Investors aren't keen to throw money at a new technology sector without at least some hope of a significant return on their investment in the future. That's why a recent run of activity within the augmented reality business space has stoked some new optimism among the financial community.
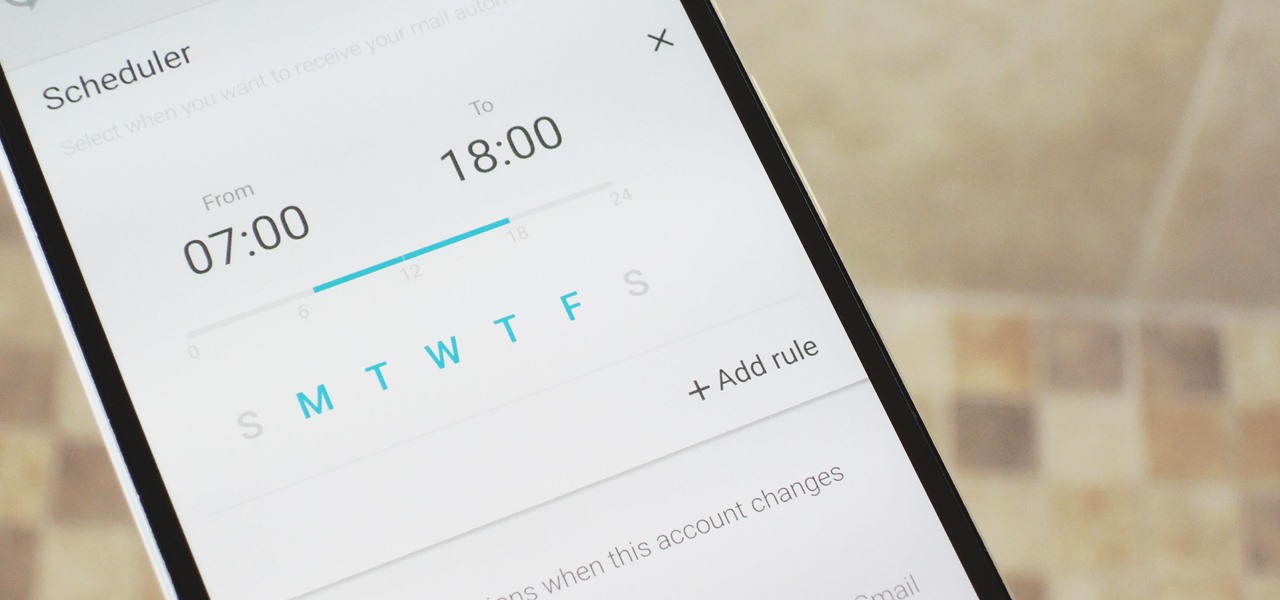
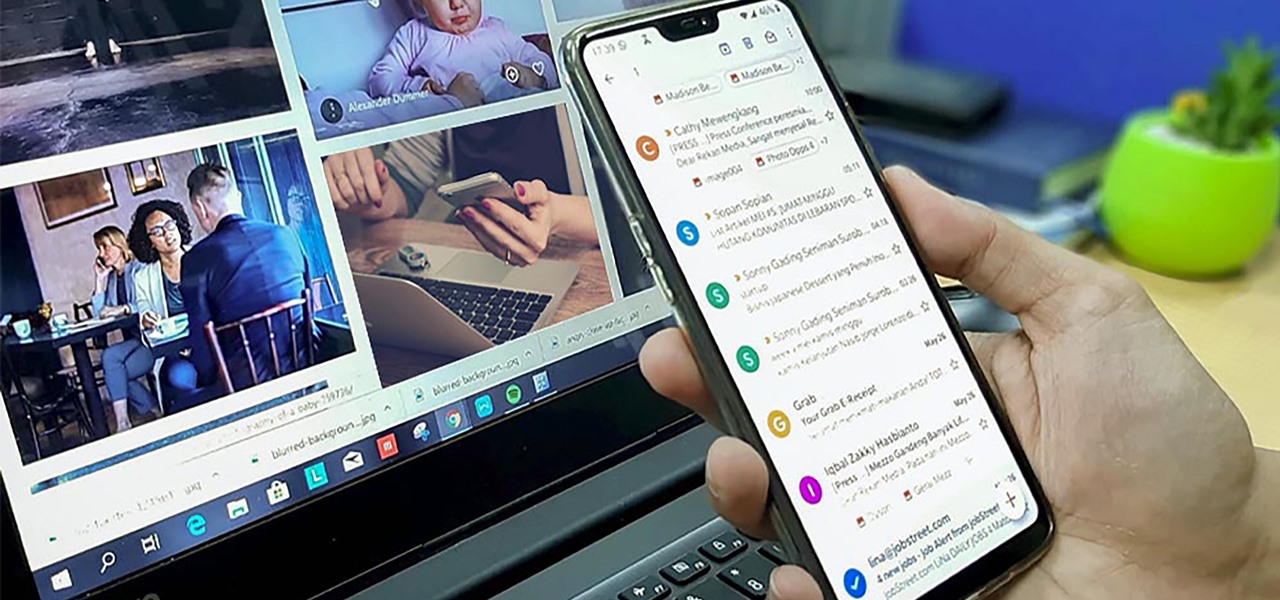
These days, when you're setting up an Android device for the first time, you'll be prompted to add extra email accounts directly to the Gmail app. It's really simple, too—just sign in with your work or exchange account, then emails from those accounts will be mixed in with your personal account in the Gmail app's "All Inboxes" view.

Collecting Pokémon in Pokémon GO is only half the fun. Once you've reached Level 5, it's time to get your Pokémon ready to do battle with other Pokémon. This is where Gyms come in.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

There are lots of great reasons for going out to a fantastic coffee shop for a cuppa. Coffee shops have a lovely ambiance, are a perfect place to meet with friends or do some work, and are a great excuse to get out of the house. Seeking out a perfect cup of coffee, however, shouldn't be one of the reasons that you hit up your local café.
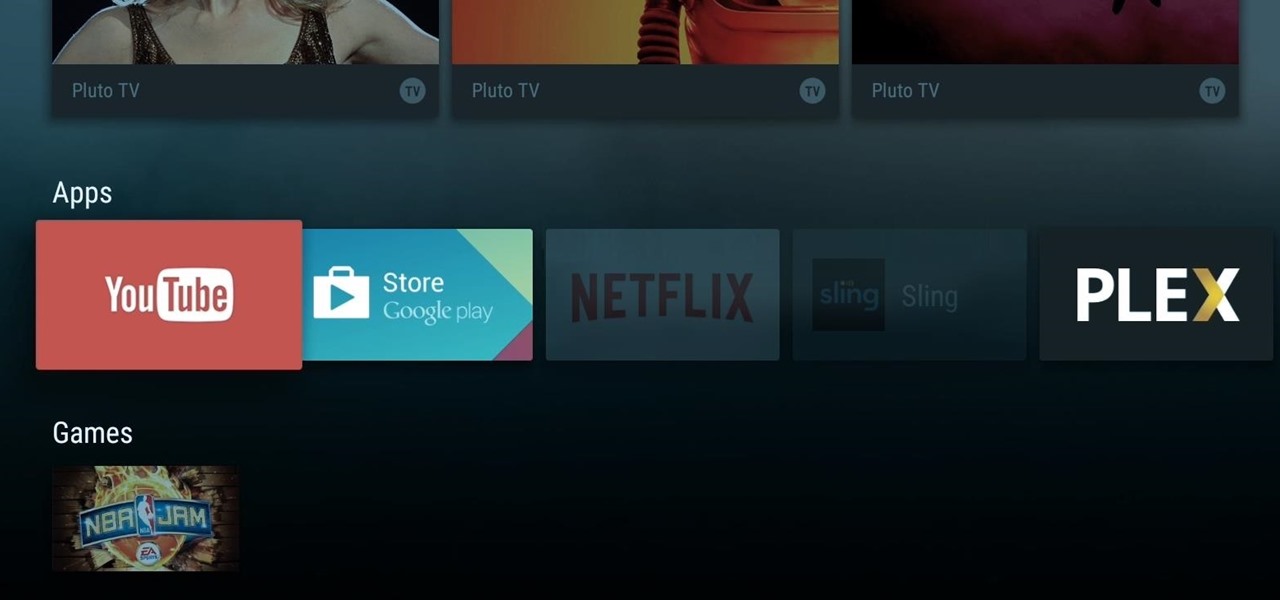
When Google announced its new Android TV platform, one of the features they advertised was a home screen that automatically reorganized your apps based on how frequently you used them. Unfortunately, this feature either didn't make the cut, or is still under development, since the home screen on the Nexus Player always remains static.

Cold pizza is the holy grail of leftovers. That's a statement that elicits a slew of impassioned feelings. Either you love the idea of biting into soft crust and cold, fatty cheese, or scowl at the idea of pizza that isn't hot, crisp, and melty. Yet if we were to stand by the former sentiment, how would we argue on its behalf? Food Science Explains Why Cold Pizza Rules

I have a theory that chocolate chip cookies are the gateway drug to cooking. The recipe is easy, no special equipment is required, and at the end, you get warm, fresh-from-the-oven cookies that are simply irresistible. It's how I got hooked on baking and cooking, and anecdotal evidence (i.e. me asking my other kitchen-obsessed friends and a few culinary students) supports me.

If you're like me, you've already spent a ton of money on your costumes, your badge, and your hotel room, and now you're looking for ways to cut costs. There are all kinds of ways to save money at DragonCon, but many of them involve violating the rules in some way, such as not buying a badge, sleeping on the floor in a hallway somewhere, etc. However, the one thing you can do that is totally not against the rules is eat for free. It requires a little self-discipline and a willingness to eat w...

Mystery, AKA VH1's "Pick Up Artist", teaches you three basic rules about meeting women in public. He explains the 3 second, 3 mintue, and 7 hour rule of meeting women. Understand the 3 second, 3 minute, 7 hour dating rule.

Learning the basics of SEO In this tutorial I will go over the basics of Search Engine Optimisation. The "white-hat-way" ("black-hat" SEO is tricking Google and other search engine providers, this will get you into trouble quick!).

The noble board game has stalwartly staved off elimination in the face of more technologically advanced video games for four decades. Try as they might, video games just can't seem to surpass them as an easy-to-use diversion for large groups of seated indoor people.

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...

Google started culling Google+ accounts. There are two main targets: businesses and those who are using pseudonyms. For businesses, Google is promising to provide their own version of Facebook Pages, which will be released later this year. For those who use pseudonyms, they aren't so lucky. According to Google+'s community standards, users must "use the name your friends, family, or co-workers usually call you". The purpose of this rule is ostensibly to discourage spammers and people from set...

In a recent episode of The Big Bang Theory, character Sheldon Cooper designed a highly complicated three-person game of chess, with an odd-shaped nonagon board and two new pieces—serpent and old woman. Seemingly pioneering, in truth, three-player chess has been around since the early-1700s, with many different variations, most of which retain the basic game structure and sixteen pieces that each player controls.
Type: Digital, Landscapes Theme: Incredible Landscapes, "Beyond the Mundane"
Type: Digital, avian Theme: Bird portraits, "The Avian Persona", wild or in captivity
Running this World has prompted me to think about MTG on a deeper level than I ever have before. In attempts to contextualize it, explain it, research it, and understand the parts of it that I don't yet understand, I have come to an unexpected conclusion: I'm old.

So says the Original Scraper Bike Team, founded by Tyrone Stevenson (aka Baybe Champ, the Scraper Bike King).

There's more to playing guitar than just holding it and strumming it. There's a correct way to do things. You need proper posture and you need to hold the guitar correctly, whether you're left-handed or right-handed. Also, you need to hold your guitar pick the right way. This will teach you that. Extremely helpful for any beginner guitar player.

Pilates is fantastic exercise. If you are a beginner, though, it can be confusing to choose the right type of class. Check out this tutorial before you head to the studio and ensure you get the most out of your exercise routine.

20 Questions is a great game to play when you have some time to kill. Check out this video and learn the basic rules of the game. 20 Questions is perfect whether you are in the car, a waiting room or anywhere else and feeling a bit bored.

The game of pig involves a bit of gambling and strategy, and is easy for any person to pick up. Learn how to play with this video.

American citizens should know the rules and etiquette of carrying, hanging and displaying the American flag. Get tips on properly handling the American flag in this free culture and society video series.

Learn how to play solitaire with expert tips and advice on shuffling, rules, game play and strategy in this free video series about card games.

Learn how to play strait whist with expert tips and advice on playing cards, rules, strategy, and bidding in this free video series.

Learn how to play bid whist with expert tips and advice on playing cards, shuffling, rules and strategy in this free video series.

Learn how to play barbu with expert tips and advice on game play, strategy, shuffling and rules in this free video series on card games.

Want a new pool game? Learn how to play nine ball in this free video series about the rules, special shots, and more!

Learn how to play the game of lacrosse including the essential equipment used, basic rules and penalties explained, beginner moves and techniques and more in these free instructional sports videos.

Whenever you design elements for your garden, you should always keep in mind, that the more natural they are the better they seem to fit in. That's exactly what is done when you create this rustic bent wood trellis. But others have taken this idea a step further. In this how to video, Jim Long, author of the book Making Bentwood Arbors and Trellises, explains how to create these artistic garden ornaments.

This tutorial for Devil May Cry 3 covers the basics of jump canceling and the overall advantages it will provide the player once mastered. The whole concept of a Jump Cancel (JC/JCing for short) is the cancellation of an aerial technique with a jump.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

Since its launch in 2009, Google Apps Script has given creative thinkers the ability to perform light-weight application development within GSuite. Based on JavaScript, you can build your own simple tools that will increase your efficiency and productivity.

The Pixel's "Flip to Shhh" feature may not be groundbreaking, but it is useful. Third-party apps are copying it for other phones because it's so convenient. But it's not enabled by default and it's fairly hidden in the settings. So to take full advantage of your Pixel's feature set, you should learn how to use Flip to Shhh.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.