Meringues are a French and Swiss dessert made of whipped egg whites and sugar, and they are light, sweet, and crispy confections. To make traditional meringues, you beat egg whites into soft foamy peaks, and then keep whipping as you gradually add sugar until the peaks become stiff. Once you've reached the right consistency, you bake them at a low temperature in the oven for a long time. They take both technique and time.

As touchscreen phones continue to evolve, the need for physical buttons seems less and less pronounced. While hard keys may seem like an endangered component on mobile devices, save for the Samsung Galaxy line, it'd be difficult to fathom a world where volume keys are absent.

I grew up eating Korean, Japanese, and Chinese food, but it wasn't until college that I experienced Thai and Vietnamese cooking. Once I started, I couldn't get enough of these cuisines. The dishes had an incredible richness and savor that I couldn't identify, but whatever it was, it made me want to keep eating.

If you have satisfying memories of slurping up the sweet milk left in the bowl after eating your cereal, then this cereal-infused milk will make you feel like a kid again. Although people have technically been enjoying cereal milk since the invention of cereal, it was recently made popular as a standalone drink by the playful and quirky Momofuku Milk Bar in New York City. Created by pastry chef Christina Tosi, it's a "recipe" that is both simple and brilliant. The original Momofuku brand cere...

Admit it: when nothing's at stake other than your boss's disapproval, you don't exactly feel the urge to get working. Finding the motivation to take on a task, whether at work or home, can be a constant struggle. Though working through your laziness might seem like the best course of action, a meaner method can make more of an impact on your productivity.

The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try to squeeze every last bit of speed and performance out of it.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

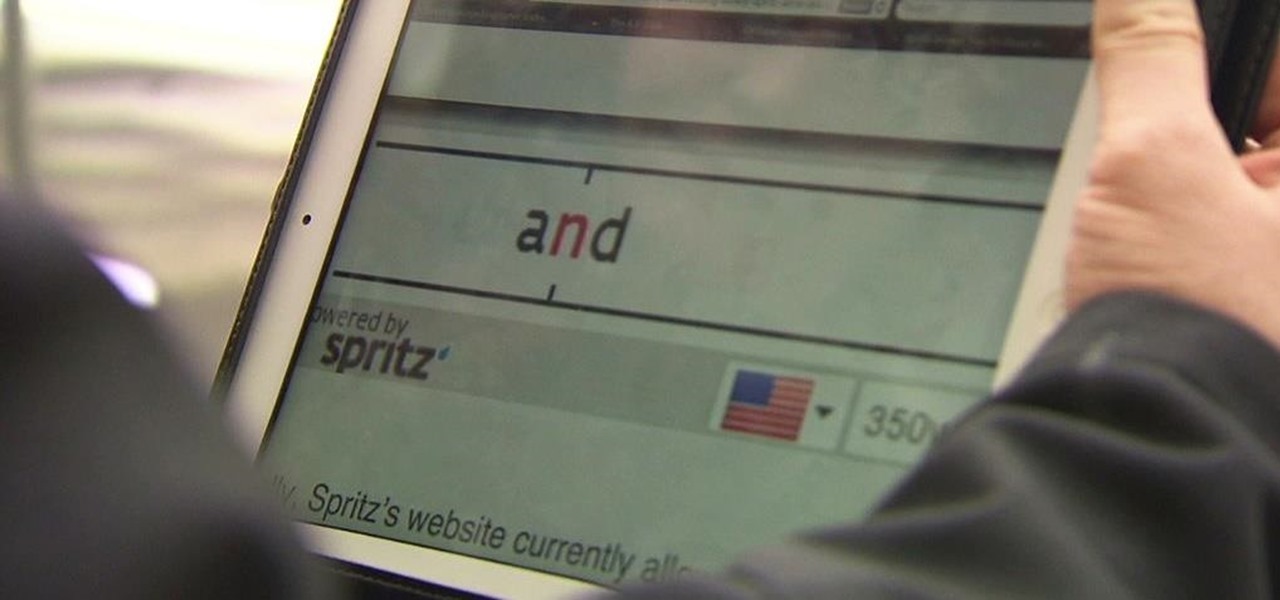
Reading is no longer a leisure activity—it's an on-the-go activity that requires speed and less attention. That's why speed reading apps are growing in popularity. As smartphones and tablets increasingly take over the traditional book market, reading skills need to be adjusted accordingly, so you can cram in 5 pages in-between texts and emails.

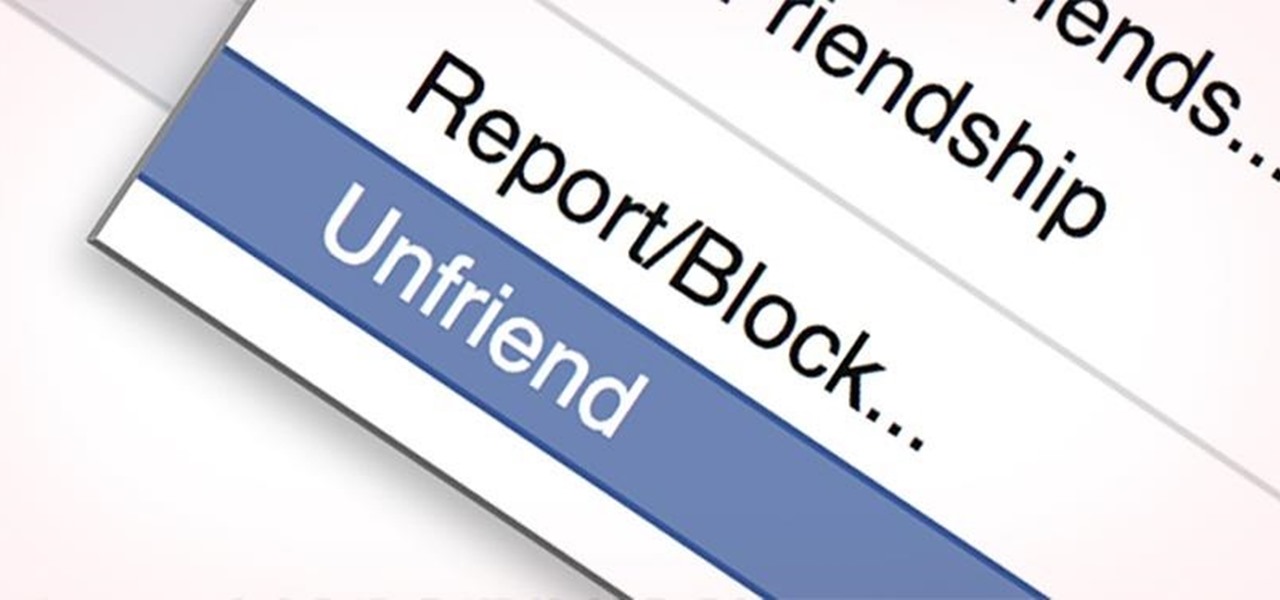
Admit it: you haven't talked to more than 70 percent of your Facebook friends in the last year. Whether you barely know the names crowding your friends list, or have vague memories of high school Spanish class with them, Facebook friends are easy to find and difficult to get rid of.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

Imagine you're holding a cookout with family and friends. You're having a good time—the grass is green, the sun is shining, and the smell of the burgers sizzling on the grill is irresistible. There's creamy potato salad, mountains of golden brown chips, and a hefty watermelon chilling on the table, but you forgot something—the drinks!

The guitar is a double-edged sword. I've played all my life, and though I love the act of guitar playing, there are quite a few people I could live with never hearing play again—ever.

Mechanical locks have been around since ancient Egypt, with the oldest known artifact found in the ruins of Nineveh, an ancient city in Assyria, Mesopotamia, which is just across the Tigris River from what is now Mosul, Iraq.

If your LCD screen in your Sony PSP is acting up, maybe it's time you had it replaced. Don't waste money taking it to a repair shop though, learn how to do it yourself.

Thanks to the PlayStation 3 and Xbox 360, video games are constantly evolving to higher degrees of sophistication, with complex graphics, lifelike resemblances and storylines that create exciting experiences that relieve the tediousness of our everyday lives.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Dawn your flannel and grow out your beard, it’s time to do some log cutting. Put good use to unwanted trees or extra lumber by making proper logs. It may seem self explanatory but the correct form will create uniform, crack free logs and keep you with all your fingers.

They say cheaters never prosper, but how will your know for sure if you don't give it a try? By a little repositioning of the blindfold and some spacial awareness you can be the master at this classic party game.

In this series of baking videos, you'll learn an easy recipe for making peanut brittle. Chef Brandon Sarkis shows you step-by-step what ingredients and bake ware you'll need to make the candy, how to heat and combine the ingredients, and cook, cool, and crack the perfect peanut brittle.

The Holy Grail of chicken has just been found by an unsuspecting reporter of the Chicago Tribune. Yes, that's right: The secret 11 herbs and spices in Colonel Sanders' Original Recipe chicken has finally been revealed, and it looks legit as hell.

This lobster claw isn't the same one you'd be cracking during dinner. This lobster claw is a clasp for jewelry making. Great for necklaces or bracelets. If you've perfected the meticulous and dexterous art of jewelry making, than this should be simple. This demonstration video will help walk you through the process of attaching a lobster claw clasp to your work of art.

Jerky is not only delicious but it is a great way to bring a protein rich energy snack with you anywhere. This video will how you how to make a great beef jerky at home. You will want a think slice of meat and you can create your own fantastic flavoring.

If you’re doing some spring cleaning and decide to throw in a little home improvement in as well you may want to remove old caulk. As we all know, old caulk is unattractive and will make areas look dirty or unfinished.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

Gboard is often considered the best keyboard for iPhone or Android. Google made sure to jam-pack it full of features, and you should expect nothing but the best when it comes to Google's own first-party software. But with so many capabilities, a few things might slip through the cracks.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.