Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.

Mason jars are a DIYer's best friend, nearly on par with duct tape and paper clips. Why? Because you can use mason jars for so many things besides just canning and drinking, and I'm not talking about other obvious uses like basic storage containers or miniature terrariums. I'm talking about MacGyver-style ingenuity. With a little creativity, the uses for those jars are practically endless.
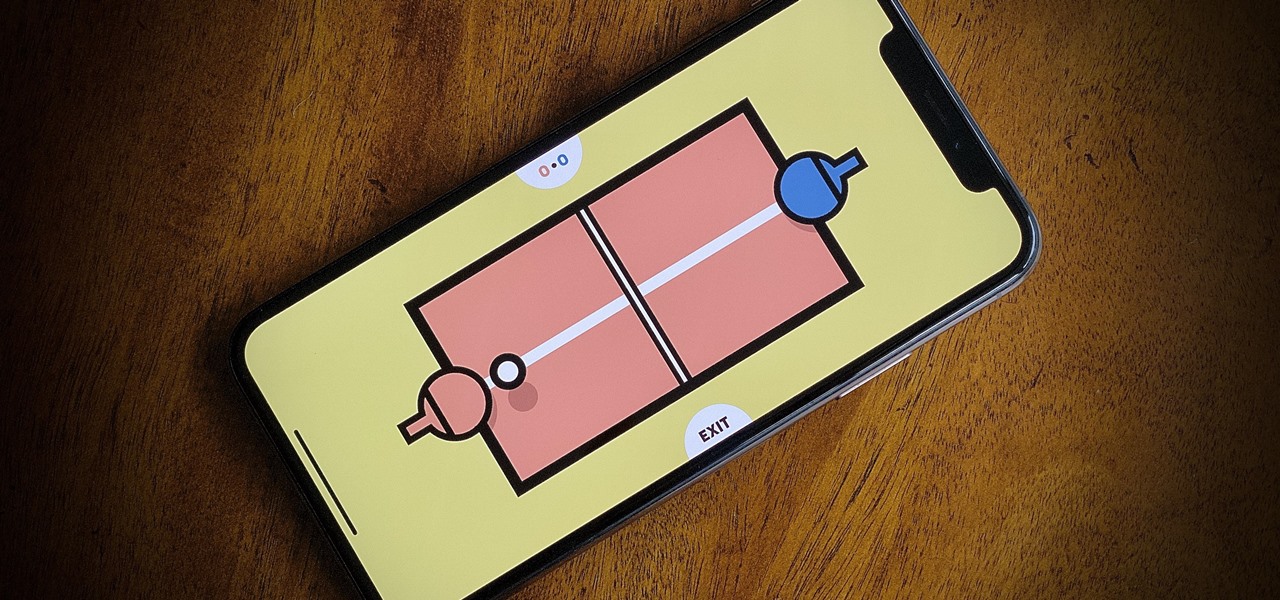
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.
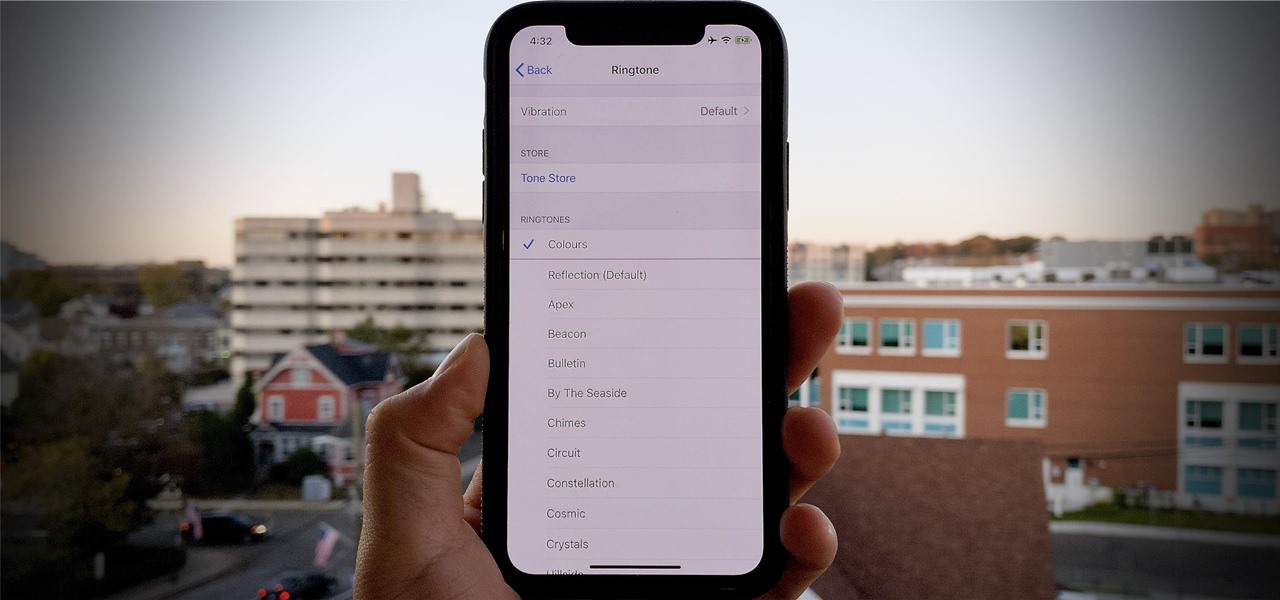
Have you ever heard someone else's iPhone ringing and thought it was yours? Of course you did. iPhone ringtones are iconic, but not varied. If you're using one of the more popular iOS sounds, you'll likely encounter it in the wild multiple times. Why bother, when you can create your own custom ringtones right on your Mac.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has lived this before and knows what to do.

How do I get rid of these zits?! Whether its pimples, blackheads, or whiteheads, the name is the same, and the name is acne.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

It's truly amazing how far smartphone camera hardware has come in such a short period of time. It took roughly 5 years to advance the image processing capabilities from a pixelated mess to the crisp and clear photos we can take today. This reaches well beyond the megapixel spec race, since camera modules these days sport vastly improved optics, wider aperture, and even larger pixel sensors that capture more light.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Whenever you buy a newer iPhone model, you get a set of Apple EarPods with remote and microphone built-in. Aside from their comfortable design and high-quality sound they provide, these headphones offer additional functionality beyond just pausing and playing music.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck.

Few summertime drinks are as sweet, tart, and refreshing as lemonade. It can cool off even the hottest day and help you relax poolside, on the beach, or just sitting around the house.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

With T-Day on the horizon and approaching rapidly, you are probably in one of two camps. The one that is eagerly awaiting the holiday feast with barely-contained drool. Or the one that involves breathing heavily into a paper bag while worrying about your lack of oven and stovetop real estate, while also bemoaning the lack of multiples of you to get all the prep work done.

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

French toast is one of those things that everybody kind of knows how to make, but few people know how to do really well. And while the dish originally does hail from France (its original name, pain perdu, means lost or wasted bread), it has become a beloved American breakfast dish.

Break out the office supplies and kitchen utensils, because improving your morning makeup routine is about to get a lot easier. Some of the things you have lying around the house can provide the perfect solution for some of the most common beauty problems. We've collected 10 of our favorites.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

It may sound irrational, but I bet a lot of you actually avoid doing any work at work—but not on purpose. You might be simply struggling with motivation, or you might just be overdosing on the caffeine. Whatever the issue, getting focused takes lots of time and effort.

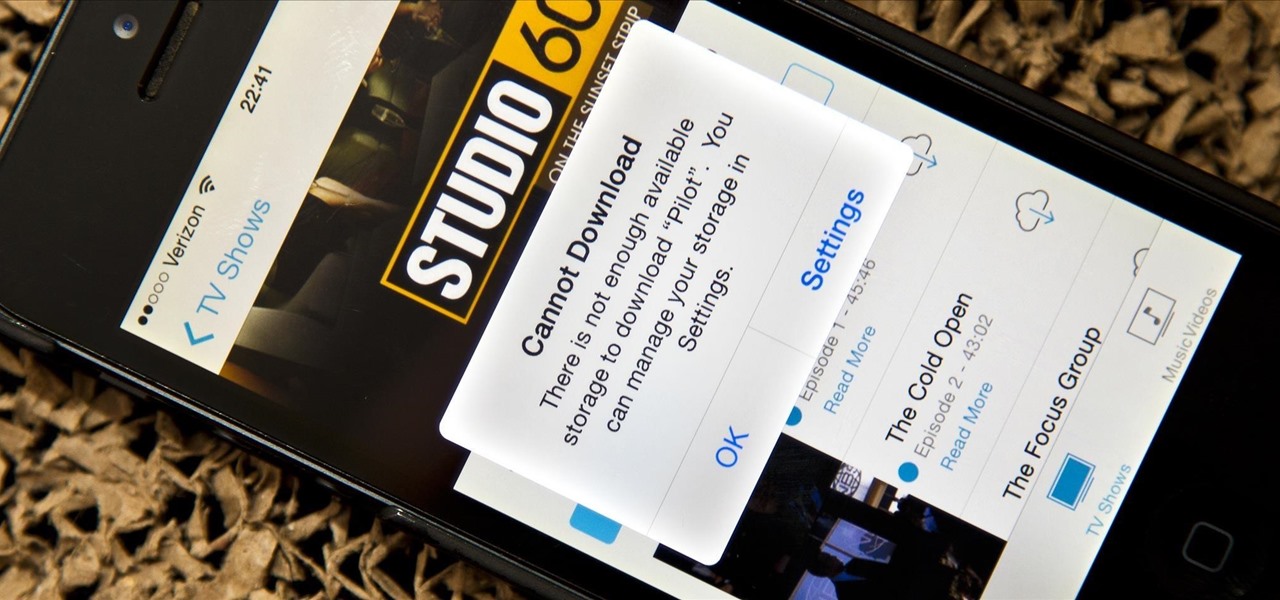
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

One of the hardest, most intimidating parts of making your own Steampunk guns from scratch is the wooden stock of the gun. To be fair, it's probably the hardest part. It requires the most artistry, and is the easiest to mess up.

Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete!

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.