
News: 8th Wall Beats Google & Apple to Market with an AR Platform for Web
Google and Apple are working to enable augmented reality content for the web, but startup 8th Wall has managed to launch a web AR platform that works on mobile browsers now.


Google and Apple are working to enable augmented reality content for the web, but startup 8th Wall has managed to launch a web AR platform that works on mobile browsers now.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.
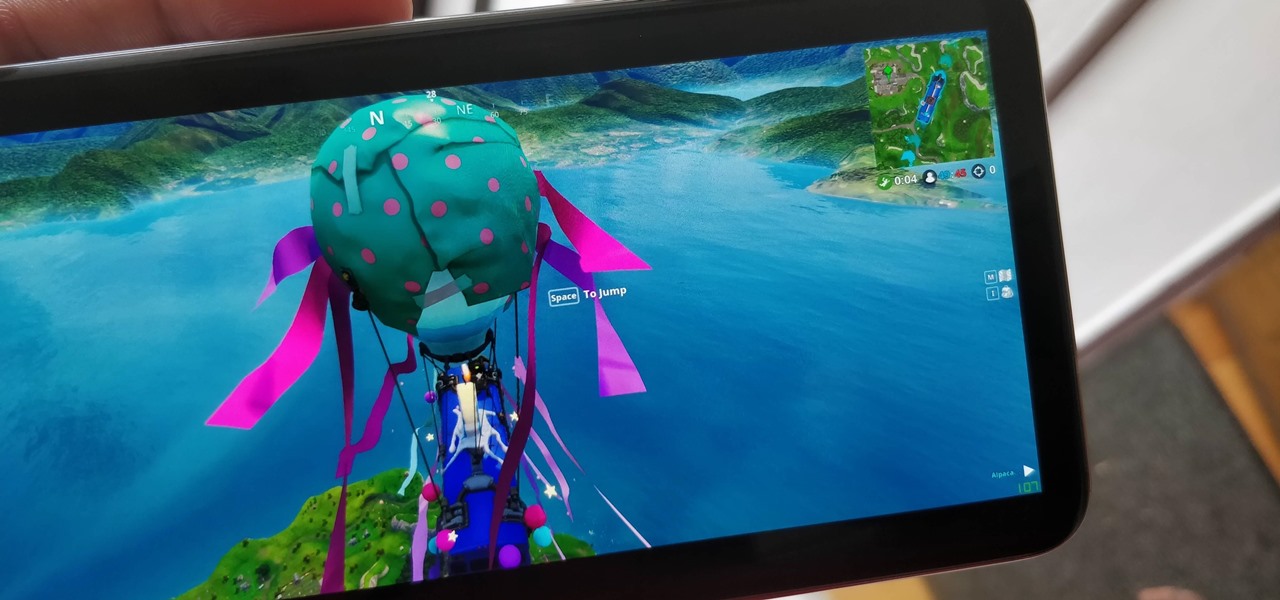
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.
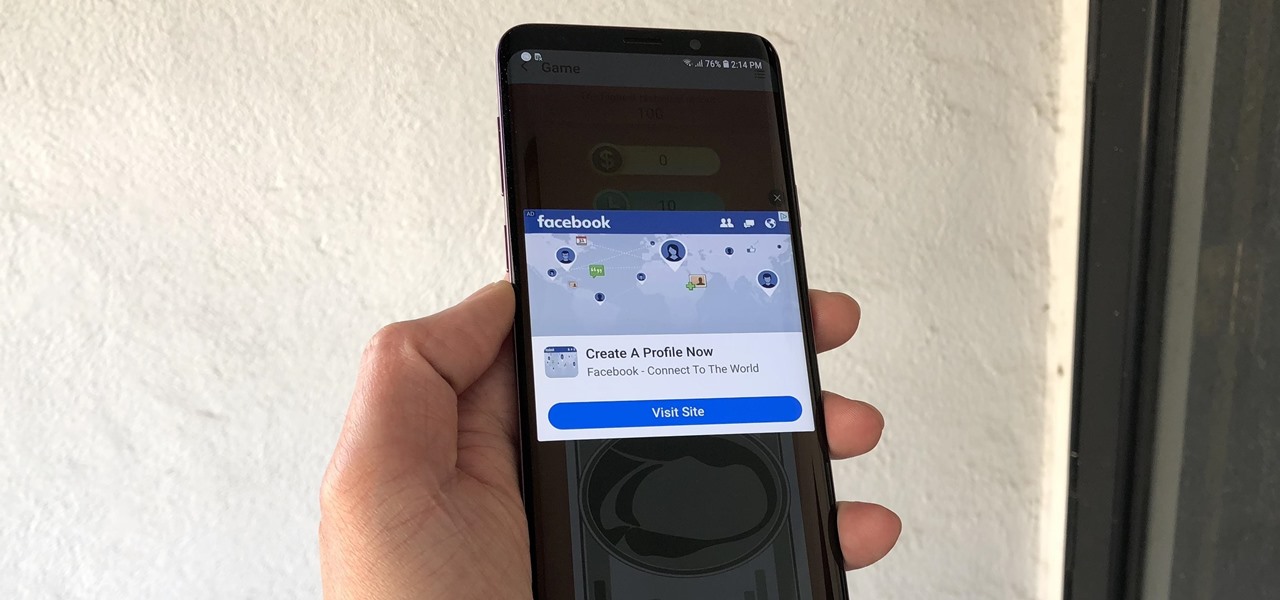
Android has gotten significantly better at handling intrusive ads over the years. Things have gotten to the point to where these nuisances are largely a non-issue for most of us. However, there are still a few ad-laden apps that fall through the cracks — particularly the kind that bombard your lock screen with ads.
Thanks in large part to our phones, many of us don't get the recommended eight hours of sleep. In Android Pie, Google introduced a feature called "Wind Down" that aims to help combat this. However, thanks to a creative app developer, we don't need to wait for Android 9.0 to enjoy this feature.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.
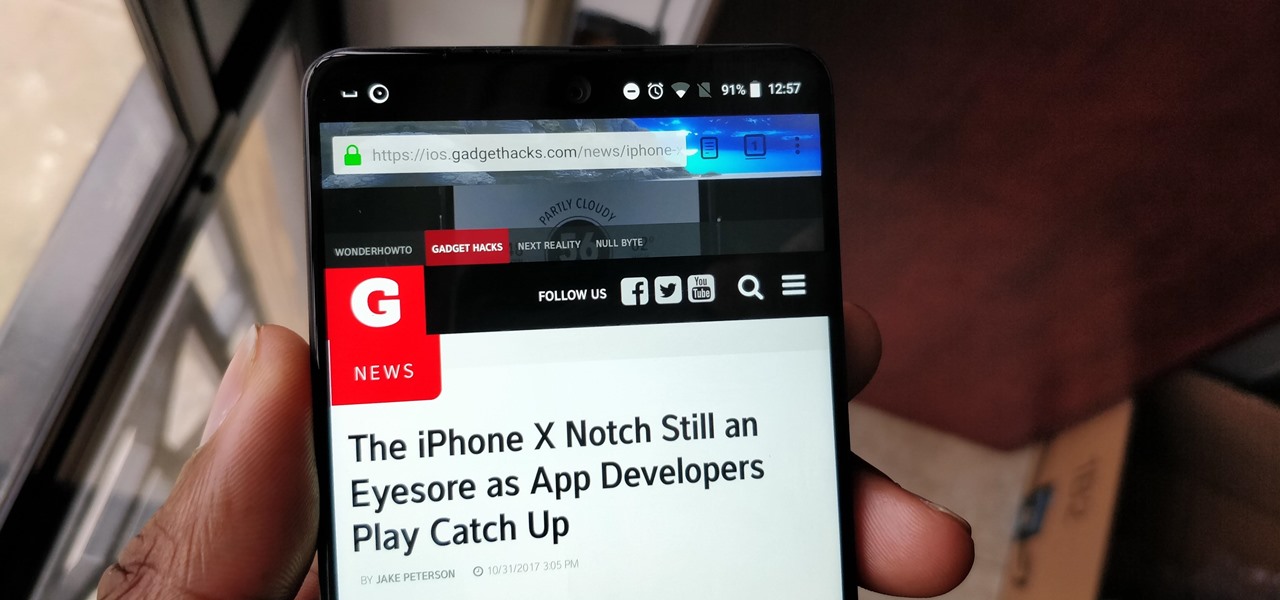
After several Android phones started incorporating the iPhone X's notch, the online community was vocal, with many expressing hatred for the trend. Well, thanks to XDA Forum Moderator Zacharee1, we already have an app to undo the incoming wave of notches.

As the week of the Game Developer's Conference hits the mid-point, we've already had some major announcements hit the AR space. The specific timing of these announcements are thanks in part to a conference within a conference called VRDC, aimed at VR, AR, and MR developers. And while the week is hardly over, the announcement that is still having a big effect on the developer population is the reveal of the Creator Portal for the long-awaited Magic Leap One device.
Unless you own an Exynos model, there won't be much development on the custom ROM front for the Galaxy S9. But that doesn't mean you have to put up with all of the UI quirks from Samsung Experience (née TouchWiz). With a little work, you can give your S9 a stock Android makeover, even without root.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

When Google first announced Android Oreo (Go edition), many believed these devices would be focused more on developing countries. However, thanks to ZTE, we'll be getting Android Go stateside, so US customers on even the tightest of budgets can still enjoy the convenience of a smartphone.

A new smartglasses powerhouse is rising in Europe, led by two of the region's leading brands, optical systems company Zeiss (also known as Carl Zeiss) and telecommunications giant Deutsche Telekom.

When it comes to mobile gaming, you have a lot of fantastic options. Most flagship devices on the market, such as the Galaxy Note 8, iPhone 8 Plus, or OnePlus 5T, are perfectly capable of giving you an excellent, immersive experience. If you're looking for the ultimate way to experience Animal Crossing: Pocket Camp or something with more action like Into the Dead 2, the Razer Phone is the winner.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

In case you didn't already know, augmented reality is here. It's no longer just an idea in a cyberpunk novel. And while augmented reality has been around for a long time, the actual technology is finally catching up to the idea.

Razer, the company known for PC peripherals and laptops, is joining the smartphone industry with a new device. Rumors have been swirling since they announced an event on November 1 at 4 PM EDT, but now, we have our best look yet with a leaked promotional video before the actual announcement.
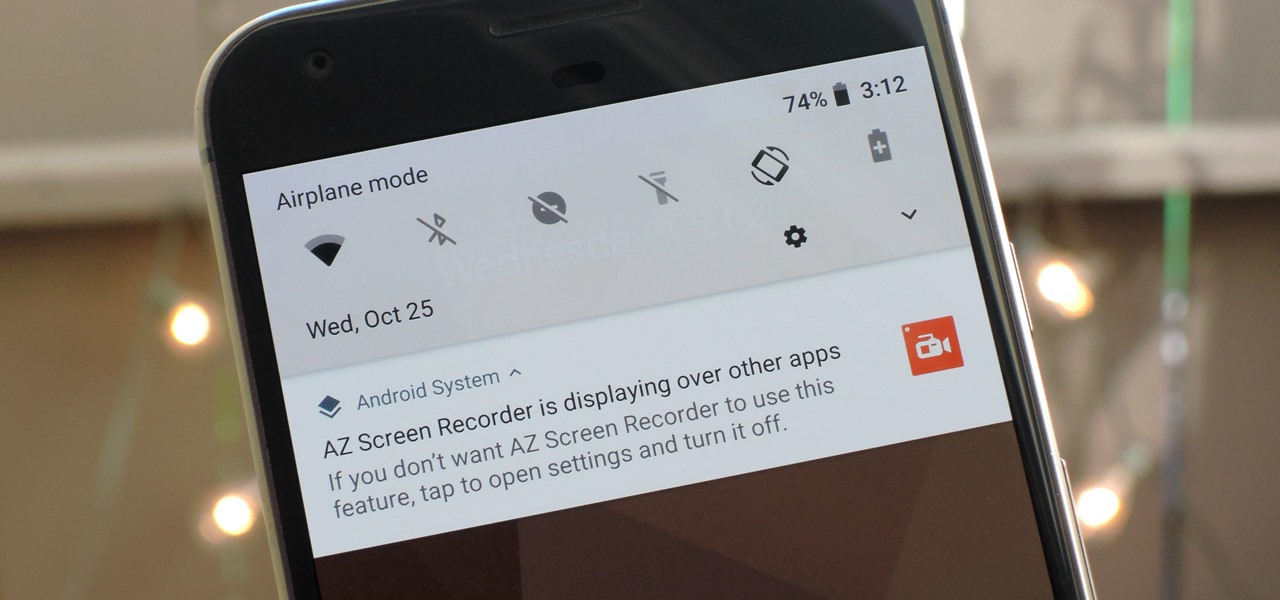
One of Android 8.0's central themes was battery improvements. Google implemented background restrictions and a few other under-the-hood changes, but the biggest battery-saving measure was almost user-hostile: A static notification that tells you when any of your apps are running in the background.
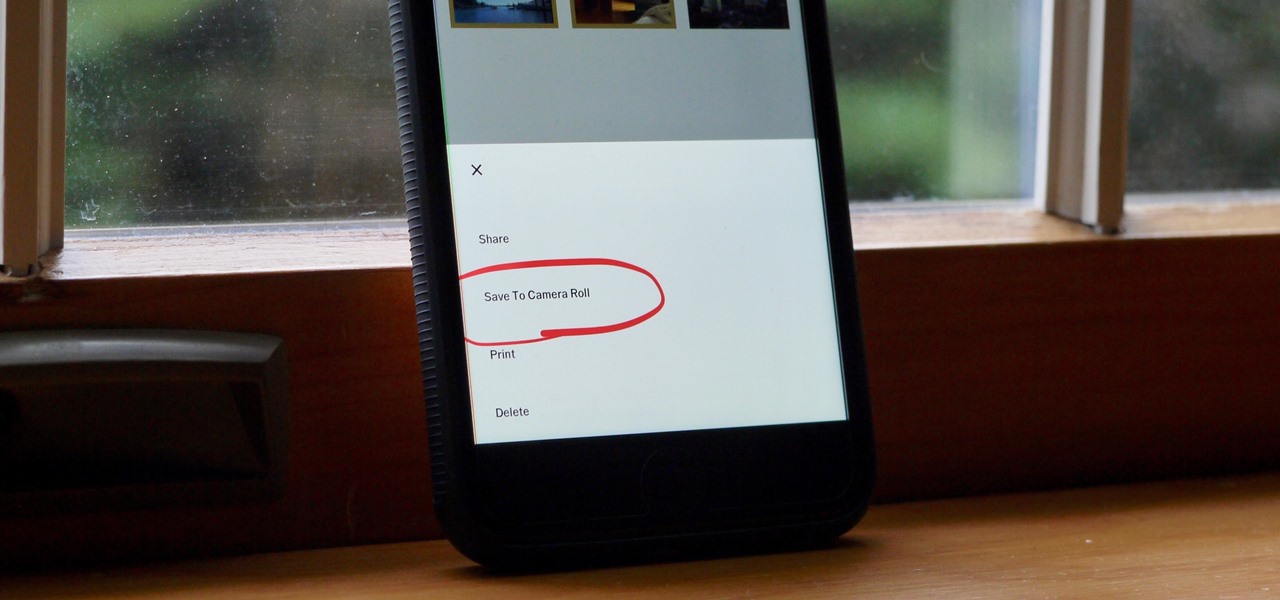
Whether you use VSCO to take all of your photos or you use it primarily to edit photos you take with others apps on your iOS or Android phone, you're at some point going to want your VSCO pics to end up in your Camera Roll or Gallery. VSCO doesn't add them there by default, but there's a couple of ways to get them there.
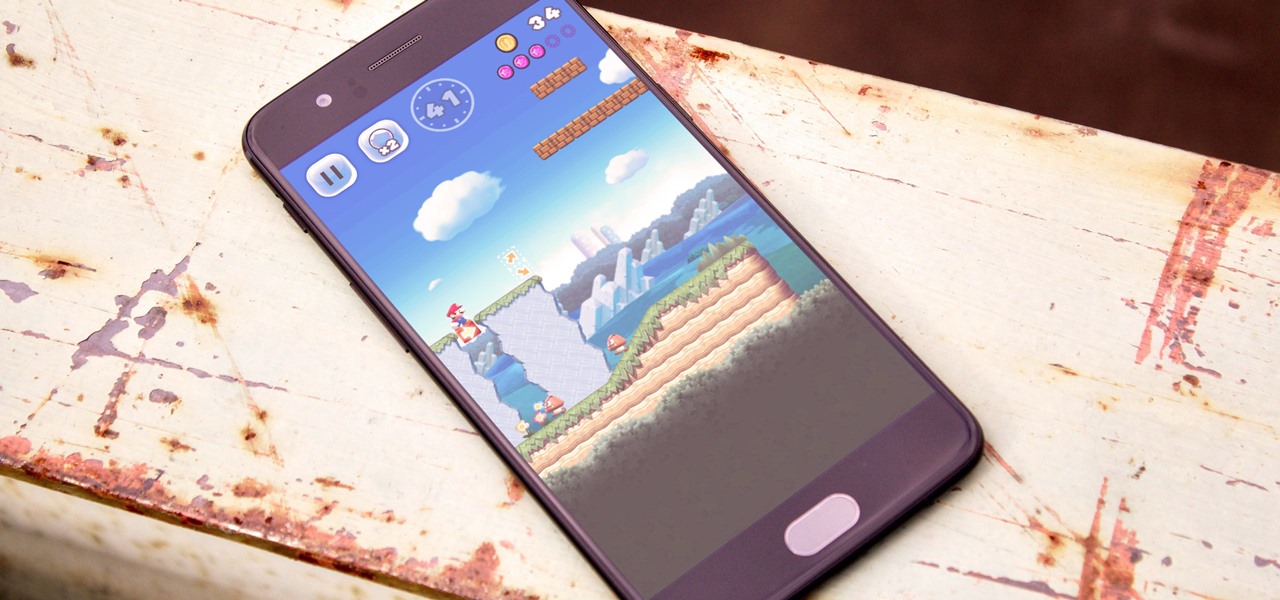
You have a lot of choices when it comes to your next smartphone. iPhone, Galaxy, Pixel, G6, V20, and many more all vie for your wallet. Each of these phones are great for different purposes, but what if your main interest is mobile gaming? Which phone will give you the longest Minecraft session, or the best performance for Pixel Gun 3D?
Let's face it — our phones are our heart and soul. We do everything on them, from banking to media consumption. However, sometimes we download apps that we don't want others to see. Sometimes, we wish to hide apps so that, in the rare times we lend our phone to someone, we don't get judged for a lifetime by what they find.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

Elon Musk's SpaceX is launching the world's most powerful rocket. The Tesla founder and CEO says the company is about to go through "manufacturing hell" to make delivery schedules for its new Tesla 3. Somehow, Musk says Tesla will offer Level 5 driving (so you can take a nap while your car drives you to and from work) within two years.

The Google Assistant is great about understanding what you actually mean, so you don't have to issue exact commands like you do with Amazon Alexa, for instance. But even though it's a master of colloquial speech, it could still be better, and that's where shortcuts come into play.
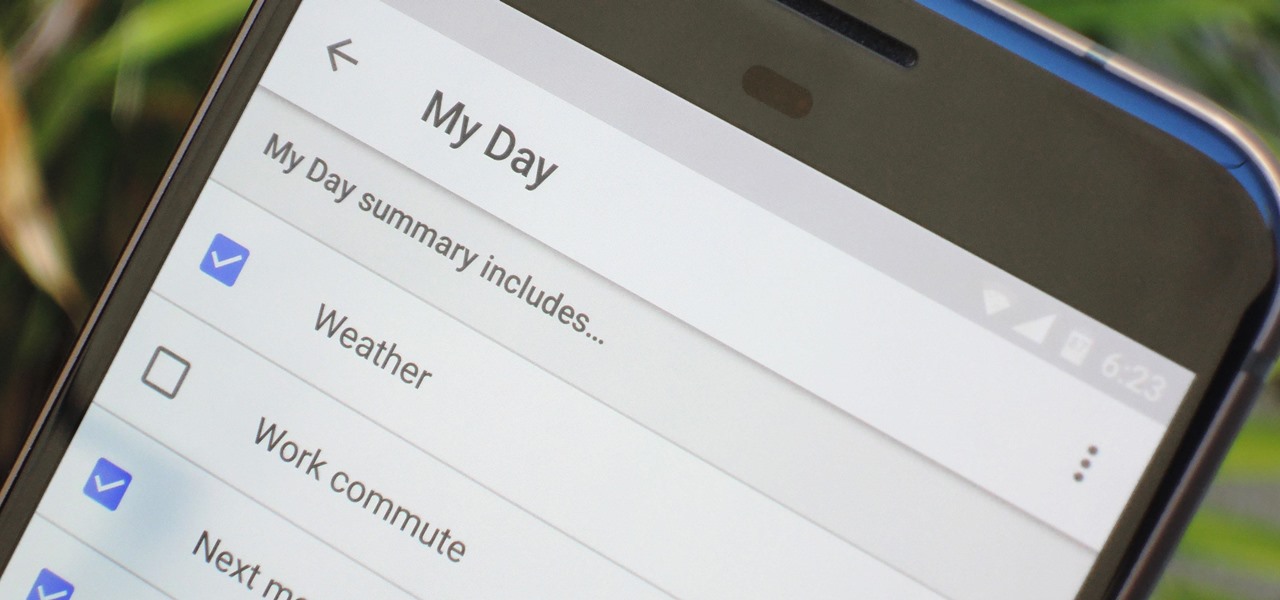
The Google Assistant comes in several different flavors. There's the baked-in Google app on Android, the dedicated Google Assistant app on iOS, and the Assistant-powered Google Home smart speaker. But no matter how you access it, your Assistant will only get better if you take some time to personalize things.

If you are an NYC commuter like me, then I'm sure you know how bad the city's transportation has gotten.
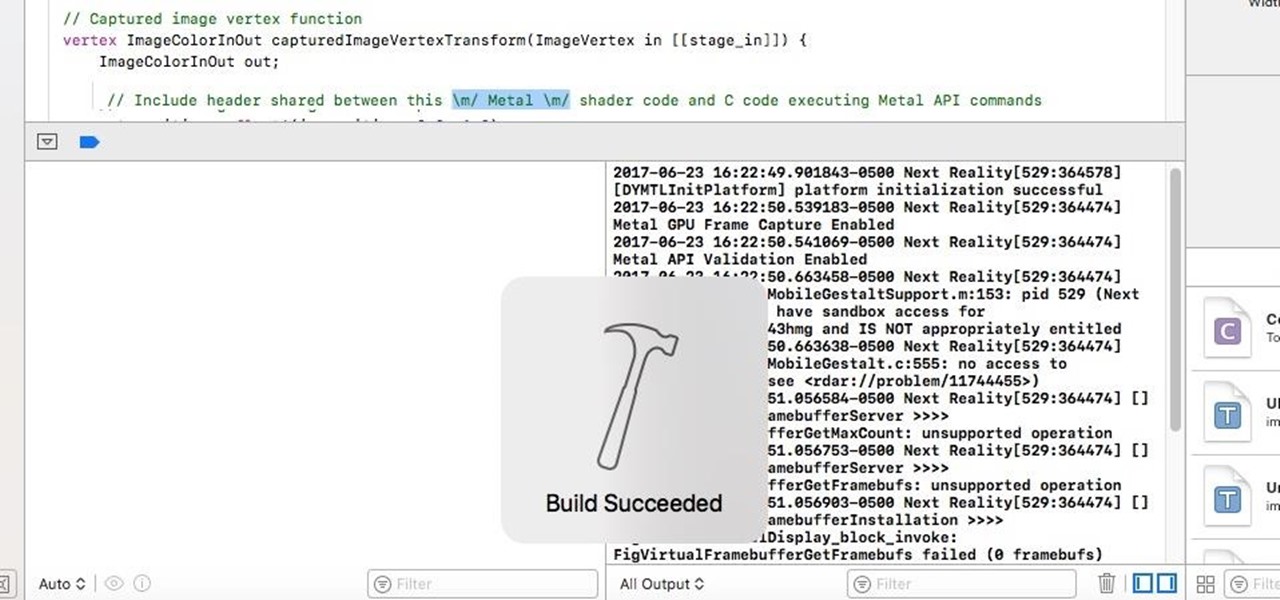
In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

Leading tier-one supplier Continental has confirmed it will sell driverless platforms developed from BMW, Mobileye, and Intel's previously announced alliance, giving the company a potential edge over competitors by widening the range of technologies it offers directly to OEMs.

Getting support for your mental health is now as easy as opening up Facebook Messenger. By just opening up the Messenger app, you can connect to Woebot, a new chatbot developed at Stanford trained in administering cognitive behavioral therapy (CBT).

Our canine best friends could spread our bacterial worst nightmare, according to a recent study. The problem with drug-resistant bacteria is well known. Overused, poorly used, and naturally adaptive bacteria clearly have us outnumbered. As science drives hard to find alternative drugs, therapies, and options to treat increasingly resistant infections, humans are treading water, hoping our drugs of last resort work until we figure out better strategies.
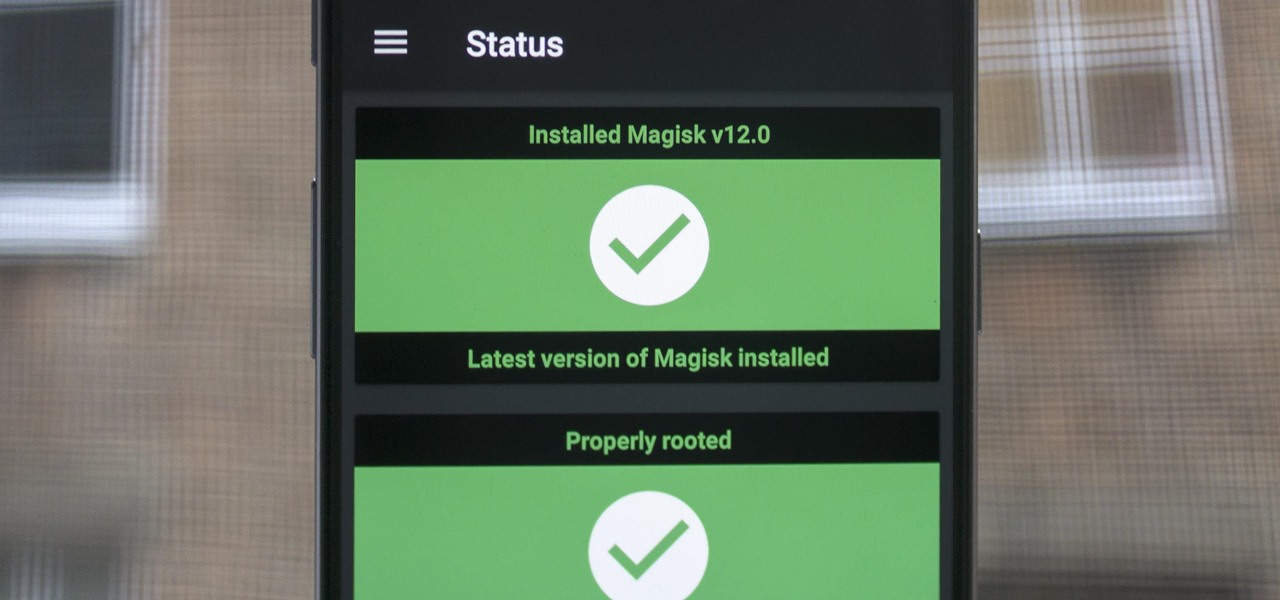
When Google added new security measures to Android Marshmallow, it had a lasting impact on the entire process of rooting. These measures prevent the the Superuser daemon (the process that handles requests for root access) from getting the permissions it needs to do its job at boot. In order to get around these issues, Chainfire created the systemless root method.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.
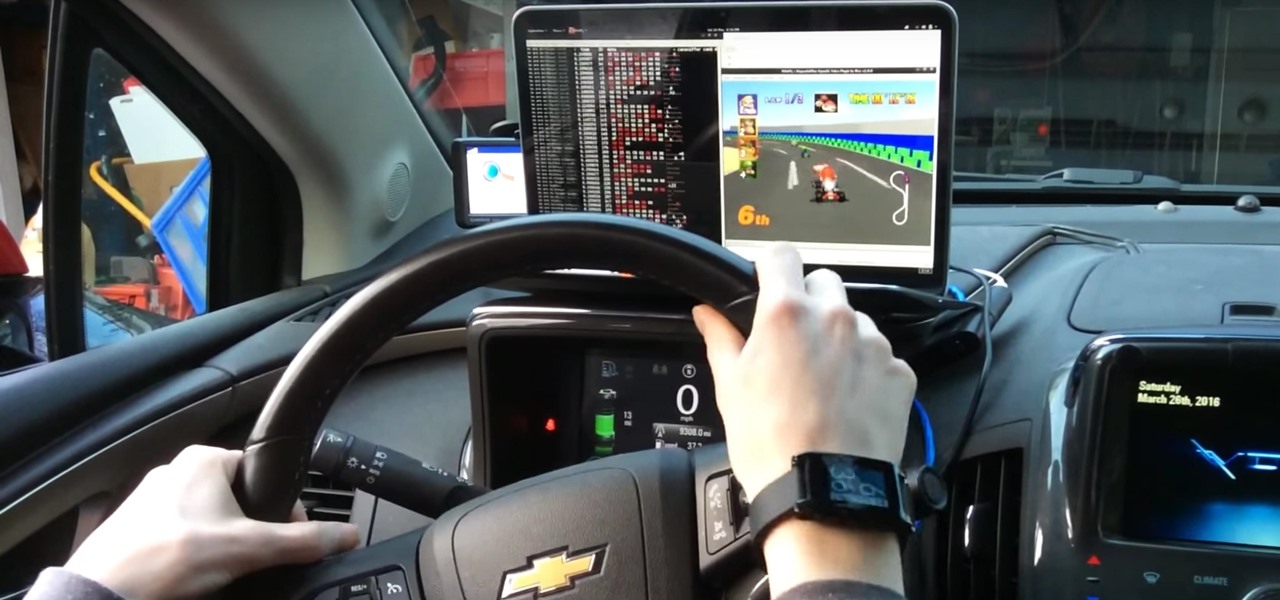
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

A state of emergency has been declared in Malaysia's northeastern Kelantan state after an outbreak of avian influenza virus H5N1.
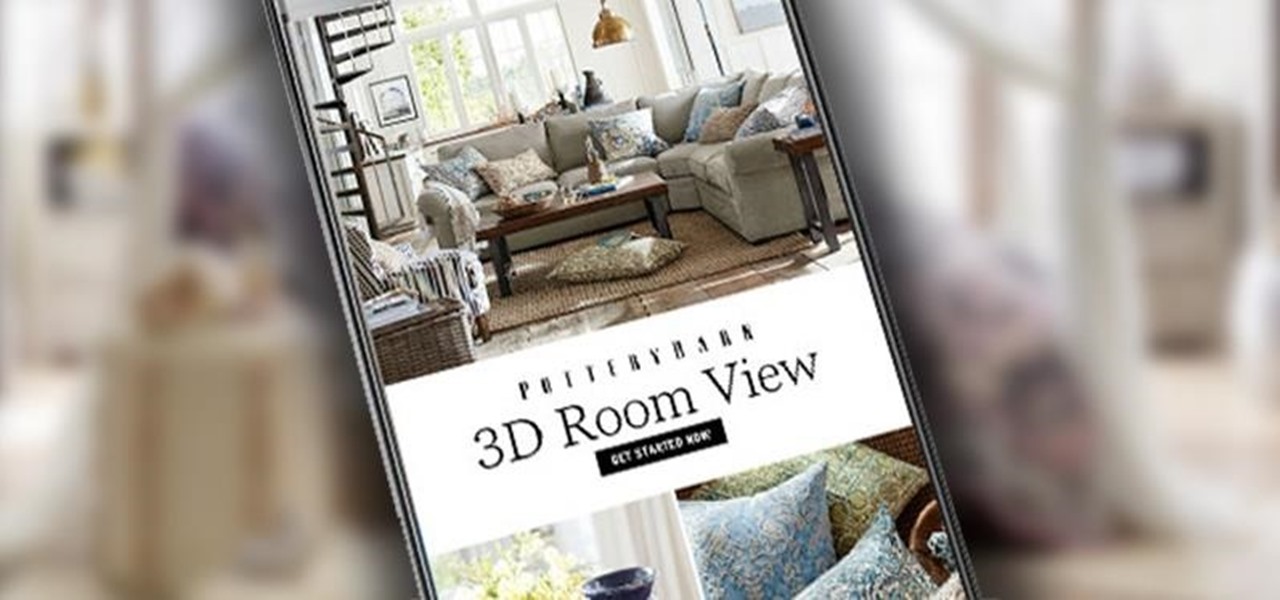
Pottery Barn has teamed up with Google to create 3D Room View, a new mobile app to allow all wannabe interior designers (like me) to pick out the perfect couch, table, or whatever, and then overlay it onto a spot in his or her house.