This video presents a system for automatically producing a wide variety of video enhancements and visual effects. Unlike traditional visual effects software (e.g., After Effects, Shake, Boujou, etc), the system is completely automatic and no manual labor is required from the user. The major limitation of the work is that it can currently handle only videos of static scenes (i.e., videos shot with a moving camera but containing no moving objects in the scene). Efforts are being made to lift th...

Balisong knives, or butterfly knives, are folding pocket knifes with two handles that can counter rotate. People love performing tricks with them because of the balisong butterfly knife's flipping ability. Since knives aren't toys, make your balisong butterfly knife out of Legos. You still might hurt yourself, but not as badly as with the real thing. Learn how to build a Lego balisong butterfly knife by watching this video tutorial.

In this gardening tutorial, Martin Fish from Garden News demonstrates how to prick out Foxglove seedlings. "Pricking out" is when seedlings are transplanted into larger pots or trays to give them more room to grow on. The ideal time to do this is when the seedlings are at the two-leaf stage and before the true leaves have developed, or as soon as they are large enough to handle.

This video pottery tutorial shows how to throw a tea bowl, or handle-less mug, on a pottery wheel. Demonstrating potter Simon Leach shows the step by step process of this free form potted project. Watch this instructional video and learn how to throw a tea bowl.

Dave and Rolf Briggs talk about ways to handle the winter moth problem.

Every day we pass bridges, whether it's a foot bridge, a highway overpass, a span over water, or a viaduct over a valley. We pass on these structures without even thinking of the engineering genius that went into their design and construction, let alone the science behind their strength.

In this tutorial, we learn how to disassemble a BMX bike. First, remove the bolts around the handles. Set the handlebars aside, then remove the bottom tired from the front out of its place. Next, set your bearing aside with the bolts. After this, remove the wheel from the part holding it in with a wrench. Next, take out the chain from the bike and remove the back wheel. Remove the rest of the bolts and the spacers from the back of the bike. When finished, you will have all the parts laid out ...

Watch to learn how to remove and repair a Neff oven door. You'll remove and replace parts on an oven door, as well as how to remove the oven door. This oven maintenance video demonstrates removal and replacement of the oven door outer glass, oven door inner glass, door hinges and door handle. Use a professional oven cleaner and ceramic scraper to remove burnt on stains from the oven inner door glass.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

If you grow your own bedding plants one of the main jobs over the next few weeks is 'pricking out'. This is when seedlings are transplanted into larger pots or trays to give them more room to grow on. The ideal time to do this is when the seedlings are at the two-leaf stage and before the true leaves have developed, or as soon as they are large enough to handle. When done at this stage of growth there is less shock and root disturbance to the seedlings and they will establish and grow on much...

During the video tutorial, you'll learn how to simply solve the easy and fun fifteen number puzzle. You'll learn a couple different moves to help you solve the 15 puzzle, which are called the curl and the box and twist. The curl is easy, but the box and twist is a little more complicated.

Grab your long-handled wooden spoon and let's get to bed making. There is a science in making the immaculate and consistent military-style bed. Use this method at home and know that your making your bed just like soldiers do every day.

Even with the convenience of online storage like iCloud and Google Drive, data management can be a constant struggle on your iPhone. If you continuously find yourself having to delete messages, photos, videos, and other files to make room for other things, know that there's an easy way to free up space without erasing anything important or having to dig through documents and data yourself.

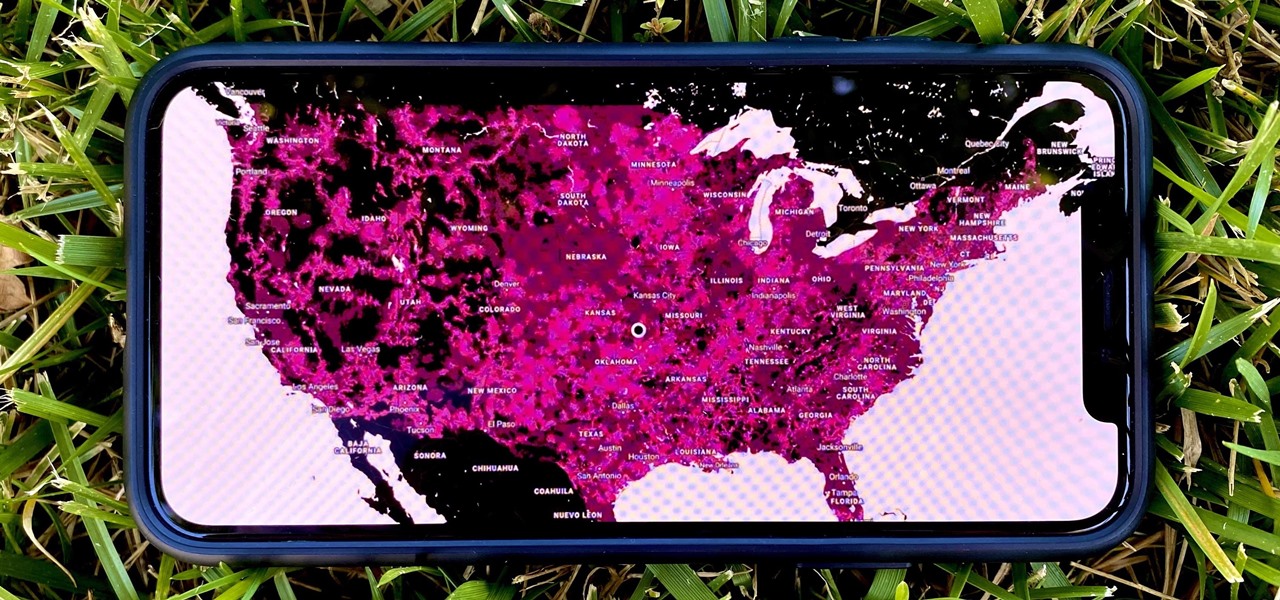
In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology among us, 5G, but can you even use it?

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

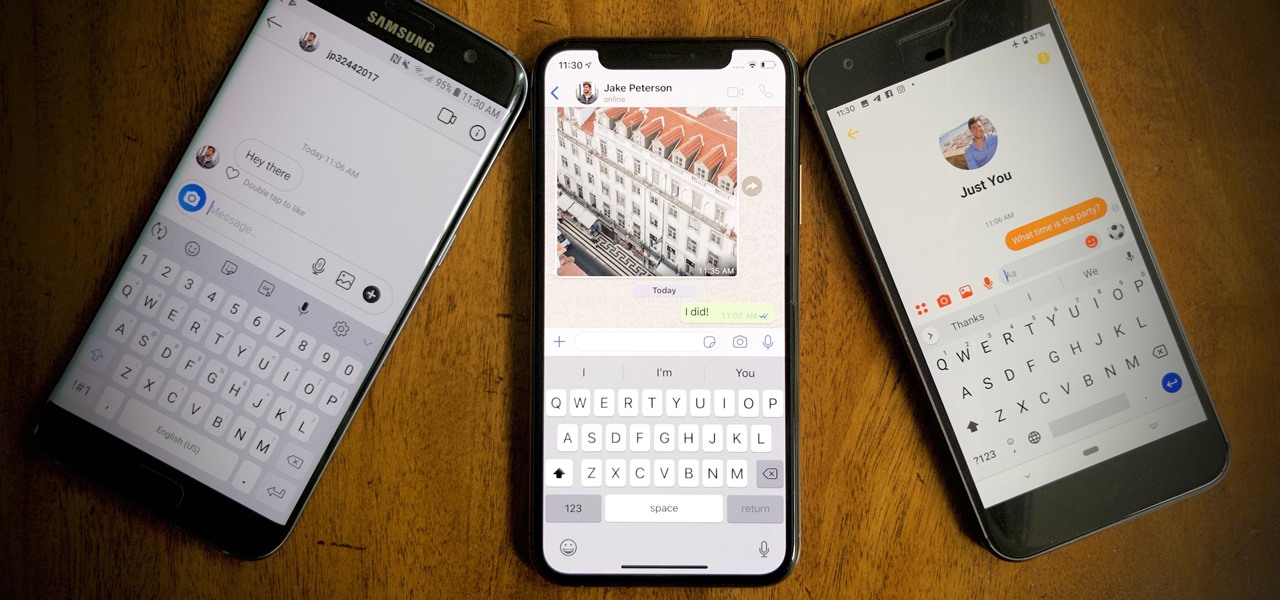
You're in constant communication with your friends and family. The only issue? Nobody uses the same app. Messenger, Instagram, WhatsApp — you have contacts spanning all three, and the resulting balancing-act to keep in touch can be overwhelming. That's why Facebook — who owns all three apps — is coming out with a way to call and message friends across all three platforms from one place.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

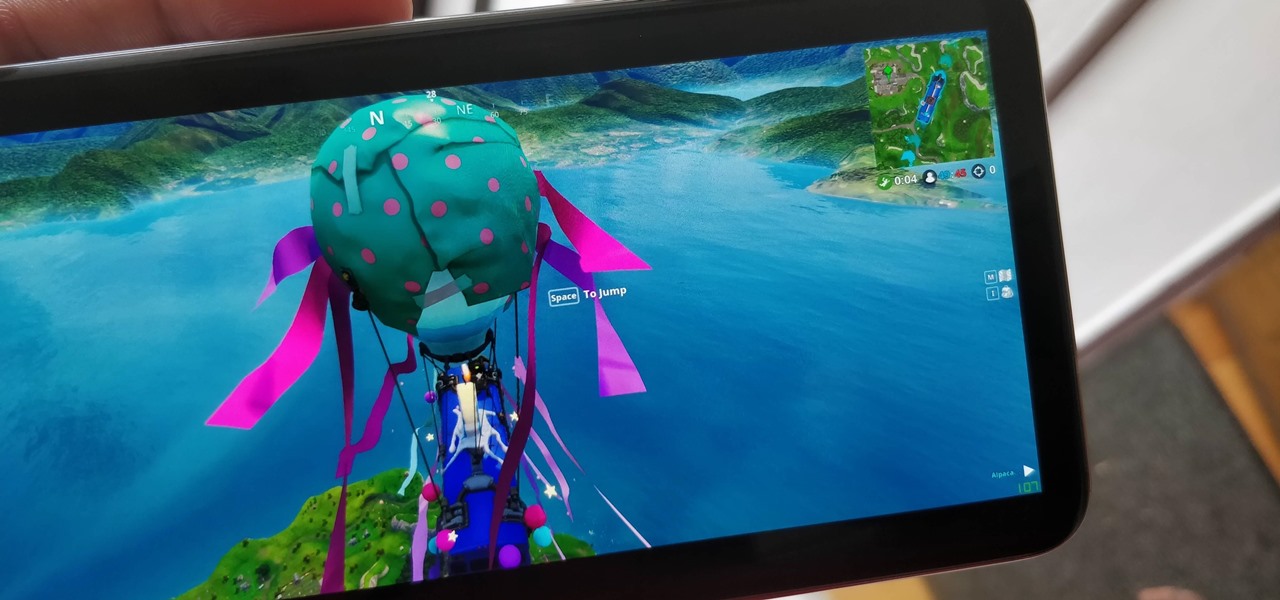
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Unless you own an Exynos model, there won't be much development on the custom ROM front for the Galaxy S9. But that doesn't mean you have to put up with all of the UI quirks from Samsung Experience (née TouchWiz). With a little work, you can give your S9 a stock Android makeover, even without root.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

"I'm Rey." That's what a lot of people will be saying again this Halloween, as Rey costumes are sure to be another favorite of trick-or-treaters and cosplayers. Yes, on Oct. 31 we all have a chance to be the scavenger of Jakku who just so happens to be the "new hope" for a Jedi renaissance.

Being a city dweller does not mean you cannot save the planet — or your food scraps. Climate change and resource management are big issues. Composting in any size space is not only possible, but it gives you a chance to reduce greenhouse gasses and reuse food scraps. Right now, about 40% of all food in the US goes to the landfill. In addition to planning meals and using your food in creative ways to reduce the amount that goes to waste, you can compost.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

Watching an ice cream pro build you a custom frozen treat mixed with your favorite fruit, candy, and/or toppings makes buying a cone even more exciting. But why go out for ice cream when you can create your favorite combinations in your own kitchen? While you might not have an expensive frozen slab for ice cream topping your kitchen counters, you can mimic the creamy consistency and customizable options from Cold Stone Creamery and Marble Slab any time you're craving it. Best of all, you don'...

Gas stations may be convenient for travel snacks, but the cost of shopping there sure can add up. If you're looking for easy, on-the-go snacks that fit into your travel budget, look no further. We've got 12 kid-friendly, portable food ideas you can make before leaving on your journey. You'll be amazed by how much money and time you will save with these satisfying travel snacks.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

The headline above may have some spice addicts shaking their heads, but, believe it or not, there are people out there who either don't like or can't handle a ton of spice.

If you think that "pawpaw" is just an affectionate name for your grandfather or a cute way of talking about your cat's feet, you're missing out on one of the most interesting fruits out there.

Up until the last 15 years or so, watching the commercials during the Super Bowl was arguably more exciting than the game itself. Super Bowl XXIV featured the San Francisco 49ers blowing out the Broncos, 55-10, in the worst Super Bowl beatdown of all time. The game might not have been that exciting, but the commercials sure were.

Sooner or later, you're going to come across a person at work that you don't like—or someone that doesn't like you. This can result in uncomfortable tension, insulting gossip, and a disrespectful attitude, to name just a few of the negatives. But it doesn't have to be that way. The next time you're having a workplace conflict with a particularly challenging coworker, the best thing you can do is keep your mouth shut, and here's how to do it.