
How To: Instantly transpose on the ukulele
This is a useful tutorial for handling transposition and key changes. It works just as well on other stringed instruments like mandolin, tenor or plectrum banjo, whatever.


This is a useful tutorial for handling transposition and key changes. It works just as well on other stringed instruments like mandolin, tenor or plectrum banjo, whatever.

Perform this advanced soccer ball handling move (Full Sole Rollover) by rolling completely over the ball before turning. This makes a great ball touch drill.

Learn the basics of correct receiving and ball handling for receivers in football.

The biggest update to arrive since iOS 18 and iPadOS 18 just came out, and it's packed with new features and changes for your iPhone or iPad. From new Apple Intelligence capabilities to Game Center improvements and new calling tools, there's a lot going on in iOS 18.1 and iPadOS 18.1.

Have you ever had the stomach flu, aka the 24-hour flu? Well, chances are high that you never had influenza, but an intestinal infection called gastroenteritis.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

Don't Miss: Revolutionary Pasta Hacks You Need to Know

The iPhone 5 will be here in no time. Pre-orders started at 12:01AM PST this morning and it's expected to start shipping in about two weeks. Verizon, AT&T, and Sprint are all handling unlimited data plans differently, so if you currently have an unlimited plan and are going to get the iPhone 5, you'll want to know what your carrier is doing before you upgrade so you don't end up with a very unpleasant surprise on your next phone bill. Verizon

In these PHP basics video the tutor shows how to do form processing. Handling forms in PHP is basically the main functionality of PHP. The forms in HTML take the values of a from and send them to the PHP in real time to do the form processing. In this video the tutor shows how to make a HTML form from the scratch inserting a form into it with some fields and buttons. Now he makes the form post a method to a PHP page when you submit it. Now he shows how to make a PHP file from the scratch by w...

Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for iPhone and iPad.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

After playing Mario Kart Tour for a little while, you'll notice it's a bit different from previous games in the series. The biggest change is how they've deferred to new players by automating many of the controls. But what if you want the traditional experience? We've got you covered.

Frozen meat is a saving grace for weeknight meals. Whenever I crave a certain protein, all I need to do is defrost it. Sometimes, I don't even need to defrost it in order to use it.

If you have ever attempted to mix and shape your own meatballs or burger patties, you may have endured bits of meat continuously and stubbornly sticking to your hands. This can make shaping more challenging than it should be.

This online manual shows you all of the ins and outs of the Canon EOS 40D digital SLR camera. The guide covers: handling the camera, shooting modes, ISO speed, AF modes, Drive modes, image quality, highlight tone priority, picture styles, white balance, and live view mode

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

Even if your cat drives you a little nuts, don't worry, because a new study says that cats pose no risk to your mental health.

This is how I upgraded my 2002 Monte Carlo End Link and Sway Bar Bushing to Polyurethane ones from MOOG. My factory hollow sway bar broke and it was replaced with a 33mm solid one from Dorman.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

This science experiment deals with sublimation of dry ice into carbon dioxide (CO2) gas. In the video, I'll demonstrate how pushing a quarter into a block of dry ice makes the quarter scream and shake vigorously.

Apple's iOS 18.2, iPadOS 18.2, and macOS Sequoia 15.2 updates are here, packed with enhancements that take device intelligence to the next level. New Apple Intelligence features lead the release, offering smarter tools for creativity, productivity, and everyday tasks. However, there are also new features for all iPhone, iPad, and Mac models — not just those supporting Apple Intelligence.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.
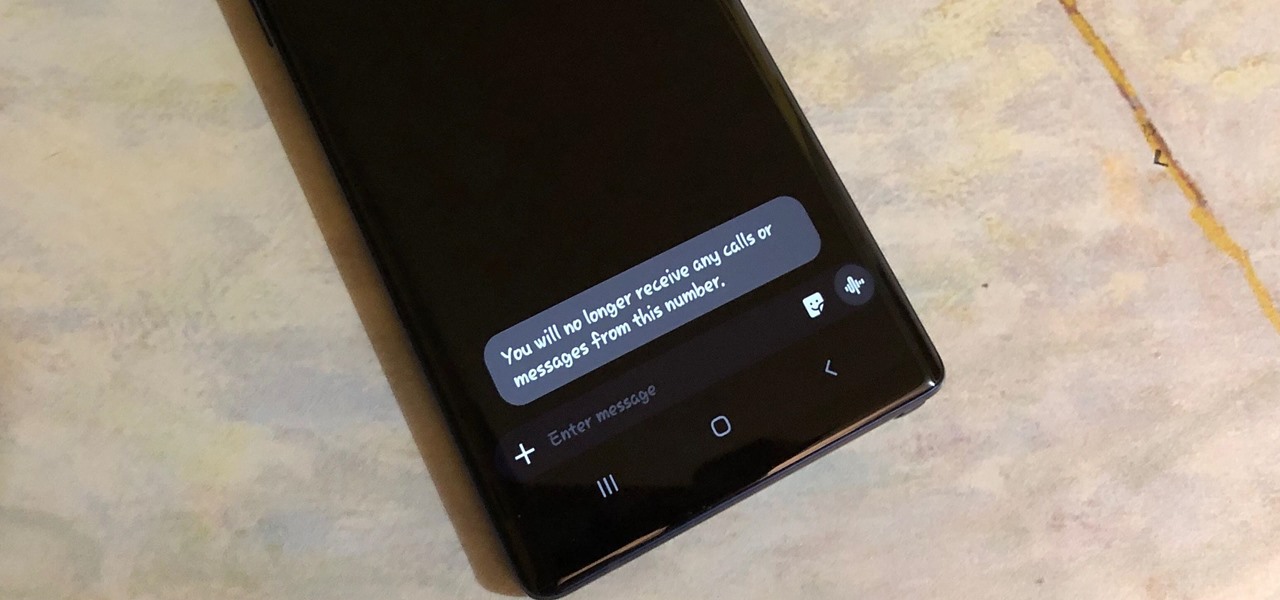
With so much of our personal data floating around the web, it's nearly impossible to get away from spam calls, texts, and emails. Unfortunately, this isn't just limited to the online world — filling in your contact information in a raffle ticket with the hope of winning that shiny new car in the mall, for instance, can often result in getting swamped with spam texts containing sketchy loan offers.

While the story of augmented reality headset maker Osterhout Design Group has come to an end, the epilogue of its demise continues.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.
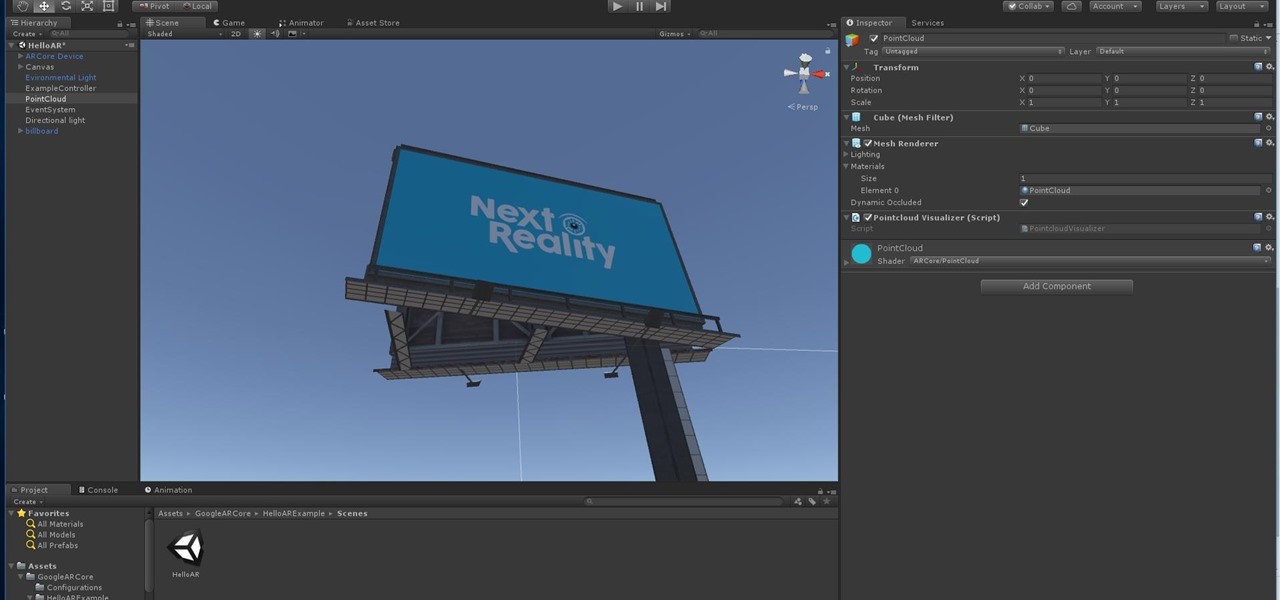
Being on the bleeding edge is a place that you will get cut from time to time, as has been the case for many developers in the HoloLens space.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

If you've been debating on whether or not HTC's new virtual reality headset, the Vive, is worth the $800 price tag, then you'll be able to find out for yourself soon enough.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Welcome back everyone. This article isn't going to contain anything related to scripting, but rather some updates about the series. We'll be quickly discussing what we've covered so far and what is to come.
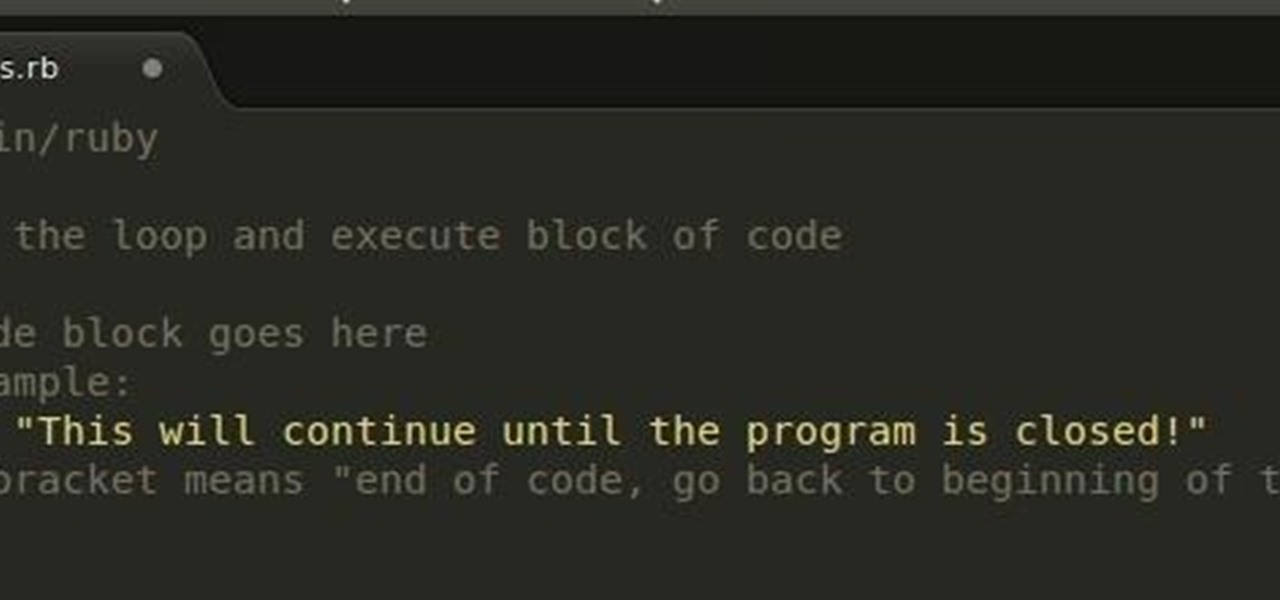
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

How to build a sandbox / sandpit using pallet wood. Using pallet wood is a really easy way to make a sandbox / sandpit and to top things off they're free! This is another one of my reclaimed wood projects that was a heap of fun to make. Like all pallet projects, it is a good idea to use Heat Treated Pallets as they are safe for handling.
Good battery life is one of the most important things any phone or tablet should have, but iOS 7 isn't always that great at handling power consumption. That leads to tunnel vision on the status bar's battery meter. After all, you don't want to be stranded in the middle of nowhere with no juice left to make a call.

The following video demonstrates and explains a classic physics experiment called a vacuum cannon. Typically these cannons are made on a much smaller scale to fire ping pong balls, but I wanted to keep things interesting with this 4" diameter monster.