Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

The iPhone XR offers a discounted experience compared to the expensive iPhone XS and XS Max. However, that lower price tag comes with some caveats, such as "Haptic Touch" in lieu of 3D Touch. If you think these two "touch" features are the same, think again. Before you get an iPhone XR, you'll want to know all the excellent features 3D Touch you might miss. Can you go without them?

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

When temperatures drop and hit new lows during the cold, winter months, it's hard not to crank the heat up. That means increased energy bills each month, no matter if you rely on gas, electric, or another fuel for heating.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

The camera situation on the all new HTC One is a little daunting. The M8 has not one, not two, but three camera lenses built in. First, there's the 5 megapixel selfie machine up front, then around back, there's the new Duo Camera with a refined UltraPixel sensor. HTC has done things differently here, and the UltraPixels and dual lenses means that the M8 doesn't necessarily take pictures like you'd expect—and that's not a bad thing. With a little guidance and some easy tricks, you can use all ...

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Over the past several weeks, I’ve had the pleasure of test driving Samsung’s next big thing, the Galaxy S4. After putting the GS4 through its paces, I have a clear picture of what this device is capable of. I’ve covered the features of the device before, and now I’ll tell you why I believe it's currently the best Android phone on the market. Initial Impressions

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

Your iPhone has a powerful feature that can keep your secrets hidden from other people, and you'll never have to worry about sharing or showing someone something embarrassing or incriminating ever again.

Your iPhone's Mail app has a lot of fantastic productivity features, such as unsending emails, follow-up reminders, opening drafts from almost any view, the snooze option, bulk-selecting messages, and the formatting toolbar, but one of the most helpful ones might just be the one you're not using.

Night Shift, Dark Mode, Reduce White Point, and Zoom's Low Light Filter all help reduce the harmful effects on your body's clock that bright iPhone and iPad screens have at night. But there's another option on iOS and iPadOS that turns your entire display red, and it's useful for so much more than just late-night browsing in bed.

Downloading content from TikTok is relatively easy, even if the video is protected, but the same can't be said of Reels, Instagram's version of short-form videos. Instagram doesn't make it easy to download content unless it's your own, and that's especially true with Reels. However, there is a way to bypass Instagram's restrictions on your iPhone and save videos locally without ever leaving the app.

Google dropped new features for its Pixel lineup of phones, and there's something here for everyone.

If you have a PlayStation 5 and an Android phone running Android 12, you can stream and play your PS5 games right from your mobile device using PS Remote Play. While simply pairing your PS5's DualSense wireless controller with your phone will give you the basic controls to play third-party games, Remote Play takes a little bit more work to set up.

Magic Leap has had a rough couple of years, highlighted by high-profile executive departures, lawsuits, troublesome patent shuffles, and massive layoffs.

Microcontrollers like ESP8266-based boards have built-in Wi-Fi, and that's really cool, but what's even cooler is that certain pro models of the D1 Mini also have a port where you can connect a directional antenna. This can give you exceptional range, but if you were to just plug one in after opening the package, it most likely wouldn't work.

Samsung and Google have done some amazing work together in the past, particularly with Android related projects. But after years of an inexplicable lack of interoperability, the primary smart home hardware divisions from both companies are finally on the same page — starting right now.

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

You can't get the same gaming experience on your iPhone as you would on a PlayStation 5, Xbox Series X, or gaming computer. The processing power is less, the controls inadequate, and there are many on-screen distractions, all of which make mobile gaming less enjoyable. While you can't fix many of these issues, there is a way to prevent some problems, and that's thanks to Guided Access.

It's common knowledge these days that Apple puts great cameras into their iPhones. So, it probably comes as no surprise to learn that the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max sport some excellent shooters. What you might not know, however, is that these cameras are quite literally capable of Hollywood-quality video. So don't be surprised to see one of these filming a Netflix series.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

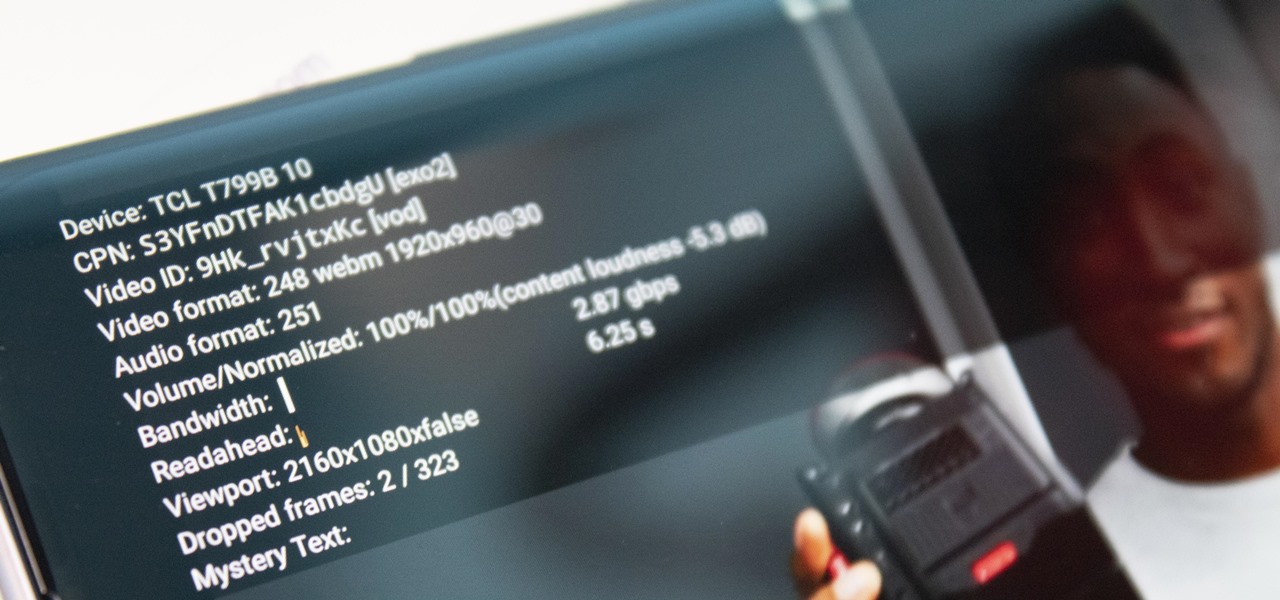
Most streaming platforms have seen a huge viewership increase in the past few months. As a result, wireless carriers and ISPs are struggling to provide the necessary bandwidth for everyone, resulting in some customers being limited to DVD quality. The same applies to YouTube, YouTube Music, and YouTube TV, but you can see the resolution being used and change it to something better.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.