Watch this instructional ceramics video to learn how to polish a piece of hand built clay sculpture before you fire it. Every piece of hand built clay sculpture should dry very slowly to avoid cracking. Use the back of a spoon to slowly polish out any imperfections on a smooth surface.

Did you forget your Windows XP password or do you just want to see what is on your parents account? This tutorial will teach you how to find out someone's Windows XP password.

Are you into Gaara? If so, why not make one of his gourds? Materials you will need:

Cover brows with wax or glue stick and concealer that is a lot lighter than your skin). Place some of the much lighter concealer under your eyes. Stroke concealer all over face for an extra layer. Apply full coverage foundation. Set makeup with powder. Use something that'll look very fake when done. Add cream blush product in bronze shade. Apply with finger to warm it up; apply to cheeks, forehead & nose. Use mineral type skin highlighter all over face. Paint on eyebrows with black liquid eye...

Feeling unprepared for the next earthquake? In this tutorial, learn what to do and what not to do to survive "the big one". You'll be surprised to learn that hiding in a doorway is a myth!

When it comes to used cars, it’s hard to make lemonade out of a lemon. So don’t get stuck with a piece of junk in the first place.

Your skateboard takes a lot of abuse. A quick check of your board before each ride will keep it in top condition so it doesn’t send you into a “slam.”

Step 1 Wash your canning jars, along with their lids and screw bands, in very hot, soapy water. Rinse well and let them air dry. Check for cracks and chips before using.

It's easy to make a peck of pickled peppers – or any other vegetable – with this basic recipe. You Will Need

Make the most of summer's bounty by learning how to preserve it for winter. You Will Need

Everybody knows it really shouldn’t matter, but sometimes entering a school cafeteria without a lunch mate can seem like walking the plank. Here’s how to survive the stroll.

Learn how to exercise your dog. Follow a regular exercise routine together with your pet. It will benefit you both!

Learn how to spot a dishonest contractor for home repair. It’s no accident contractors have such a bad reputation – they get more fraud complaints than any other workers! Here’s how to find a reputable one – and skip the scammers.

Find out the benefits of hot cereal grains and how to make oatmeal, cracked wheat, brown rice, and other rolled grains; explore hot cereals and healthy alternatives to oatmeal in this free video on whole grain cereal tips.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

For many of you, the carving fork only comes out at Thanksgiving as an essential turkey-slicing aid. Perhaps you pull it out of the knife block to slice up the occasional roast. But the carving fork (also known as kitchen fork) can be used for many more tasks around the kitchen, and some of the more unusual involve your favorite shellfish.

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Every morning, my origami alarm clock wakes me up at the crack of dawn. What's that? You don't have an origami alarm clock? Well this video demonstration will show you how you can fold your own origami rooster, and soon enough you'll be waking at the crack of dawn, too.

Rattling doesn't just sound bad, but can create stress cracks in the body of plastic on an RC car. Use foam cutouts around the body posts to stop the body from rattling around. Watch this video tutorial and learn how to prevent the body of an RC car from rattling by softening with scrap foam.

Eating any type of shellfish can be messy especially if you don't know the right way to remove the meat. This how-to video demonstrates how to pick the meat from a cooked crab. Remove the legs, grab a small knife and start cracking open the sell to uncover the delicious crab meat.

The stress cracks in your driveway could cause serious damage to your car. This how to video shows you some ways that you can fix a damaged driveway. This is a great DIY home improvement project.

This amazing modeling material is light and easy to work with. It hardens without cracking and will stay fresh if kept inside of its container. It will also stick well to almost any surface (cardboard, plastic, wire, wood) without glue. A great project to do with your kids!

Pop a raw egg like a balloon without cracking the shell. All you need to do is soak the egg in vinegar.

You must ONLY conduct this experiment if you are experienced in using combustibles and understand the risk. Fire is very dangerous and can seriously burn you. Seems harmless at first, but believe me, these are bubbles turned evil. When ignited, the bubbles pop almost instantly, and all the propane is released in a huge fireball.

There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking about. You're addicted to finding out what's going on with your friends and addicted to telling those friends everything you're doing. You can't stop, even when you're at work.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

After leveraging the well-known intellectual property of Rovio's Angry Birds for its first game for the Magic Leap One, Resolution Games is singing a new song with a familiar refrain for its next game for the augmented reality headset.

After recently renewed enthusiasm for the arrival of Apple's long-awaited AR wearables -- the subject of multiple reports and rumors over the past few years -- some of that excitement may now be dampened a bit.

When the titular hero of your superhero movie activates his powers with a catchphrase, it would be pretty neat if your augmented reality promotion for that film could react to the user's voice.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

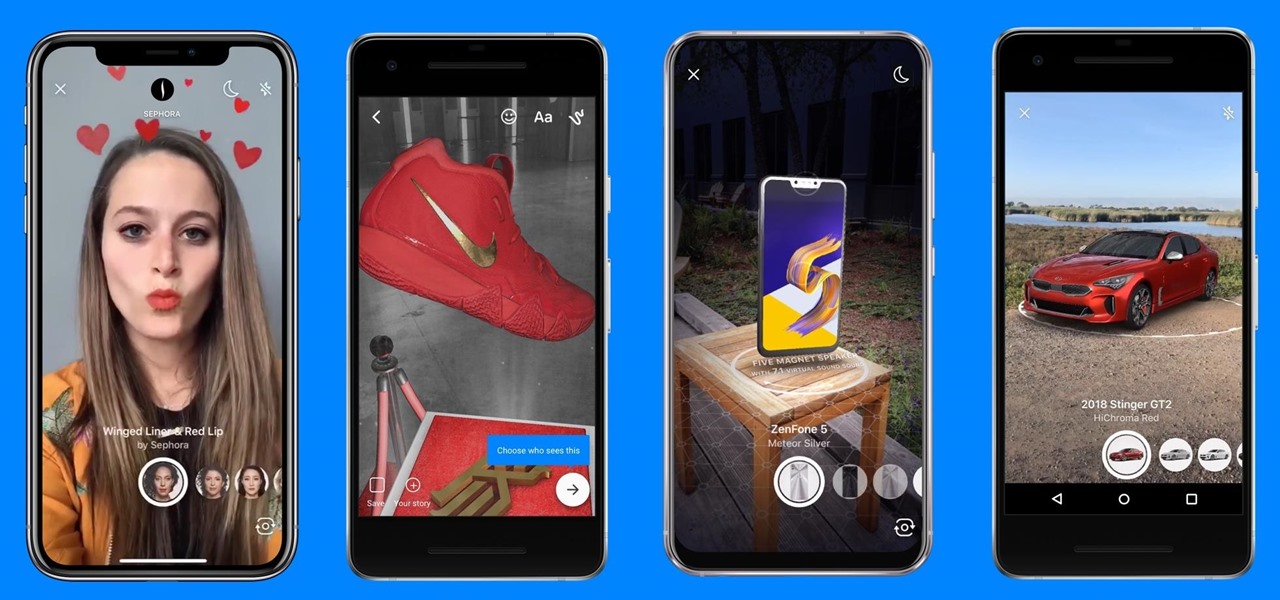
On Tuesday, on the one-year anniversary of the announcement of its AR Camera platform, Facebook founder and CEO Mark Zuckerburg revealed at the company's F8 developers conference that the platform will be extended to the company's Instagram and Messenger apps.