Samsung's Galaxy S7 is an incredible piece of technology, but the Skype app that's preinstalled on some models may have some nasty issues, such as video and audio that freezes. Luckily, the fix for these problems is a simple one, although somewhat buried in the phone's Settings app.

Normally, you have to hold down the on-screen button to record videos on Snapchat, but if you want to go hands-free for some more creative video selfies or less shaky landscapes, there's a workaround on iPhones that lets you do just that.
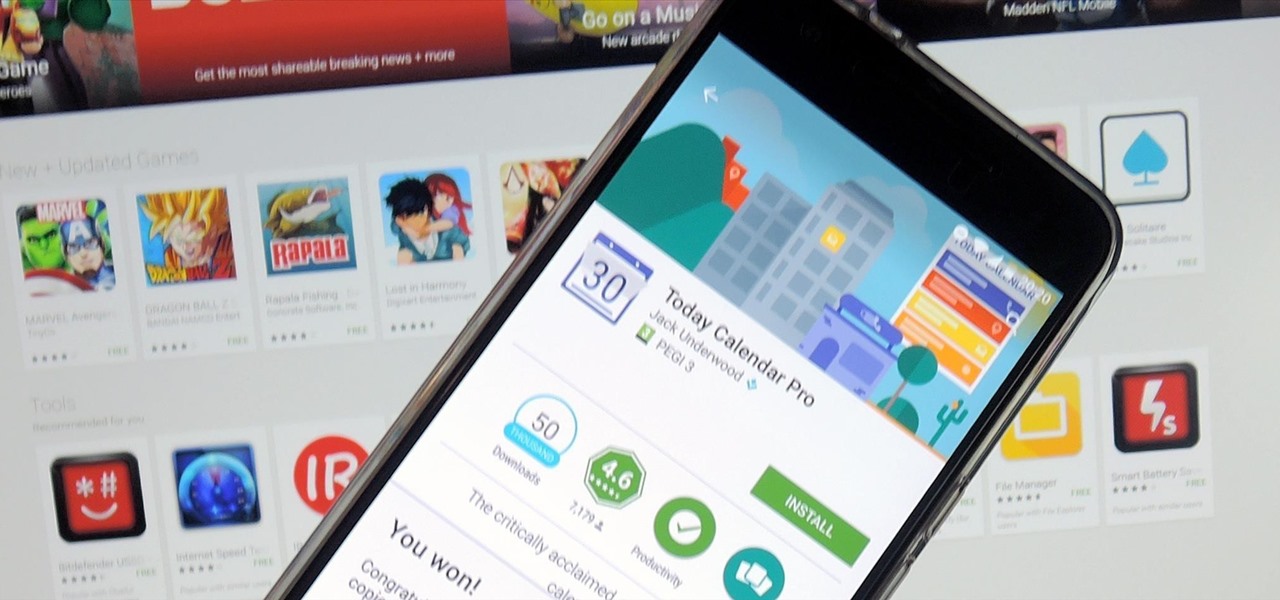
If you're a developer looking to get some exposure for your high-quality app, or if you're a user hunting for new apps and would like a chance to win a paid app at no cost, then Jack Underwood's new Promo Codes app may get you there, which you can install for free from the Google Play Store.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

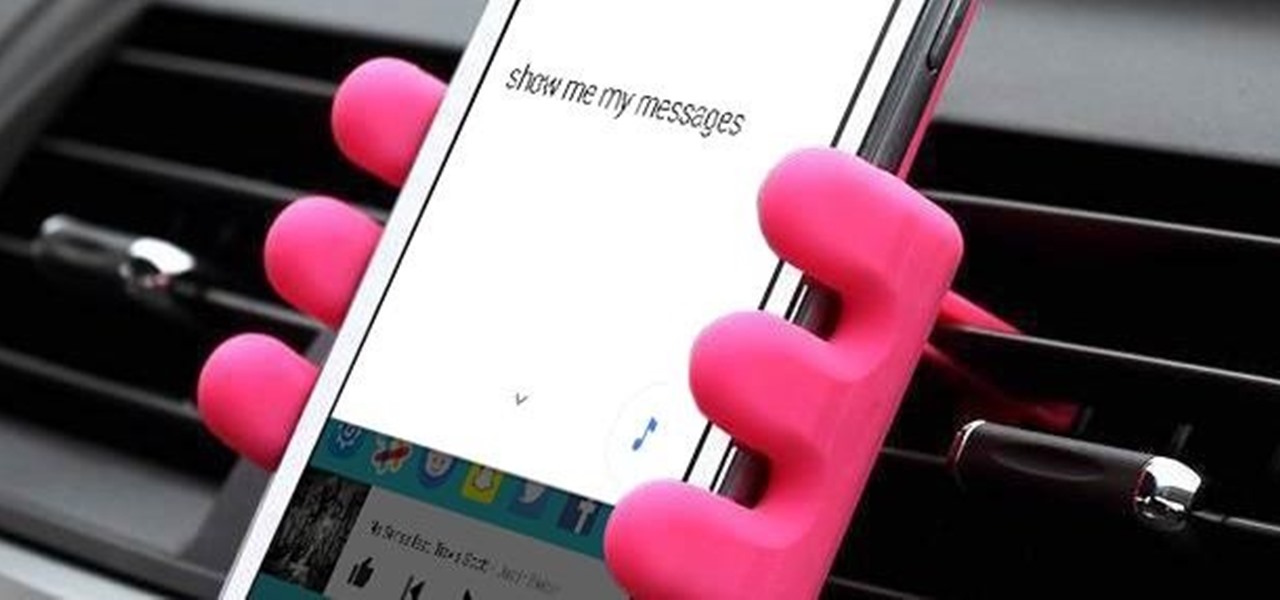
For some time now, iPhone owners have been able to use Siri to listen to and reply to text messages, but that functionality has been lacking on Android. That is, until Google silently rolled out a similar feature for Google Now (thanks to Android Police for the tip).

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

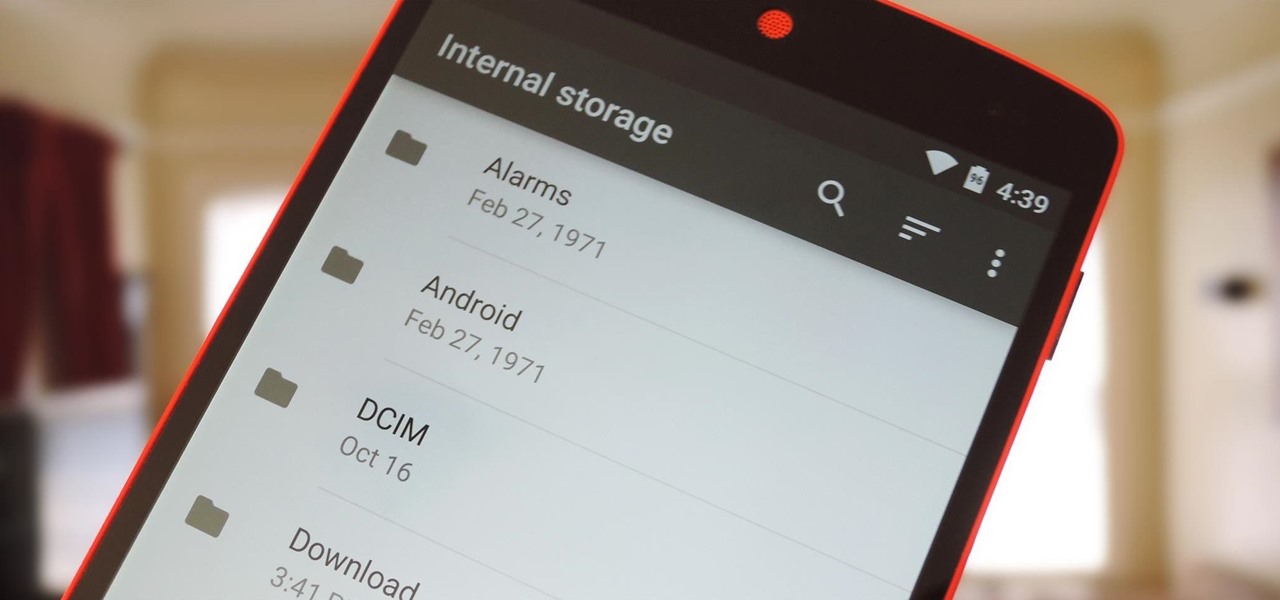
For years, we've had to download third-party apps if we wanted to browse or manage the files stored on our Android devices, but Google has finally included a bare-bones file explorer in Android 6.0 Marshmallow. Only thing is, it's not easy to find—but I'll show you how to access and use it below.

Not that long ago, Google introduced a beta program for their Google Search app on Android. Much like any beta program, testers will get access to new features before they officially debut, but you might have to put up with the occasional bug as new functionality is introduced. If you'd like to sign up, it's quite simple, but I'll go over the process in detail below.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Between sharp knives and slippery produce, basic meal prep can be an absolute massacre. Even the most professional knife-wielders don't stand a chance if they're working on unstable surfaces.

Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun and cheap prizes that no one needs—boy, do you want them.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

If you've noticed a tiny discolored spot on your computer screen that just doesn't seem to go away, chances are you have a stuck pixel. With modern LCD and OLED screens, there are millions of incredibly small dots (pixels) that make up all of the contents of your display—and within these pixels, there is a set of red, green and blue subpixels. These mix together at various levels to create all of the different colors you see.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Welcome back, my hacker novitiates!

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

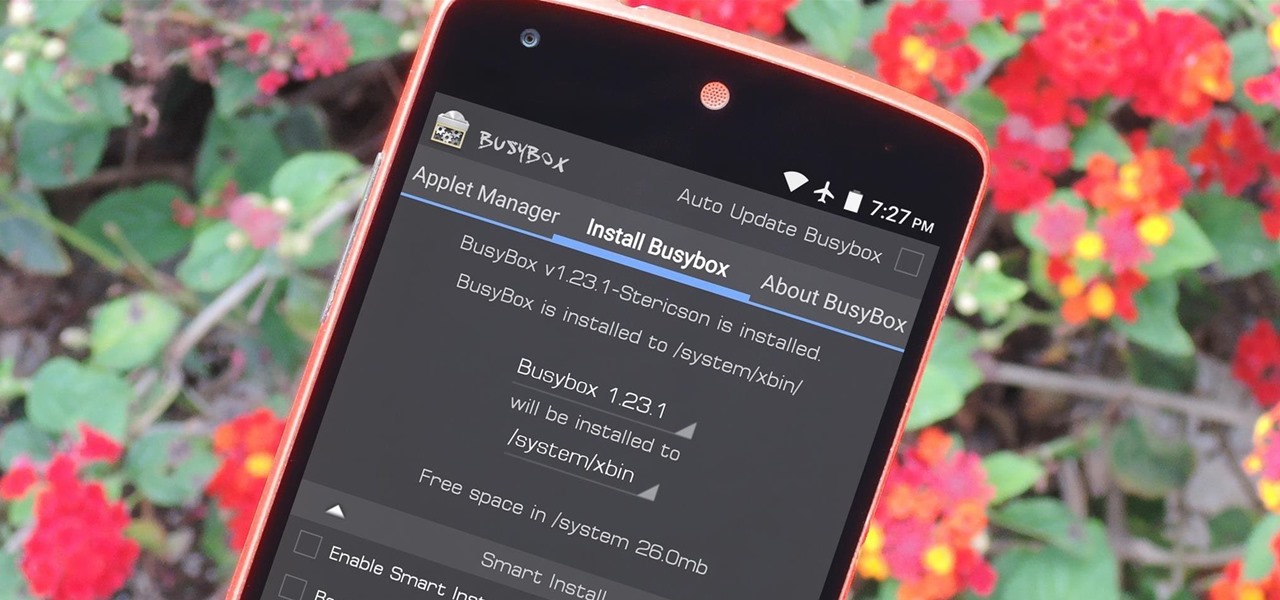
If you're a rooted user, you've probably heard the term "BusyBox" by now. Many mods require these powerful root commands, but the process of installing BusyBox can be a bit confusing for the uninitiated.

As with any software, Android apps can occasionally suffer from bugs. But finding the root cause of such issues can often be difficult, and reporting bugs is a cumbersome experience.

When you think about it, YouTube may actually have one of the largest music collections on the planet. This is why, at $10 per month, Google's new YouTube Music Key subscription is a solid value for many users, especially with its inclusion of Google Play Music.

Mobile service providers have an uncomfortably strong grip on the Android platform as a whole. For instance, all four U.S. versions of the Galaxy S6 and S6 Edge play their carrier's obnoxious jingle every time they boot up. You don't get any say in the matter—if you buy your phone from one of the big 4, you're a walking audible billboard.

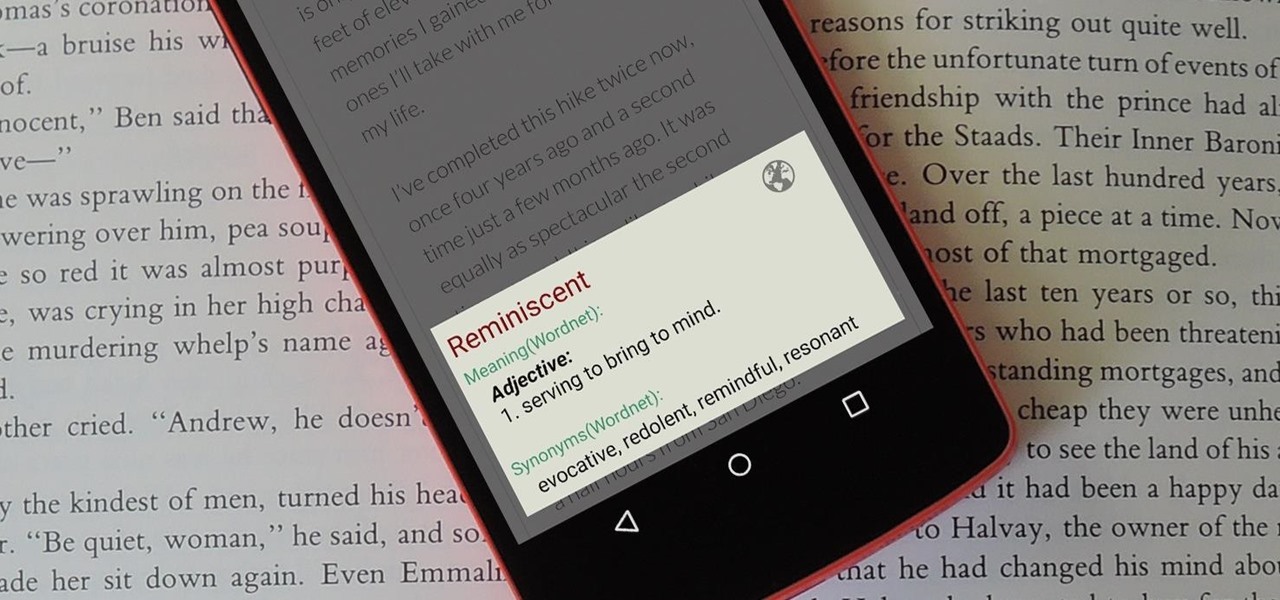
When you're browsing the web, going through emails, or reading a book or magazine, you'll occasionally come across a word or phrase that you haven't seen before. This would be a perfect time to have some sort of built-in dictionary lookup service, but most Android apps lack such a feature.

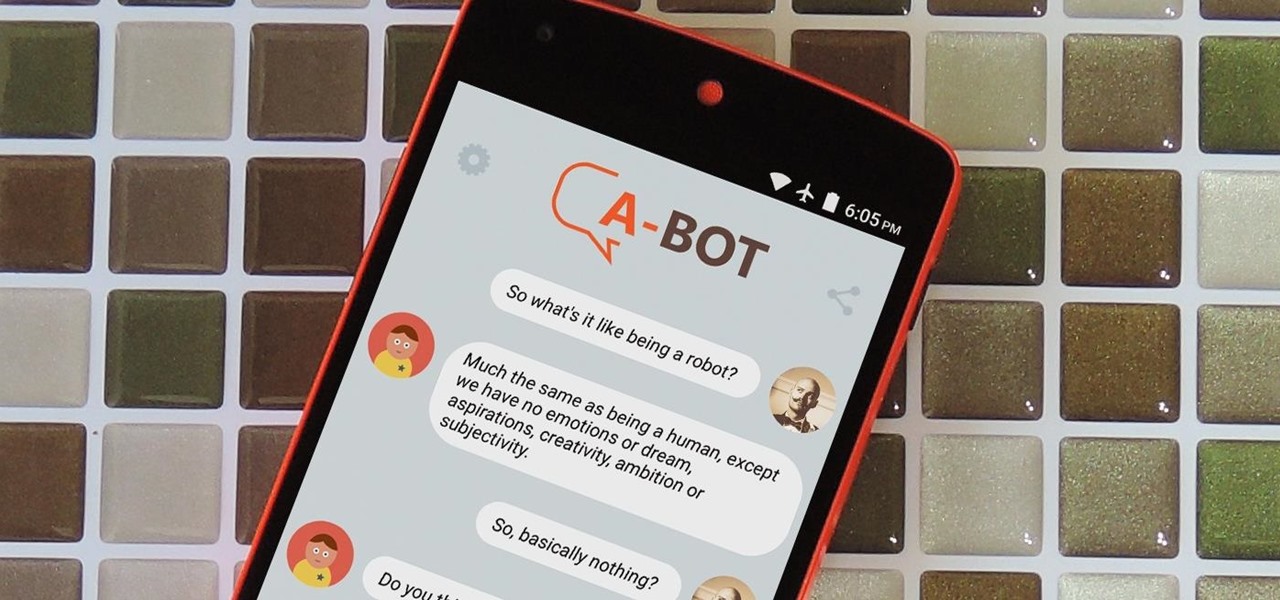
We all have those moments where we're bored or lonely, and in those times, just having anyone to talk to would be awesome. But maybe your friends are all busy, or everyone you know is at work and nobody's responding to your text messages.

Some variants of the Galaxy S6 will allow you to silence the camera shutter sound with an option in the app's settings menu. But this is not true of all models, plus there's an additional annoyance—when you're filming video and you get a notification, you'll actually hear this tone on the final recording.

One of Android's biggest strengths relative to iOS was the ability to switch to a third-party keyboard. While Apple has finally included this feature in its latest OS and leveled the playing field a bit, the variety of options still pales in comparison to what's available on Android.

Android has a permission that allows apps to draw on top of other apps, but as fun as that may sound, it has mostly been used to create floating multitasking utilities. While these can certainly be useful, it would still be nice if this permission were taken literally and we could actually draw on top of apps.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

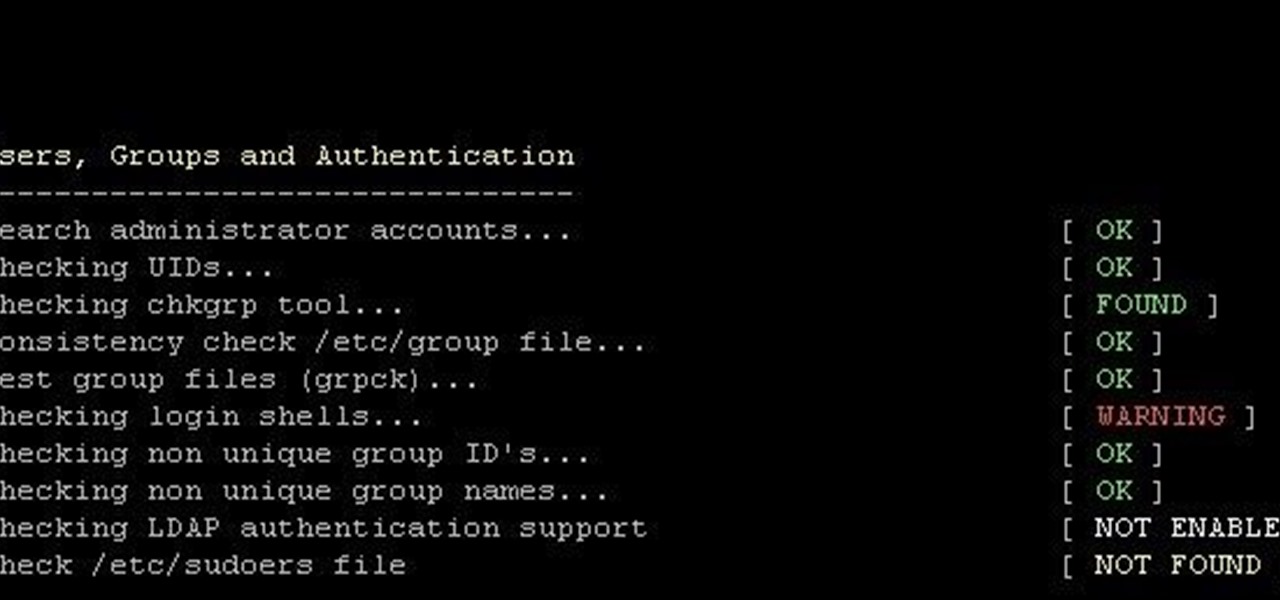
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

Pizza. It's seen you through your best and worst times. It was there during your first relationship and the subsequent dumping. It got you through college, and maybe even your twenties. Domino's phone number is programmed in your speed dial, and though you won't admit it out loud, you love pizza, you really do.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

We're always looking for great food hacks to help us become better cooks who can create delicious food with less waste, fuss, and hassle. You never know where the next good tip will come from, so we've all learned to keep our eyes and ears wide open.