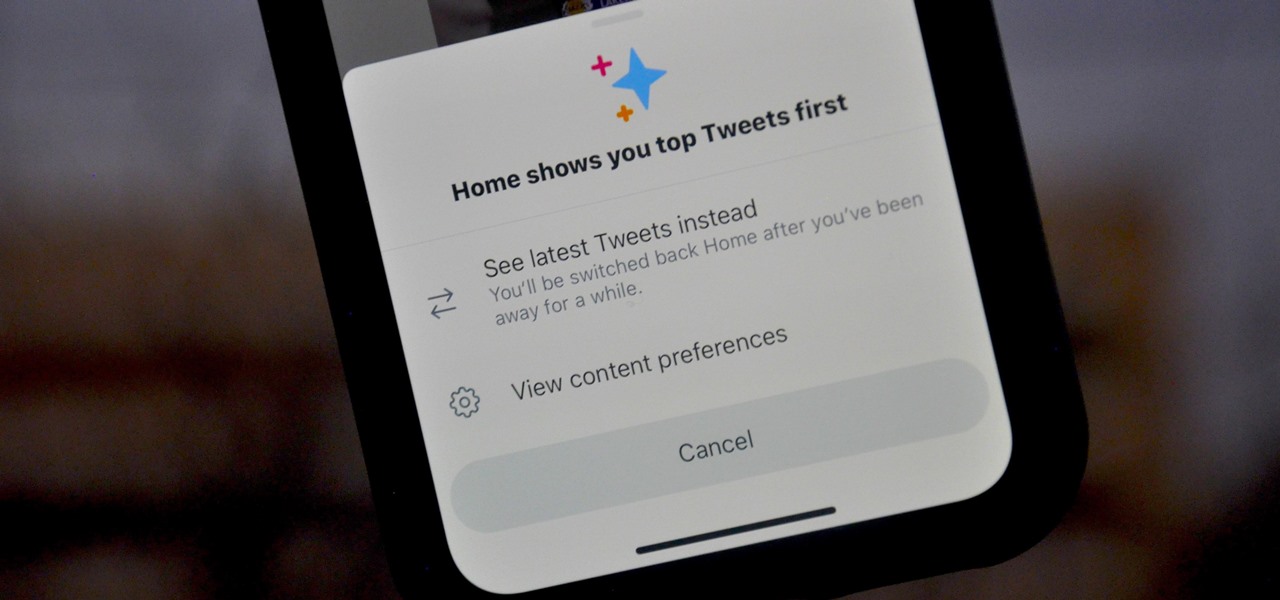
If you're tired of the so-called "top" tweets appearing first in your Twitter timeline instead of only the latest from the people, companies, and bots you follow, there's a way to get rid of them.

The Google Pixel's camera is a status symbol of sorts. When someone sees you with one, you become the photographer of choice for social events. And where do those photos end up? Social media, of course. It's how we share our lives now, and the smartphone camera defines how we approach that.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.

Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

After establishing itself as a leader among media companies in augmented reality in journalism over the course of 2018, The New York Times pulled back from the technology this year.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

One of my favorite iOS hacks is Type to Siri. This lets you type your queries to the iPhone digital assistant without needing to use your voice. Unfortunately, Type to Siri replaces the typical Siri voice prompt on the Home or Side button, meaning you need to choose between one or the other. That is, until iOS 13.