Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions used to operate and control the peripherals such as the keyboard, text display functions and so forth, and these software library functions are callable by external software such as the OS and system software within sai...

Most of the car owners pay attention to the maintenance of the vehicle but among them, many forget to include windscreen maintenance in their periodic checkups. Car windscreen maintenance is quite simple and can be done on your own. In order to maintain car,the drivers should treat this with utmost care as they do for tyres because neglecting small issues in windscreen can land you in deep trouble and on safety prospects as well,it is unsafe.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

There's still about eight months before the final chapter in the Mass Effect series comes out, but some trigger happy fans are already building replica costumes and prop weapons to celebrate the upcoming release. BioWare themselves recently commissioned some of these projects, which were shown at their booth at Comic-Con 2011 a couple weeks ago in San Diego. One of these projects was the armor that turian Garrus Vakarian sports in Mass Effect 3, by Kommissar Props. But even more impressive wa...

Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was hacked by LulzSec, with 1 million passwords taken and 40,000 made publicly available. Comparing the two data sets, Troy Hunt found 88 accounts on both sites that used the same email address, and of those accounts, 67% use...

Mold making is pretty thrilling—the ability to replicate objects right down to every little crack and crevice seems like something only a machine would be able to do. But in many cases creating a replica from a mold is surprisingly simple. Found on Tasteologie, La Receta de la Felicidad presents a fun alternative to the classic Jello jiggler. For a Dada-esque dessert, try using a banana peel as your mold. As you can see below, it works quite well at capturing the natural texture of the banana.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

After stumbling across an interesting article by Hanne Blank—(apparent) hobbyist chef and widely known activist on the issues of weight, bisexuality, and sexuality—I've become even more fascinated by kitchen shortcuts. Former Microsoft CTO Nathan Myhrvold's recently released Modernist Cuisine also spurred a similar interest, particularly after reading a WSJ piece in which Myhrvold attests —by law of science, of course— that a ¼-inch-thick sheet of steel is more than adequate in place of an ex...
Beware the Canning Mission! The Zynga Community Forum is full of complaints about the new Canning Mission. Here is an outline:

Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

By "God," I mean Morley Davidson, John Dethridge, Herbert Kociemba, Tomas Rokicki and about 35 CPU-years.

If you don't have the time or money for a trip to the spa for a pedicure, follow these steps for a quick at home fix. Prep

This is the cheapest device to gather interviews as a small, easy-to-carry recorder. I started to use it for preproduction and film documentation after I bought it in a Polish discount shop for about 100 Euro. The only problem was very poor sound quality.

Many things cause a bike tire to deflate. Glass, sharp rocks, tacks, and nails can pierce the tire and puncture the tube within. A tube can be pinched between the rim and tire causing the tube to split when inflated. If a tire has a hole in it, the tube, which is filled with air pressure, will bulge out of the opening and pop. As well, the valve holding the air pressure in the tube can be damaged or faulty.

Jet engines combine oxygen from the surrounding air with on-board fuel to burn at very high temperatures and create thrust in the direction of the flame. Rockets, which we will learn about in a later post, are similar but carry oxygen internally and can therefore function in space!

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

In this Null Byte, we are going to be installing Packet Injection capable drivers in Linux. These are the open-source drivers required to sniff wireless traffic, inject packets to crack a wireless access point, and go into "monitor-mode". These drivers are superior because they are the fastest available drivers.

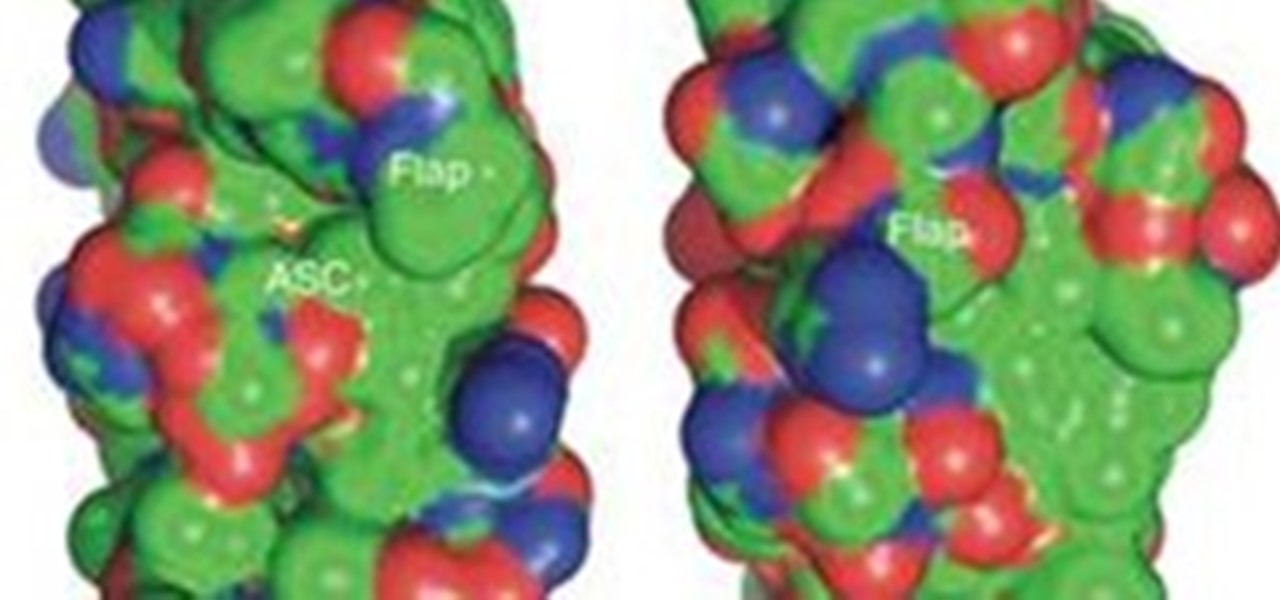
Foldit is definitely a niche game. The sole gameplay mechanic is attempting to fold complex proteins into smaller and more efficient shapes following the rules of molecular physics and biology. Points are awarded based on how small one can make the protein. Online leaderboards track players' relative progress and allows them to view and manipulate other players' completed designs. It's original, certainly, but no developer is going to ship a million units of a game about molecular-level prote...

Gone are the days when you had to carry a clunky DynaTAC to make phone calls, pocket phone book for you contact list, Sony Discman for your tunes, and wallet for you cash and credit cards. Today, all you need is your smartphone. To be specific, Google's Nexus S 4G on Sprint.

Bourbon is the ultimate American spirit, considering the barrel-aged distilled spirit was originally produced in an area known as Bourbon County, Kentucky. To meet the legal definition of bourbon, it must be produced in the United States, must be created with at least 51% corn, and aged in new oak barrels. There are two types of bourbon whiskeys—straight and blended. Straight bourbon means that the bourbon has been aged for a minimum of 2 years, and has no other coloring or flavoring added. B...

This is a refreshing and light crab salad with a savory basil lemon sherbet on top. I know it sounds weird, but it's perfect for summer and helps you cool off from the heat.

You're walking down the street, minding your own business. Then you see it—a large, bright fireball in the near distance. A tremendous heat wave speeds towards you at one thousand miles an hour, and before you can think, before you can even blink, the extremely heated wind pushes right through you. Your skin melts, your eyes liquefy—your face disappears into the wind. Before you know it, your pancreas collide with what’s left of the person next to you, your duodenum is dissolving faster than ...

People smile in this movie. This is a genius breakthrough Another day, another remake. Another safe choice during apparently rocky times - this wintry economic climate, don't you know - and we're off and watching Joe Carnahan's big-screen version of the A-Team. In 2010.

If your PS3 is YLOD (flashing the Yellow/Red/Green Light Of Death), try sticking it in the oven. Why does this work? Instructables user formulajake88 explains what causes YLOD and why the oven re-flow method will (likely) work:

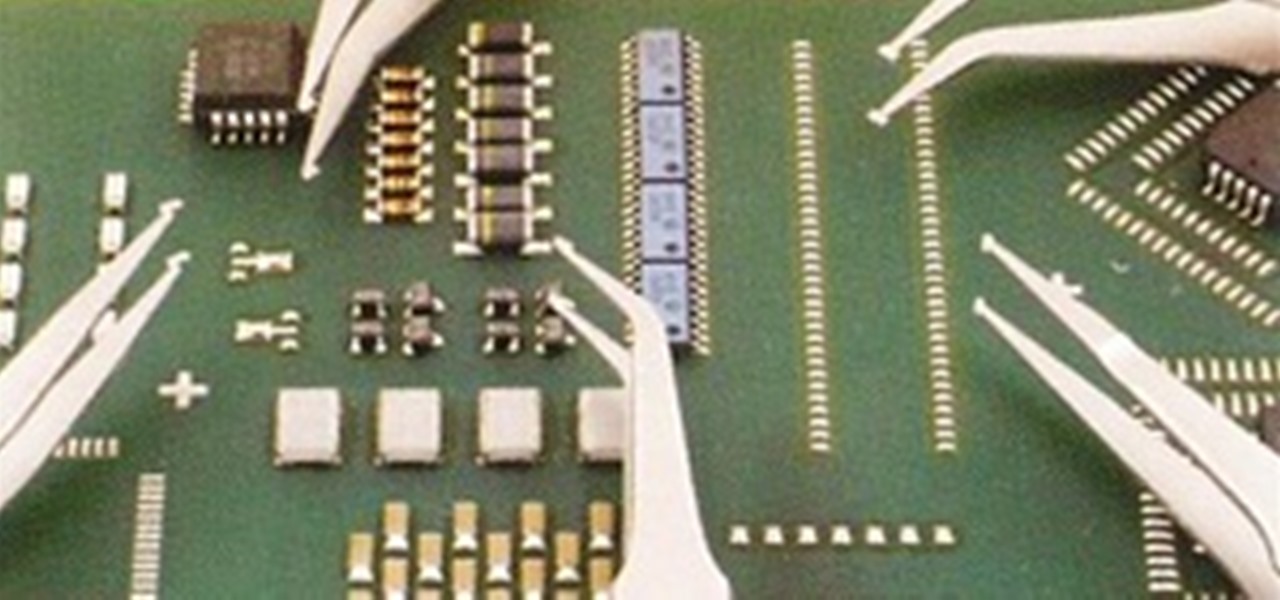
Whenever we make a homemade circuit, we use what are called through-hole components. Any components with long metal leads is a through-hole component. They are great for soldering to, but it's tough to fit enough through-hole resistors and capacitors into a smartphone. To get those last microns, we have surface-mount components for SMDs (surface-mount devices). These are all of those teeny, tiny things you see when you crack open your digital camera or laptop case.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

It's really a shame that it is so hard for people to make money on the internet these days. The dot com bubble has receded and scams are plentiful on the web. There are, however, a couple of legitimate ways to make a few extra bucks online, Amazon Mechanical Turk, or MTurk for short, is one of them. The idea of MTurk is to hook up programmers with people that do tasks that computers can not, these tasks are called HITs (Human Intelligence Task). These tasks include article creation, creative ...

The days of trundling hoops, hopscotch and painted wooden rocking horses are long since past. The latest trend in toys? Biofeedback. Electroencephalography. A decade into the 21st century, the toy market is awash in products that incorporate functional neural sensors.

We’ve all been there before. Relentlessly refreshing Ticketmaster and filling in those CAPTCHA codes only to receive the miserable “No tickets are available at this time” message. That’s because ticket brokers with a dozen screens and God knows how many browsers snatch up anything and everything.

This how-to is aimed at the uncynical, bright-eyed outsider who wants to become a television producer…the talented person who believes he or she has the ‘it’ to crack Hollywood. The ‘Sammy’ who just arrived in 90210.

Holiday dinners can be the same every year, but many are starting to switch it up, making new traditions and getting a new dining experience for everyone at the table. It’s not unusual to see sweet potatoes on an Easter dinner menu or lamb at Thanksgiving dinner.

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

The stunt is not simple. FOLLOWING THIS IS A NO AIRPLANE VERSION, and you do not need to get your freinds drunk in the no airplane version you need to get them into the fake house and using the fake bathroom. etc.

With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighbors up. These "farmers" are the ones seeking quick hacks and cheats.

If you've ever had teeth removed/minor surgery, you most likely received some laughing gas, or nitrous oxide. This gas creates a happy, lightened feeling, and causes instant laughter. In this article, I'll show you how to make some. BUT BE CAREFUL!!! DO NOT proceed in this experiment unless you have EXTENSIVE knowledge of chemistry!!! Misuse of this procedure could result in the production of LETHAL GASSES! However, the set-up is quite simple, if done correctly should not lead to any issues. ...

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.