Creating a haunted house for Halloween was a big deal when I was growing up, and the neighborhood kids were always coming up with ways to try and out-do each other when it came to this frightful night. One beloved game was to blindfold the participants and play the Withered Corpse.

"Cooking" with liquid nitrogen seems like one of those activities that should be strictly limited to pros who are appearing on Top Chef, but it's the only way you'd ever be able to make Dippin' Dots at home. If that isn't enough of a reason for you to get some LN2 for your kitchen, check out this dose of pretty:

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.

Navigating through row after row of plants, my tiny fingers would reach into the leaves to pluck all the vile little creatures from their homes and deposit them into a can of gasoline. Potato bug duty, my least favorite gardening chore. Growing up, my family had a small garden every year. And every year, I was recruited to help plant, maintain, and eventually harvest the vegetables from it. There were some tasks I didn't mind, but the ones I hated most usually involved bugs (have you ever see...

Food can smell great before, during, and after cooking. A pot of stew simmering away on the stove will tantalize you all afternoon, and there's nothing better than the smell of fresh-baked cookies lingering in the house for hours.

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

This week, the recurring theme in augmented reality can be summed up fairly succinctly: content is king.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

HMD (the company currently making Nokia-branded phones) only released one flagship device last year, with the rest of the phones falling in the mid-range and entry-level tiers. However, at Mobile World Congress 2018, HMD announced their ambition to become a top five smartphone maker in 3–5 years. Meeting this goal will require penetration in all markets — especially the United States — and it looks like Nokia will get the ball rolling early this year.

Deadly rat lungworm parasites have found their way into Florida. The parasitic worm relies on snails and rats to complete its life cycle, but don't let this nematode's name fool you. This worm can cause meningitis and death in humans who inadvertently consume snails, frogs, or crustaceans harboring the infective parasite.

We know that healthcare-related facilities can be fertile ground for antibiotic-resistant bacteria, but recent research suggests your produce aisle might be too.

The noses of kids who live in areas of intense pig farming may harbor antibiotic-resistant bacteria, presumably acquired from the animals, according to a new study by scientists at the Johns Hopkins Bloomberg School of Public Health, UNC Gillings School of Global Public Health, and Statens Serum Institut in Denmark, published in Environmental Health Perspectives.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

The LG V30 has finally been announced and was rumored to be released sometime in September, but September has come and is almost gone, while LG fans have been waiting anxiously. The V series offers a more robust media experience when compared to LG's other flagship, the LG G6. Since the phone has been announced, we do have all of the details for the third flagship in LG's V series, and believe me, it's sounds like it'll be worth the wait.

Hospitals are places we go to get well, and we don't expect to get sick or sicker there. But a study from researchers at the Cleveland Clinic, Case Western Reserve University School of Medicine, and Cleveland VA Medical Center in Ohio found that hospital floors in patient rooms were frequently contaminated with healthcare-associated pathogens—often dangerous multi-drug resistant bacteria.

A group of researchers from Stanford University and Princeton University has put together the largest RGB-D video dataset to date with over 1,500 scans of over 700 different locations across the world, for a total of 2.5 million views.

Ecosystem changes caused by agricultural choices in Brazil are creating a dangerous microbe mix in exploding populations of vampire bats and feral pigs.

Although their effectiveness is waning, antibiotics remain a front-line defense against many infections. However, new science reveals using the wrong antibiotic for an infection could makes things much worse.

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

When to throw meat away is a common question, and one I often ask when faced with meat sitting in the fridge after a few days. With vegetables, you can usually tell on sight (or with this guide) when they're past due, but meat is not as simple.

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.

If you're a sushi lover but not an expert sushi maker, you can still enjoy the flavors of sushi rolls at home with these deconstructed sushi dishes.

Herbs, both fresh and dried, can be intimidating and mysterious to cooks. Just how much is too much? How do you prepare them?

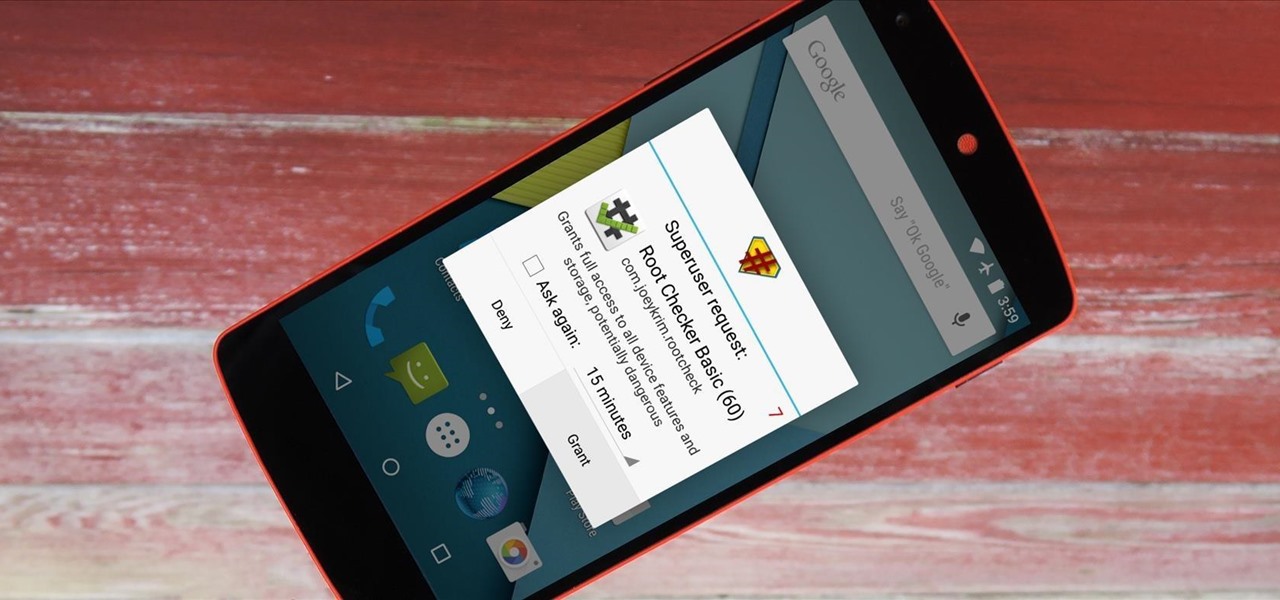
It didn't take long at all for developer Chainfire to sort out a root method for the new Android 5.0 Lollipop. After handling a few issues with changes to the SELinux kernel module, Chainfire pushed out an update to his popular SuperSU root app.

Your beloved Samsung Galaxy S3 is nearing the end of its life cycle. Sure, it can do most of what newer devices can, especially if you were lucky enough to receive the KitKat update, but your diminishing battery and scratched up screen have seen better days.

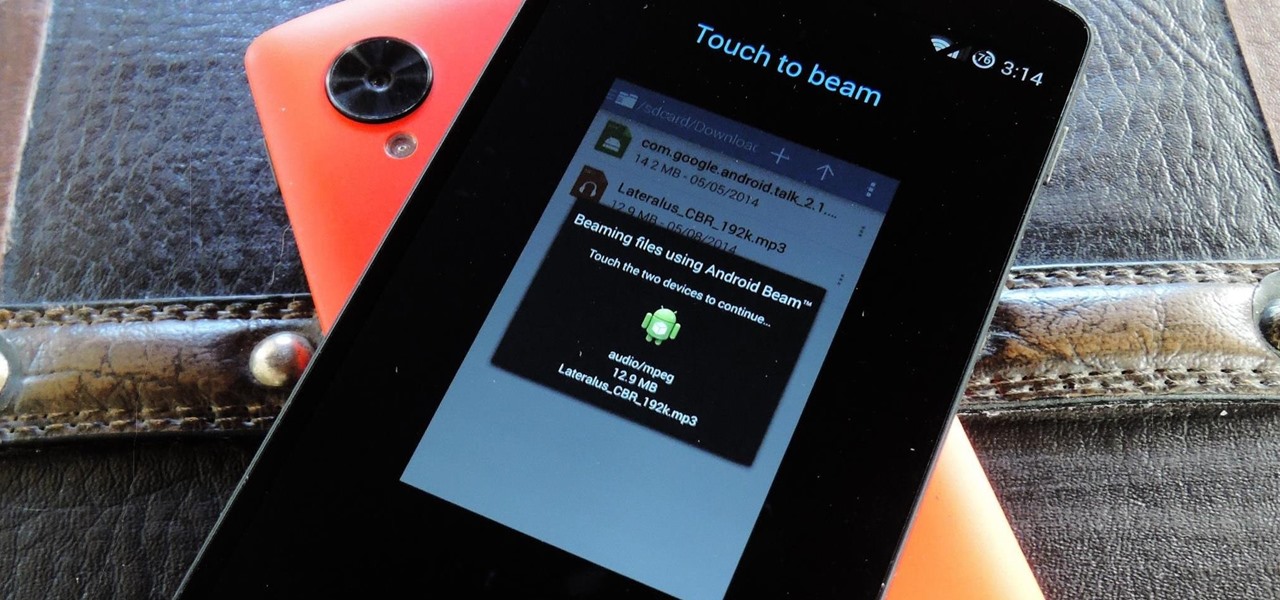
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

There's no reason to wait for Halloween to play with dry ice. It definitely creates a creepy fog-like effect when you add a little water to it, but there are some other really cool things you can do wit dry ice. Here are just 5 non-Halloween ways to use dry ice for tricks or pranks.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

When filtered through the prism of the top stories of the year, the business of augmented reality 2019 was defined as much by epic failures of AR startups as it was by the promising developments that propelled the industry forward into 2020.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.