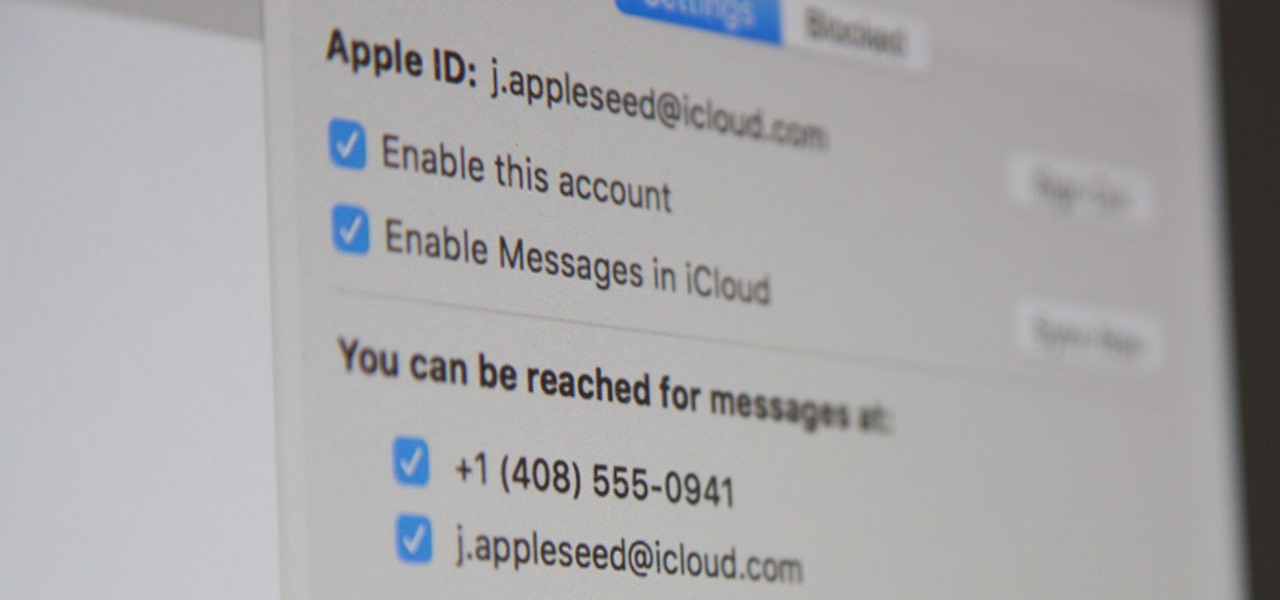
Apple pushed out iOS 11.4 on May 29 to iPads and iPhones, which included the long-awaited Messages in iCloud feature. The company did not release macOS High Sierra 10.13.5 at the same time, limiting the usefulness of being able to sync messages in the cloud since 10.13.4 is not compatible with Messages in iCloud. But three days later, Apple finally released macOS 10.13.5.

In usual Apple fashion, there are new wallpapers to go along with their new operating systems, iOS 10 and macOS Sierra. The background that's included in iOS 10 for iPad, iPhone, and iPod touch is a crashing aqua-colored wave with land just below its surface, and macOS Sierra's is a razor-sharp mountain ridge from the Sierra Nevada mountain range in California.

While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.
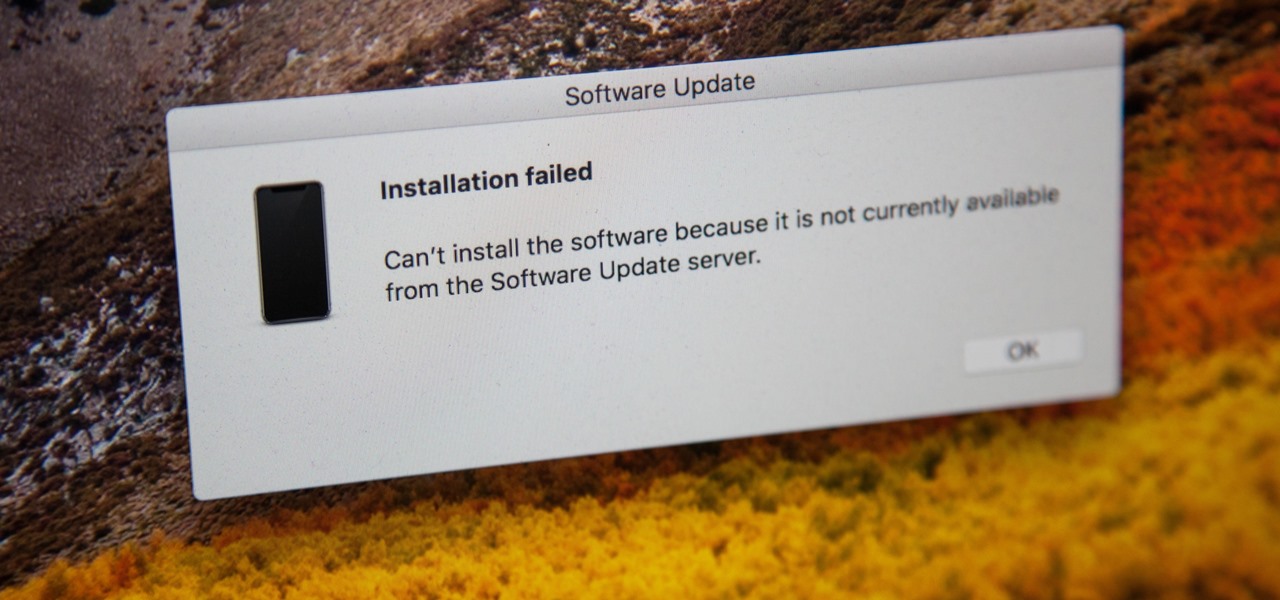
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

The official release of Apple's iOS 10 mobile operating system is still a few months away, but starting today, June 7, the public beta version is available to download if you'd like to get a head start on checking out all the cool new features included in Apple's latest mobile OS.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Apple revealed three new iPhone models on Wednesday, Sept. 12, at its "Gather Round" event in Cupertino, as well as announced the official release date of iOS 12, its newest mobile operating system. If you missed it and want to watch the full event, here's how to do it on your computer, smartphone, or Apple TV.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

It's here! Apple just released the latest version of iOS today, Monday, March 25. Version 12.2 has seen six beta releases, spanning the course of fewer than three months. The new update sports 30+ awesome features, including new Animoji, air quality reports in Apple Maps, and AirPlay 2 support for compatible TVs, in addition to a slew of new UI tweaks and redesigns.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might be a little confused on how to enter DFU mode when your iPhone acts up.

Nothing has stopped you from taking a screenshot of a funny moment in a FaceTime video call before, and nothing probably will. But screenshots are old news. Apple has made it even easier to take capture FaceTime moments on your iPhone, and the results are more lively.

Monday has been a big update day for Apple. Alongside the release of iOS 10.3, iWork has been updated across both iOS and macOS. The biggest change is the ability to unlock password-protected files with Touch ID, either on iPhone and iPad, or on the new MacBook Pro with Touch Bar.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

The next big event Apple is holding is WWDC 2018, its Worldwide Developers Conference, is about to happen. If you want to see the first glimpse of iOS 12 for yourself, as well ARKit improvements, Apple Watch news, and maybe even some macOS announcements, here's how you can tune into the event right at home from your computer or mobile device.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

This video illustrates the easiest method to Dual Boot Vista and MacOS on a single PC. This process is comprised of the following steps-Step 1. First install Windows Vista to your PC.Step 2. Run the software "Bootmaster" in windows.Step 3. When asked for the number of operating system to be installed choose Dual Boot option.Step 4. You would be asked for the type of operating systems to be installed on the computer.Step 5. Choose MAC OS and Windows Vista OS.Step 6. Insert the MAC OS CD and th...

This video tutorial from JdudeTutorials presents how to download a torrent for the first time.To start, open your Internet browser. Browse to utorrent web page.Download and install uTorrent client version, suitable for your operating system (MacOS or Windows).Once you've installed application, browse to The Pirate Bay.This is the largest torrent source in the world.Check Video option under the search bar and type family guy (as an example).Click Enter. A list of torrents connected to family g...

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

Apple had its Worldwide Developers Conference on June 3, 2019, which showcased big software announcements for all of Apple's hardware, and anyone can watch the keynote as it happened.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

It's that time of year again — Apple will be hitting the stage in California to talk about new features coming to iOS and macOS devices in the near future. Of course, you're going to want to tune in and be up to date on all the changes coming to your Apple products.

You may not want to disable notifications for the Mail app entirely on your iPhone since you could miss essential emails when they come in. But you can at least silence conversation threads on an individual basis. Doing so won't mute all conversations from the same sender, only the thread you select. Plus, it works for group email threads where things can get chaotic.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.

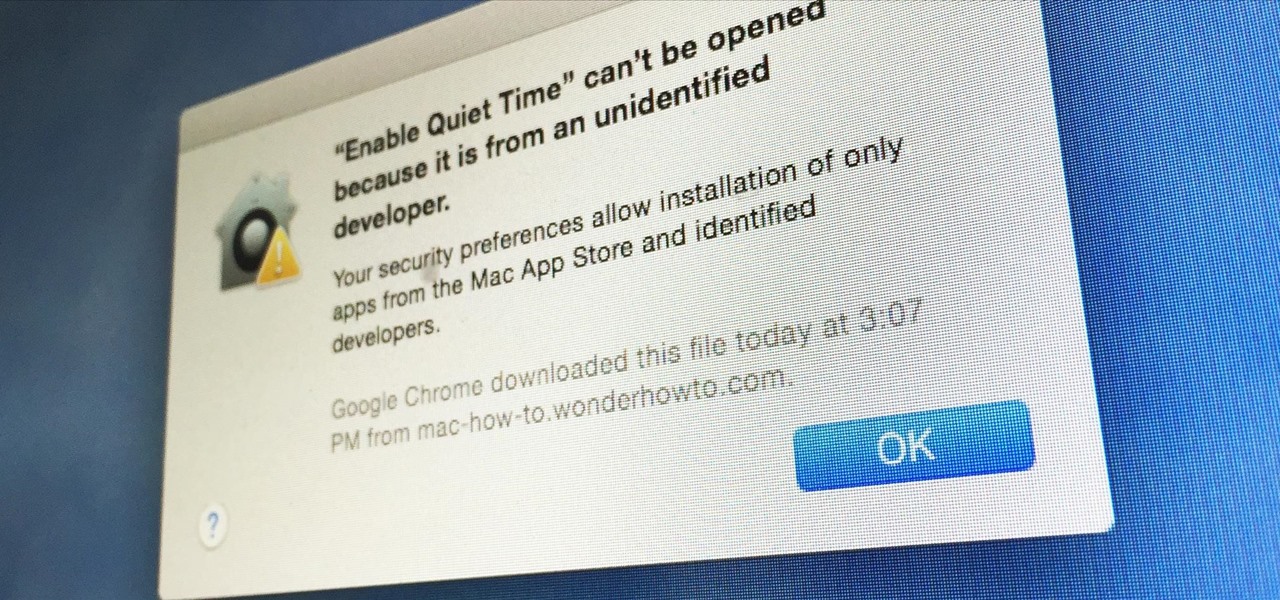
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

This video tutorial from dproxisback presents how to download and install Handbrake DVD ripping tool.To avoid installation problems, carefully choose application version for each type of computer and operating system.Open your internet browser and visit http://handbrake.fr/?article=download web page.Choose correct version for your type of operating system (MacOS, Linux, Windows).Download and install the application. Run Handbrake once it's installed.Click File-Select Source. Browse for your f...

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.