When I crack open a new book, I always make sure I have a pen and a highlighter nearby so I can mark away! Anything particularly witty, inspiring, or engaging gets highlighted, underlined, or circled. When I use the Amazon Kindle app on my phone, I do the same thing by writing notes and highlighting, but I often find it difficult to keep track of my markings.

UPDATE: It was previously reported that the OnePlus 3T 128 GB in Gunmetal would be discontinued. GSM Arena received an official rebuttal from the company which noted that the phone is not discontinued, but rather, out of stock. Though, it seems like the company has more of a problem keeping track with what its reps report, rather than its phone supply.

The Nokia 6 has been out since January, releasing in China before having a slow trickle of releases throughout the year. Despite announcing a global release, the United States never received a street date for the smartphone, and for all this time, Nokia has left us out to dry. Now, it seems, their phone could be on its way as the 6 has received its FCC certification.

Google's Gboard is by far the most popular keyboard available right now. Gboard lets you search almost anything—from regular Google searches, to emojis, and even GIFs—just by using your keyboard. The app even lets you share search results, saving you a great deal of time, which would've otherwise been spent juggling between apps and programs.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.
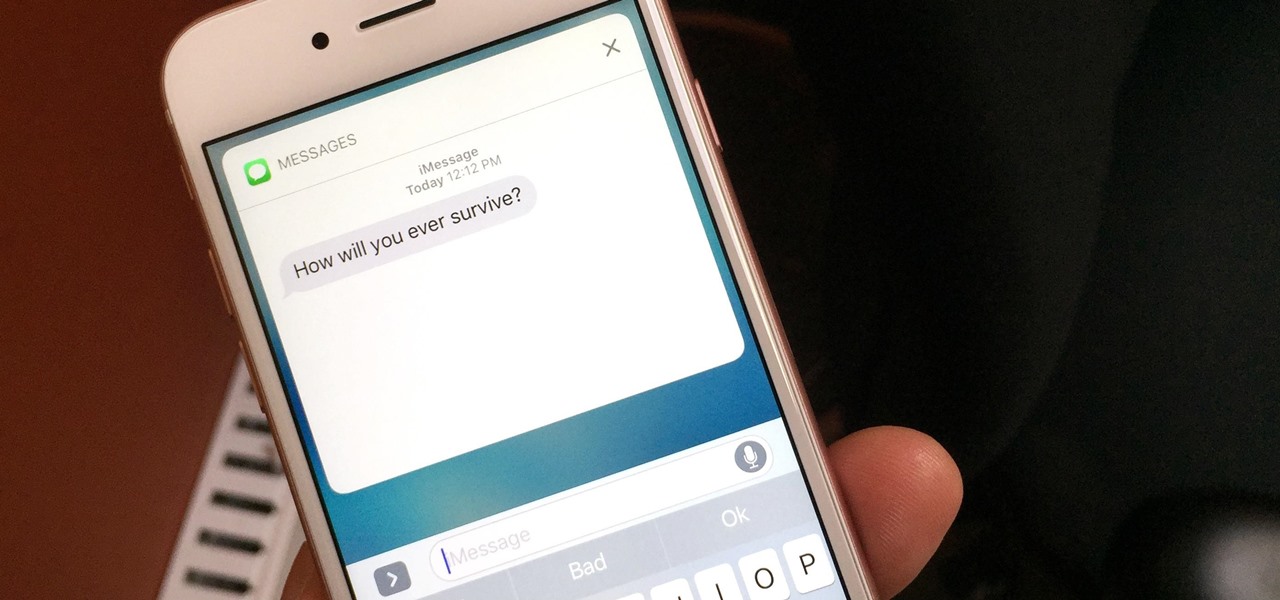
If you have an iPhone with 3D Touch or Haptic Touch, some lock screen notifications will let you respond to a message without even unlocking the screen. This is definitely a handy feature, and it should save a lot of time in some cases, but there are some obvious security concerns.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

Google switched things up this year by releasing a developer version of Android N far ahead of I/O, but that's not the only convention they've done away with this year. For the first time, Google will accept name suggestions from the public.

One of the more annoying parts about cooking or baking at home is dealing with sticky ingredients. You scrape the peanut butter out of the jar and into a measuring cup to make sure you have the right amount for your recipe, then scrape the correct amount into the bowl you're cooking with.

Even the most seasoned cook is always looking for ways to make cooking easier and cleaning up after meal prep a breeze. There are a million and one tricks and tips out there to simplify your kitchen routines, but some of them are more valuable than others.

Learn how to paint nails perfectly - with nail hacks every girl should know, with my SuperWowStyle Nail Art Videos!

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

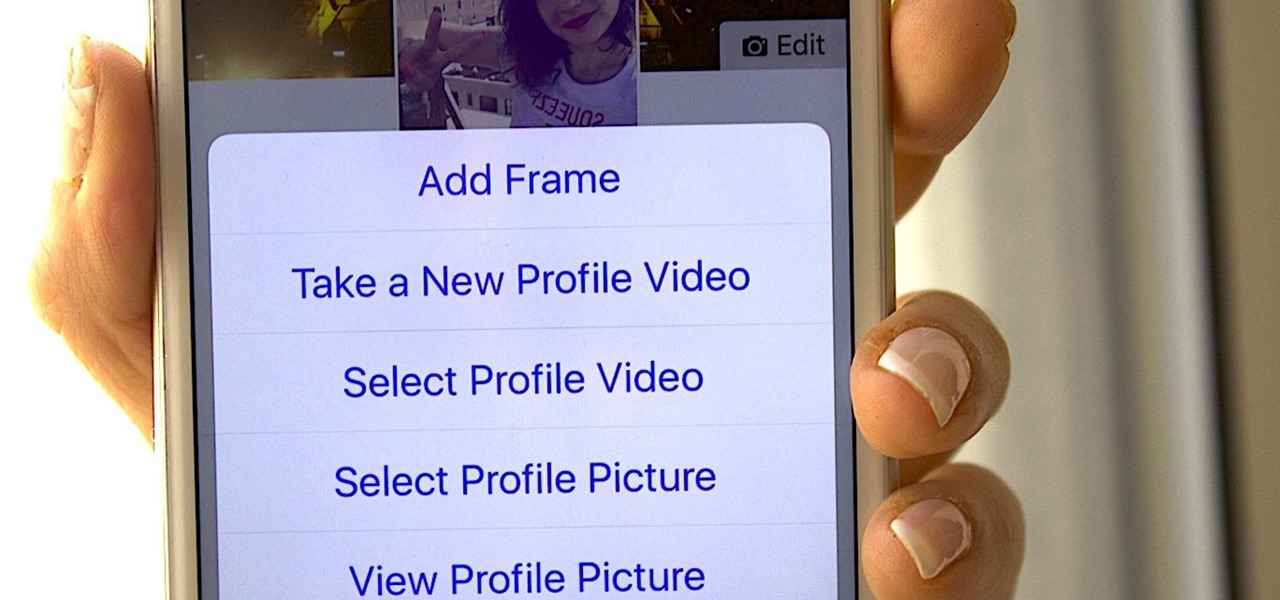
Instead of the still image we've been accustomed to since the inception of Facebook, you also have the option to apply a seven-second video as your profile image, which definitely mixes things up a bit with GIF-like animations. Best of all, this can be done straight from your iPhone or Android device.

Many home chefs are deterred from whisk-intensive recipes such as mayonnaise because they seem to require more than two hands—which is obviously the maximum number we possess. One hand is required to stabilize the bowl, another must be whisking constantly... and a third hand is needed to pour a steady stream of oil.

Bored of your old casual tees? Try these hacks to make them snazzy in a jiffy!

Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this:

Check out this video from CouponCodesHero on hacking a vending machine in no time. All you need is a little packing tape and some paper money, then fool the machine to either get free stuff, or use the "change" to get free money!

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

This video has 7 fraction hacks that can save you time when working with fractions. The hacks are: Adding fractions without a LCM

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

10 Life Hacks: 1.Wifi Booster

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

How to hack an Oreo, i.e. dunk an Oreo in milk perfectly.

In a 10 button Nesquik vending machine or other 10 button vending machines, you can hack to get credited for free drinks.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

Wouldn't it be awesome if your glasses could detect when it's bright outside and automatically darken? Well, the technology has been around for a while, but it'll set you back a few hundred bucks.

The Lesser Evils side quest is accessible immediately after completing the factory hostage mission at the start of Deus Ex: Human Revolution. This Giant Bomb tutorial will take you through the mission, which involves breaking into an apartment building complex and hacking into a computer to uncover the location of a video.

If you want to enter the police station armory in Detroit while playing Deus Ex: Human Revolution, you either need to have enough credits to afford it, or you need a high hacking skill. This video from Game Front will allow you to skip both of those requirements by giving you the password to the armory so you can take all the weapons you want.

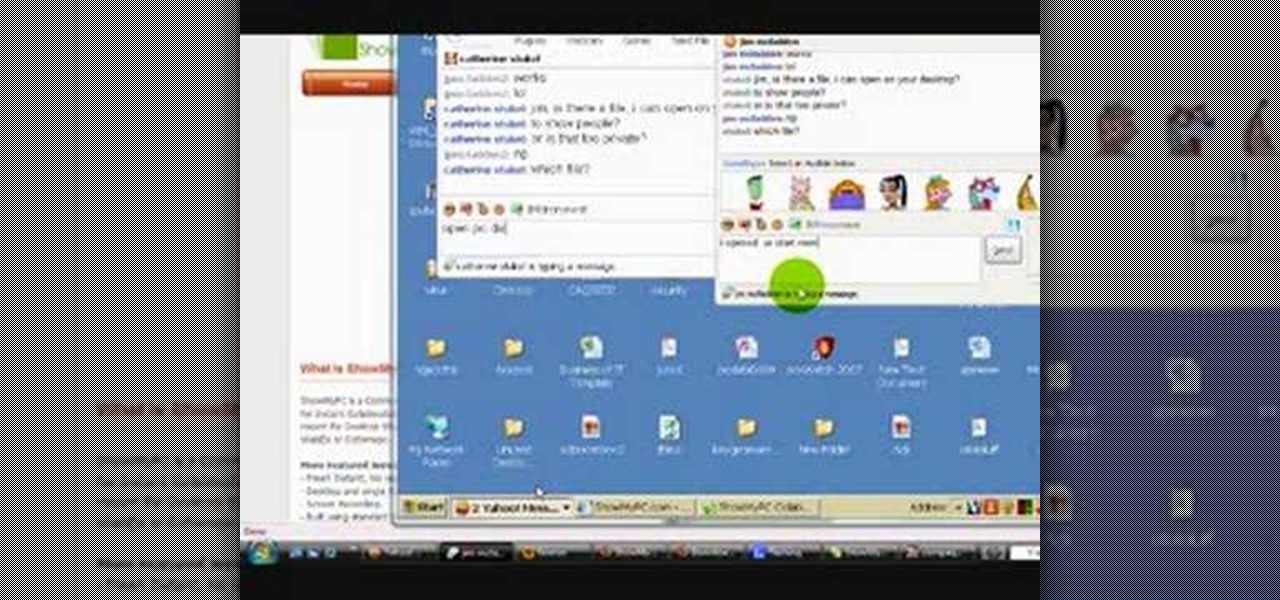
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the website ShowMyPc.com and be able to see what your target has been up to. Even better, you can use that computer and the files on it as if it were your own desktop!

Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account.

You need money to become King and then run a country, and in Fable 3 this is especially true. If you need more gold in Fable 3, you've come to the right place, because this video will show you how to get unlimited, infinite gold. Literally as much as you want. Cheat away, good friends, before this glitch is patched.

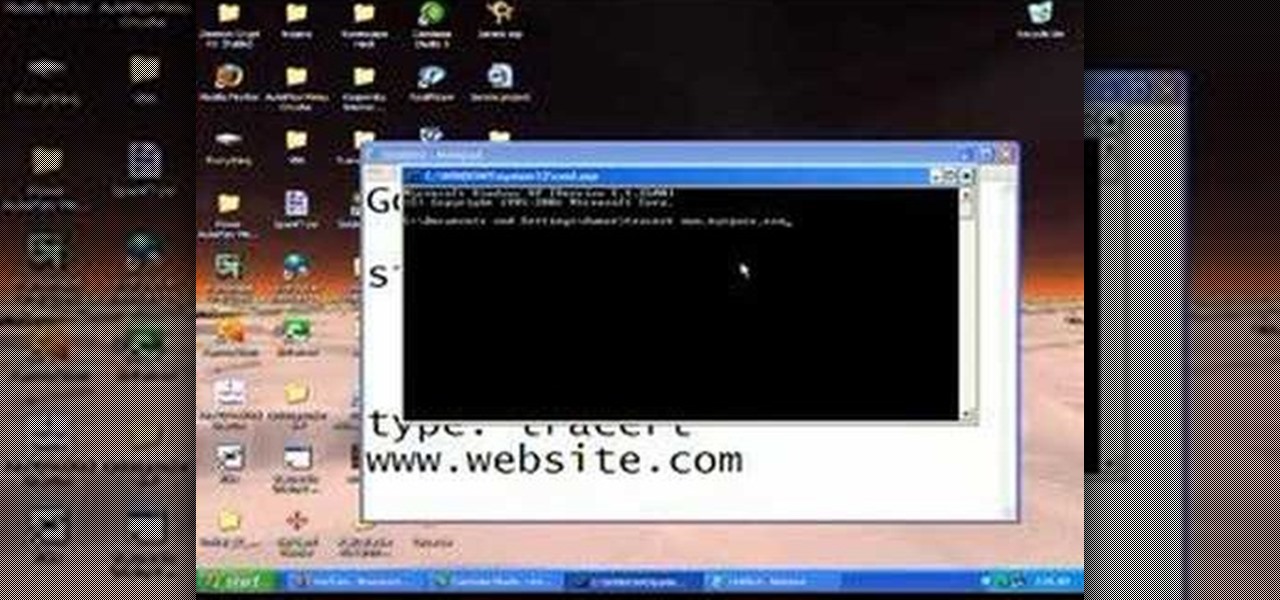
In this video, we learn how to hack school filters to get on Facebook with Tracert. First, go to the start menu and then type in "cmd" into where it says run. After this, type in "tracert" and then the website name. Wait for all of the information to fill in in the black screen. Then, copy and paste the IP address that appears inside. Now you can take this and use it to go to Facebook while you are at school. Or, you can go to any website that you'd like to that you normally can't go to at sc...

In this video, we learn how to hack your iPhone 3G. To do this, you will need: iPhone 3G, Firmware 3.0 or 3.1 file, charger cable, and the Redsn0w program. First, connect your phone to the computer and then start up the Redsn0w program on your computer. Turn the phone off, then restart it. The phone will now connect to the program on the phone and it will say "downloading jailbreak data". You will see a pineapple walking around on the screen. After this, restart your phone again and it will b...

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

In this clip, you'll learn how to hack a Flip UltraHD camera to use a wide-angle lens. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started creating your own custom wide-angle UltraHD cams, take a look.