A relatively new feature in Snapchat, having been first introduced in February 2018, is GIF support. These new animated stickers, straight from a partnership with Giphy, came to the app about a month after Instagram received GIF capabilities. If you've used Instagram's version, adding GIFs to snaps is even more intuitive. While they were late to the game, they're doing it better.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

Just yesterday, Google announced that it is banning all apps that contain any form of lock screen ads. Today, they posted a list of the Best Apps of 2017 for the Play Store. Given the new policy of cracking down on apps with advertisements on the lock screen, you wouldn't expect to see one of those in the list of top apps. Unfortunately, that's exactly what happened — Google is promoting obvious adware in their list of best apps.

If you're like me, you probably have a wishlist of Android games you'd love to buy, except the high price tags keep you away. A few bucks can feel like a fortune in the Google Play Store — you just can't bring yourself to pay that much. Well, lucky for you, Google Play has some serious discounts this Cyber Monday. There won't be a better time to buy these games, until next year, of course.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

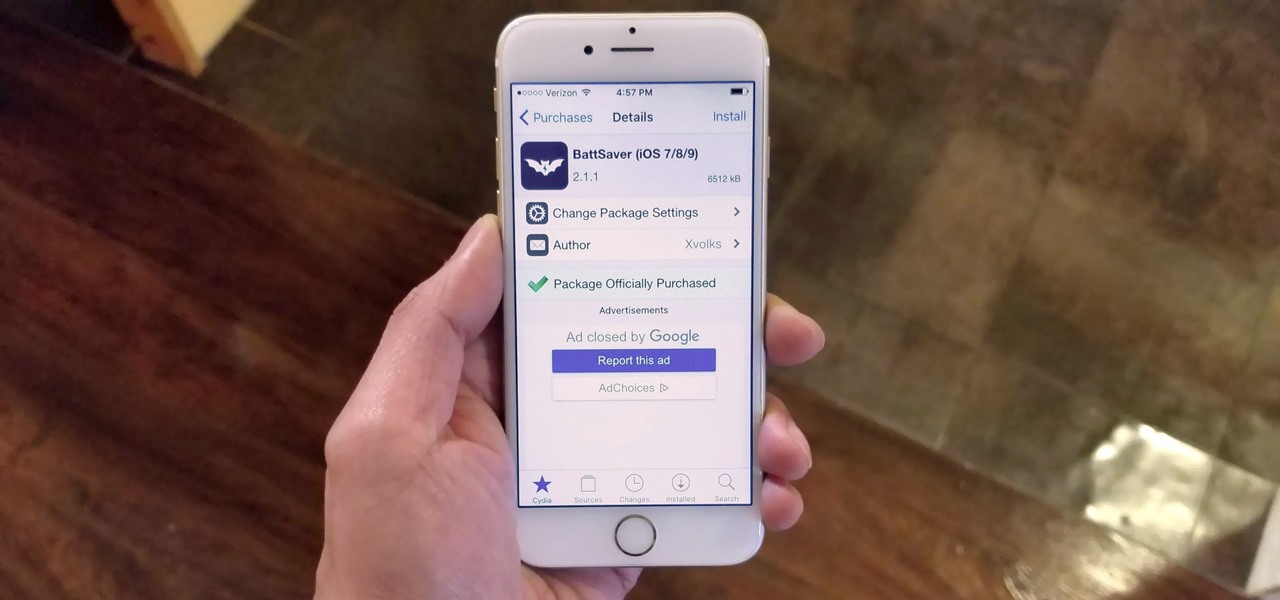
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

Niantic pioneered location-based augmented reality gaming with Ingress and popularized it with Pokémon Go, but others have attempted to replicate the model without reaching the level of success that Niantic has garnered.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

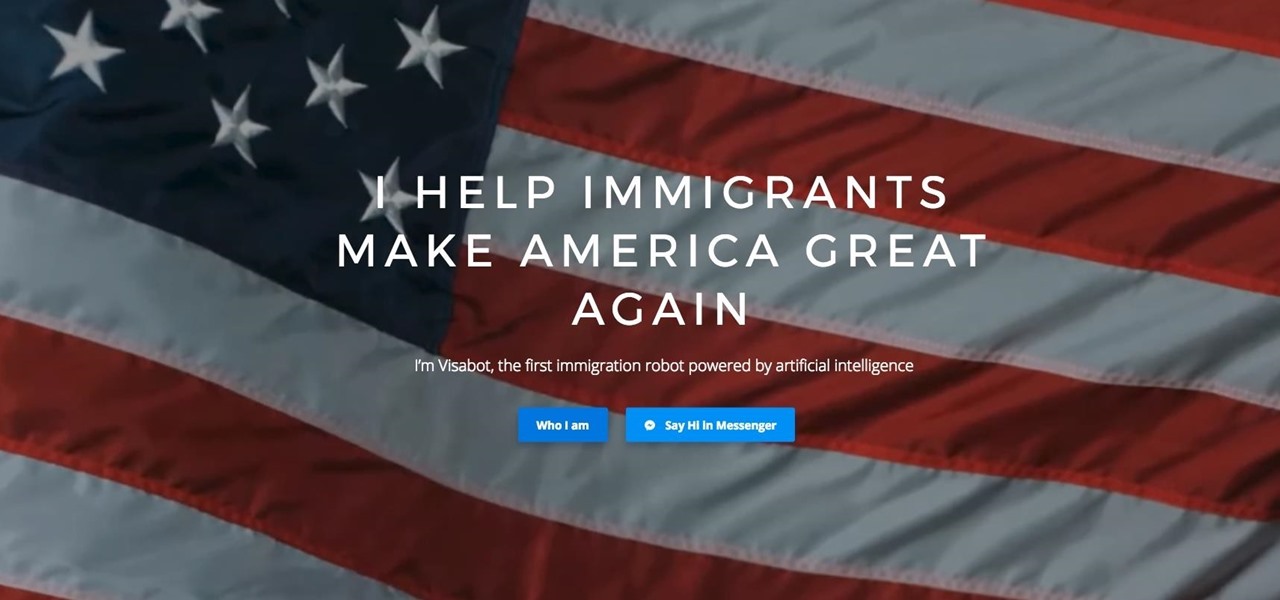
Getting your green card can be an extraordinarily complicated and difficult task. Often times it seems so daunting that it's hard to know where to begin. Thankfully, Facebook Messenger introduced "Visabot" last year, a chatbot in the app that helps with all things immigration. Now including applying for your green card.

As a part of the already crowded field of diseases transmitted by ticks, you may not know the disease babesiosis, a dangerous infection caused by a parasite that infiltrates blood cells.

Savor this moment: we've got a confirmed number of sales for the Google smartphone. We say this because unlike most hardware manufacturers, Google refuses to share official sales numbers for their phone. Instead, during earning reports they simply bundle the product under Alphabet's "Other Revenues", leaving us in the dark about how successful the product is.

Replacing your iPhone fingerprint sensor has been one of Apple's most cruel tortures. It's a slow and painful process made worse last year when Error 53 messages started appearing on the phones of users who had tried to repair their sensors outside of Apple. The error rendered the phones essentially useless. Since then, Apple has provided fixes but is now finally making it much easier to replace your iPhone fingerprint sensor with the releasing of "Horizon Machines" to official repair locations.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

Earlier last week, there were a number of fake five-star WhatsApp reviews to be found on the Google Play Store. Now, Gmail, Chrome, Messenger, and Firefox are all the latest victims to be saturated in five-star spam that wrongly refers to the word "game" in reference to non-game apps.

During the last few months, WhatsApp's Google Play Store ratings have been tanking—all the way down to an average of 3.4 stars from the instant messenger's usual average of 4.1. Within the last week, though, WhatsApp has received thousands of seemingly fake 5-star reviews that have bumped up the company's overall average to a 4.4.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

When we tell folks how often we use apple cider vinegar, they are baffled and bewildered. "I've had a bottle sitting in my pantry for 10 years," is the response we encounter most. And "I never use it!" Some have never even used apple cider vinegar at all in their lifetime, believe it or not.

We like our Egg McMuffins around here, albeit homemade with our preferred ingredients: whole wheat (or homemade sourdough) English muffins, a slice of thick Tillamook cheddar cheese, a meat, perhaps, like Canadian bacon, and finally—that perfectly-fried, perfectly-shaped egg.

The VLC media player just celebrated its 15th birthday in February 2016, marking a decade and a half of hassle-free video playback for hundreds of millions of users on virtually every major operating system. The free and open-source player is so powerful and easy to use that it has almost completely vanquished all would-be competitors in its rise to the top.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Cheesecake is pretty awesome. It's super versatile, allowing you to change crust bases and toppings quite dramatically and still end up with something that's elegant and delicious. Which is why it's a great dish to add to your dessert repertoire! There are a number of approaches to making a cheesecake base: classic, new york style and no-bake. Today we're going to go down the more classic route.

The buttery scent of crescent rolls bring me back to my childhood, but those tubes that open with such a satisfying pop are more than just retro reminders. Crescent rolls can morph and serve as the base for hundreds of creative and cool dishes.

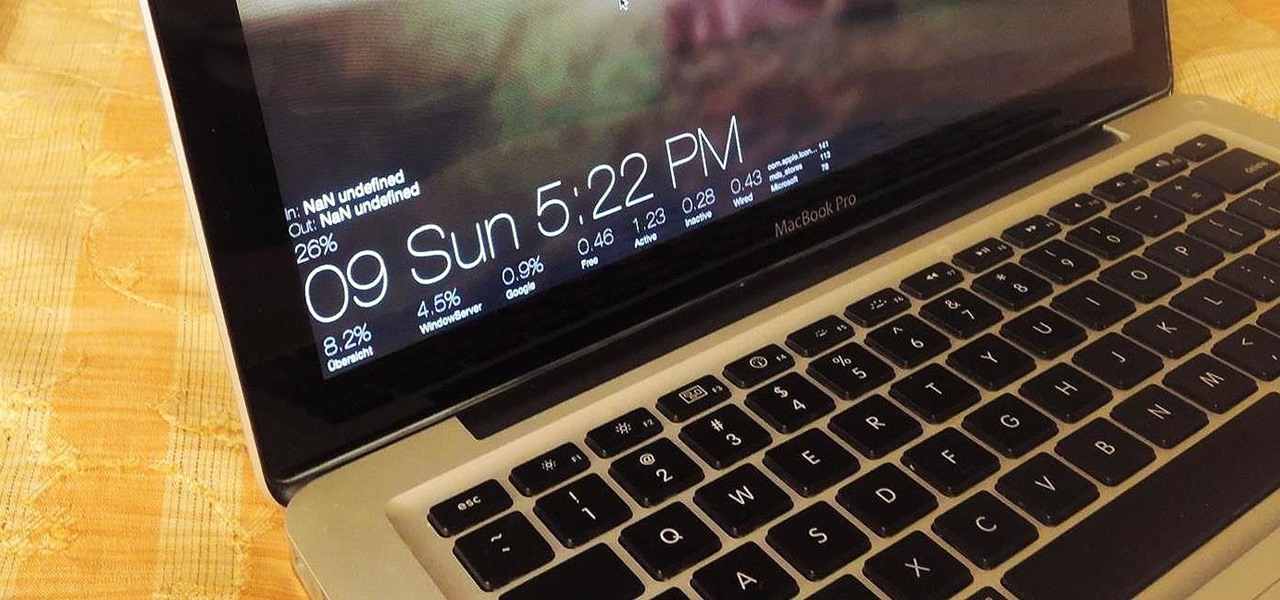
Apple hasn't been the most avid supporter of widgets over the years. Yes, they added them to the Notification Center in Yosemite, but that requires a drawer to be opened and closed whenever you want to check them. In my search for a better solution, I came across Ubersicht by developer Felix Hageloh.

As messaging and texting have all but replaced the need to actually call someone, emojis have seemingly replaced our need to type out text. With a simple emoji, you can relay emotions like "I don't feel very well" or "I love you" quickly and easily, knowing that the other party will instantly know what you're feeling.

If you purchased your Nexus 5 from Google Play in the United States, we've got great news for you. In an unprecedented move, Google has started offering customers the chance to exchange their broken or water-damaged Nexus 5 for a new or refurbished unit—free of charge.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Even though I often end the workday exhausted and just want to wrap rotisserie chicken parts in a store-bought tortilla and shove it in my eating hole, I generally try and take a couple of minutes to warm up said tortillas before I begin my meal. But if you're starving, do you really need to take the time? Do warm tortillas really make that much of a difference?

Normal wear and tear, combined with unfortunate accidents, can take a toll on any smartphone leading to scratches, cracks, and breaks that can leave physical buttons useless. One of the first buttons to usually go is the power button, since it's the main way to turn your phone (and screen) off and on.

Are you tired of your snoopy coworkers and friends lingering over your shoulder as you type in your security passcode? Unless you have the newer iPhone 5S with Touch ID that scans your fingerprint, you've only got a couple of security options—either a 4-digit numeric passcode or a cumbersome password.