Let's start with the bike: The most important thing on your bike, is your brake system, you will need the brake lever on your handle bars. When performing a wheelie, this will help you control speed and prevent you from falling on your butt. Your rear brake has to function properly or you will face the risk of falling.

This is a Google Tech Talk from March, 26 2008. Timothee Cour - Research Scientist lectures. Movies and TV are a rich source of highly diverse and complex video of people, objects, actions and locales "in the wild". Harvesting automatically labeled sequences of actions from video would enable creation of large-scale and highly-varied datasets. To enable such collection, we focus on the task of recovering scene structure in movies and TV series for object/person tracking and action retrieval. ...

Make deviled chicken with vegetables. Cooking Instructions

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.

Strings of DNA aren't the only things that contain helixes. With a bit of skill and practice, you can make your own rope helix for fun or bondage and BDSM play by watching this video by Two Knotty Boys.
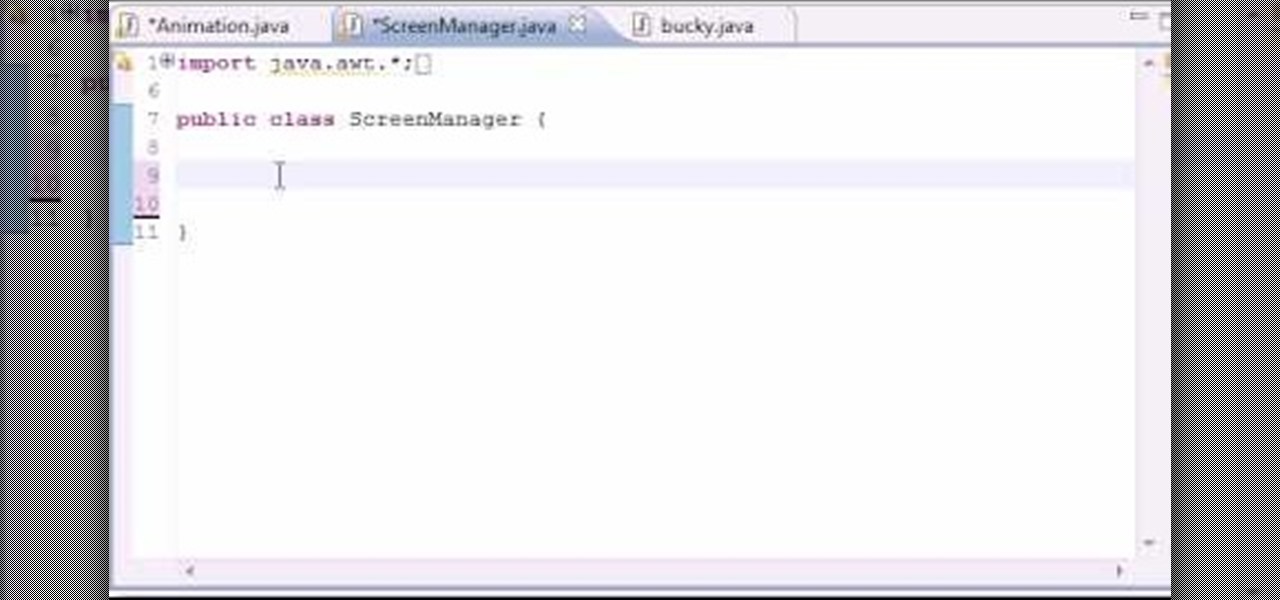
In this 14th video in a series about JAVA game development, "thenewboston" (Bucky Roberts) explains how to redefine your screen to avoid annoying flickering. Flickering in JAVA games often occurs because of time lags as the viewer watches the computer draw a new screen, pixel by pixel. Pre-installed code in JAVA can be used to eliminate this problem by taking advantage of "Buffering" and "Page Flipping". These functions permit you to delay the composition of a new screen until it is finished,...

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Play on your own private server on World of Warcraft, be sure to follow the instructions to the letter!

Learn how to hold a golf club properly in this sports video tutorial. The first thing is to allow the handle of the club to lie on the fingers of your left hand. It should lie diagonally. As you close your hand around the grip and lift the club off the ground, you should have a sensation that the handle is underneath the back of your palm and the last three fingers are applying pressure and squeezing it into your palm. The second step is to put the right hand on the golf grip in a diagonal li...

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

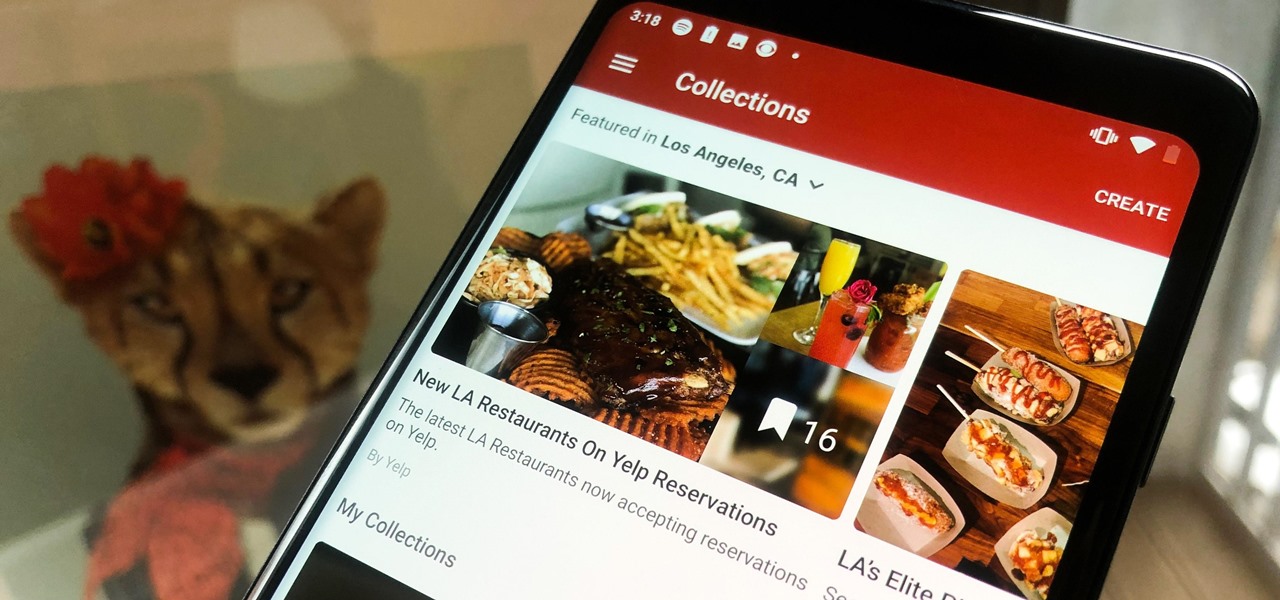
In the past, if you stumbled upon a Yelp listing you liked, you could bookmark it and check it out later on your profile. You can still take advantage of this feature in the mobile apps, but it's more refined now than it ever was thanks to Collections, a feature Yelp first added back in May 2018. You get more power over organizing, accessing, sharing, and discovering favorite businesses.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

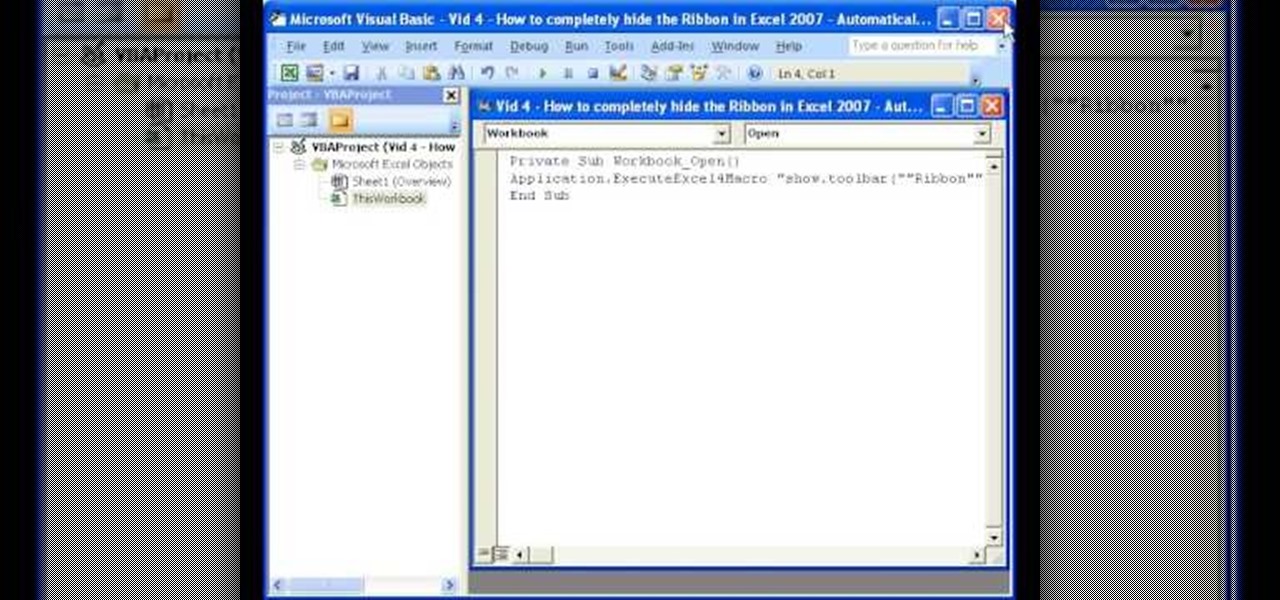
Teach Excel demonstrates how to completely hide the Ribbon menu system in Excel 2007 as soon as the workbook is opened. This will be done by writing a macro which hides the Ribbon only for the specific workbook in which the macro is implemented. Some helpful shortcuts are Ctrl+F1 which partially hides the ribbon, Alt+F11, which opens the Visual Basic screen, and Alt+F8, which opens the macros list. First, hit Alt+F11 to open the Visual Basic screen. Then double-click "This Workbook" on the le...

This is a steamy part of Heavy Rain for PS3. Steamy and sexy. But this is edited for nudity, so don't worry about seeing anything you shouldn't. See how to beat Chapter 5 - On the Loose.

in this episode of Heavy Rain, you confront the Shark. Just try not to get yourself killed when he pulls out that shotgun. Then, are you going to kill him, or are you not? See how to beat Chapter 4 - The Shark.

Now that the identity of the Origami Killer has been revealed, it should be easy to find him. In this walkthrough of Heavy Rain (PS3), you'll be in the killer's apartment. See how to beat Chapter 5 - Killer's Place.

Is the real killer captured now, or is a different man? Will you leave the case or will you continue the hunt on your own? The Origami Killer may still be out there, and it's up to you to find him. See how to beat Chapter 5 - Solving the Puzzle.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

The city is full of reptiles, and in Heavy Rain, the lizard is the most treacherous of all. See if the lizard can get you one step closer to solving the murder mystery of the Origami Killer. Porcelain isn't what it used to be. See how to beat Chapter 3 - The Lizard.

Butterflies are usually sweet and innocent, but not in the downpour that is Heavy Rain. In this PS3 walkthrough, see what's up with the Butterfly and if you're ever going to catch the Origami Killer. See how to beat Chapter 3 - The Butterfly.

Can't sleep? Of course you can't, not with a stage called "Sleepless NIght" in the video game Heavy Rain for the PS3. Watch a walkthrough of this level and see if you can get some zzz's, or see if you should be sleeping. See how to beat Chapter 2 - Sleepless Night.

This level of Heavy Rain has you in the Lexington Station, where hopefully you can make it through the crowd without embarrassing yourself. Watch the full video walkthrough to see what happens, and how to continue on. See how to beat Chapter 2 - Lexington Station.

Nothing can beat a father and son. Check out this Heavy Rain video walkthrough for the PS3 on "Father and Son". Do you think you're getting closer to catching the murderous Origami Killer in this level? See how to beat Chapter 1 - Father and Son.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

At Daily Mugshots, you will be able to save your own mug shot. The first thing that you will have to do is sign up for an account. You will need a Flash Player in order to use this site. After you have your account set up, you can take a picture from your computer. You can also upload pictures that you have taken elsewhere. When you save your picture, you will have to wait until it is finished processing. When the blue bar is filled, then it will be stored in your mug show.

In this video from rscp1050 we learn how to SSH into a jailbroken ipod touch or iphone. First go into Cydia and search for SSH. You need to download OpenSSH. Then also install Toggle SSH. After installed, restart the iphone. Now on your computer, download WinSCP. Once installed, open it. Type in your IP address which can be found by going to your settings on your iphone. Click wifi, and click the blue arrow next to your network. There is your IP address. Then, User name is root. Password is a...

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.