The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — solutions and platforms currently available for mobile AR.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.
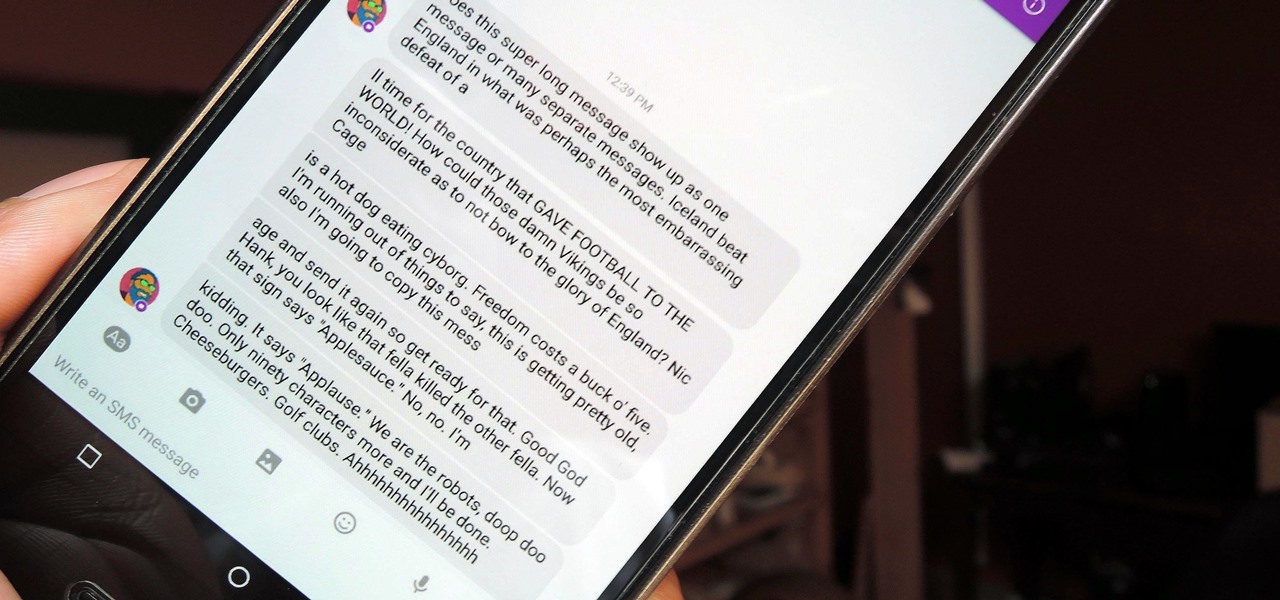
Depending on your carrier and the texting app that you use, sending long SMS messages from an Android phone often results in the recipient being hit with a barrage of fragmented, out of order texts.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

So, how does someone keep their hacking life completely secret? What This Is:

If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and novices alike.

Step aside, vodka—whiskey will soon be the best-selling hard liquor in the United States. The whiskey renaissance has been largely attributed to the current trend for locally- and artisan-produced goods. Local whiskey distilleries are rapidly increasing in number across the nation while bars in every state are including the old-fashioned cocktail on their menus in an attempt to capitalize on the trend (which we can probably thank Mad Men for).

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

If you have a Barnes & Noble Nook, you may be surprised to find that your eReader can do a lot more than just display ebooks, which makes it a great alternative to those more expensive all-in-one tablets that do everything (seriously, everything). If you want to get more bang for your buck, here are a few ways you can hack your own Nook.

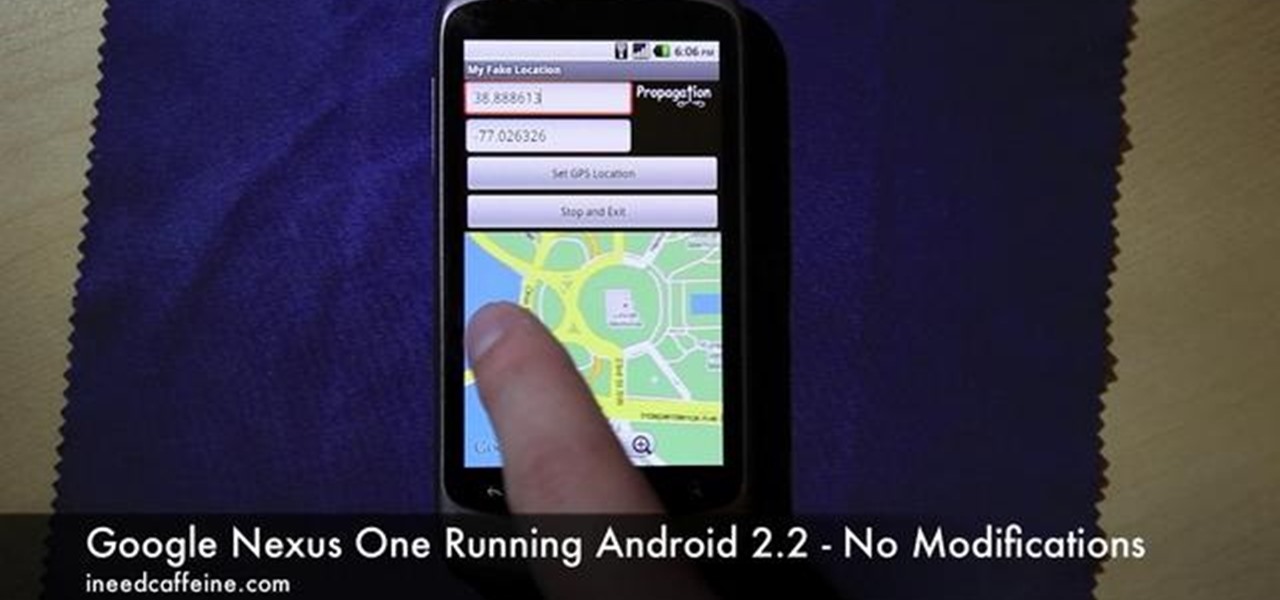
Enjoying the many benefits of Facebook Places? But what if you want to check in somewhere you're not? Your smartphone can automatically detect your geographical location, preventing you from just checking in just anywhere, but like all technology… it's a long way from perfect, even Android mobile devices.

There are several different kinds of disc drives that come in different iterations of the XBox 360, and each one has to be hacked a little differently. This video will show you how to flash the ms28 drive used in some systems, the second part of the video will show you how to determine what model of drive you have. It is very detailed, and should have you well on your way to hacking you beloved XBox 360 and maximizing its potential.

This video tutorial shows how to hack FarmVille (07/02/10).

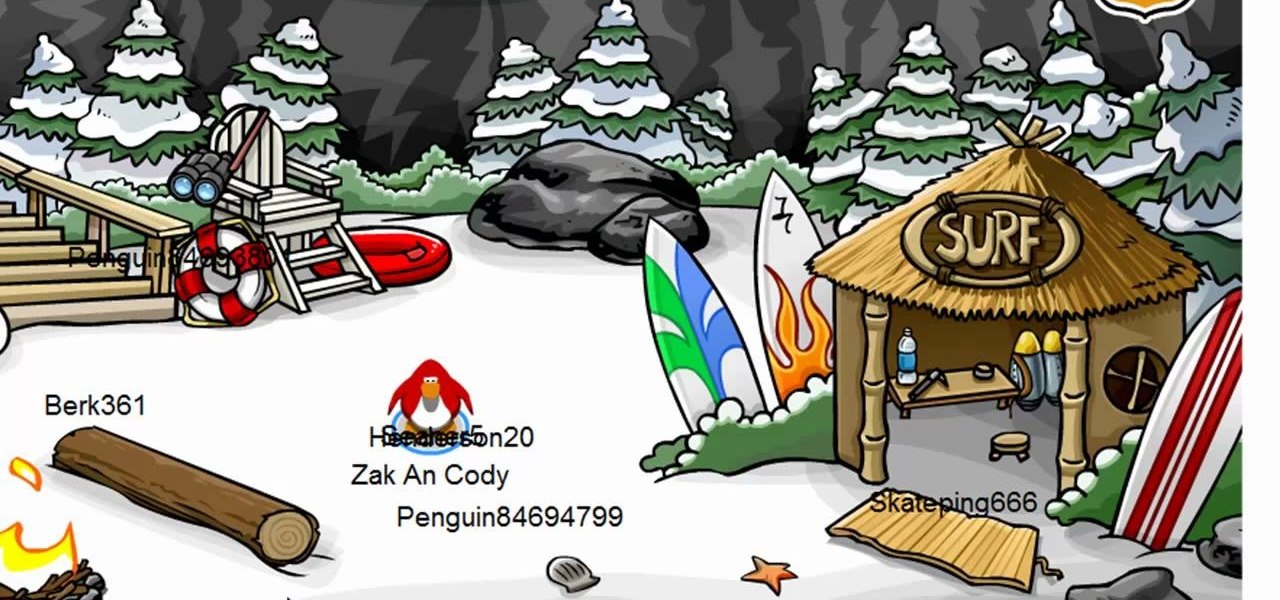
Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to hack Club Penguin for loads of money with WPE Pro (03/22/09).

Farkle hacks, cheats, glitches. How to hack Farkle. Watch this video tutorial to learn how to play Farkle and Farkle Pro on Facebook. Learn about scoring and gameplay in Farkle. What's you highest score?

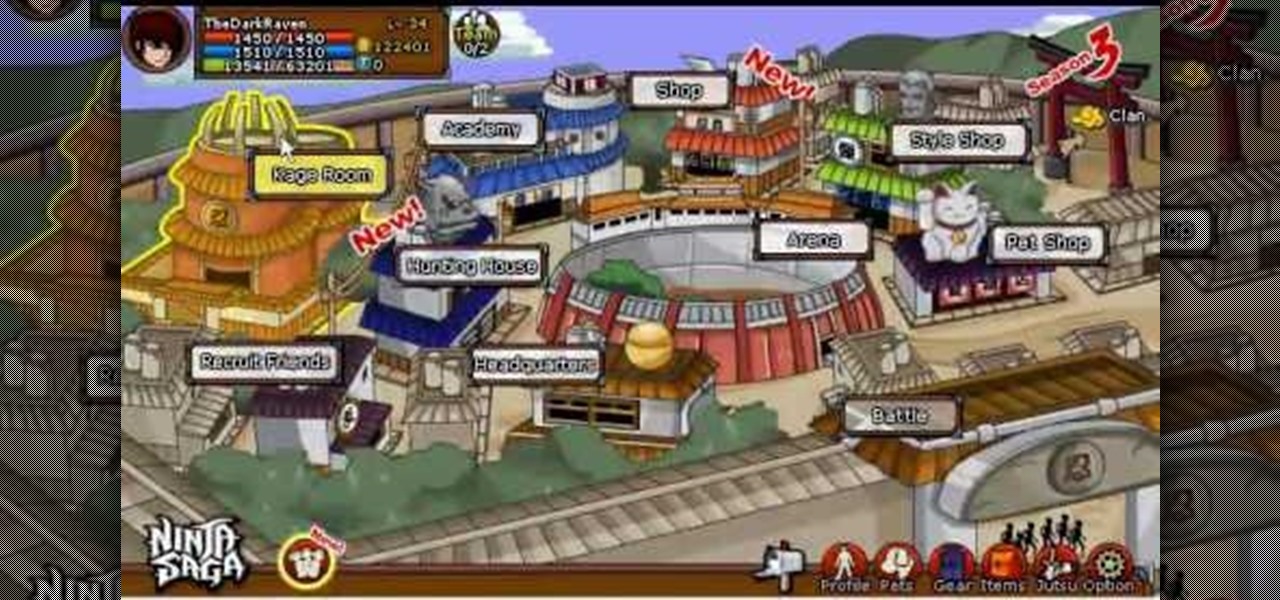
Get higher skills in Ninja Saga! This cheat lets you hack into the game and give yourself higher skills in your jutsu. This shows you how to use Cheat Engine 5.6 and increase all your jutsu skills for your play session. As long as you're using Mozilla Firefox, this cheat will work!

Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack levels and gold in Ninja Saga (11/11/09).

Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack Ninja Saga EXP (11/07/09). Download Cheat Engine.

Hack MyBrute with this MyBrute cheat! MyBrute is an online flash game where you battle other brutes one on one. Watch this video tutorial to learn how to hack MyBrute to receive a bear pet (11/07/09).

Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack millions on Restaurant City (11/15/09).

This might be an old hack for Happy Aquarium, but for some of you it may still work. Most of you will not be able to do this, but it's always worth a shot, right? It's a cheat from 9/29/09 (wow!—retro hack) for which you need Cheat Engine 5.4. Newer versions of Cheat Engine should work, too.

Craving candy but have no change? Then listen closely to this hack. This con how-to video shows you how to hack a candy machine by creating fake quarters. This hack trick should also work on parking meters. Never pay for candy or meters again. Watch this video tutorial on YouTube and learn how to hack a candy machine with a paper coin or cardboard.

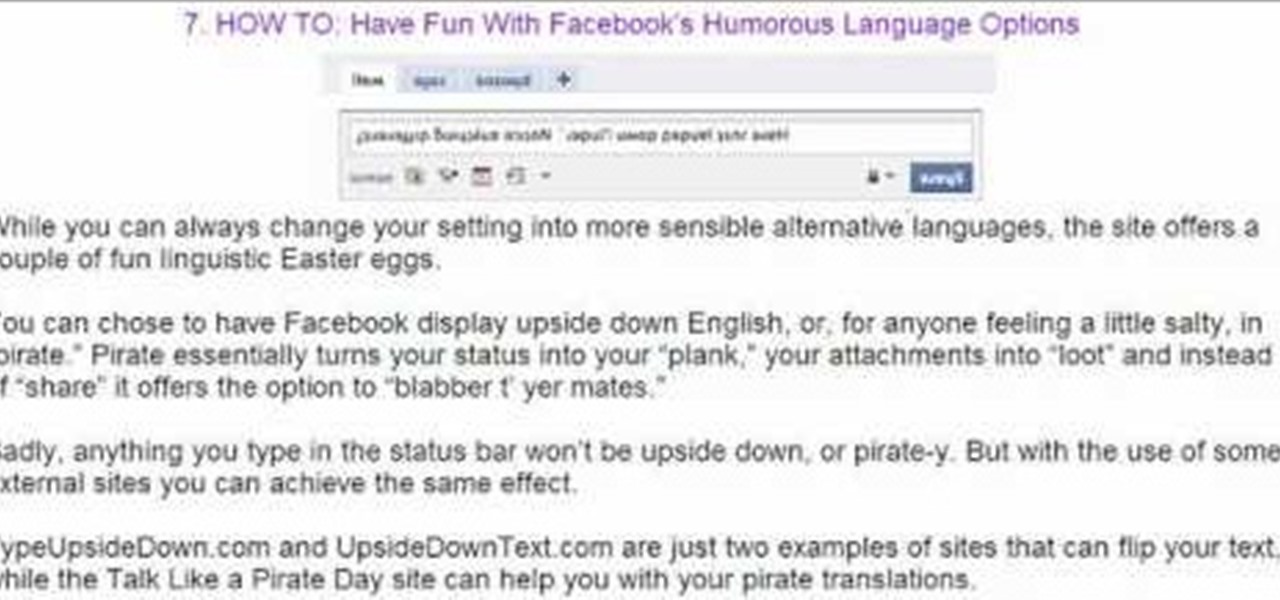
Want to add a dislike button to your page? Or want to make an update about what you did last night, but don't want your grandmother to read it? This video shows you ten ways you can hack your Facebook page. You can also pre-schedule certain status updates, set your Facebook language to 'Pirate English', create a status update word cloud, tag your friends in updates, add symbols to updates, and even redirect your friends back to their own profile page!

In this video, we learn how to hack Sandcastle with Cheat Engine. First, start the game and then click the process list icon. Now, use the Firefox browser and then type in the amount of gold you have into the value section. Now, buy something and then click the frozen box and change the value to 999. Next, when you buy something it will say that you have unlimited amount of cash. You will be able to buy all of the things you want, and you won't have to gather more coins to do so! This is a ve...

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to restore your Google ranking after your website has been hacked. Hopefully you never will be, but if you are this video is her...

ios249 is a sweet little hack for the Wii that allows you to play backup burned copies of games on your console. Pirated games will work too, although we DO NOT condone piracy. This video will walk you through the whole rather elaborate process of installing it on a hacked Wii with the Homebrew channel. You will need to download a whole mess of free software:

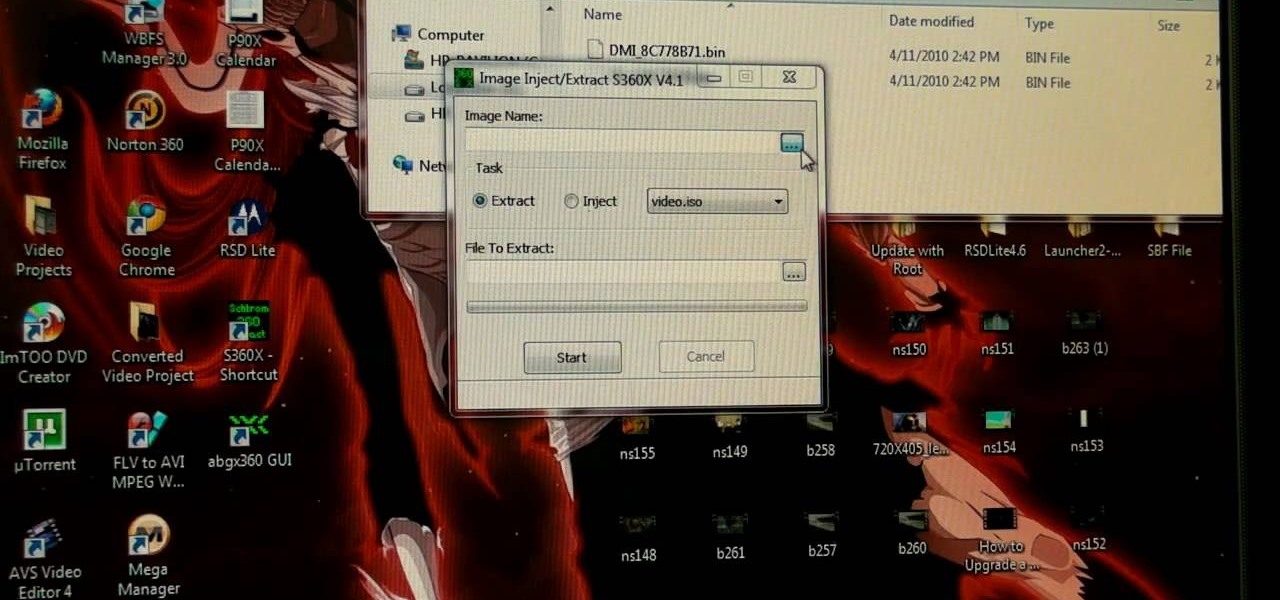
You can hack you XBox 360 as perfectly as you please, but if you don't burn the games that you want to play on it properly than it will all be for naught. This video will teach you an important part of the process, using AGBX360 and S360X to stealth patch your .iso game files and make sure that they are SSv2. Taking these steps will ensure that the games you are burning are ready to be played on XBox 360's and ensure greater enjoyment of you XBox hacking experience.

God knows there are a lot of shabby sandals around today. The only solution to the perfect pair of flip-flops is to mod them yourself. Add a little glamour to your sandals and see how to glam up your flip-flops in this video from GiannyL.

This is a Computers & Programming video tutorial where you will learn how to hack Google to find anything. There are no audio instructions; only a demonstration of the steps to follow. Go to Google and type into the search box: intitle:”index.of” (type anything here) and search. For example, type in: intitle:”index.of”Shakira mp3. And click search. Then you will get the search results. Now you can click on Index of…/songs and it will take you to the songs index page. From there you can downlo...